
Network Security Expert 8 Written Exam
Last Update Feb 28, 2026
Total Questions : 105
We are offering FREE NSE8_812 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE8_812 free exam questions and then go for complete pool of Network Security Expert 8 Written Exam test questions that will help you more.



An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
Refer to the CLI configuration of an SSL inspection profile from a FortiGate device configured to protect a web server:

Based on the information shown, what is the expected behavior when an HTTP/2 request comes in?
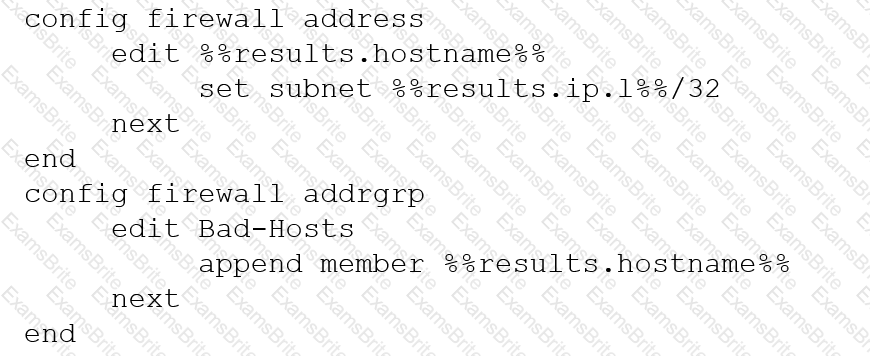
Refer to the exhibits.
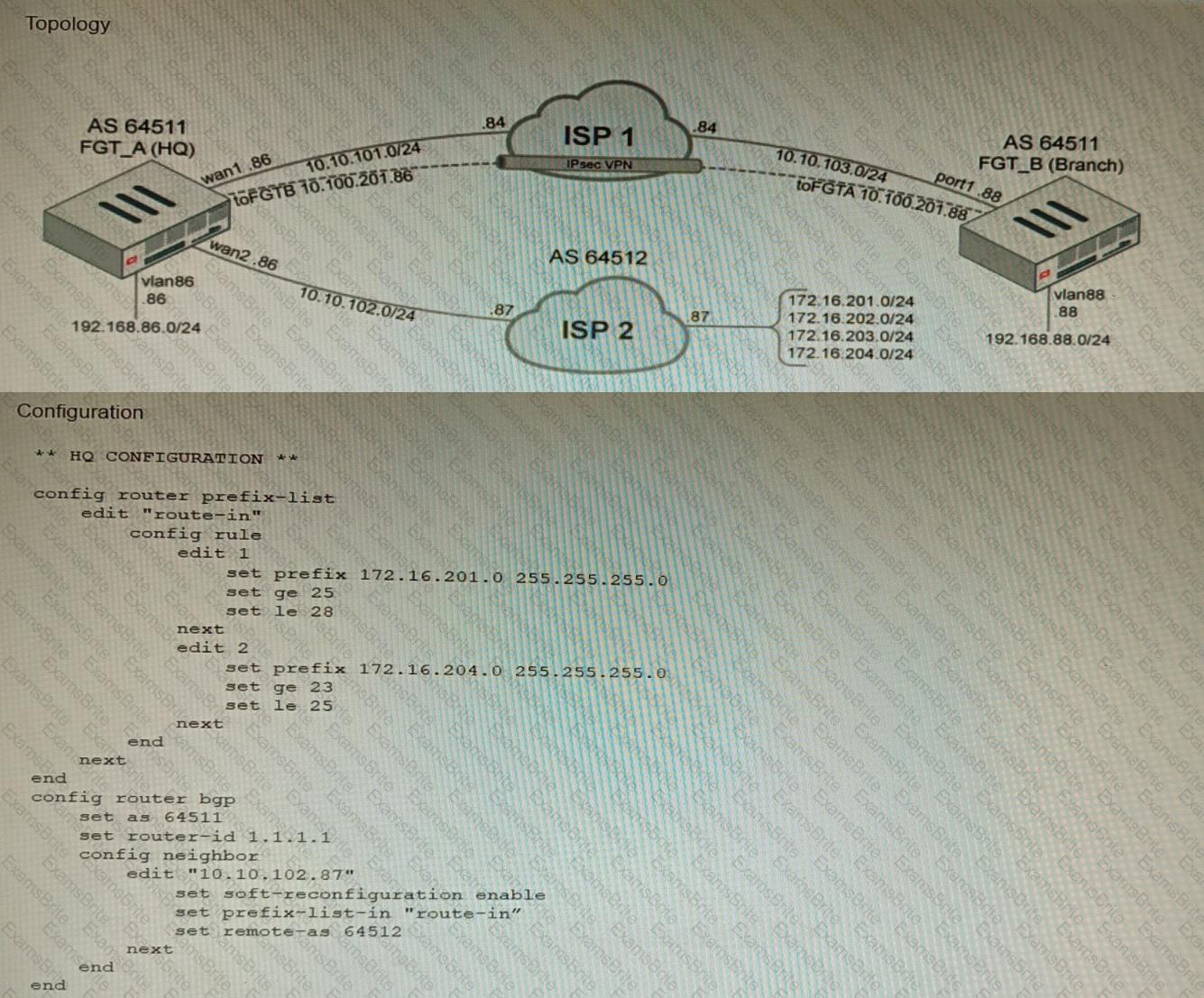
A customer has deployed a FortiGate with iBGP and eBGP routing enabled. HQ is receiving routes over eBGP from ISP 2; however, only certain routes are showing up in the routing table-Assume that BGP is working perfectly and that the only possible modifications to the routing table are solely due to the prefix list that is applied on HQ.
