
Fortinet NSE 7 - OT Security 7.2
Last Update Feb 28, 2026
Total Questions : 69
We are offering FREE NSE7_OTS-7.2 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE7_OTS-7.2 free exam questions and then go for complete pool of Fortinet NSE 7 - OT Security 7.2 test questions that will help you more.



Refer to the exhibit.
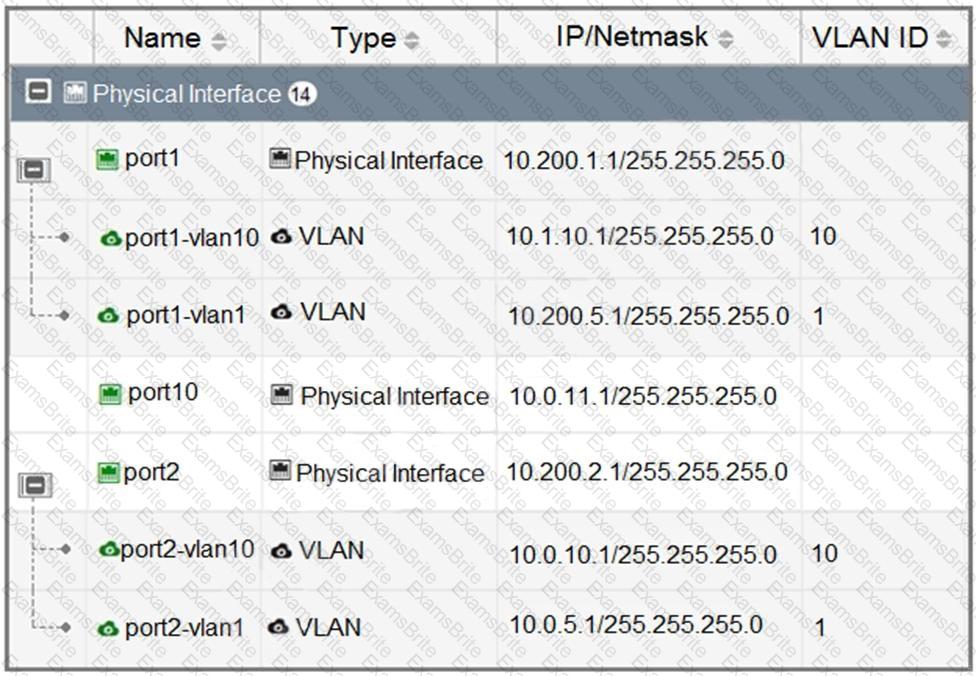
Which statement about the interfaces shown in the exhibit is true?
Refer to the exhibit.
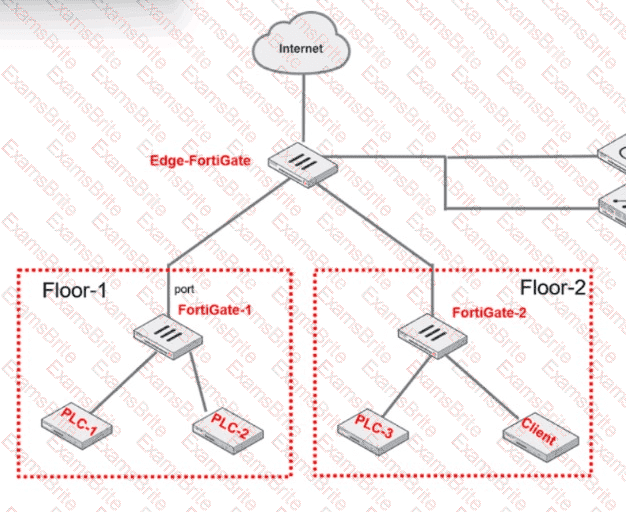
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2 level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
Refer to the exhibit.
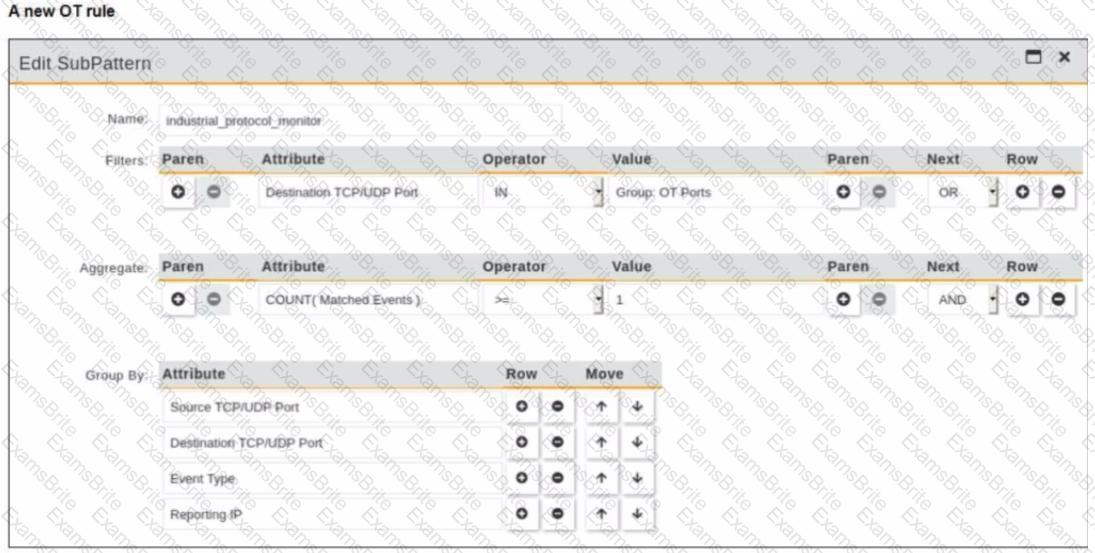
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
Refer to the exhibit and analyze the output.
