
FCP - FortiGate 7.4 Administrator
Last Update Feb 28, 2026
Total Questions : 89
We are offering FREE FCP_FGT_AD-7.4 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare FCP_FGT_AD-7.4 free exam questions and then go for complete pool of FCP - FortiGate 7.4 Administrator test questions that will help you more.



An administrator must enable a DHCP server on one of the directly connected networks on FortiGate. However, the administrator is unable to complete the process on the GUI to enable the service on the interface.
In this scenario, what prevents the administrator from enabling DHCP service?
Which statement is correct regarding the use of application control for inspecting web applications?
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
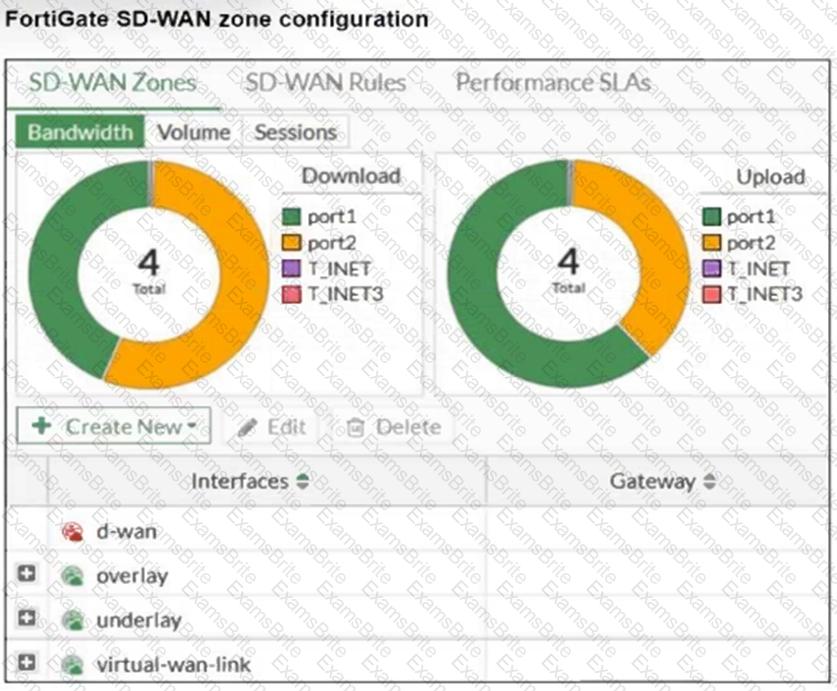
Based on the exhibit, which statement is true?
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors?
Refer to the exhibit.
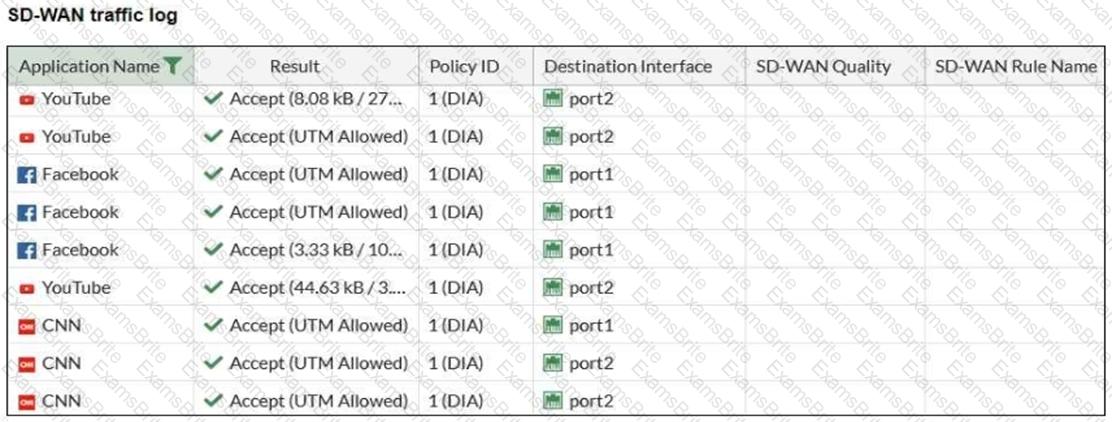
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
Refer to the exhibit.
