
Fortinet NSE 6 - Network Security 7.6 Support Engineer
Last Update Feb 28, 2026
Total Questions : 95
We are offering FREE FCSS_NST_SE-7.6 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare FCSS_NST_SE-7.6 free exam questions and then go for complete pool of Fortinet NSE 6 - Network Security 7.6 Support Engineer test questions that will help you more.



Refer to the exhibits.
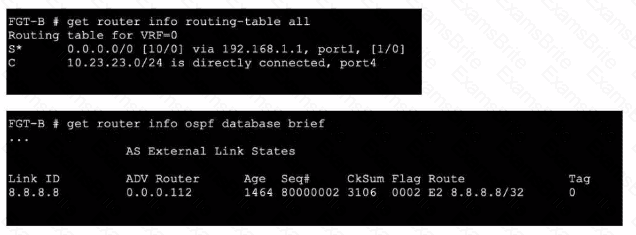
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
Refer to the exhibit, which contains partial output from an IKE real-time debug.

The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change the administrator make to the local gateway to resolve the phase 1 negotiation error?
Refer to the exhibit, which shows the partial output of a real-time OSPF debug.
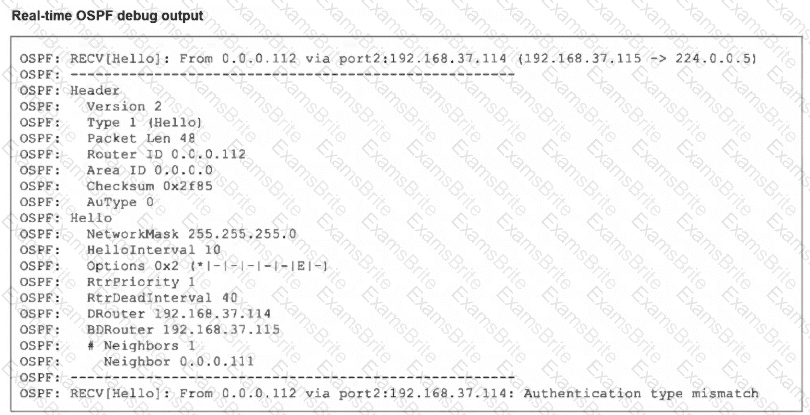
Why are the two FortiGate devices unable to form an adjacency?
Refer to the exhibit.
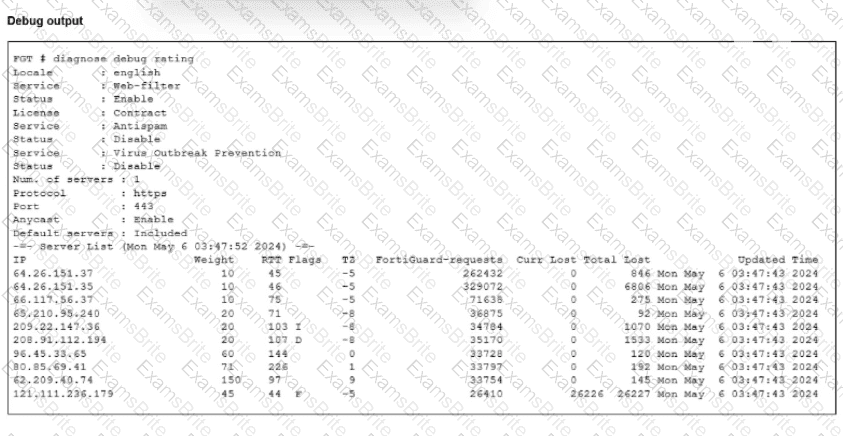
The administrator did not override the FortiGuard FODN or IP address in the FortiGate configuration
Which IP address did FortiGate get when resolving the servicem,fortiguard.net name?
Refer to the exhibit, which shows the modified output of the routing kernel.
