
FCSS - FortiSASE 25 Administrator
Last Update Mar 1, 2026
Total Questions : 53
We are offering FREE FCSS_SASE_AD-25 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare FCSS_SASE_AD-25 free exam questions and then go for complete pool of FCSS - FortiSASE 25 Administrator test questions that will help you more.



Which FortiSASE feature ensures least-privileged user access to corporate applications that are protected by an on-premises FortiGate device?
Which secure internet access (SIA) use case minimizes individual endpoint configuration?
Which two advantages does FortiSASE bring to businesses with microbranch offices that have FortiAP deployed for unmanaged devices? (Choose two.)
Refer to the exhibit.
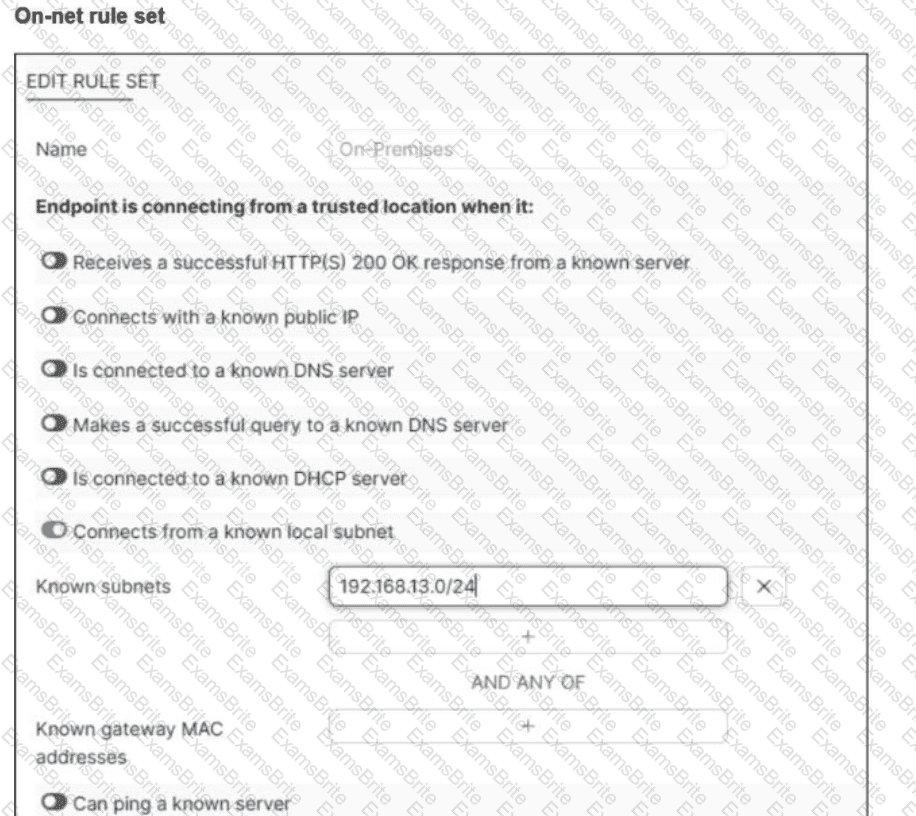
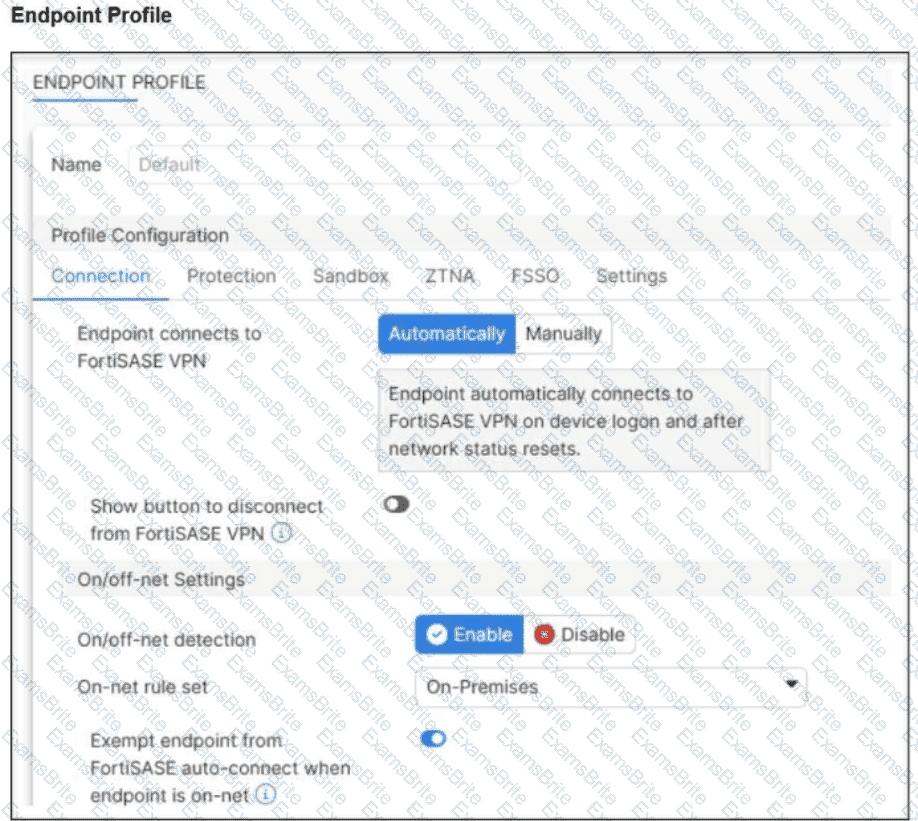
An endpoint is assigned an IP address of 192.168.13.101/24.