Given the exhibits, which two routes will be active in the routing table on the HQ firewall? (Choose two.)
Refer to the exhibit showing an SD-WAN configuration.
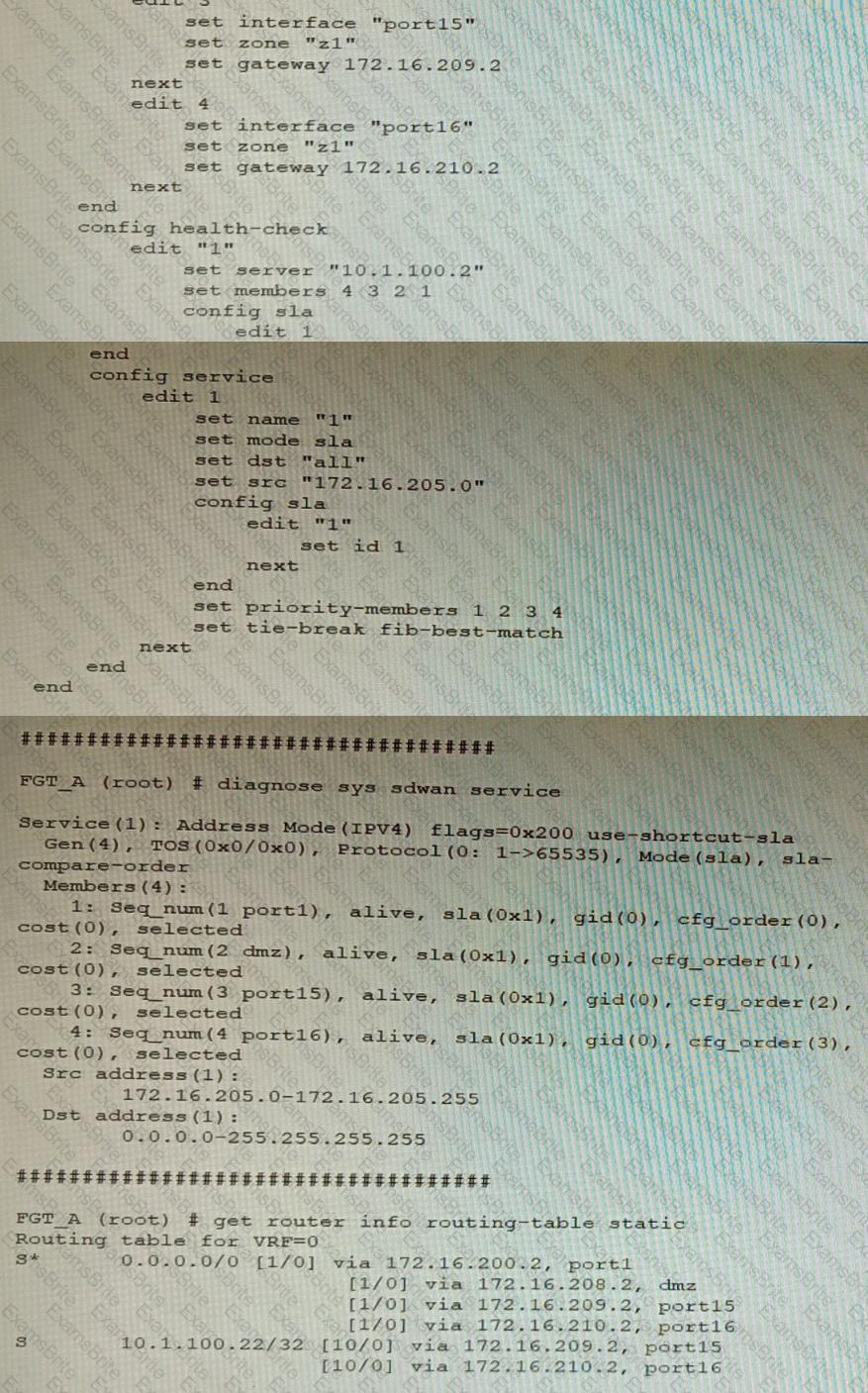
According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
Refer to the exhibit.
