
Palo Alto Networks Certified Network Security Consultant
Last Update Feb 28, 2026
Total Questions : 60
We are offering FREE PCNSC Paloalto Networks exam questions. All you do is to just go and sign up. Give your details, prepare PCNSC free exam questions and then go for complete pool of Palo Alto Networks Certified Network Security Consultant test questions that will help you more.



Which administrative authentication method supports authorization by an external service?
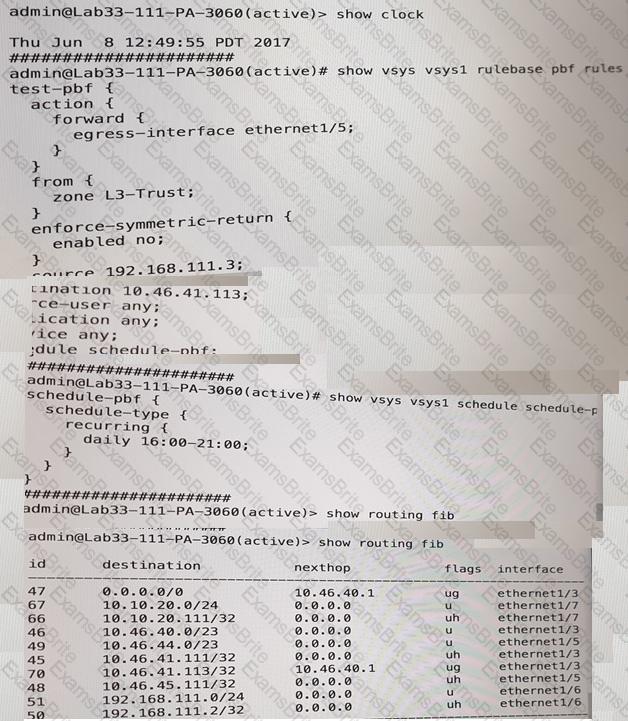
What will be the egress interface if the traffic’s ingress interface is Ethernet 1/6 sourcing form 192.168.11.3 and to the destination 10.46.41.113.during the.
An administrator accidentally closed the commit window/screen before the commit was finished. Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
A)

B)
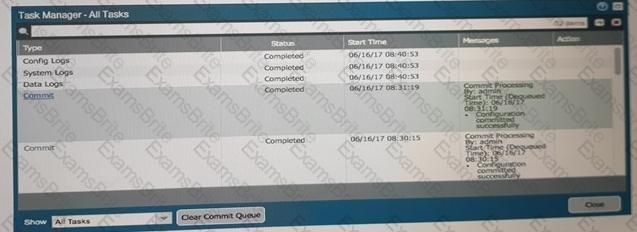
C)
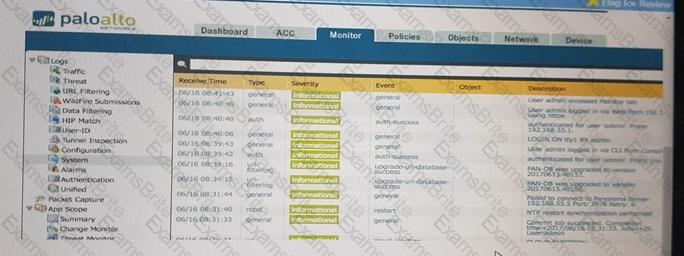
D)
Which method will dynamically register tags on the Palo Alto Networks NGFW?
Which three authentication faction factors does PAN-OS® software support for MFA? (Choose three.)
Which two action would be part of an automatic solution that would block sites with untrusted certificates without enabling SSLforward proxy? (Choose two.)
An administrator deploys PA-500 NGFWs as an active/passive high availability pair . Thedevices are not participating in dynamic router and preemption is disabled.
What must be verified to upgrade the firewalls to the most recent version of PAN OS® software?
A Palo Alto Networks NGFW just submitted a file lo WildFire tor analysis Assume a 5-minute window for analysis. The firewall is configured to check for verdicts every 5 minutes.
How quickly will the firewall receive back a verdict?
Which administrative authentication method supports authorization by an external service?