
Netskope Certified Cloud Security Administrator (NCCSA)
Last Update Feb 28, 2026
Total Questions : 129
We are offering FREE NSK101 Netskope exam questions. All you do is to just go and sign up. Give your details, prepare NSK101 free exam questions and then go for complete pool of Netskope Certified Cloud Security Administrator (NCCSA) test questions that will help you more.



A Netskope administrator wants to create a policy to quarantine files based on sensitive content.
In this scenario, which variable must be included in the policy to achieve this goal?
Which compliance standard should a company consider if both controllers and processors have legal entities in the EU?
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
Which Netskope component would an administrator use to see an overview of private application usage and performance?
Your company asks you to obtain a detailed list of all events from the last 24 hours for a specific user. In this scenario, what are two methods to accomplish this task? (Choose two.)
Which two functions are available for both inline and API protection? (Choose two.)
A new customer is concerned about performance, especially with respect to Microsoft 365. They have offices in 20 countries around the world and their workforce is mostly mobile.
In this scenario, which two statements about NewEdge would align with the customer's requirements? (Choose two.)
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
Which two common security frameworks are used today to assess and validate a vendor's security practices? (Choose two.)
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
There is a DLP violation on a file in your sanctioned Google Drive instance. The file is in a deleted state. You need to locate information pertaining to this DLP violation using Netskope. In this scenario, which statement is correct?
You investigate a suspected malware incident and confirm that it was a false alarm.
What are two supported ways to provision users to your customer's Netskope tenant? (Choose two.)
What is the limitation of using a legacy proxy compared to Netskope's solution?
What are two valid use cases for the Cloud Confidence Index (CCI)? (Choose two.)
You are setting up a real-time threat protection policy for patient zero to block previously unseen files until a benign verdict is produced by the Netskope Threat Protection Service. In this scenario, which two policy parameters must you configure? (Choose two)
You are required to restrict cloud users from uploading data to any risky cloud storage service as defined by the Cloud Confidence Index. In the Netskope platform, which two policy elements would enable you to implement this control? (Choose two)
Your organization has recently implemented Netskope Private Access. During an investigation, your security team has asked you to provide a list of all hosts including domains and IP addresses that a user accessed through Netskope Private Access for the past seven days.
Which two locations in the Netskope Web UI would allow you to obtain and export the requested data? (Choose two.)
Click the Exhibit button.
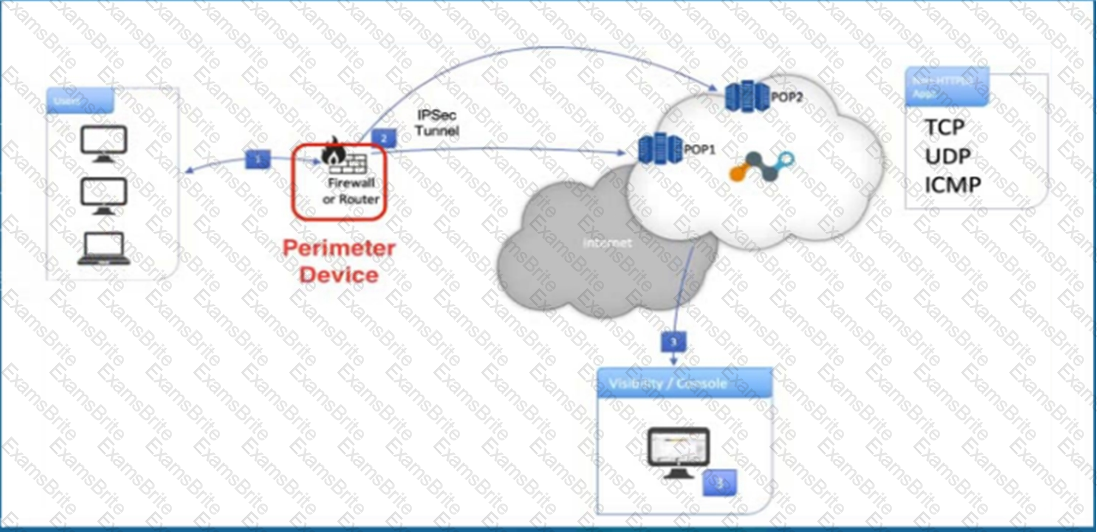
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
A company user cannot open a sports news site. You want to review the category of the website and see how the rules are applied even though this category is allowed. In this scenario, which action will accomplish this task?
