
FCP - FortiWeb 7.4 Administrator
Last Update Feb 28, 2026
Total Questions : 36
We are offering FREE FCP_FWB_AD-7.4 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare FCP_FWB_AD-7.4 free exam questions and then go for complete pool of FCP - FortiWeb 7.4 Administrator test questions that will help you more.



Refer to the exhibit.
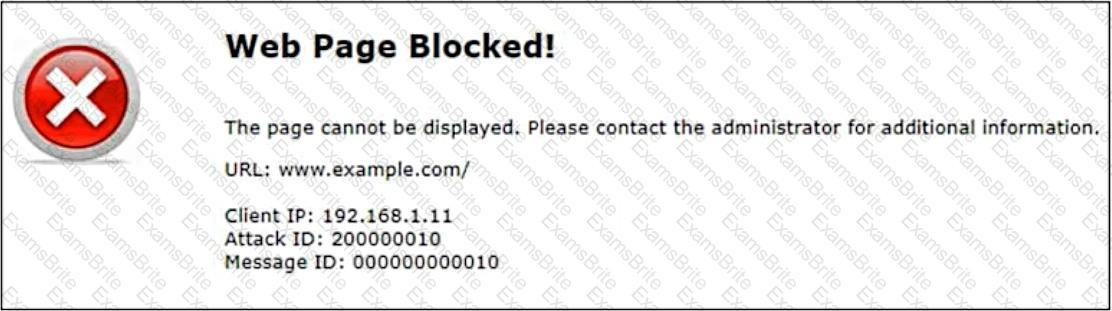
Attack ID20000010is brute force logins.
Which statement is accurate about the potential attack?
In SAML deployments, which server contains user authentication credentials (username/password)?
Which two objects are required to configure a server policy in reverse proxy mode without content routing? (Choose two.)
An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
Refer to the exhibit.
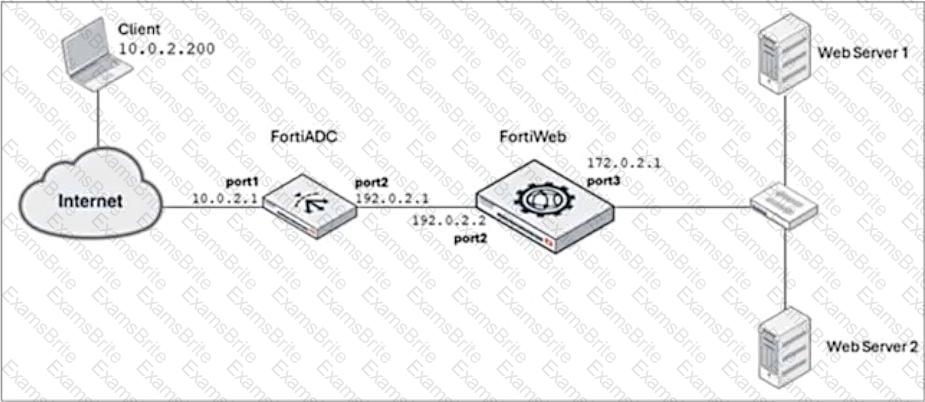
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the192.0.2.1source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
Refer to the exhibit.
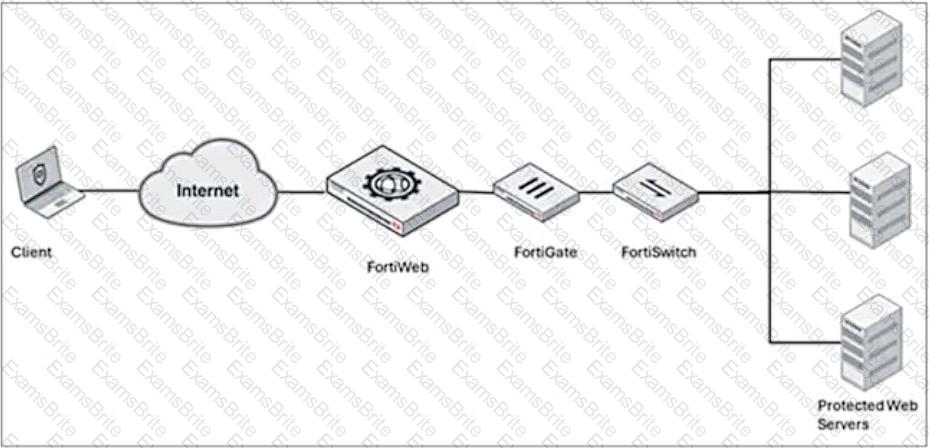
A FortiWeb device is deployed upstream of a device performing source network address translation (SNAT) or load balancing.
What configuration must you perform on FortiWeb to preserve the original IP address of the client?
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose three.)
Which high availability mode is commonly used to integrate with a traffic distributer like FortiADC?