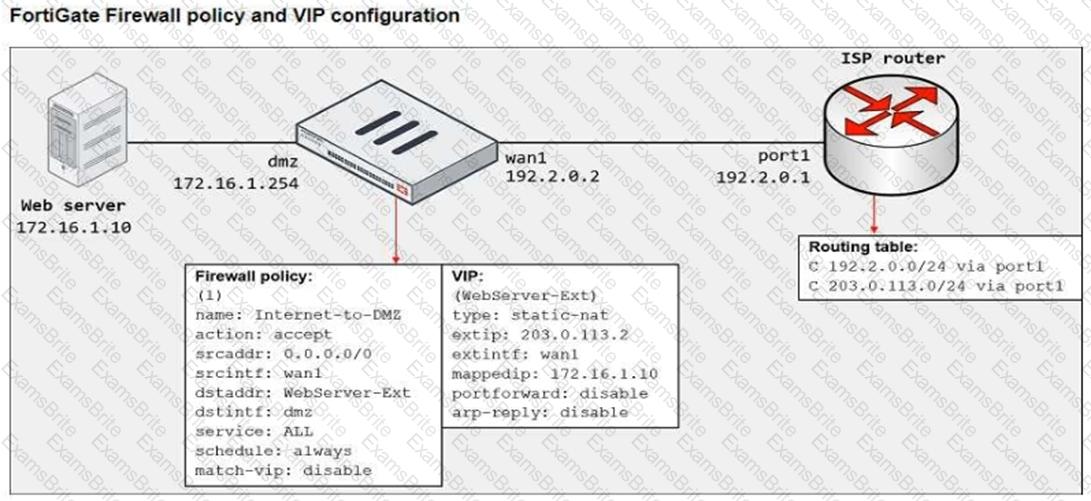
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
Refer to the exhibit.

The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.
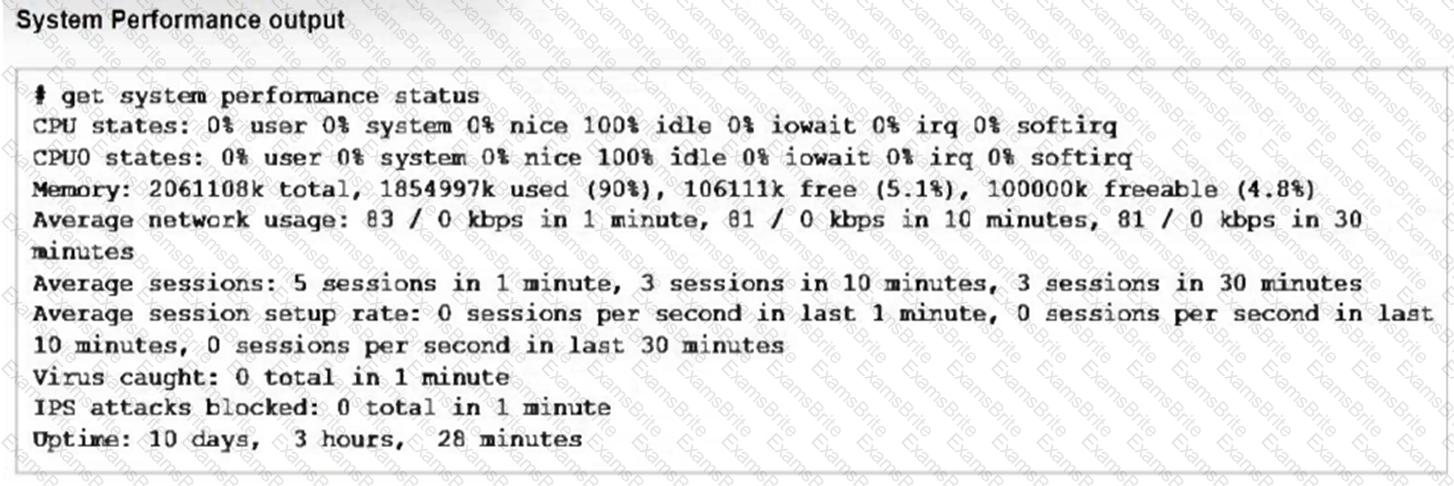
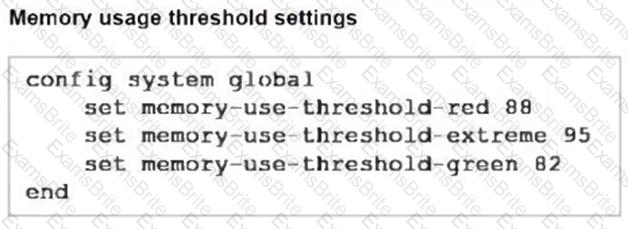
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
Refer to the exhibits.