Click the Exhibit button.
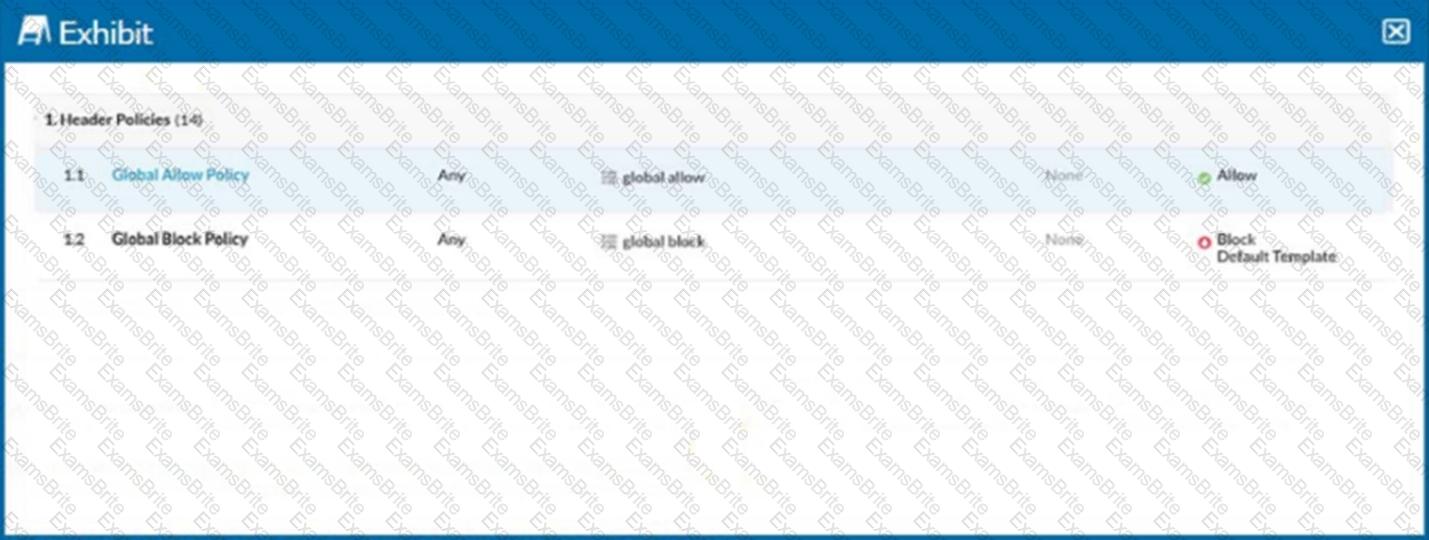
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
You determine that a business application uses non-standard HTTPS ports. You want to steer all HTTPS traffic for this application and have visibility and control over user activities.
Which action will allow you to accomplish this task?
