
AWS Certified SysOps Administrator - Associate
Last Update Feb 28, 2026
Total Questions : 263
We are offering FREE SOA-C01 Amazon Web Services exam questions. All you do is to just go and sign up. Give your details, prepare SOA-C01 free exam questions and then go for complete pool of AWS Certified SysOps Administrator - Associate test questions that will help you more.



A SySOps Administrator is managing an AWS account where Developers are authorized to launch Amazon EC2 instances to test new code. To limit costs, the Administrator must ensure that the EC2 instances in the account are terminated 24 hours after launch.
How should the Administrator meet these requirements?
An e-commerce company wants to lower costs on its nightly jobs that aggregate the current day’s sales and store the results in Amazon S3. The jobs are currently run using multiple on-demand instances and the job take just under 2 hours to complete. If a job fails for any reason, it needs to be restarted from the beginning.
What method is the MOST cost effective based on these requirements?
An application is being developed that will be served across a fleet of Amazon EC2 instances, which require a consistent view of persistent data. Items stored vary in size from 1 KB lo 300MB; the items are read frequently, created occasionally, and often require partial changes without conflict. The data store is not expected to grow beyond 2TB. and items will be expired according to age and content type.
Which AWS service solution meets these requirements?
After launching a new Amazon EC2 instance from a Microsoft Windows 2012 Amazon Machine Image (AMI), the SysOps Administrator is unable to connect to the instance using Remote Desktop Protocol (RDP). The instance is also unreachable. As part of troubleshooting, the Administrator deploys a second instance from a different AMI using the same configuration and is able to connect to the instance.
What should be the next logical step in troubleshooting the first instance?
A company is expanding its use of AWS services across its portfolios. The company wants to provision AWS accounts for each team to ensure a separation of business processes for security, compliance, and billing account creation and bootstrapping should be completed in a scalable and efficient way so new accounts are created with a defined baseline and governance guardrails in place. A sysops administrator needs to design a provisioning process that save time and resources.
Which action should be taken to meet these requirements?
An organization created an Amazon Elastic File System (Amazon EFS) volume with a file system ID of fs-85ba41fc, and it is actively used by 10 Amazon EC2 hosts. The organization has become concerned that the file system is not encrypted?
How can this be resolved?
A Systems Administrator is responsible for maintaining custom, approved AMIs for a company. These AMIs must be shared with each of the company’s AWS accounts.
How can the Administrator address this issue?
A company is planning to deploy multiple ecommerce websites across the eu-west-1, ap-east-1, and us-west-1 Regions. The websites consist of Amazon S3 buckets Amazon EC2 instances, Amazon RDS databases and Elastic Load Balancers.
Which method will accomplish the deployment with the LEAST amount of effort?
A SysOps Administrator is running Amazon EC2 instances in multiple AWS Regions. The Administrator wants to aggregate the CPU utilization for all instances onto an Amazon CloudWatch dashboard. Each region should be present on the dashboard and represented by a single graph that contains the CPU utilization for all instances in that region.
How can the Administrator meet these requirements?
A company needs to run a distributed application that processes large amounts of data across multiple EC2 instances. The application is designed to tolerate processing interruptions.
What is the MOST cost-effective Amazon EC2 pricing model for these requirements?
A company's IT department noticed an increase in the spend of their Developer AWS account. There are over 50 Developers using the account and the Finance Tram wants to determine the service costs incurred by each Developer.
What should a SysOps Administrator do to collect this information? (Select TWO)
A SysOps administrator created an AWS service catalog portfolio and shared the portfolio with a second AWS account in the company. The second account is controlled by a different administrator.
Which action will the administrator of the second account be able to perform?
A company has a business application hosted on Amazon EC2 instances behind an Application Load
Balancer. Amazon CloudWatch metrics show that the CPU utilization on the EC2 instances is very high. There are also reports from users that receive HTTP 503 and 504 errors when they try to connect to the application.
Which action will resolve these issues?
A company has a multi-tier web application. In the web tier, all the servers are in private subnets inside a VPC. The development team wants to make changes to the application that requires access to Amazon S3.
What should be done to accomplish this?
The Accounting department would like to receive billing updates more than once a month. They would like the updates to be in a format that can easily be viewed with a spreadsheet application.
How can this request be fulfilled?
A company has several accounts between different teams and wants to increase its auditing and compliance capabilities The accounts are managed through AWS Organizations. Management wants to provide the security team with secure access to the account logs while also restricting the possibility for the logs to be modified.
How can a sysops administrator achieve this is with the LEAST amount of operational overhead?
A chief financial officer has asked for a breakdown of costs per project in a single AWS account using cost explorer.
Which combination of options should be set to accomplish this? (Select two)
A web application runs on Amazon EC2 instances and accesses external services. The external services require authentication credentials. The application is deployed using AWS CloudFormation to three separate environments development test, and production Each environment requires unique credentials for external services
What option securely provides the application with the needed credential while requiring MINIMAL administrative overhead?
A company is concerned about a security vulnerability impacting its Linux operating system.
What should the SysOps Administrator do to alleviate this concern?
A financial service company is running distributed computing software to manage a fleet of 20 servers for their calculations. There are 2 control nodes and 18 worker nodes to run the calculations. Worker nodes can be automatically started by the control nodes when required. Currently, all nodes are running on demand, and the worker nodes are uses for approximately 4 hours each day.
Which combination of actions will be most cost-effective? (Select Two)
A SysOps Administrator needs to confirm that security best practices are being followed with the AWS account root user.
How should the Administrator ensure that this is done?
An HTTP web application is launched on Amazon EC2 instances behind an ELB Application Load Balancer. The EC2 instances run across multiple Availability Zones. A network ACL and a security group for the load balancer and EC2 instances allow inbound traffic on port 80. After launch, the website cannot be reached over the internet.