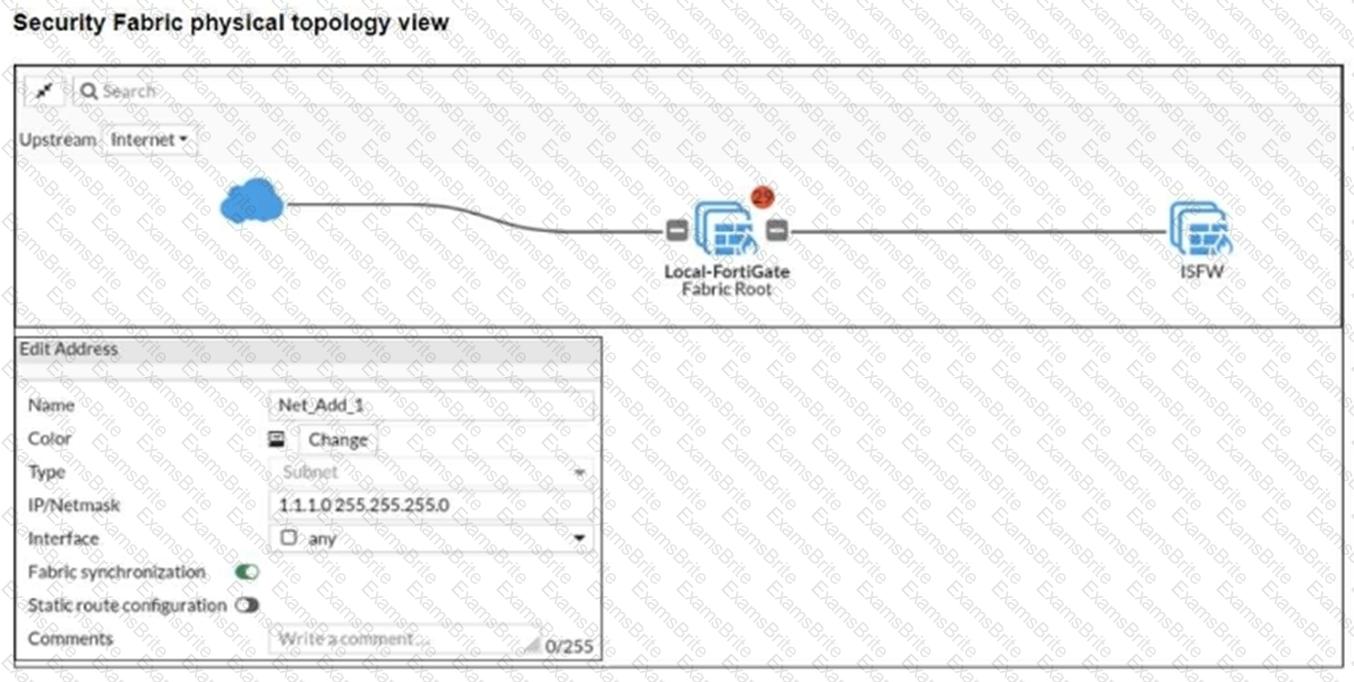
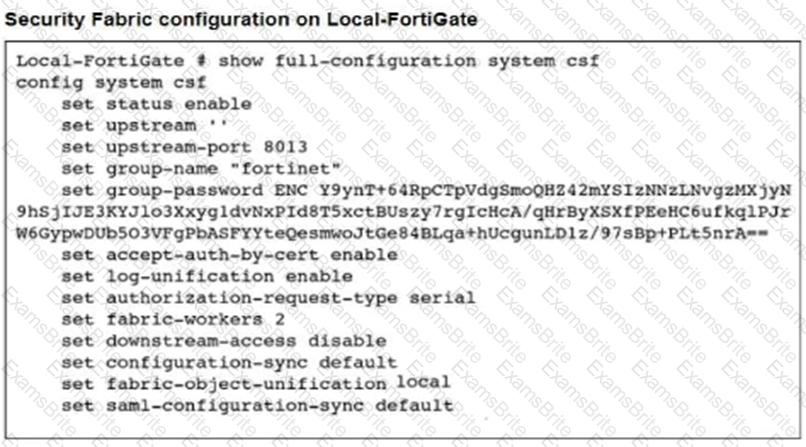
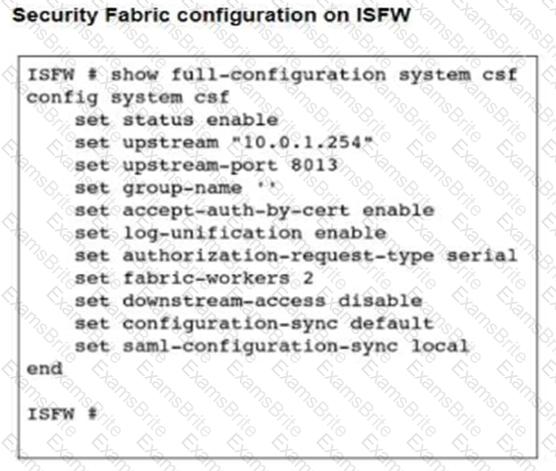
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
Refer to the exhibits.