Exhibit
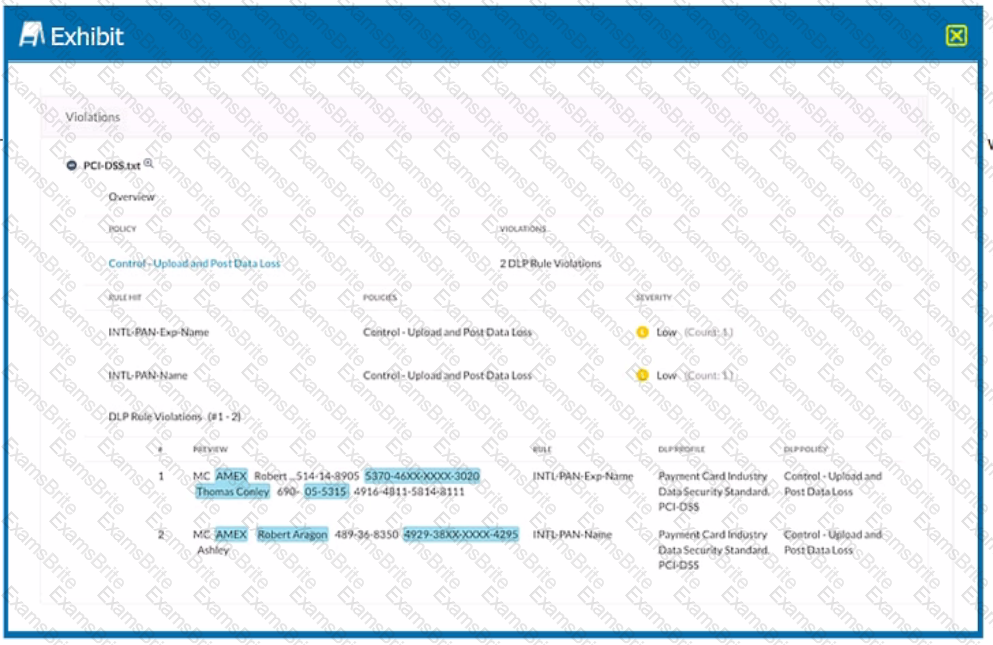
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
Click the Exhibit button.
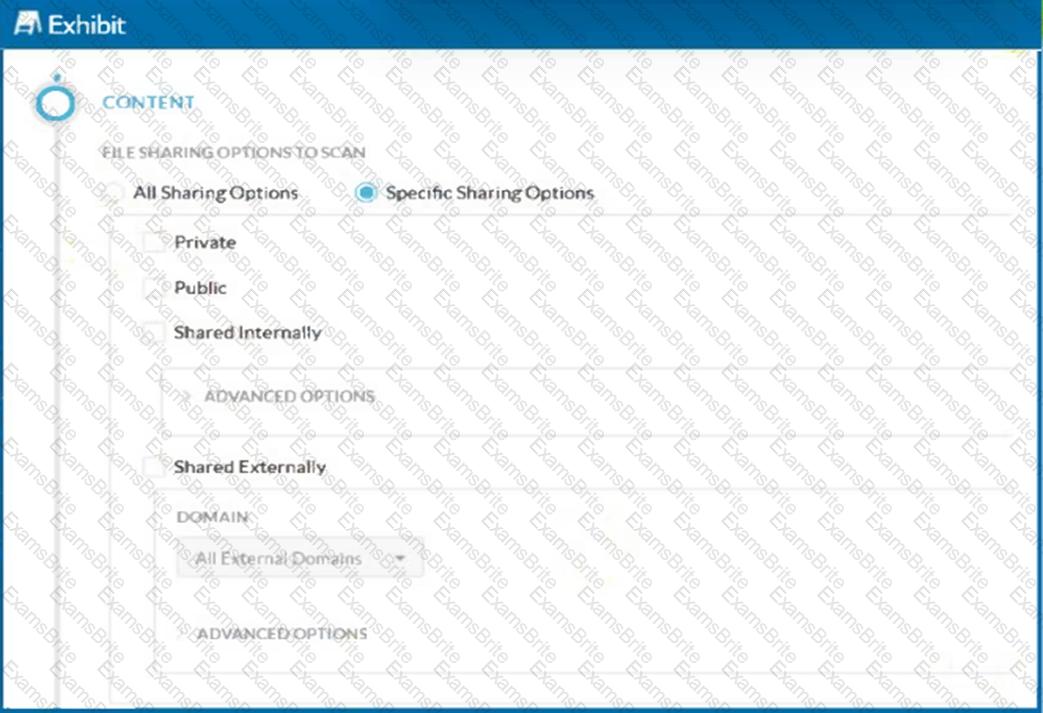
A customer has created a CASB API-enabled Protection policy to detect files containing sensitive data that are shared outside of their organization.