Which action will be run on the endpoint?
Refer to the exhibits.
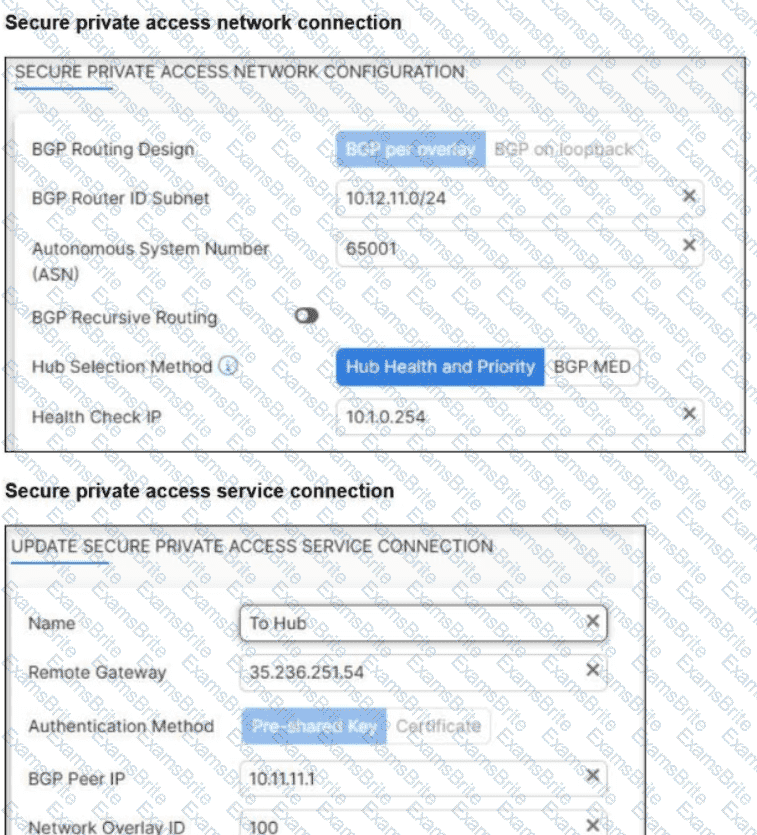
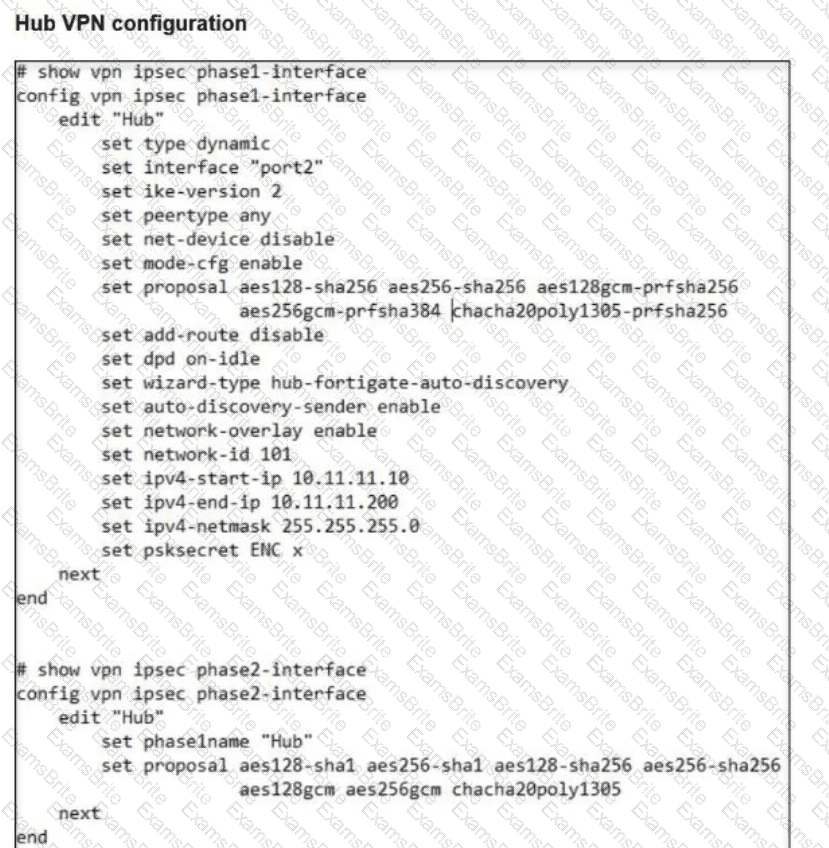
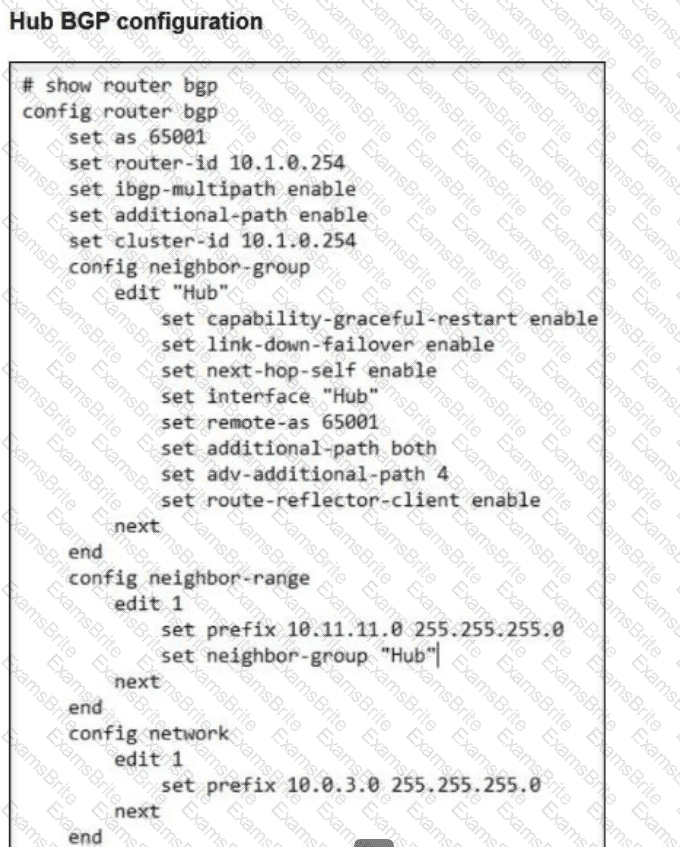

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub.
The VPN tunnel does not establish.
Which configuration needs to be modified to bring the tunnel up?
An administrator must restrict endpoints from certain countries from connecting to FortiSASE.
Which configuration can achieve this?
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