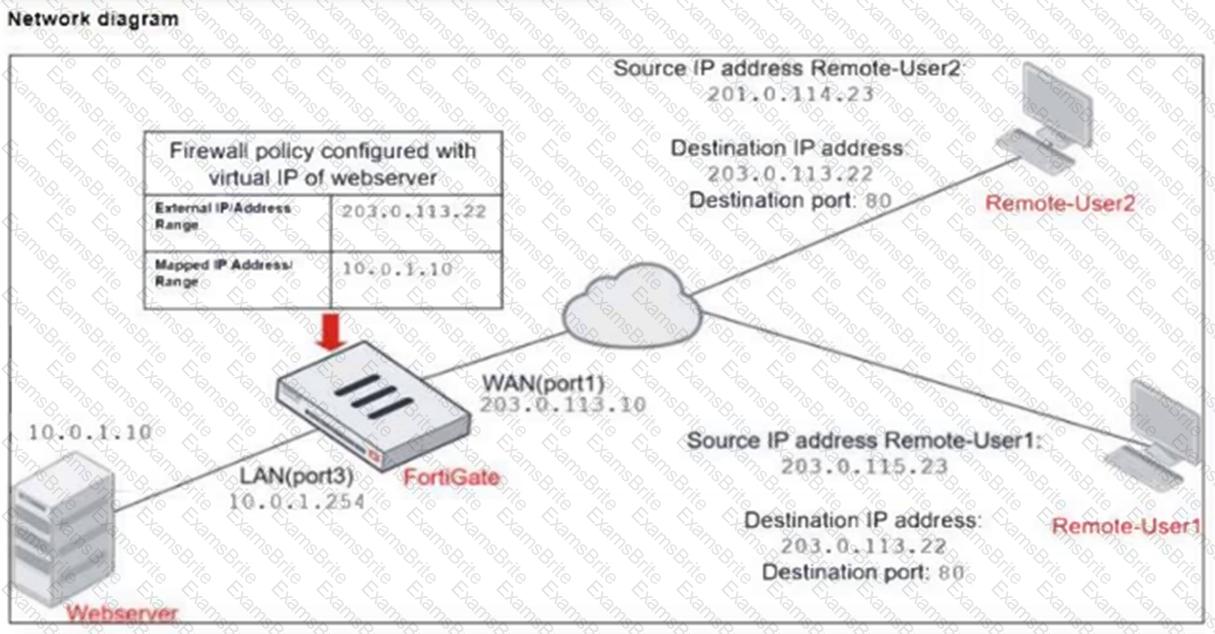
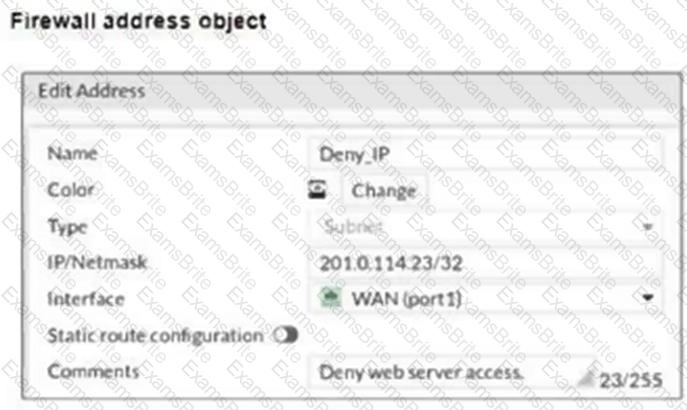
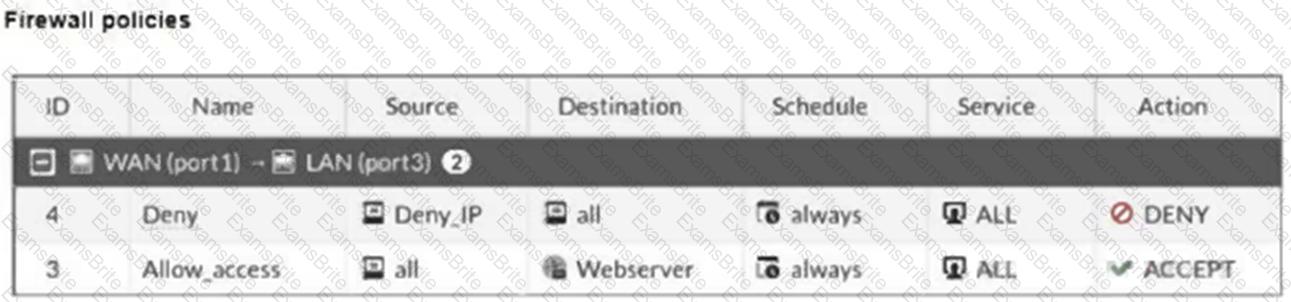
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors?