Referring to the exhibit, which statement is correct?
As an administrator, you are investigating an increase in the number of incidents related to compromised credentials. You are using the Netskope Compromised Credentials feature on your tenant to assess the situation. Which insights would you find when using this feature? (Choose two)
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors potential risky users for a malicious activity that would cause data loss?
Your department is asked to report on GDPR data publicly exposed in Microsoft 365, Salesforce. and Slack-sanctioned cloud applications. Which deployment model would you use to discover this data?
How do you provision users to your customer's Netskope tenant? (Choose two.)
What are two reasons why legacy solutions, such as on-premises firewalls and proxies, fail to secure the data and data access compared to Netskope Secure Web Gateway? (Choose two.)
Which networking function does a SASE solution provide above and beyond an SSE solution?
Click the Exhibit button.
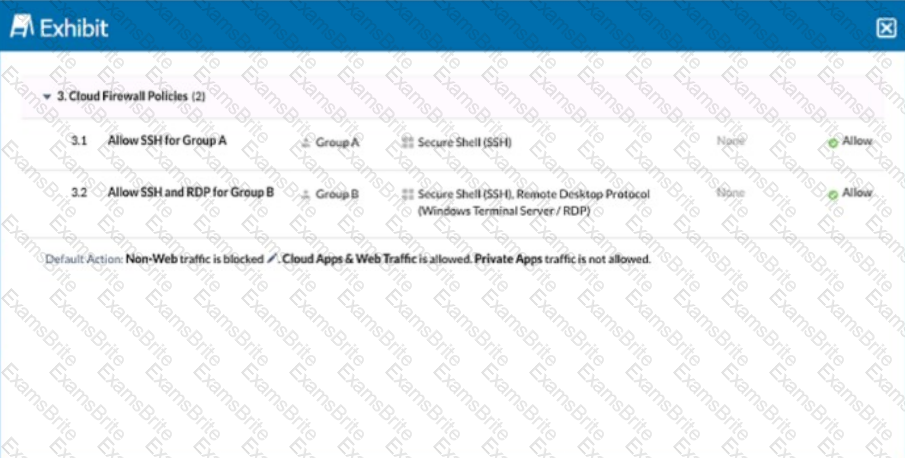
You configured a set of Cloud Firewall policies as shown in the exhibit and changed your Steering Configuration to All Traffic for Group A and Group B. Users in Group A report that they are unable to access a third-party server using TCP port 3389. Referring to the exhibit, which action correctly describes how you would allow these connections without allowing unnecessary access?
The Netskope deployment for your organization is deployed in CASB-only mode. You want to view dropbox.com traffic but do not see it when using SkopeIT.
In this scenario, what are two reasons for this problem? (Choose two.)
What are two benefits of creating a policy group as a logical collection of Real-time Protection policies? (Choose two.)
All users are going through Netskope's Next Gen SWG. Your CISO requests a monthly report of all users who are accessing cloud applications with a "Low" or a "Poor" CCL, where the activity is either "Edit" or "Upload".
Using the Advanced Analytics interface, which two statements describe which actions must be performed in this scenario? (Choose two.)
An administrator has created a DLP rule to search for text within documents that match a specific pattern. After creating a Real-time Protection Policy to make use of this DLP rule, the administrator suspects the rule is generating false positives.
Within the Netskope tenant, which feature allows administrators to review the data that was matched by the DLP rule?
Which two statements are correct about Netskope’s NewEdge Security Cloud Network Infrastructure? (Choose two.)