Refer to the exhibits.
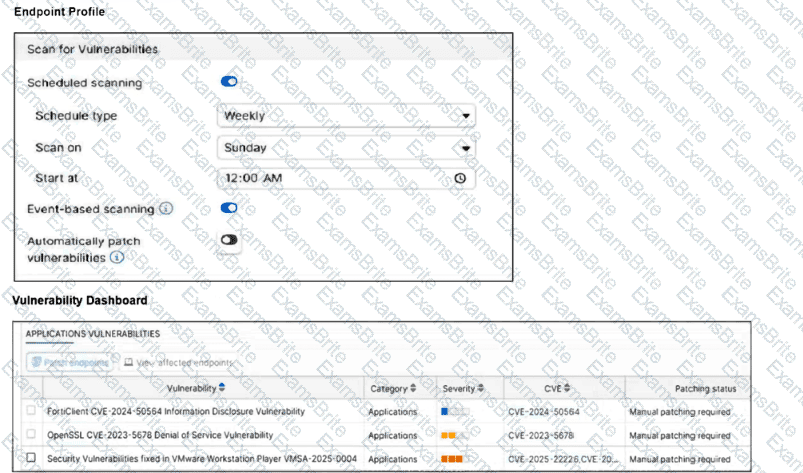
How will the application vulnerabilities be patched, based on the exhibits provided?
Which authentication method overrides any other previously configured user authentication on FortiSASE?
A customer wants to ensure secure access for private applications for their users by replacing their VPN.
Which two SASE technologies can you use to accomplish this task? (Choose two.)
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Refer to the exhibits.