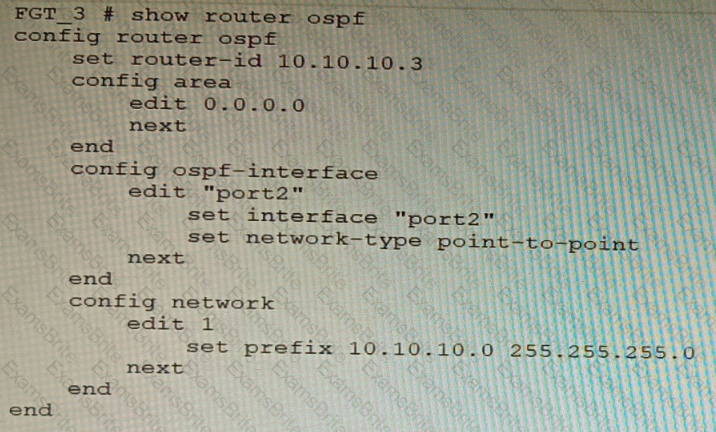
You are operating an internal network with multiple OSPF routers on the same LAN segment. FGT_3 needs to be added to the OSPF network and has the configuration shown in the exhibit. FGT_3 is not establishing any OSPF connection.
What needs to be changed to the configuration to make sure FGT_3 will establish OSPF neighbors without affecting the DR/BDR election?
A)
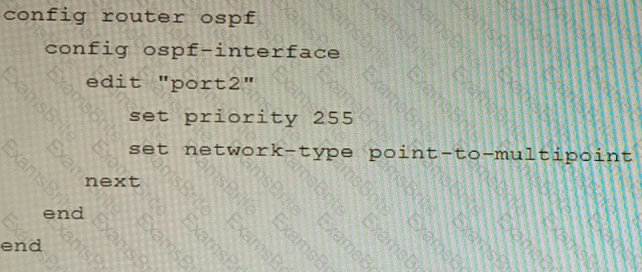
B)
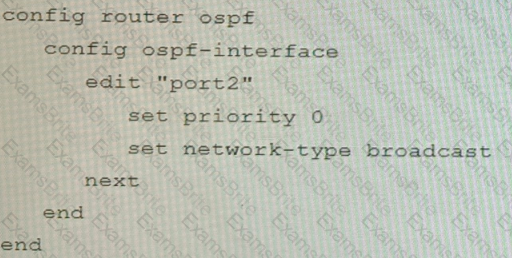
C)
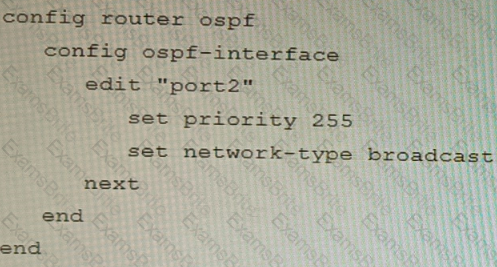
D)

Refer to the exhibits.
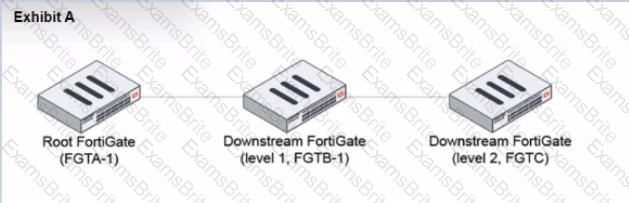
During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
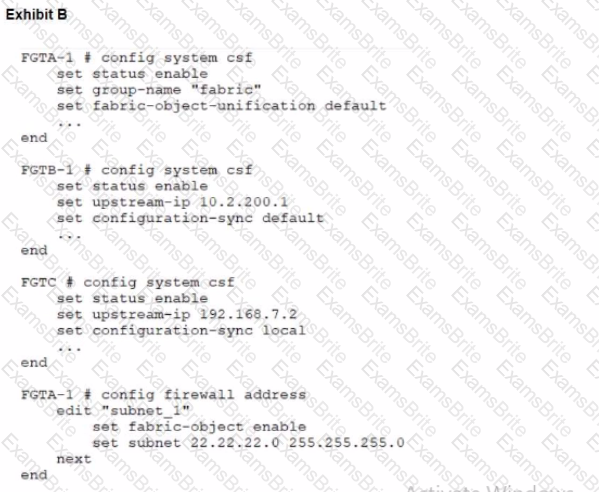
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
Refer to the exhibit showing a firewall policy configuration.
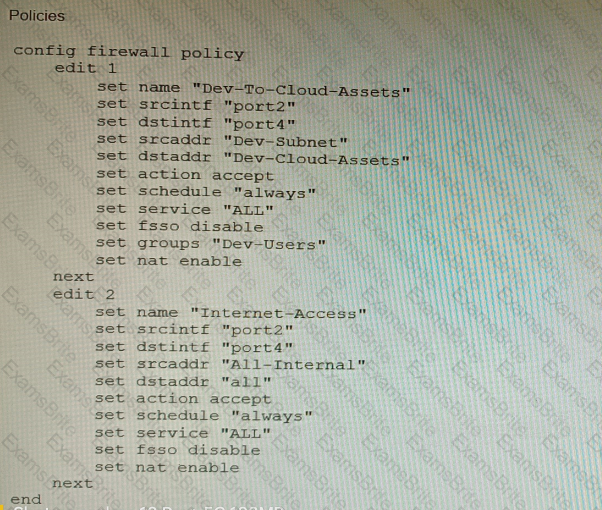
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1.