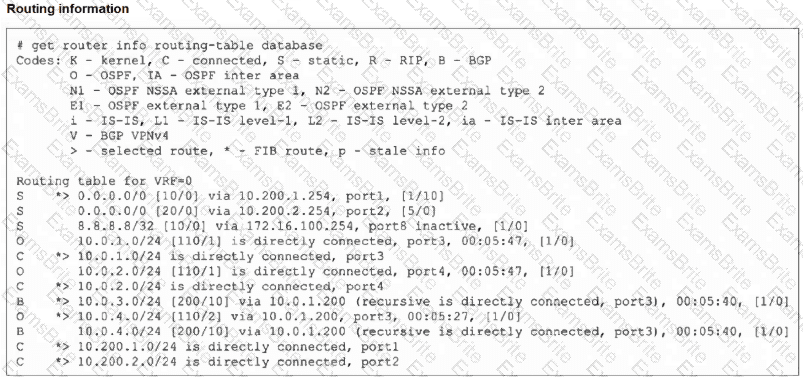
Which statement is true?
Refer to the exhibit showing a debug output.
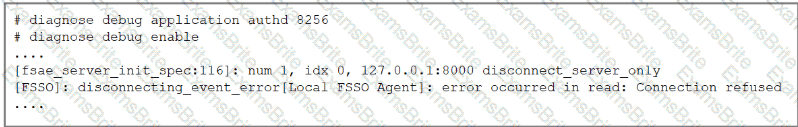
An administrator deployed FSSO in DC Agent Mode but FSSO is failing on FortiGate. Pinging FortiGate from where the collector agent is deployed is successful.
The administrator then produces the debug output shown in the exhibit.
What could be causing this error message?
Refer to the exhibit.
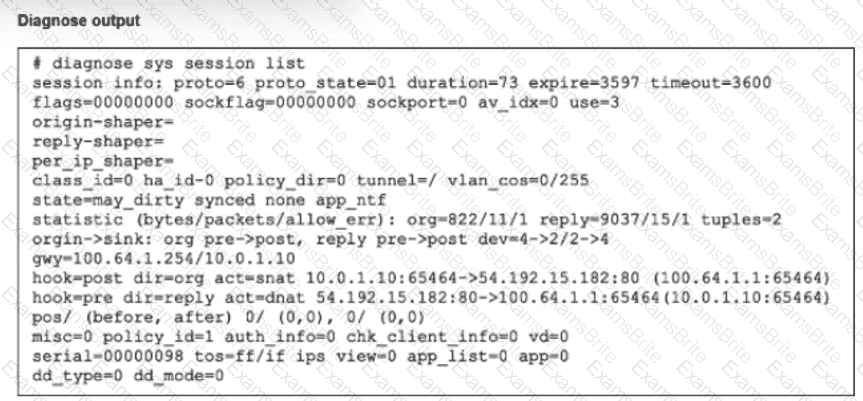
The output of diagnose sys session list command is shown.
If the HA ID for the primary device is 9, what happens if the primary fails and the secondary becomes the primary?
What is an accurate description of LDAP authentication using the regular bind type?
Exhibit.
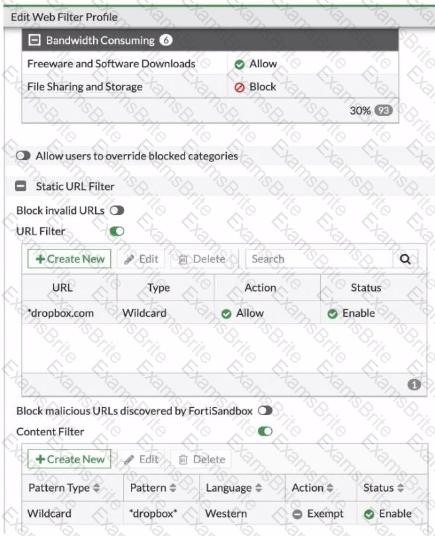
Refer to the exhibit, which shows a partial web fillet profile configuration.
Which action does FortiGate lake if a user attempts to access www. dropbox. com, which is categorized as File Sharing and Storage?
Refer to the exhibit.
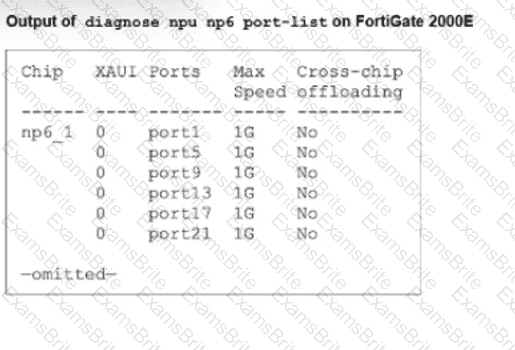
A partial output of diagnose npu up6 port-list on FortiGate 2000E is shown.