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is outbound traffic but no response from the peer.
Which DPD mode on FortiGate meets this requirement?
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
An administrator manages a FortiGate model that supports NTurbo.
How does NTurbo enhance performance for flow-based inspection?
Refer to the exhibit.
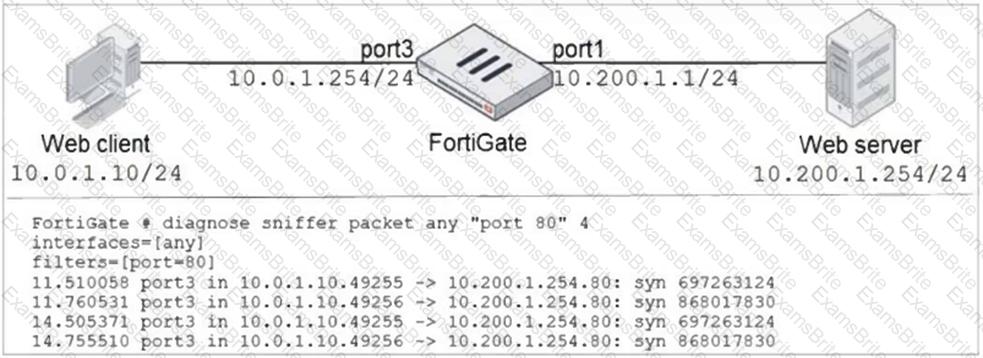
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Refer to the exhibit.
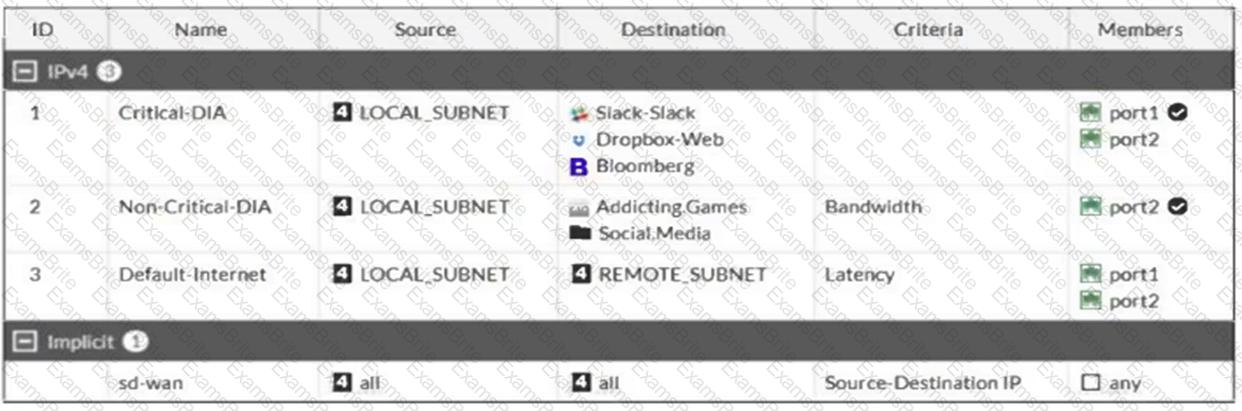
Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
Which inspection mode does FortiGate use for application profiles if it is configured as a profile-based next-generation firewall (NGFW)?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Refer to the exhibit.

The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
Refer to the exhibit showing a FortiGuard connection debug output.