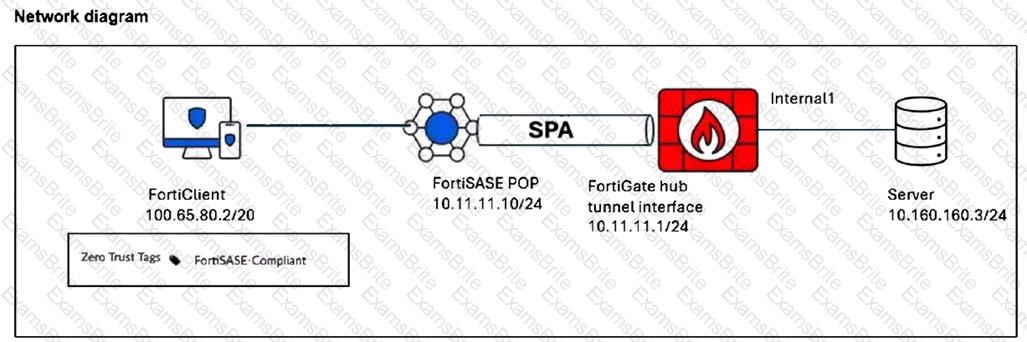
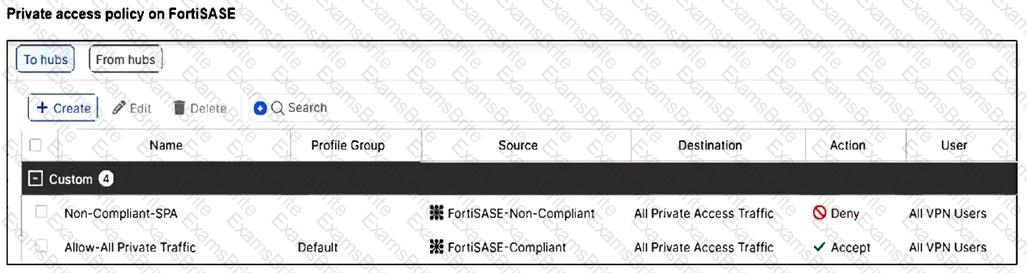
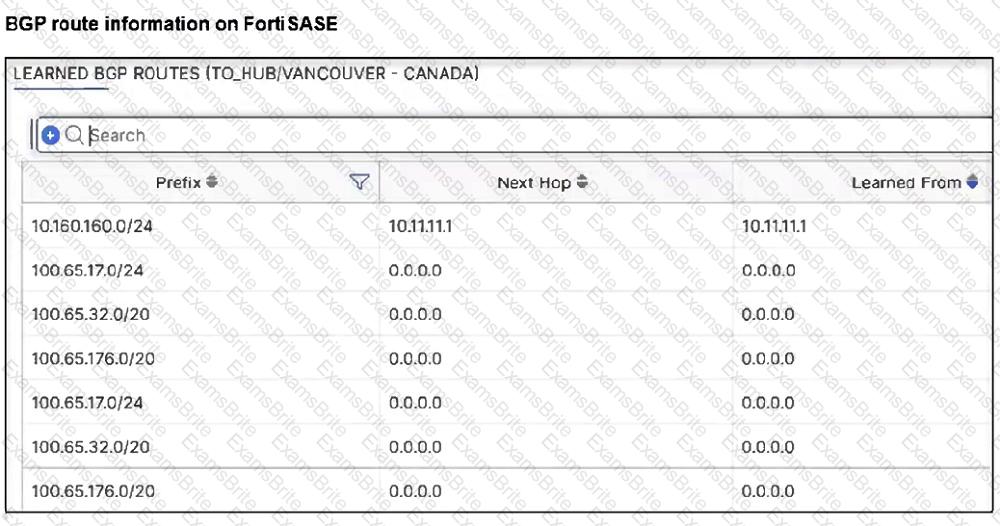
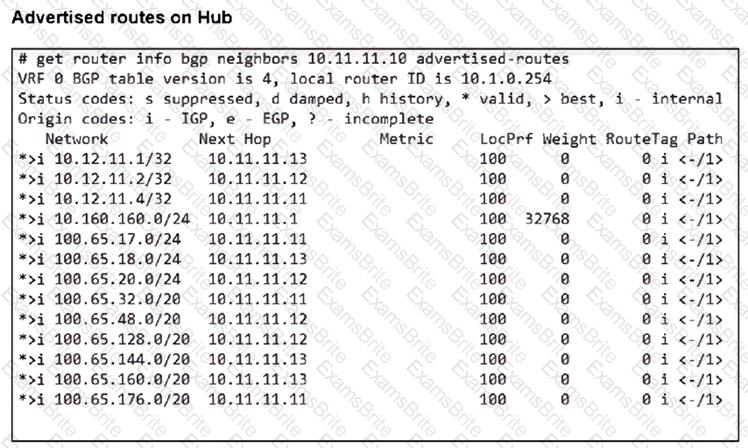
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub.
Based on the exhibits, what is the reason for the access failure?
How do security profile group objects behave when central management is enabled on FortiSASE?
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?