What additional step should be taken?
An application team has asked a sysops administrator to provision an additional environment for an application in four additional regions. The application is running on more than 100 instances in us-east-1, using fully baked AMIs, An AWS CloudFormation template has been created to deploy resources in us-east-1.
What must the sysops administrator do to provision the application quickly?
A SysOps Administrator has implemented a VPC network design with the following requirements
• Two Availability Zones (AZs) - Two private subnets
• Two public subnets
• One internet gateway
• One NAT gateway
What would potentially cause applications in the VPC to fail during an AZ outage?
An application resides on multiple EC2 instances in public subnets in two Availability Zones. To improve security, the Information Security team has deployed an Application Load Balancer (ALB) in separate subnets and pointed the DNS at the ALB instead of the EC2 instances.
After the change, traffic is not reaching the instances, and an error is being returned from the ALB.
What steps must a SysOps Administrator take to resolve this issue and improve the security of the application? (Select TWO.)
A SysOps Administrator has been tasked with deploying a company’s infrastructure as code. The Administrator wants to write a single template that can be reused for multiple environments in a safe, repeatable manner.
What is the recommended way to use AWS CloudFormation to meet this requirement?
A SysOps Administrator has an AWS CloudFormation template of the company’s existing infrastructure in us-west-2. The Administrator attempts to use the template to launch a new stack in eu-west-1, but the stack only partially deploys, receives an error message, and then rolls back.
Why would this template fail to deploy? (Choose two.)
A web application accepts orders from online users and places the orders into an Amazon SQS queue. Amazon EC2 instances in an EC2 Auto Scaling group read the messages from the queue, process the orders, and email order confirmations to the users. The Auto Scaling group scales up and down based on the queue depth. At the beginning of each business day, users report confirmation emails are delayed.
What action will address this issue?
A company wants to identify specific Amazon EC2 instances that ate underutilized and the estimated cost savings for each instance How can this be done with MINIMAL effort?
A security researcher has published a new Common Vulnerabilities and Exposures (CVE) report that impacts a popular operating system A SysOps Administrator is concerned with the new CVE report and wants to patch the company's systems immediately The Administrator contacts AWS Support and requests the patch be applied to all Amazon EC2 instances
How will AWS respond to this request?
A SysOps Administrator working on an Amazon EC2 instance has misconfigured the clock by one hour. The EC2 instance is sending data to Amazon CloudWatch through the CloudWatch agent. The timestamps on the logs are 45 minutes in the future.
What will be the result of this configuration?
A medical imaging company needs lo process large amounts of imaging data in real time using a specific instance type. The company wants to guarantee sufficient resource capacity for 1 year
Which action will meet these requirements in the MOST cost-effective manner?
A company manages multiple AWS accounts and wants to provide access to AWS from a single management account using an existing on-premises Microsoft Active Directory domain. Which solution will meet these requirements with the LEAST amount of effort?
A company monitors its account activity using AWS CloudTrail, and is concerned that some log files are being tampered with after the logs have been delivered to the account’s Amazon S3 bucket.
Moving forward, how can the SysOps Administrator confirm that the log files have not been modified after being delivered to the S3 bucket.
A Security and Compliance team is reviewing Amazon EC2 workloads for unapproved AMI usage.
Which action should a SysOps Administrator recommend?
A company needs to ensure that all IAM users rotate their password on a regular basis.
Which action should be taken to implement this?
A SysOps administrator needs to register targets for a Network Load Balancer (NL8) using IP addresses Which prerequisite should the SysOps administrator validate to perform this task?
A popular auctioning platform requires near-real-time access to dynamic bidding information. The platform must be available at all times The current Amazon RDS instance often reaches 100% CPU utilization during the weekend auction and can no longer be resized. To improve application performance, a sysops administrator is evaluating Amazon ElastiCache and has chosen Redis (cluster mode enabled) instead of Memcached
What are reasons for making this choice? (Select TWO.)
A SysOps administrator implemented the following bucket policy to allow only the corporate IP address range of 54.240.143.0/24 to access objects in an Amazon S3 bucket. 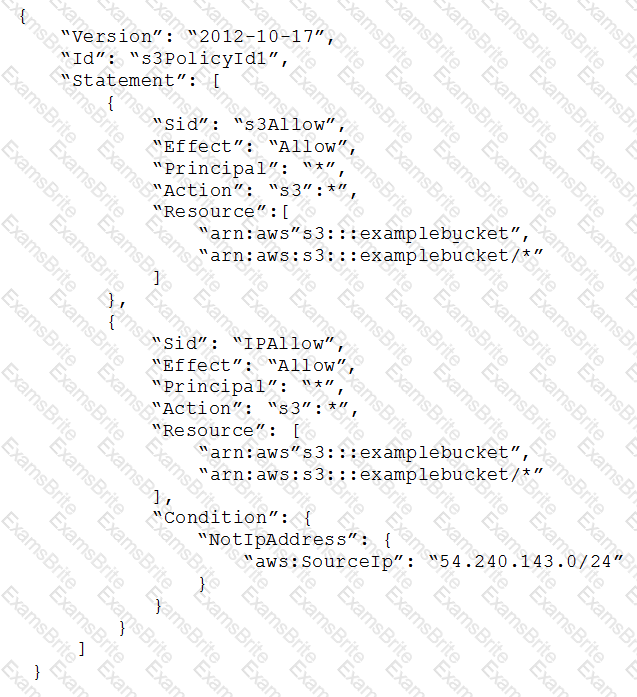
Some employees are reporting that they are able to access the S3 bucket from IP addresses outside the corporate IP address range.
How can the Administrator address this issue?