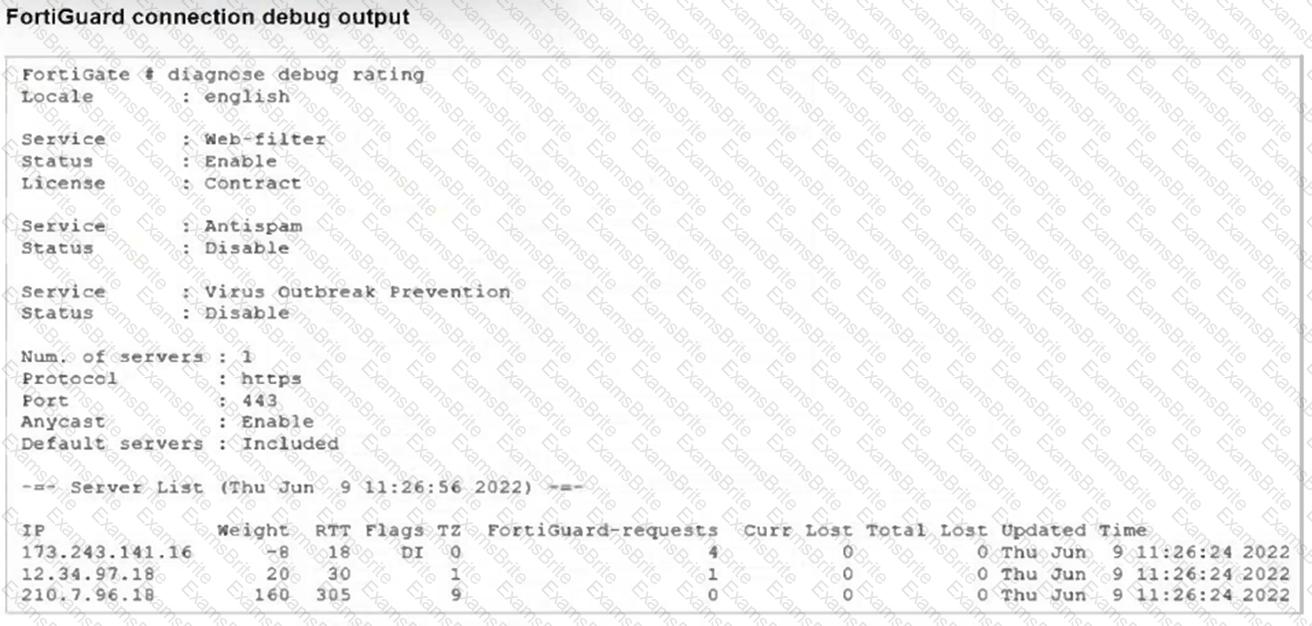
Based on the output, which two facts does the administrator know about the FortiGuard connection? (Choose two.)
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Refer to the exhibits.



The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
Refer to the exhibit.
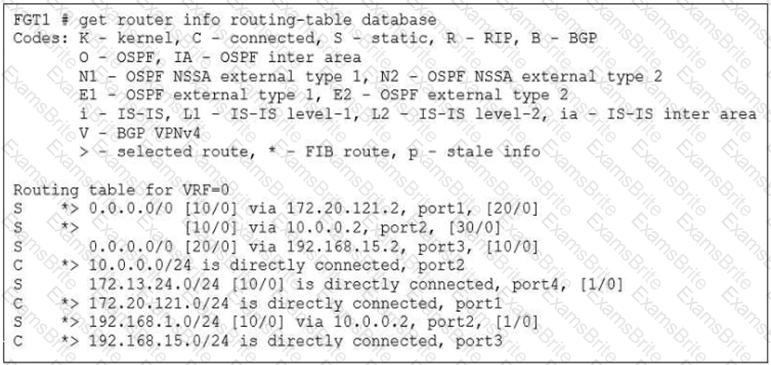
Based on the routing database shown in the exhibit which two conclusions can you make about the routes? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL inspection? (Choose two.)
Refer to the exhibit.

The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)
Refer to the exhibit, which shows the IPS sensor configuration.
