
Fortinet NSE 7 - Security Operations 7.6 Architect
Last Update Feb 28, 2026
Total Questions : 57
We are offering FREE NSE7_SOC_AR-7.6 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE7_SOC_AR-7.6 free exam questions and then go for complete pool of Fortinet NSE 7 - Security Operations 7.6 Architect test questions that will help you more.



Refer to the exhibits.
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
Refer to the exhibit.
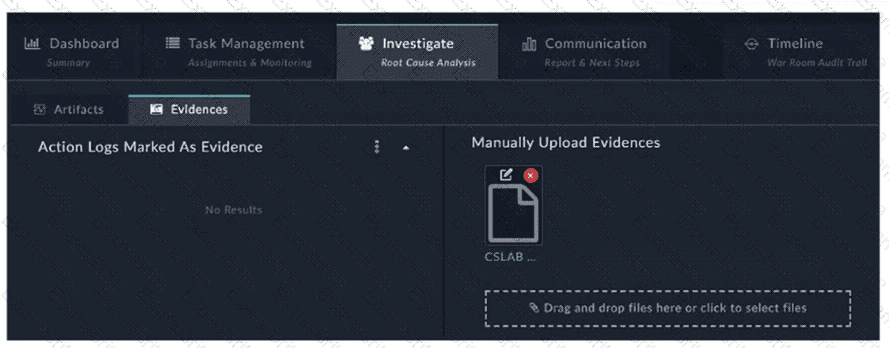
How do you add a piece of evidence to the Action Logs Marked As Evidence area? (Choose one answer)
While monitoring your network, you discover that one FortiGate device is sending significantly more logs to FortiAnalyzer than all of the other FortiGate devices in the topology.
Additionally, the ADOM that the FortiGate devices are registered to consistently exceeds its quota.
What are two possible solutions? (Choose two.)
Refer to the exhibit.
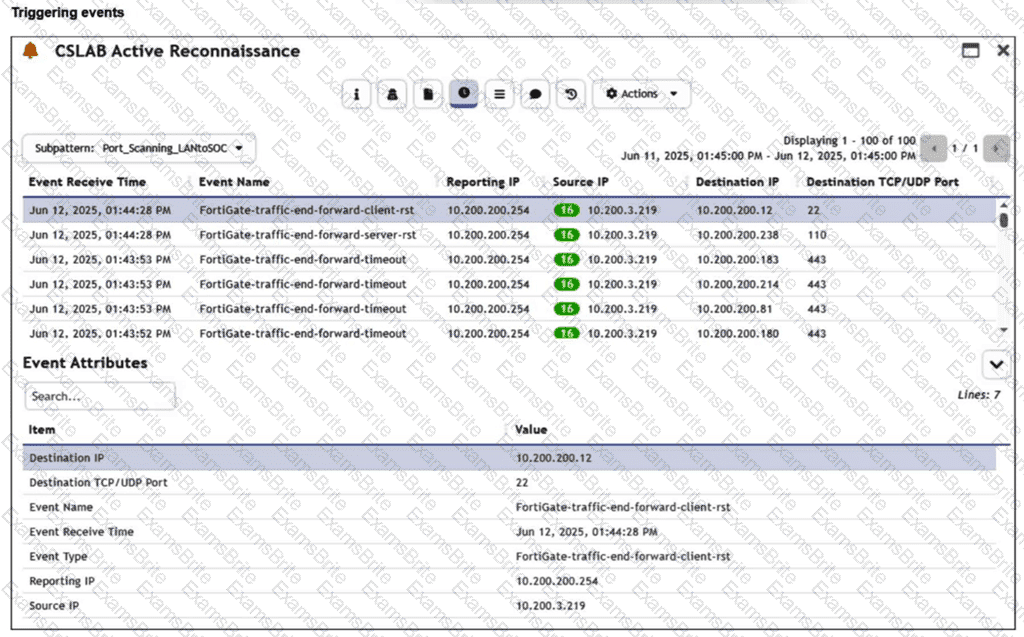
You are reviewing the Triggering Events page for a FortiSIEM incident. You want to remove the Reporting IP column because you have only one firewall in the topology. How do you accomplish this? (Choose one answer)
Refer to the exhibit.