What change does the administrator need to make?

An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
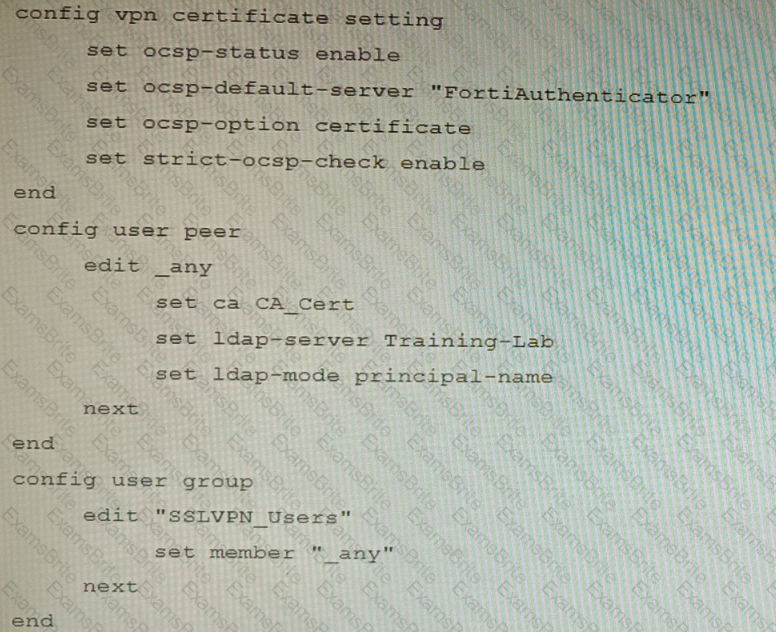
Based on this configuration, which two statements are true? (Choose two.)
You are deploying a FortiExtender (FEX) on a FortiGate-60F. The FEX will be managed by the FortiGate. You anticipate high utilization. The requirement is to minimize the overhead on the device for WAN traffic.
Which action achieves the requirement in this scenario?
Refer to the exhibit of a FortiNAC configuration.
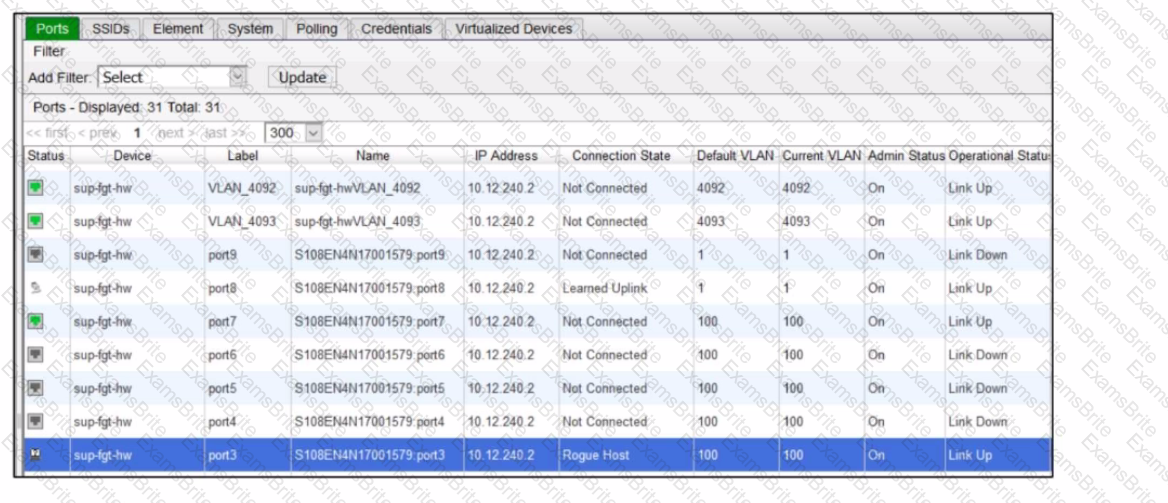
In this scenario, which two statements are correct? (Choose two.)
Refer to the exhibits.
