
Palo Alto Networks System Engineer - Cortex Professional
Last Update Feb 19, 2026
Total Questions : 168
We are offering FREE PSE-Cortex Paloalto Networks exam questions. All you do is to just go and sign up. Give your details, prepare PSE-Cortex free exam questions and then go for complete pool of Palo Alto Networks System Engineer - Cortex Professional test questions that will help you more.



"Bob" is a Demisto user. Which command is used to add 'Bob" to an investigation from the War Room CLI?
Which playbook functionality allows grouping of tasks to create functional building blocks?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
A Cortex XSOAR customer wants to send a survey to users asking them to input their manager's email for a training use case so the manager can receive status reports on the employee's training. However, the customer is concerned users will provide incorrect information to avoid sending status updates to their manager.
How can Cortex XSOAR most efficiently sanitize user input prior to using the responses in the playbook?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
Cortex XSOAR has extracted a malicious Internet Protocol (IP) address involved in command-and-control (C2) traffic.
What is the best method to block this IP from communicating with endpoints without requiring a configuration change on the firewall?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS

Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
Which statement applies to the malware protection flow of the endpoint agent in Cortex XSIAM?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
Which command is used to add Cortex XSOAR "User1" to an investigation from the War Room command-line interface (CLI)?
Which integration allows searching and displaying Splunk results within Cortex XSOAR?
A General Purpose Dynamic Section can be added to which two layouts for incident types? (Choose two)
A customer has purchased Cortex XDR and requires 24/7 monitoring of the platform. However, the customer only has staff available during business hours.
Which Palo Alto Networks offering would best meet this requirement?
An antivirus refresh project was initiated by the IT operations executive. Who is the best source for discussion about the project's operational considerations'?
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
An adversary attempts to communicate with malware running on a network in order to control malware activities or to exfiltrate data from the network.
Which Cortex XDR Analytics alert will this activity most likely trigger?
How does Cortex XSOAR automation save time when a phishing incident occurs?
What is a key difference between audit users and full users in Cortex XSOAR?
Which statement applies to the malware protection flow in Cortex XDR Prevent?
The certificate used for decryption was installed as a trusted root CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
A Cortex XSOAR customer has a phishing use case in which a playbook has been implemented with one of the steps blocking a malicious URL found in an email reported by one of the users.
What would be the appropriate next step in the playbook?
If a customer activates a TMS tenant and has not purchased a Cortex Data Lake instance.
Palo Alto Networks will provide the customer with a free instance
What size is this free Cortex Data Lake instance?
An administrator has a critical group of systems running Windows XP SP3 that cannot be upgraded The administrator wants to evaluate the ability of Traps to protect these systems and the word processing applications running on them
How should an administrator perform this evaluation?
Which resource can a customer use to ensure that the Cortex XDR agent will operate correctly on their CentOS 07 servers?
Which process in the causality chain does the Cortex XDR agent identify as triggering an event sequence?
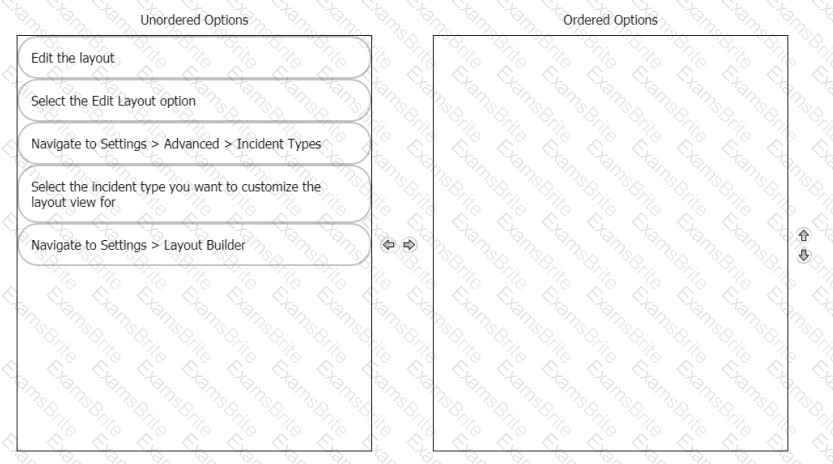
Rearrange the steps into the correct order for modifying an incident layout.
What is the size of the free Cortex Data Lake instance provided to a customer who has activated a TMS tenant, but has not purchased a Cortex Data Lake instance?
Which Cortex XDR license is required for a customer that requests endpoint detection and response (EDR) data collection capabilities?
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Which two areas of Cortex XDR are used for threat hunting activities? (Choose two.)
Which deployment type supports installation of an engine on Windows, Mac OS. and Linux?
How does a clear understanding of a customer’s technical expertise assist in a hand off following the close of an opportunity?
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
Which feature of Cortex Xpanse allows it to identify previously unknown assets?
Which service helps identify attackers by combining world-class threat intelligence with Cortex XSIAM technology?