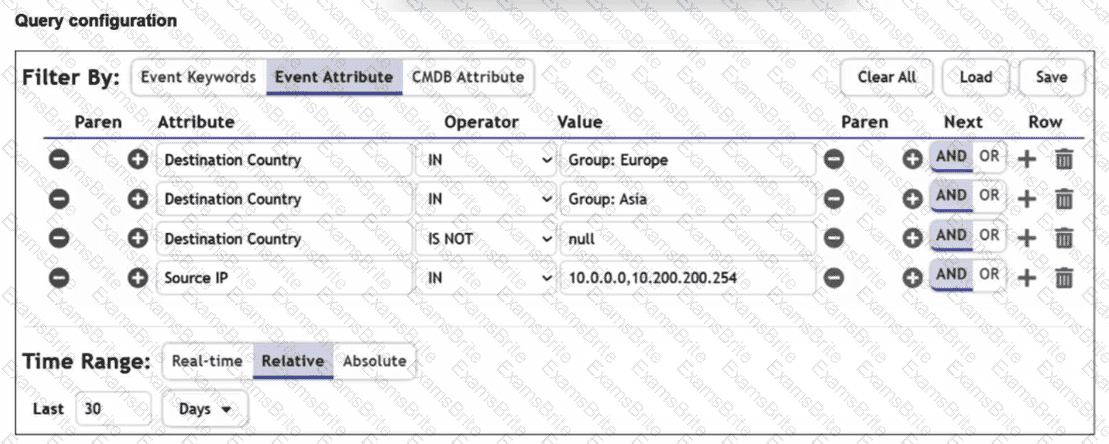
You are trying to find traffic flows to destinations that are in Europe or Asia, for hosts in the local LAN segment. However, the query returns no results. Assume these logs exist on FortiSIEM.
Which three mistakes can you see in the query shown in the exhibit? (Choose three answers)
Which three statements accurately describe step utilities in a playbook step? (Choose three answers)
You are trying to create a playbook that creates a manual task showing a list of public IPv6 addresses. You were successful in extracting all IP addresses from a previous action into a variable calledip_list, which contains both private and public IPv4 and IPv6 addresses. You must now filter the results to display only public IPv6 addresses. Which two Jinja expressions can accomplish this task? (Choose two answers)
When configuring a FortiAnalyzer to act as a collector device, which two steps must you perform? (Choose two.)
Which two best practices should be followed when exporting playbooks in FortiAnalyzer? (Choose two answers)
Refer to the exhibits.
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Refer to the Exhibit:
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
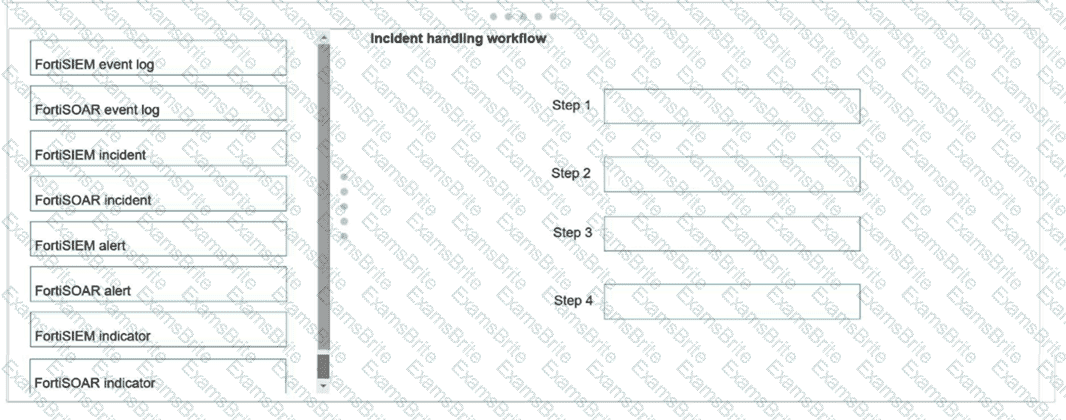
Using the default data ingestion wizard in FortiSOAR, place the incident handling workflow from FortiSIEM to FortiSOAR in the correct sequence. Select each workflow component in the left column, hold and drag it to a blank position in the column on the right. Place the four correct workflow components in order, placing the first step in the first position at the top of the column.
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Refer to the exhibits.
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three answers)
Refer to Exhibit:
A SOC analyst is designing a playbook to filter for a high severity event and attach the event information to an incident.
Which local connector action must the analyst use in this scenario?