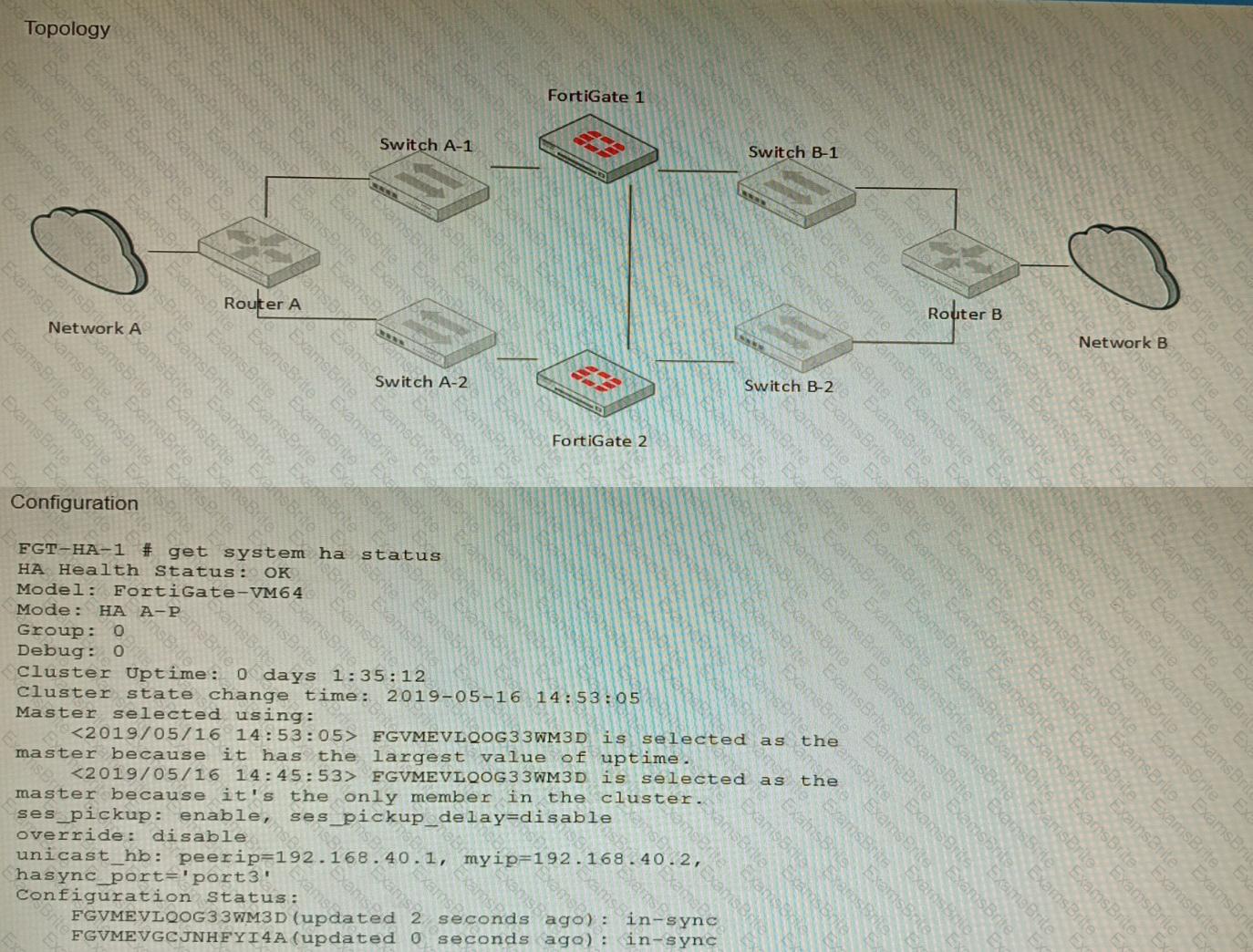
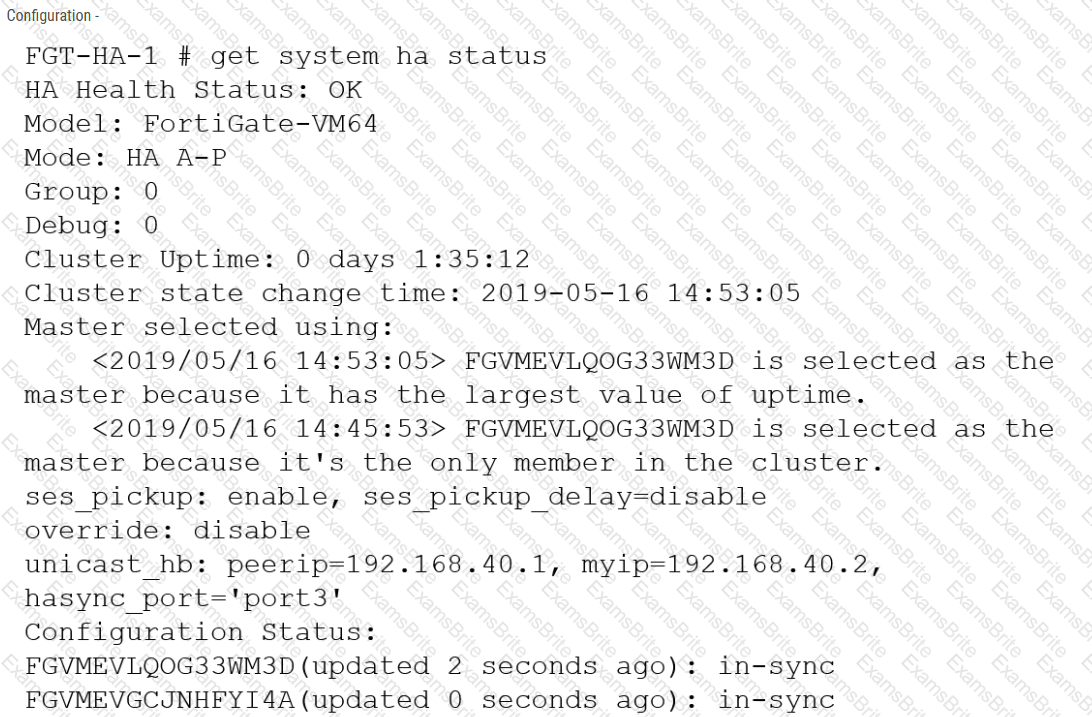
The exhibits show a FortiGate network topology and the output of the status of high availability on the FortiGate.