An administrator is unable to analyze traffic flowing between port1 and port17 using the diagnose sniffer command.
Which two commands allow the administrator to view the traffic? (Choose two.)
A)
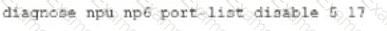
B)
C)

D)

Refer to the exhibit, which shows the output of get router info bgp summary.
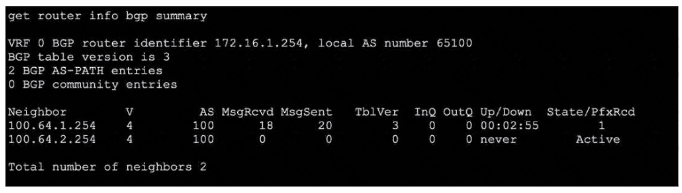
Which two statements are true? (Choose two.)
Refer to the exhibit, which shows a partial output of the fssod daemon real-time debug command.

What two conclusions can you draw from the output? (Choose two.)
Refer to the exhibit, which shows a session entry.
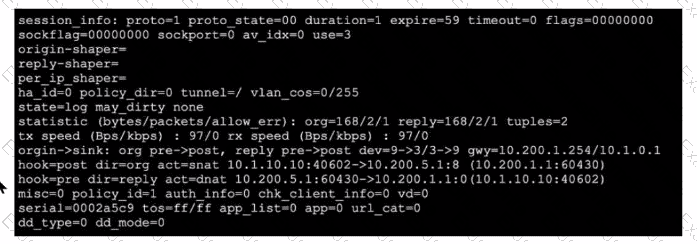
Which statement about this session is true?
While troubleshooting a FortiGate web filter issue, users report that they cannot access any websites, even though those sites are not explicitly blocked by any web filter profiles that are applied to firewall policies.
What are the three most likely reasons for this behavior? (Choose three answers)
Refer to the exhibit.
Partial output of diagnose sys session stat command is shown.
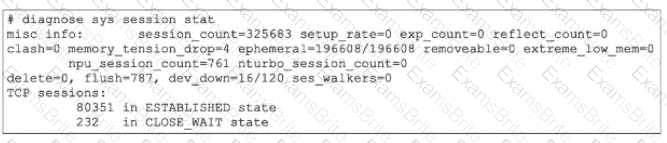
An administrator has noticed unusual behavior from FortiGate. It appears that sessions are randomly removed. Which two reasons could explain this? (Choose two.)
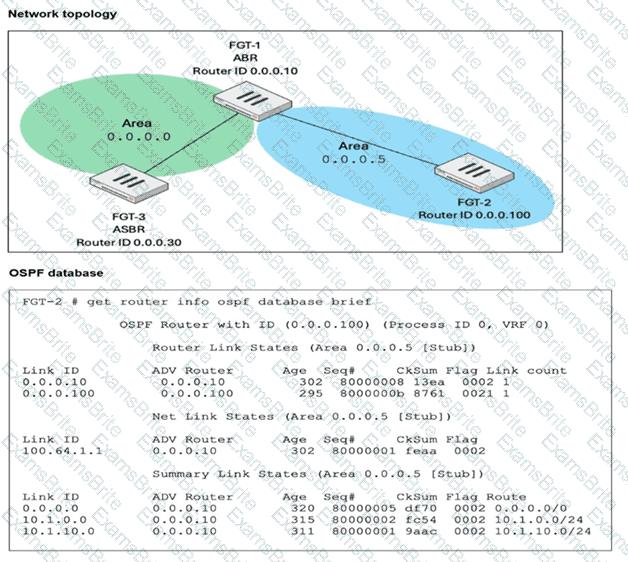
Refer to the exhibit, which shows the output of the command get router info ospf neighbor.
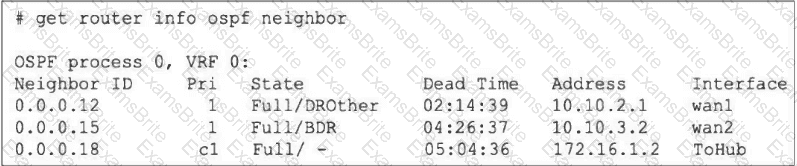
To what extent does FortiGate operate when looking at its OSPF neighbors? (Choose two.)
