Microsoft Cybersecurity Architect
Last Update Feb 28, 2026
Total Questions : 246
We are offering FREE SC-100 Microsoft exam questions. All you do is to just go and sign up. Give your details, prepare SC-100 free exam questions and then go for complete pool of Microsoft Cybersecurity Architect test questions that will help you more.



You have an Azure subscription that contains multiple Azure Data Lake Storage accounts.
You need to recommend a solution to encrypt the content of the accounts by using service-side encryption and customer-managed keys. The solution must ensure that individual encryption keys are applied at the most granular level.
At which level should you recommend the encryption be applied?
Your company is moving all on-premises workloads to Azure and Microsoft 365. You need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
• Minimizes manual intervention by security operation analysts
• Supports Waging alerts within Microsoft Teams channels
What should you include in the strategy?
Your company uses Azure Pipelines and Azure Repos to implement continuous integration and continuous deployment (CI/CD) workflows for the deployment of applications to Azure.
You are updating the deployment process to align with DevSecOps controls guidance in the Microsoft Cloud Adoption Framework for Azure.
You need to recommend a solution to ensure that all code changes are submitted by using pull requests before being deployed by the CI/CD workflow.
What should you include in the recommendation?
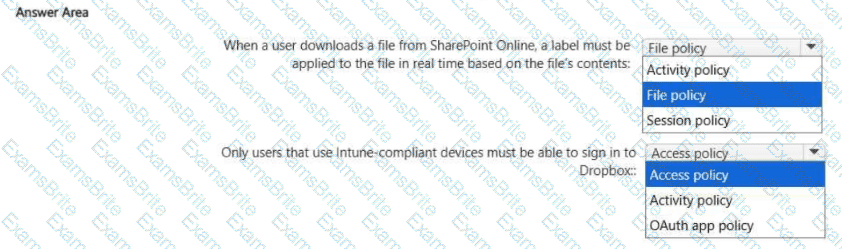
You have a Microsoft 365 E5 subscription. The subscription contains 1,000 devices that run Windows 11 Pro and are enrolled in Microsoft Intune. You need to recommend a Microsoft Defender for Cloud Apps solution that meets the following requirements:
• When a user downloads a file from Microsoft SharePoint Online, a label must be applied to the file in real time based on the file's contents.
• Only users that use Intune-compliant devices must be able to sign in to Dropbox.
Which type of policy should you recommend for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You plan to deploy enterprise-scale landing zones based on the Microsoft Cloud Adoption Framework for Azure. The deployment will include a single-platform landing zone for all shared services and three application landing zones that will each host a different Azure application.
You need to recommend which resource to deploy to each landing zone. The solution must meet the Cloud Adoption Framework best-practice recommendations for enterprise-scale landing zones.
What should you recommend?
What should you create in Azure AD to meet the Contoso developer requirements?

Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
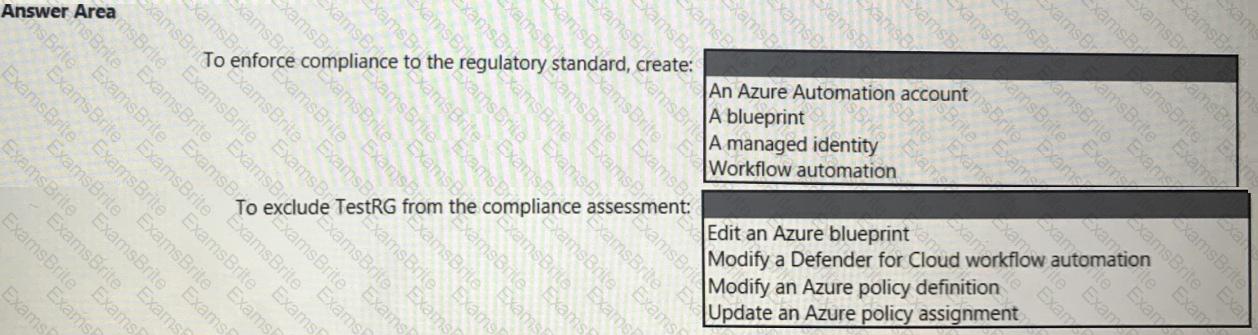
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
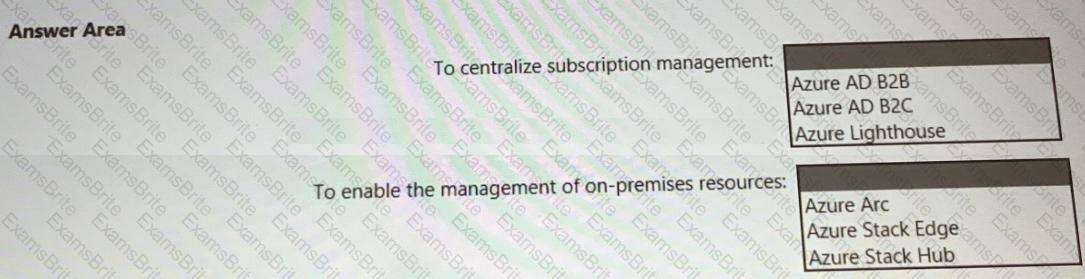
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
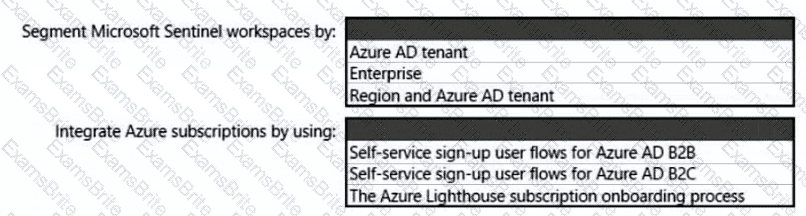
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
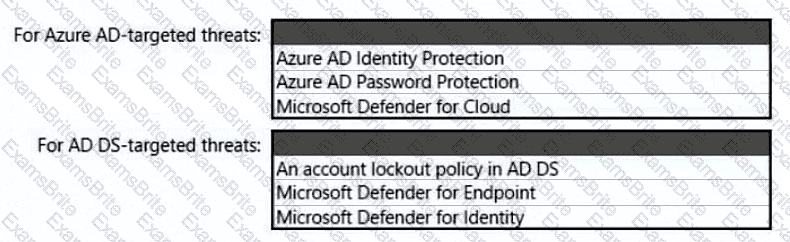
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags.
Does this meet the goal?
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard.
You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices:
• Computers that run either Windows 10 or Windows 11
• Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored. What should you include in the recommendation?
For a Microsoft cloud environment, you need to recommend a security architecture that follows the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
Which security methodologies should you include in the recommendation? To answer, drag the appropriate methodologies to the
correct principles. Each methodology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

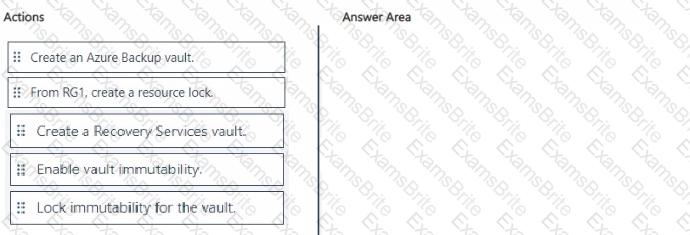
You have an Azure subscription that contains a resources group named RG1. RG1 contains multiple Azure Files shares.
You need to recommend a solution to deploy a backup solution for the shares. The solution must meet the following requirements:
• Prevent the deletion of backups and the vault used to store the backups.
• Prevent privilege escalation attacks against the backup solution.
• Prevent the modification of the backup retention period.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
You have an Azure subscription and a Microsoft 365 subscription.
Your company uses several software as a service (SaaS) applications.
To align with Microsoft cloud security benchmark (MCSB) and Microsoft Cybersecurity Reference Architectures (MCRA), you plan to design a solution to provide visibility into user activity across the applications and detect potentially risky behavior in real time.
Which service should you recommend?
You have a customer that has a Microsoft 365 subscription and an Azure subscription.
The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure.
You need to design a security solution to assess whether all the devices meet the customer's compliance rules.
What should you include in the solution?
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
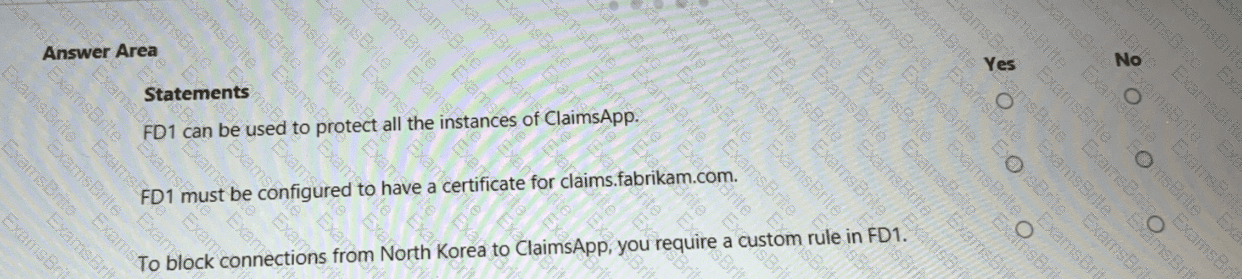
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.