Given this information, which statement is correct?
Refer to the exhibit showing a FortiView monitor screen.
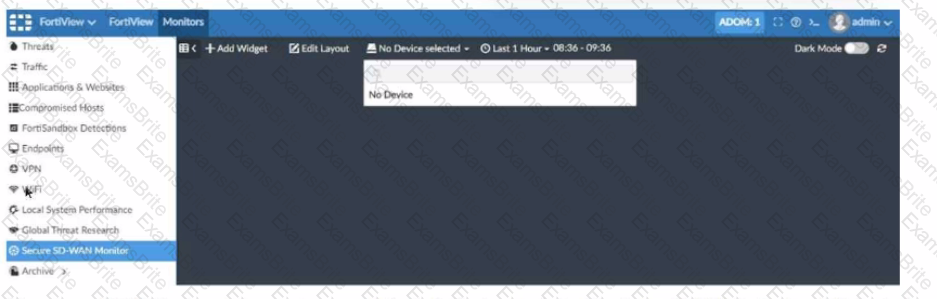
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
Refer to the exhibits.
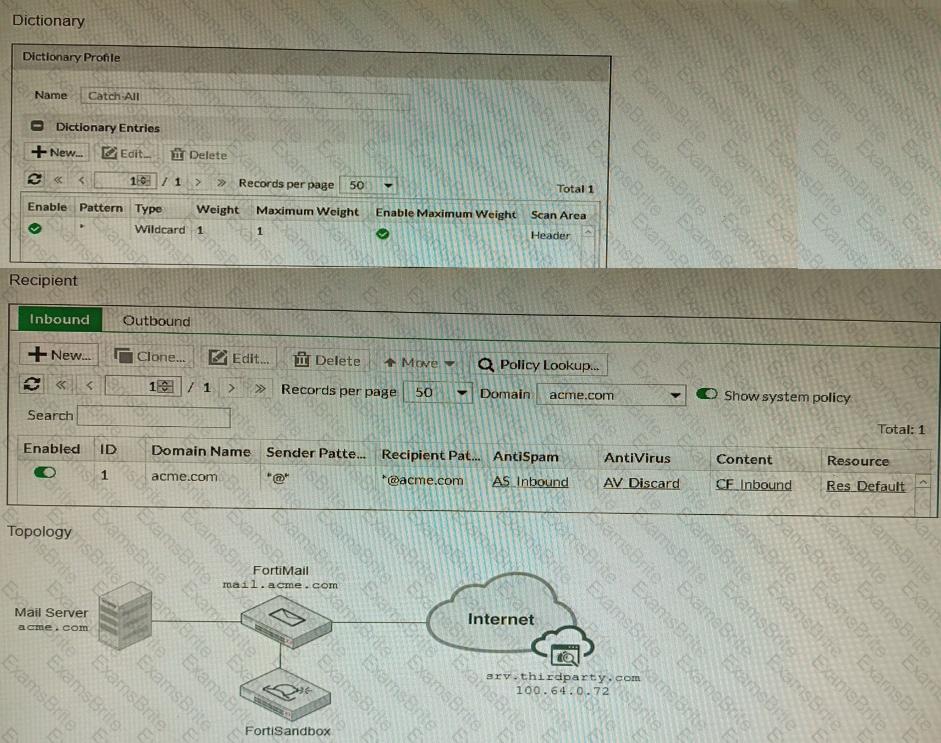
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
Refer to the exhibits.
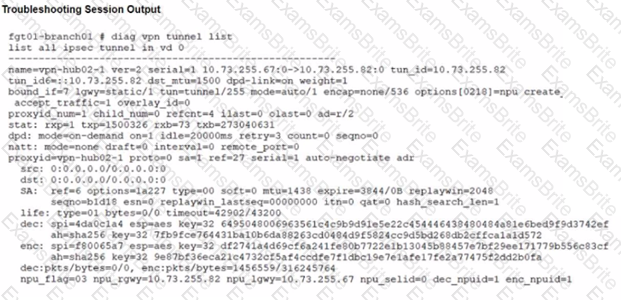
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.