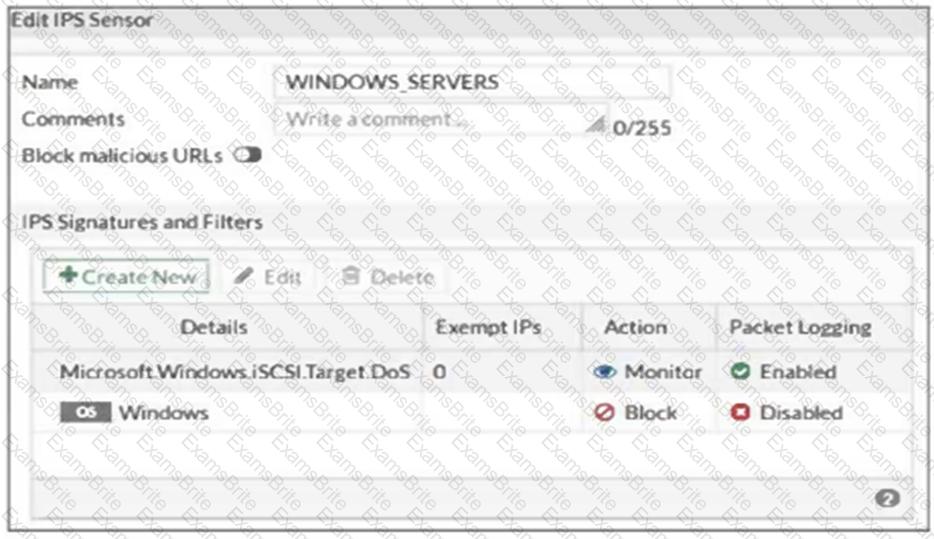
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
What is the primary FortiGate election process when the HA override setting is disabled?
Refer to the exhibit.
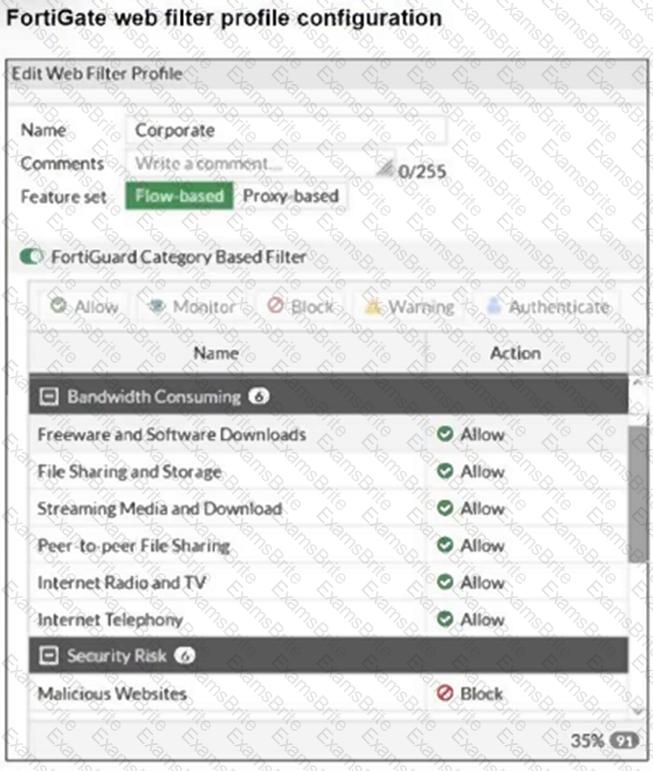
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
Refer to the exhibit.

Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
Which order must FortiGate use when the web filter profile has features such as safe search enabled?
Refer to the exhibit which contains a RADIUS server configuration.
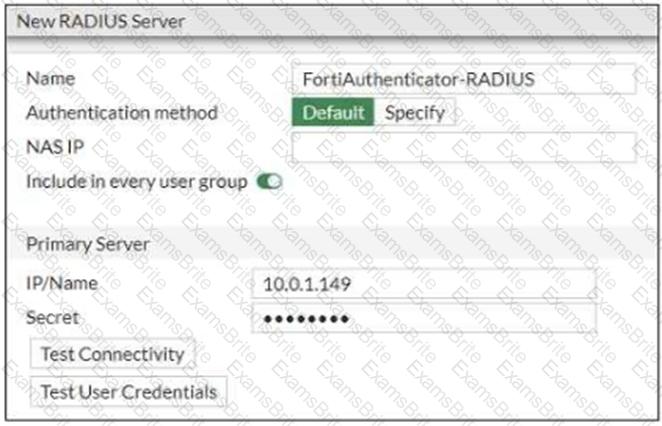
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
What is the impact of using the Include in every user group option in a RADIUS configuration?
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
Refer to the exhibits.
