
Netskope Certified Cloud Security Integrator (NCCSI)
Last Update Feb 28, 2026
Total Questions : 93
We are offering FREE NSK200 Netskope exam questions. All you do is to just go and sign up. Give your details, prepare NSK200 free exam questions and then go for complete pool of Netskope Certified Cloud Security Integrator (NCCSI) test questions that will help you more.



You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
You are currently migrating users away from a legacy proxy to the Netskope client in the company’s corporate offices. You have deployed the client to a pilot group; however, when the client attempts to connect to Netskope, it fails to establish a tunnel.
In this scenario, what would cause this problem?
An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
You are provisioning Netskope users from Okta with SCIM Provisioning, and users are not showing up in the tenant. In this scenario, which two Netskope components should you verify first In Okta for accuracy? (Choose two.)
Review the exhibit.
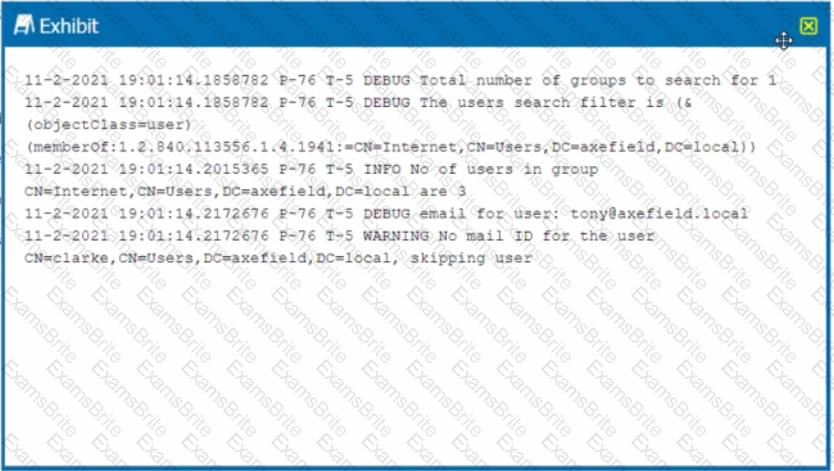
You are troubleshooting a Netskope client for user Clarke which remains in a disabled state after being installed. After looking at various logs, you notice something which might explain the problem. The exhibit is an excerpt from the nsADImporterLog.log.
Referring to the exhibit, what is the problem?
You have deployed Netskope Secure Web Gateway (SWG). Users are accessing new URLs that need to be allowed on a daily basis. As an SWG administrator, you are spending a lot of time updating Web policies. You want to automate this process without having to log into the Netskope tenant
Which solution would accomplish this task?
You are creating an API token to allow a DevSecOps engineer to create and update a URL list using REST API v2. In this scenario, which privilege(s) do you need to create in the API token?
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents. In this scenario, which two statements are true? (Choose two.)
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
Your organization has three main locations with 30.000 hosts in each location. You are planning to deploy Netskope using iPsec tunnels for security.
What are two considerations to make a successful connection in this scenario? (Choose two.)
You have created a specific Skope IT application events query and want to have the query automatically run and display the results every time you log into your tenant.
Which two statements are correct in this scenario? (Choose two.)
Your customer is concerned about malware in their AWS S3 buckets. What two actions would help with this scenario? (Choose two.)
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or "Access key"?
Review the exhibit.
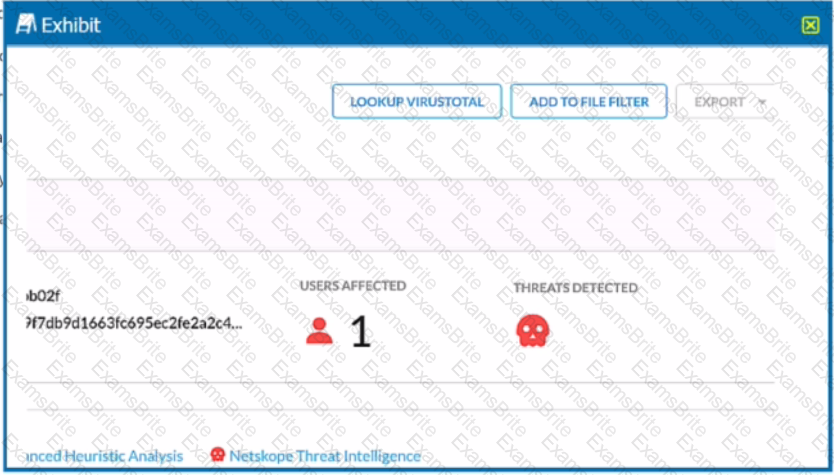
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
You are comparing the behavior of Netskope's Real-time Protection policies to API Data Protection policies. In this Instance, which statement is correct?