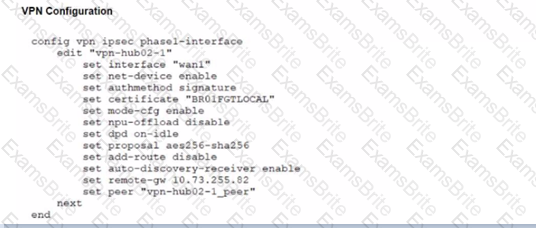
Which configuration parameters will restore VPN connectivity based on the diagnostic output?
You are running a diagnose command continuously as traffic flows through a platform with NP6 and you obtain the following output:
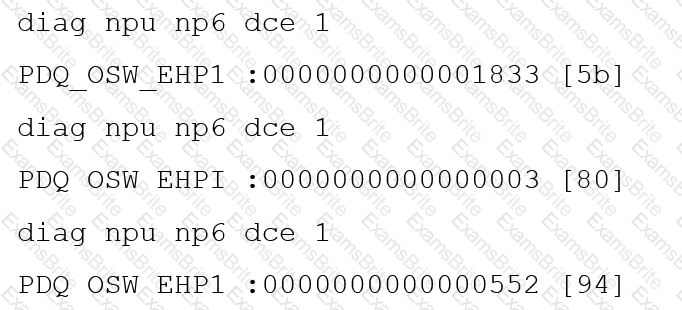
Given the information shown in the output, which two statements are true? (Choose two.)
Refer to the exhibit.
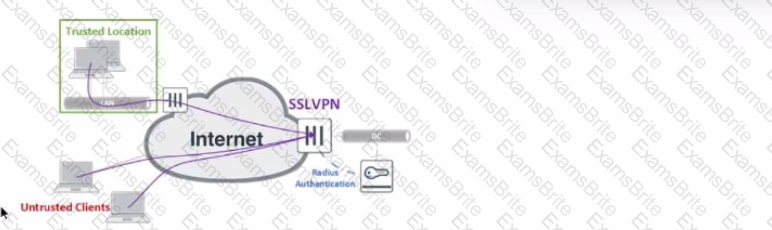
The exhibit shows the topology a customer wants to implement using a flexible authentication scheme. Users connecting from trusted remote locations are authenticated using only their username/password when connecting to the SSLVPN FortiGate in the data center.
When connecting from the Untrusted Clients, users must authenticate using 2-factor authentication.
In this scenario, which RADIUS attribute can be used as a RADIUS policy selector on the FortiAuthenticator to accomplish this goal?
Refer to the exhibits.
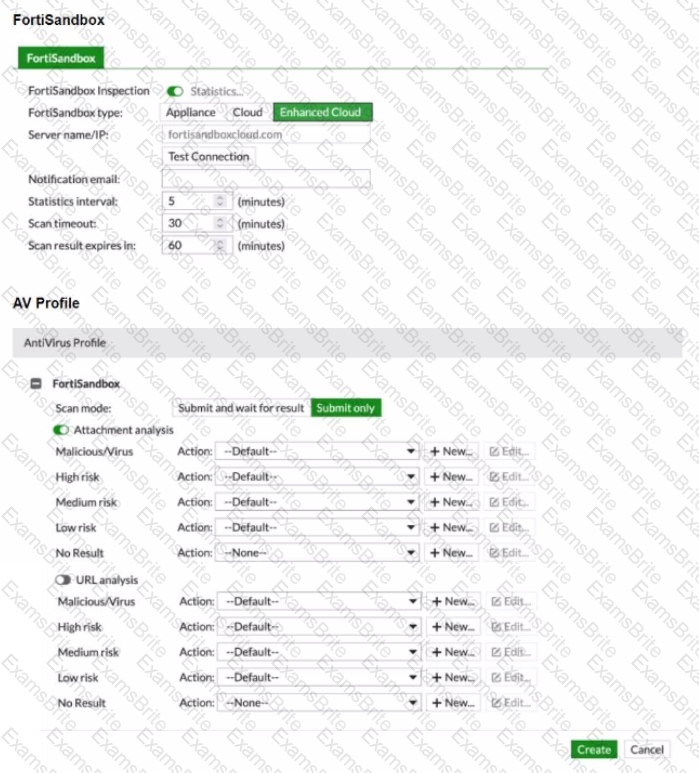
You must integrate a FortiMail and FortiSandbox Enhanced Cloud solution for a customer who is concerned about the e-mails being delayed for too long.
According to the configuration shown in the exhibits, which would be an expected behavior?
Refer to the exhibit, which shows a multi-region SD-WAN architecture.