Refer to the exhibit, which shows a partial web filter profile configuration.
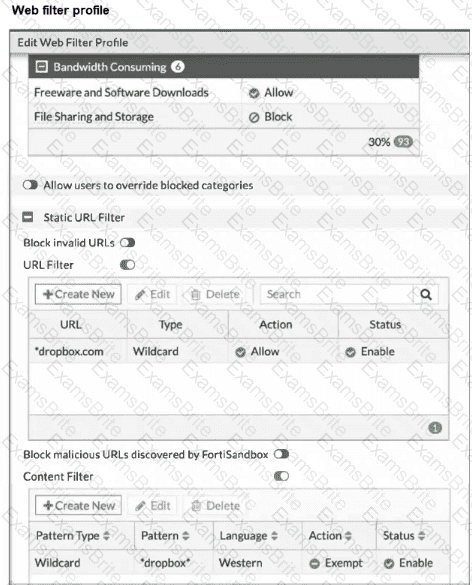
The URL www.dropbox.com is categorized as File Sharing and Storage.
Which action does FortiGate take if a user attempts to access www.dropbox.com?
Refer to the exhibit, which shows a partial output of the real-time LDAP debug.
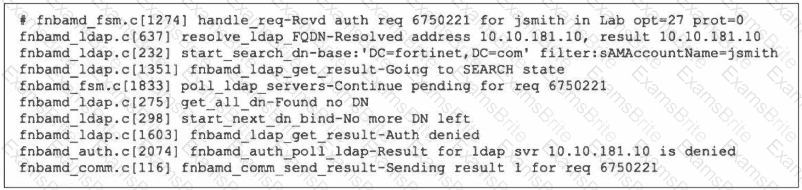
What two actions can the administrator take to resolve this issue? (Choose two.)
Exhibit 1.
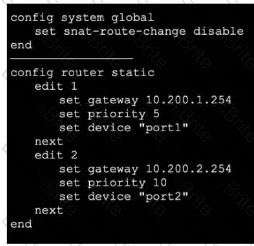
Exhibit 2.
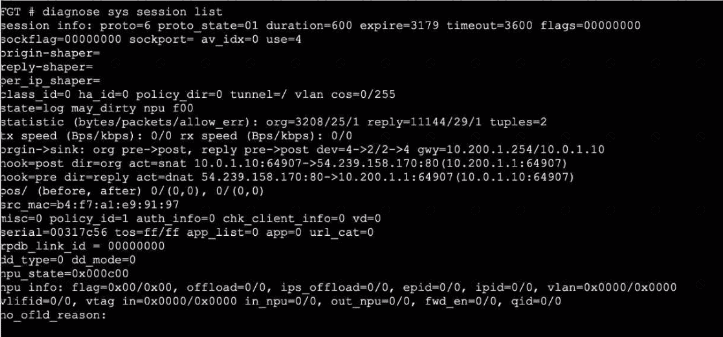
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
An administrator would like to lest session failover between the two service provider connections.
Which two changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
Exhibit.

Refer to the exhibit, which shows two entries that were generated in the FSSO collector agent logs.
What three conclusions can you draw from these log entries? {Choose three.)
Refer to the exhibit.
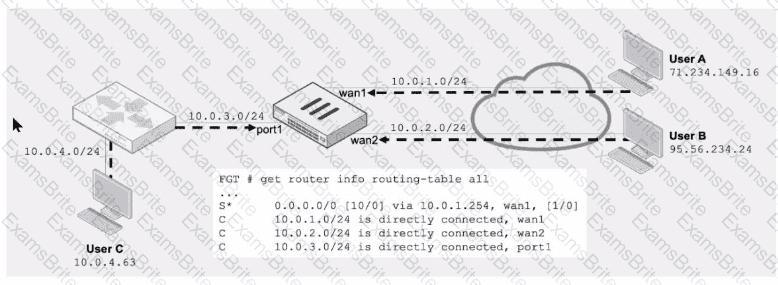
Assuming a default configuration, which three statements are true? (Choose three.)
