
Fortinet NSE 6 - FortiNAC 7.2
Last Update Mar 1, 2026
Total Questions : 57
We are offering FREE NSE6_FNC-7.2 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE6_FNC-7.2 free exam questions and then go for complete pool of Fortinet NSE 6 - FortiNAC 7.2 test questions that will help you more.



Where do you look to determine which network access policy, if any is being applied to a particular host?
Which command line shell and scripting language does FortiNAC use for WinRM?
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously appeared on a port that is a member of the Forced Registration port group?
View the command and output shown in the exhibit.
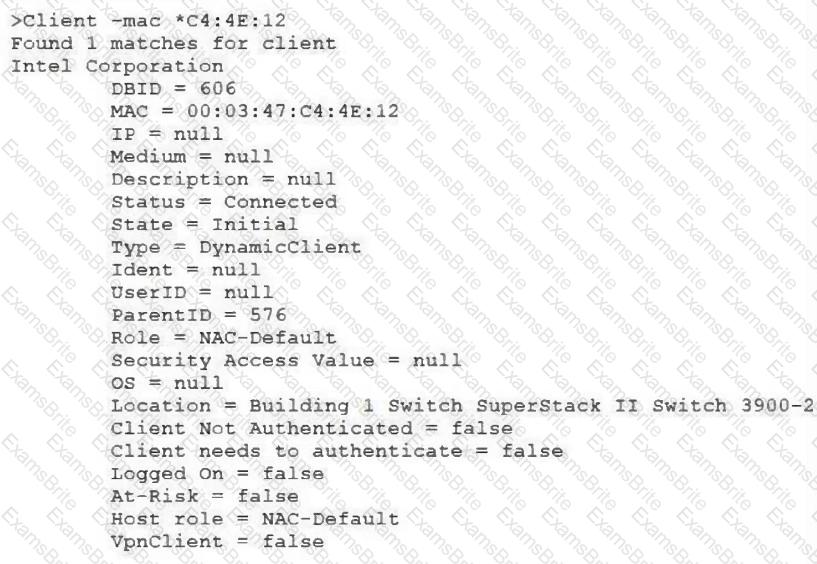
What is the current state of this host?
Two FortiNAC devices have been configured in an HA configuration. After five failed heartbeats between the primary device and secondary device, the primary device fail to ping the designated gateway. What happens next?
While troubleshooting a network connectivity issue, an administrator determines that a device was being automatically provisioned to an incorrect VLAN.
Where would the administrator look to determine when and why FortiNAC made the network access change?
Refer to the exhibit.
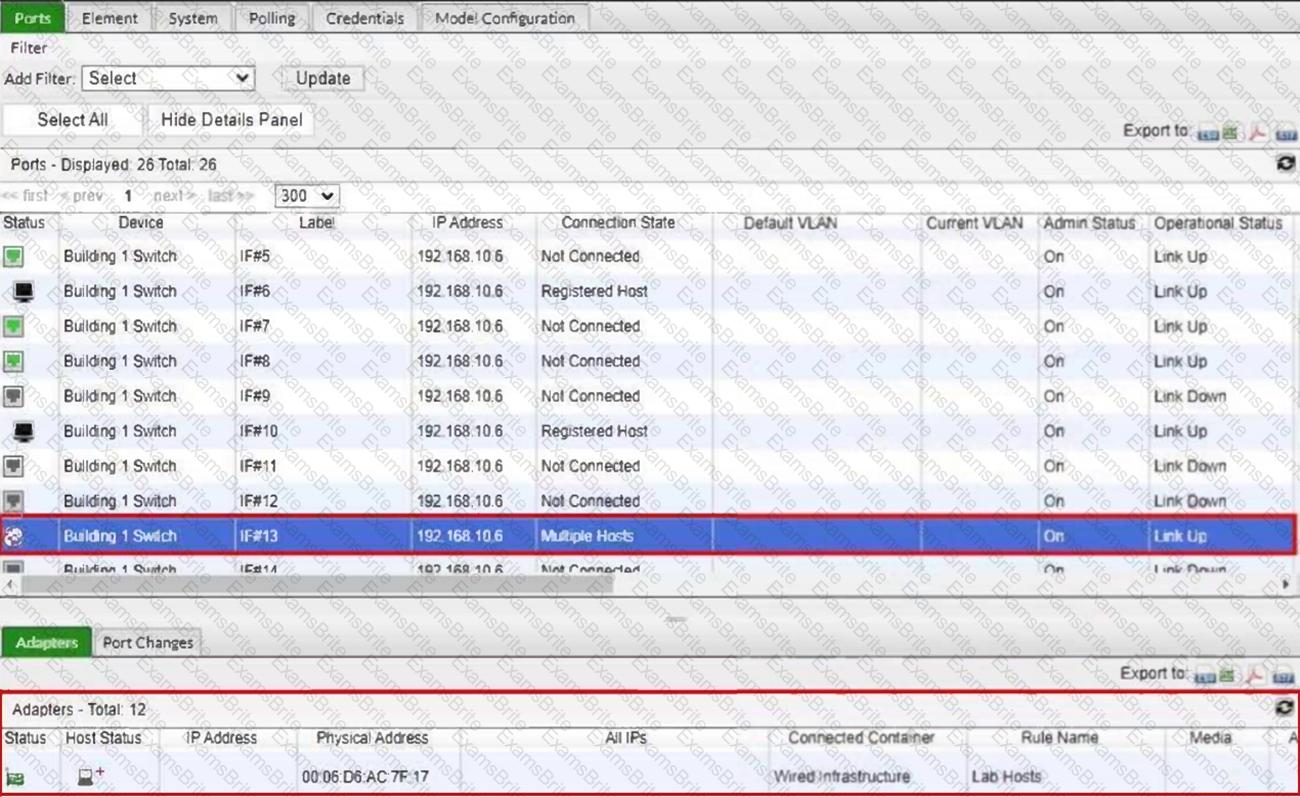
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
By default, if after a successful Layer 2 poll, more than 20 endpoints are seen connected on a single switch port simultaneously, what happens to the port?
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Which three of the following are components of a security rule? (Choose three.)
Which connecting endpoints are evaluated against all enabled device profiling rules?
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
Which system group will force at-risk hosts into the quarantine network, based on point of connection?