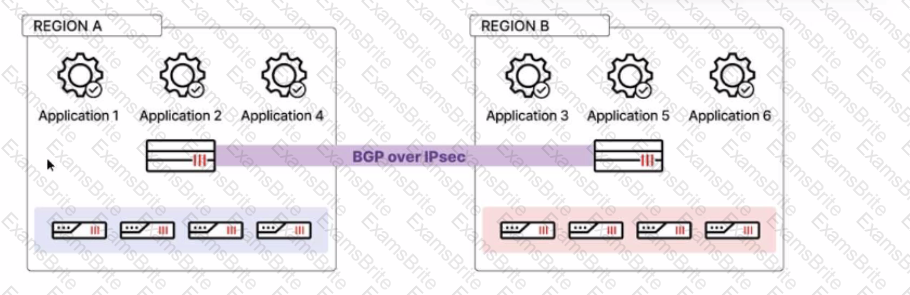
Given this scenario, which two statements are true? (Choose two.)
Refer to the exhibit, which shows diagnostic output.

A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
Refer to the exhibit.

A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
Refer to the exhibit showing the history logs from a FortiMail device.
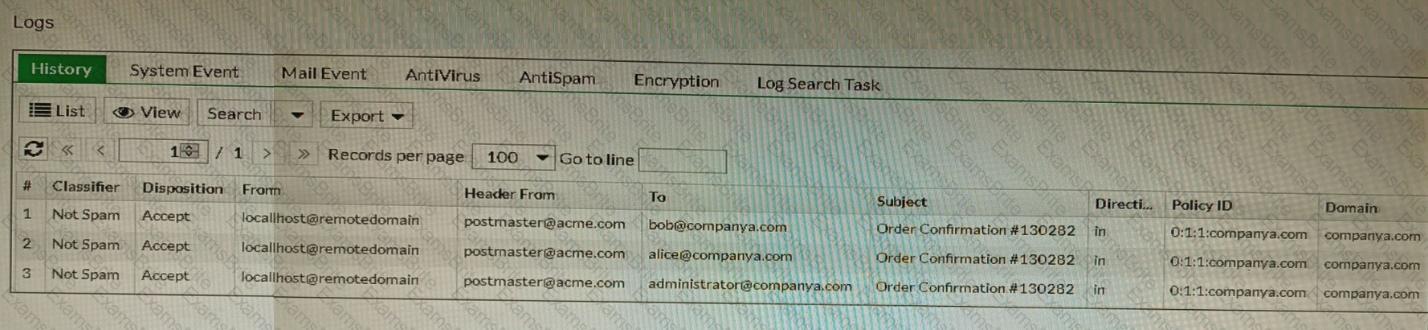
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
Refer to the exhibit showing FortiGate configurations
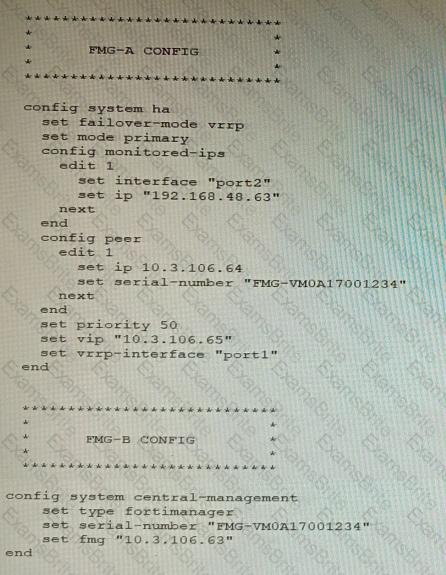
FortiManager VM high availability (HA) is not functioning as expected after being added to an existing deployment.
The administrator finds that VRRP HA mode is selected, but primary and secondary roles are greyed out in the GUI The managed devices never show online when FMG-B becomes primary, but they will show online whenever the FMG-A becomes primary.
What change will correct HA functionality in this scenario?
A customer has FortiAP devices in three branch offices managed from a FortiGate in the HQ. Each FortiAP is connected to a dedicated management VLAN.
The customer wants the users connected to the FortiAP SSIDs to use the branch local internet connection, but each branch uses a different VLAN ID for the bridge. HQ users travel to different branches and connect to the same SSID.
Which configuration option will solve this requirement?
A FortiGate deployment contains the following configuration:
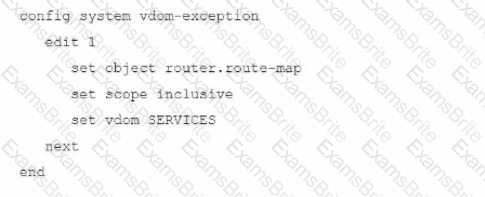
What is the result of this configuration?
You have configured a Site-to-Site IPsec VPN tunnel between a FortiGate and a third-party device but notice that one of the error counters on the tunnel interface keeps increasing.

Which two configuration options can resolve this problem? (Choose two.)
A FortiGate must be configured to accept VoIP traffic which will include session initiation protocol (SIP) traffic. Which statement about the VoIP configuration options is correct?
A customer is operating a FortiWeb cluster in a high volume active-active HA group consisting of eight FortiWeb appliances. One of the secondary members is handling traffic for one specific VIP.
What will happen with the traffic if that secondary FortiWeb appliance fails?