Exhibit.
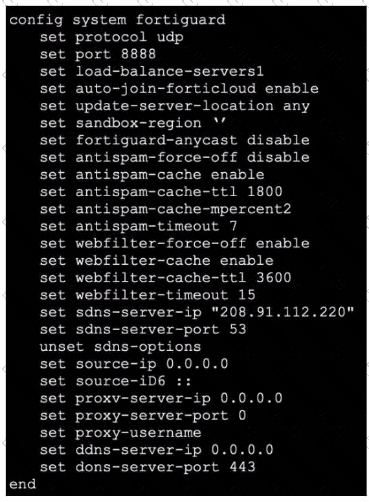
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator do to fix the issue?
Refer to the exhibit, which shows the port1 interface configuration on FortiGate and partial session information for ICMP traffic.
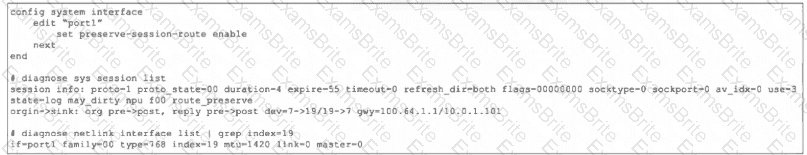
What happens to the session information if a routing change occurs that affects this session?
Refer to the exhibit.
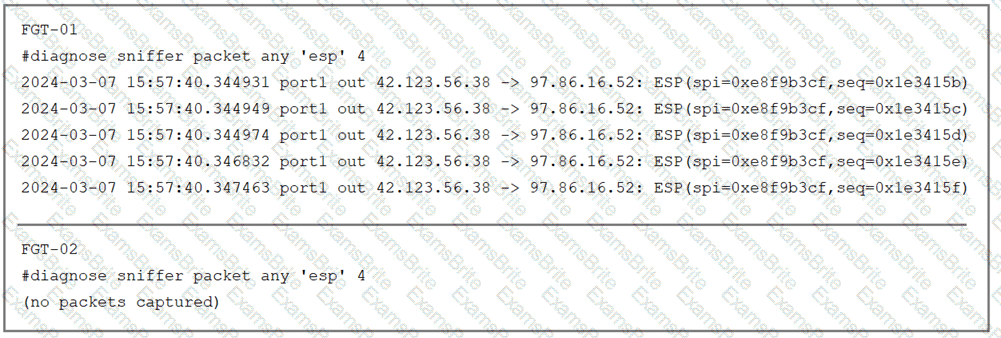
The sniffer log on two FortiGate devices are shown. Based on the information in the log, which two factors explain the output on FortiGate FGT-02? (Choose two answers)
Consider the scenario where the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate. Which two actions will FortiGate take when using the default settings for SSL certificate inspection? (Choose two answers)
Refer to the exhibit.
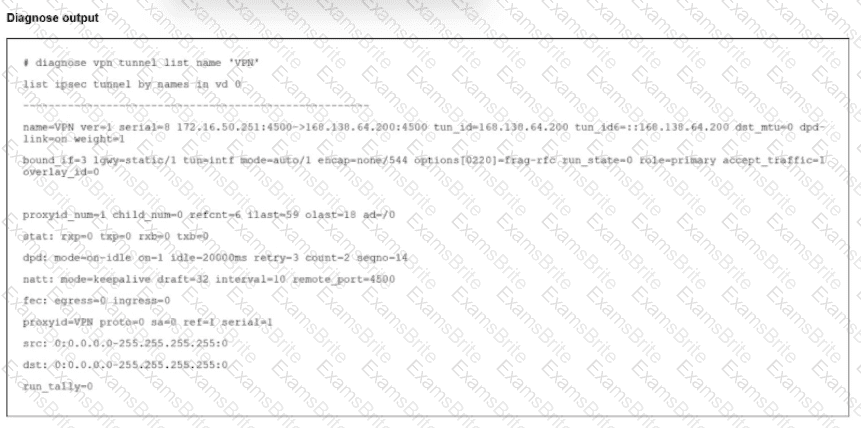
The output of the command diagnose vpn tunnels liar is shown.
Which two statements accurately describe the status of the tunnel? (Choose two.)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)