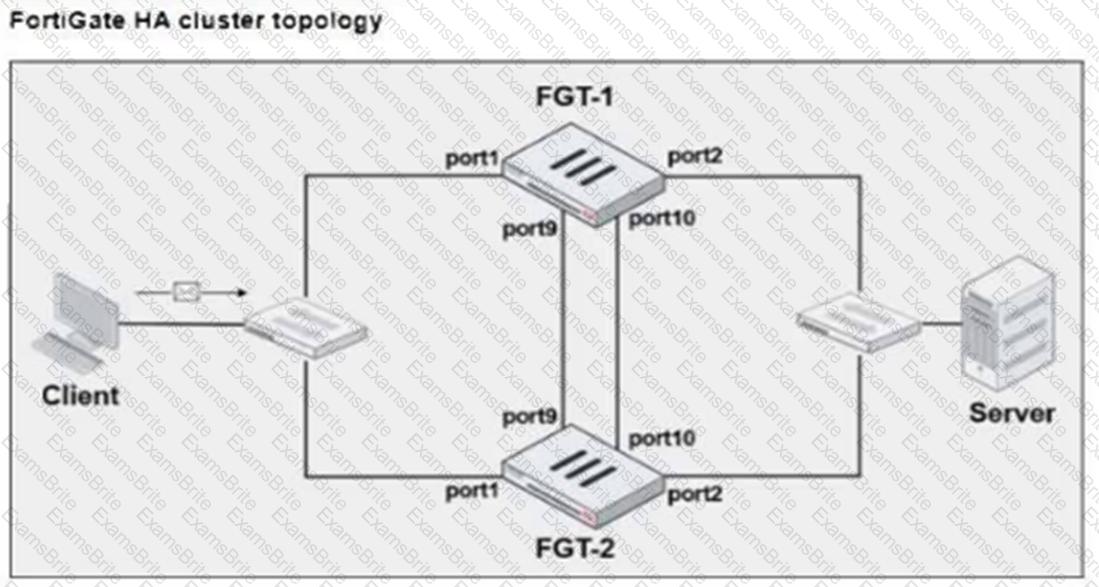
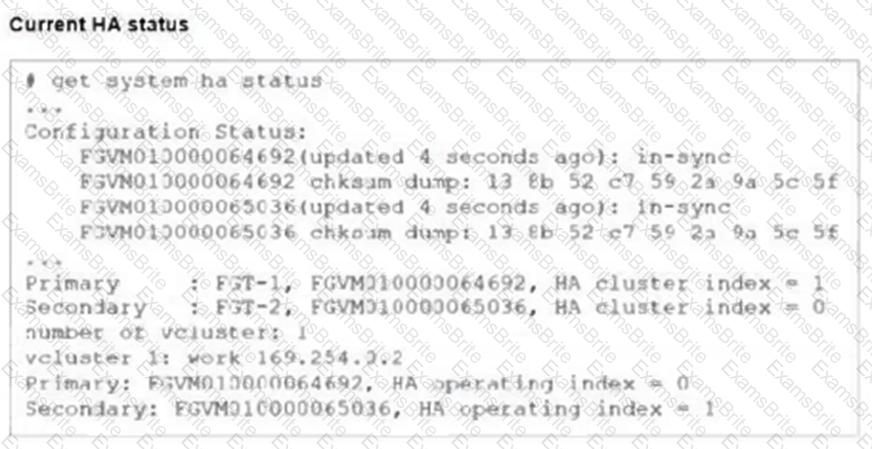
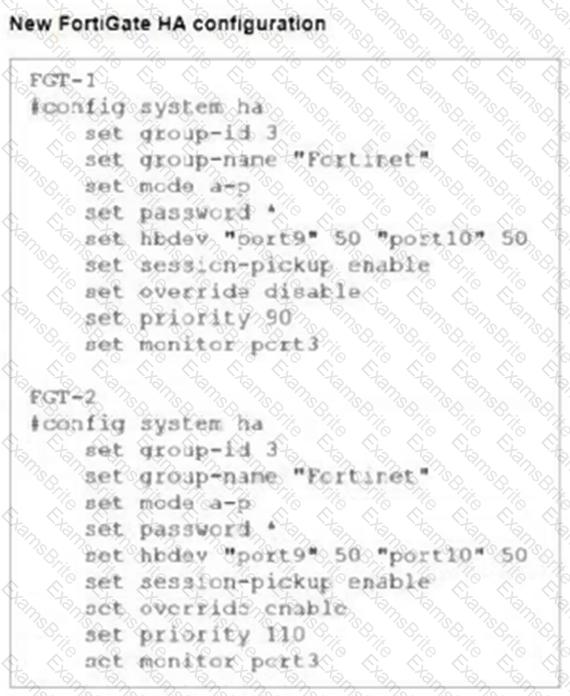
FGT-1 and FGT-2 are updated with HA configuration commands shown in the exhibit.
What would be the expected outcome in the HA cluster?