
Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
Last Update Mar 10, 2026
Total Questions : 393
We are offering FREE 350-401 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 350-401 free exam questions and then go for complete pool of Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) test questions that will help you more.




Refer to the exhibit. Which Python snippet stores the data structure of the device in JSON format?
Which AP mode allows an engineer to scan configured channels for rogue access points?

Refer to the exhibit. The existing configuration must be updated to terminate all EXEC sessions after 120 minutes. Which command set should be applied?
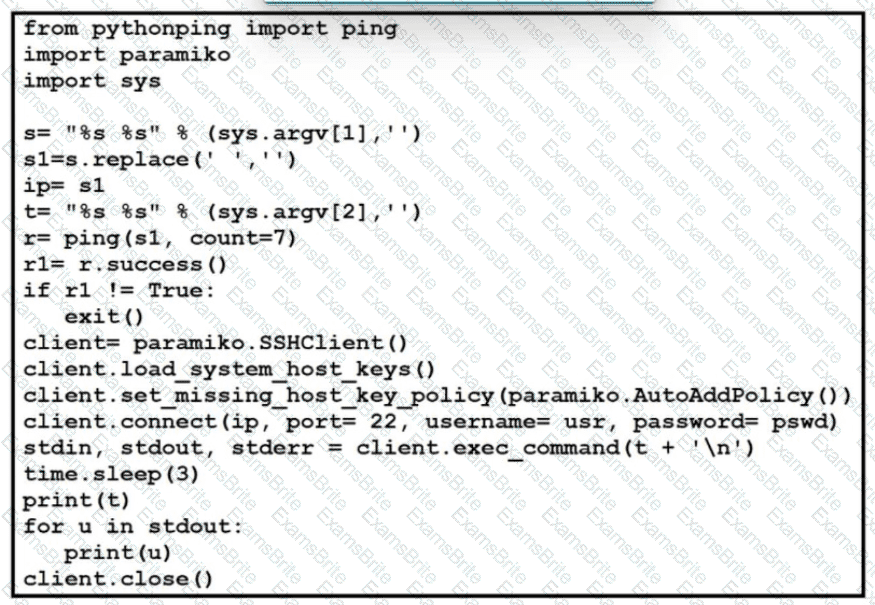
Refer to the exhibit. Which action results from executing the Python script?
Which LISP device is responsible for publishing EID-to-RLOC mappings for a site?
A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP. Which deployment model meets this requirement?
In a campus network design, what are two benefits of using BFD for failure detection'? (Choose two.)
Which protocol does Cisco SD-WAN uso to protect control plane communication?
Which method ensures the confidentiality of data exchanged over a REST API?
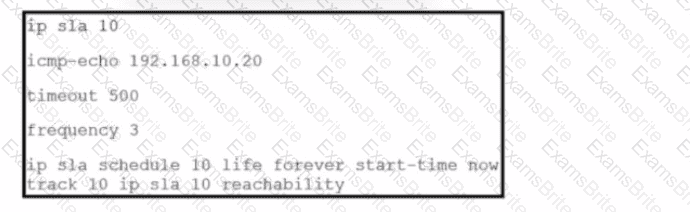
Refer to the exhibit. The IP SLA is configured in a router. An engineer must configure an EEM applet to shut down the interface and bring it back up when there is a problem with the IP SLA. Which configuration should the engineer use?
What is one characteristic of Cisco Catalyst Center (formerly DNA Center) and vManage northbound APIs?
With IGMPv2, which multicast group address does the IGMP querier use to send query messages to all hosts on the LAN?
In Cisco CatalystCenter(formerly DNA Center) Inventory, the Software Version of a networkdevice displays a status of OUTDATED. What does It me?
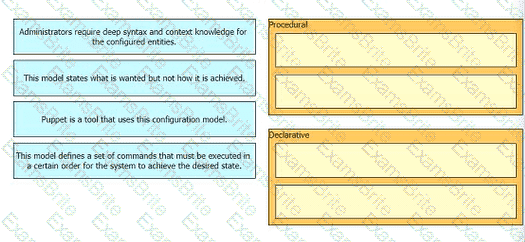
Drag anti drop the characteristics from the ten onto the configuration models on the right.
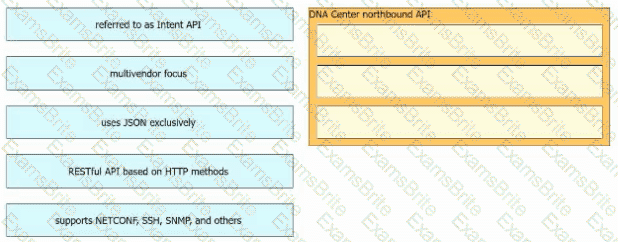
Drag and drop the Cisco Catalyst Center (formerly DNA Center) northbound API characteristics from the left to the right. Not all options are used.
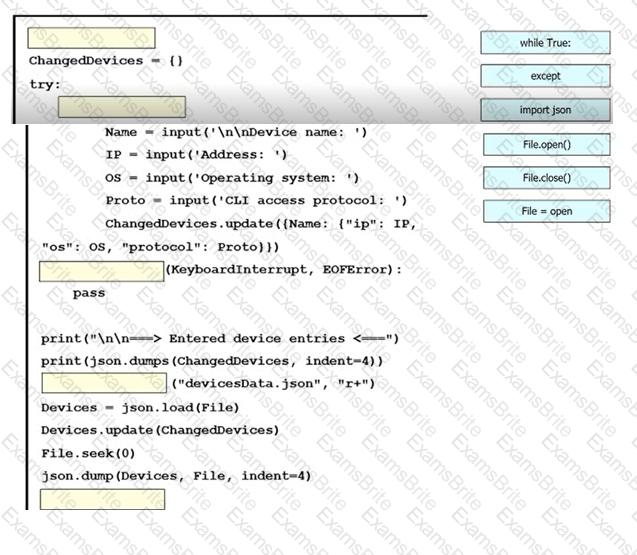
An engineer must create a script to append and modify device entries in a JSON-formatted file. The script must work as follows:
Until interrupted from the keyboard, the script reads in the hostname of a device, its management IP address, operating system type, and CLI remote access protocol.
After being interrupted, the script displays the entered entries and adds them to the JSON-formatted file, replacing existing entries whose hostname matches.
The contents of the JSON-formatted file are as follows

Drag and drop the statements onto the blanks within the code to complete the script. Not all options are used.
Why are stateless calls executed by REST API useful in cloud applications?
What is used by vManage to interact withCiscoSD-WAN devices in the fabric?
Which HTTP status code is the correct response for a request with an incorrect password applied to a REST API session?

Refer to the exhibit. The key value pairs must be extracted by iterating through a list of tuples. Which statement completes the snippet and prints each key value pair as a tuple?
Which feature allows HSRP to failover from the active route processor to the standby route processor without loss of data or path change?
A corporate policy mandates that a certificate-based authentication system must be implemented on the wireless infrastructure. All corporate clients will contain a certificate that will be used in conjunction with ISE and user credentials to perform authentication before the clients are allowed to connect to the corporate Wi-Fi. Which authentication key option must be selected to ensure that this authentication can take place?
Which feature does the Cisco DNA Center User-Defined Network workflow provide?