
CyberArk CDE Recertification
Last Update Mar 1, 2026
Total Questions : 221
We are offering FREE PAM-CDE-RECERT CyberArk exam questions. All you do is to just go and sign up. Give your details, prepare PAM-CDE-RECERT free exam questions and then go for complete pool of CyberArk CDE Recertification test questions that will help you more.



What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
Which option in the PrivateArk client is used to update users' Vault group memberships?
When creating Distributed Vault environment architecture, what is the maximum number of Vault servers that can be deployed''
A company requires challenge/response multi-factor authentication for PSMP sessions. Which server must you integrate with the CyberArk vault?
You have associated a logon account to one your UNIX cool accounts in the vault. When attempting to [b]change [/b] the root account’s password the CPM will…..
A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights.
Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
To enable the Automatic response “Add to Pending” within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
What is a prerequisite step before CyberArk can be configured to support RADIUS authentication?
All of your Unix root passwords are stored in the safe UnixRoot. Dual control is enabled for some of the accounts in that safe. The members of the AD group UnixAdmins need to be able to use the show, copy, and connect buttons on those passwords at any time without confirmation. The members of the AD group Operations Staff need to be able to use the show, copy and connect buttons on those passwords on an emergency basis, but only with the approval of a member of Operations Managers never need to be able to use the show, copy or connect buttons themselves.
Which safe permission do you need to grant Operations Staff? Check all that apply.
You are installing HTML5 gateway on a Linux host using the RPM provided. After installing the Tomcat webapp, what is the next step in the installation process?
For a safe with Object Level Access enabled you can turn off Object Level Access Control when it no longer needed on the safe.
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
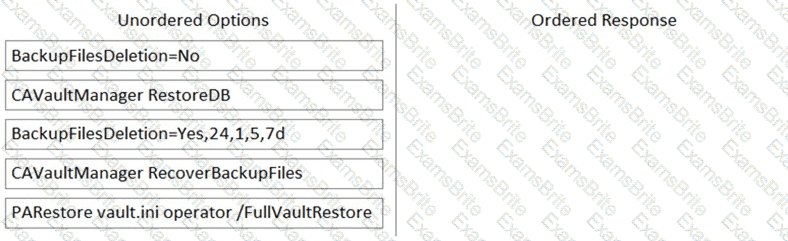
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
To ensure all sessions are being recorded, a CyberArk administrator goes to the master policy and makes configuration changes.
Which configuration is correct?
What is a prerequisite step betore CyberArk can be configured to support RADIUS authentication?
In addition to bit rate and estimated total duration of recordings per day, what is needed to determine the amount of storage required for PSM recordings?
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
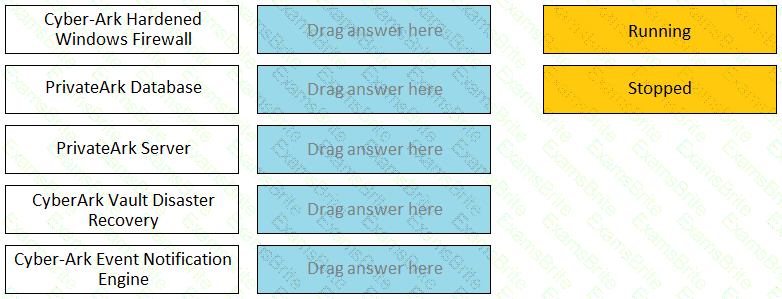
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.
Which parameter controls how often the CPM looks for accounts that need to be changed from recently completed Dual control requests.
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
You want to generate a license capacity report.
Which tool accomplishes this?
A customer is moving from an on-premises to a public cloud deployment. What is the best and most cost-effective option to secure the server key?
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
You are helping a customer prepare a Windows server for PSM installation. What is required for a successful installation?
A user has successfully conducted a short PSM session and logged off. However, the user cannot access the Monitoring tab to view the recordings.
What is the issue?
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
You are installing multiple PVWAs behind a load balancer. Which statement is correct?
After installing the first PSM server and before installing additional PSM servers you must ensure the user performing the installation is not a direct owner of which safe?
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
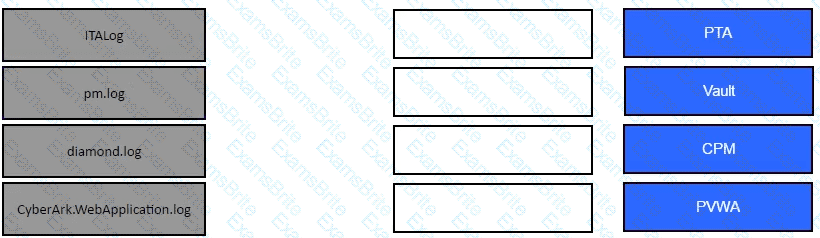
Match the log file name with the CyberArk Component that generates the log.
Which of the following Privileged Session Management (PSM) solutions support live monitoring of active sessions?
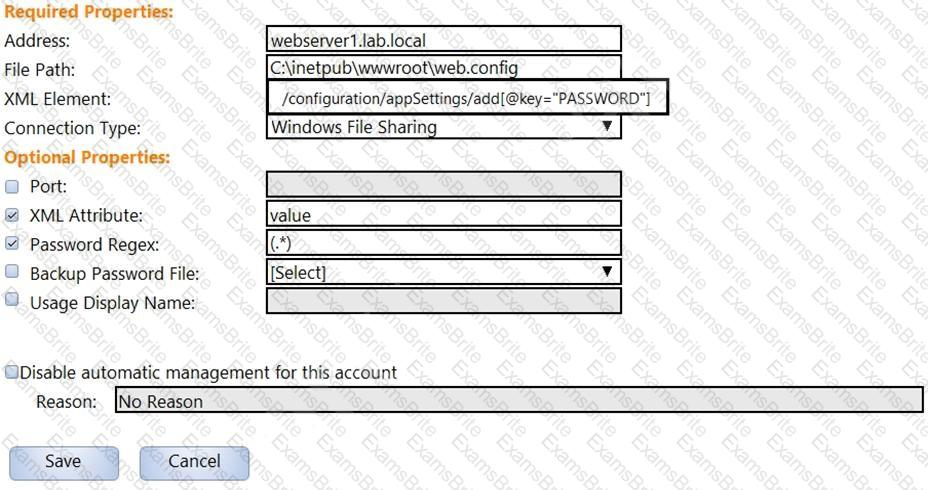
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
CyberArk recommends implementing object level access control on all Safes.
You have been asked to turn off the time access restrictions for a safe.
Where is this setting found?
You have been asked to design the number of PVWAs a customer must deploy. The customer has three data centers with a distributed vault in each, requires high availability, and wants to use all vaults, at all times. How many PVWAs does the customer need?
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
Users who have the 'Access Safe without confirmation' safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.