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as Crowdstrike.
Which two requirements are needed for a successful integration and sharing of threat data? (Choose two.)
You use Netskope to provide a default Malware Scan profile for use with your malware policies. Also, you want to create a custom malware detection profile.
In this scenario, what are two additional requirements to complete this task? (Choose two.)
Netskope is being used as a secure Web gateway. Your organization's URL list changes frequently. In this scenario, what makes It possible for a mass update of the URL list in the Netskope platform?
Review the exhibit.
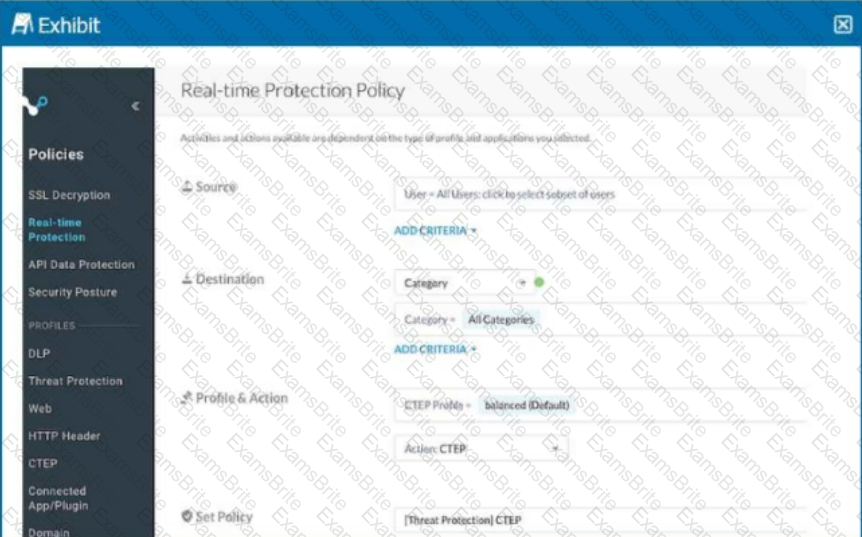
Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
Review the exhibit.
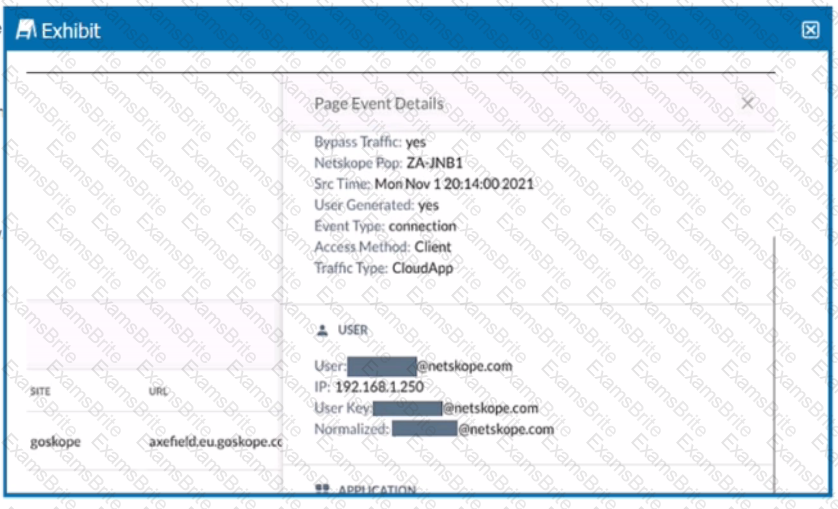
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
Your customer currently only allows users to access the corporate instance of OneDrive using SSO with the Netskope client. The users are not permitted to take their laptops when vacationing, but sometimes they must have access to documents on OneDrive when there is an urgent request. The customer wants to allow employees to remotely access OneDrive from unmanaged devices while enforcing DLP controls to prohibit downloading sensitive files to unmanaged devices.
Which steering method would satisfy the requirements for this scenario?
You are an administrator writing Netskope Real-time Protection policies and must determine proper policy ordering.
Which two statements are true in this scenario? (Choose two.)
Your company wants to know if there has been any unusual user activity. In the UI, you go to Skope IT -> Alerts.
Which two types of alerts would you filter to find this information? (Choose two.)