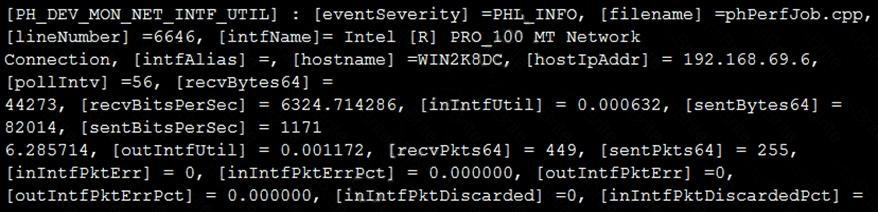
Which statement about the output is true?
How can you achieve remote access and internet availability in an OT network?
Refer to the exhibits.

Which statement is true about the traffic passing through to PLC-2?
Refer to the exhibit.
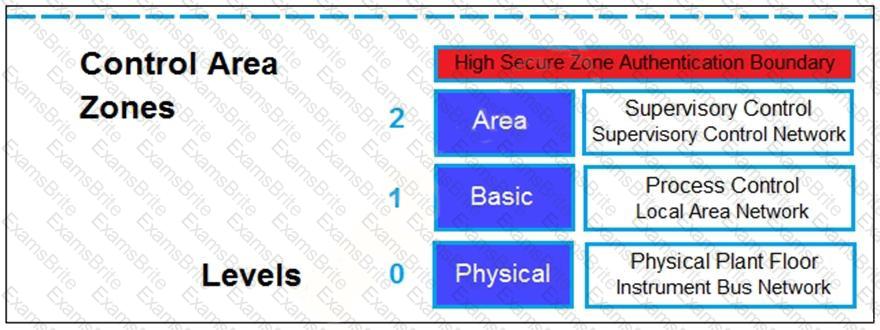
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric? (Choose three.)
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-party company while continuing to secure the ICS networks?
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
As an OT network administrator you are managing three FortiGate devices that each protect different levels on the Purdue model To increase traffic visibility you are required to implement additional security measures to detect protocols from PLCs
Which security sensor must you implement to detect protocols on the OT network?
Refer to the exhibit.
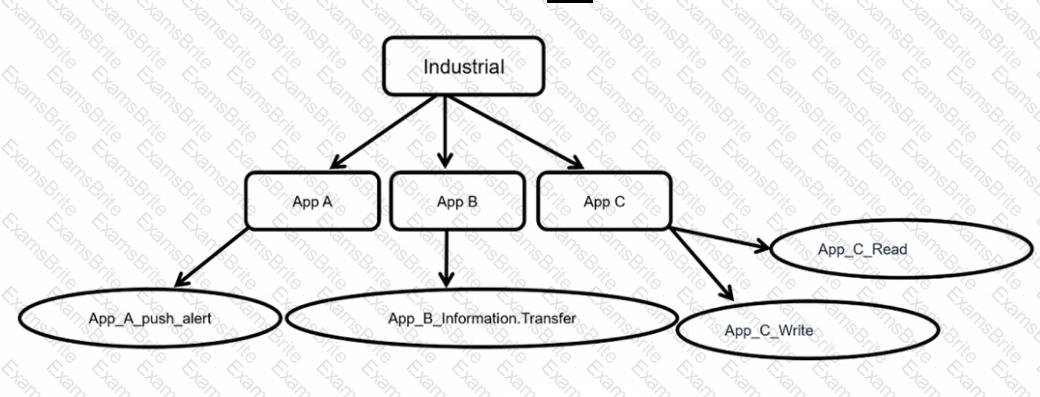
Which statement is true about application control inspection?
Refer to the exhibit.
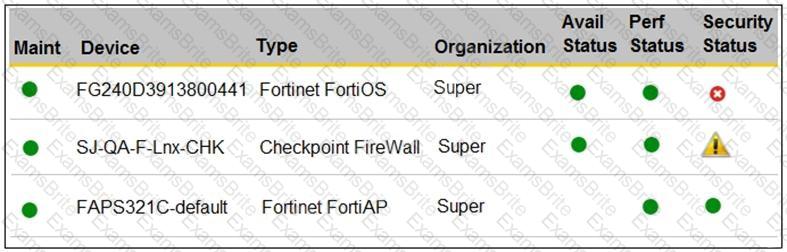
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
With the limit of using one firewall device, the administrator enables multi-VDOM on FortiGate to provide independent multiple security domains to each ICS network. Which statement ensures security protection is in place for all ICS networks?
Refer to the exhibit.
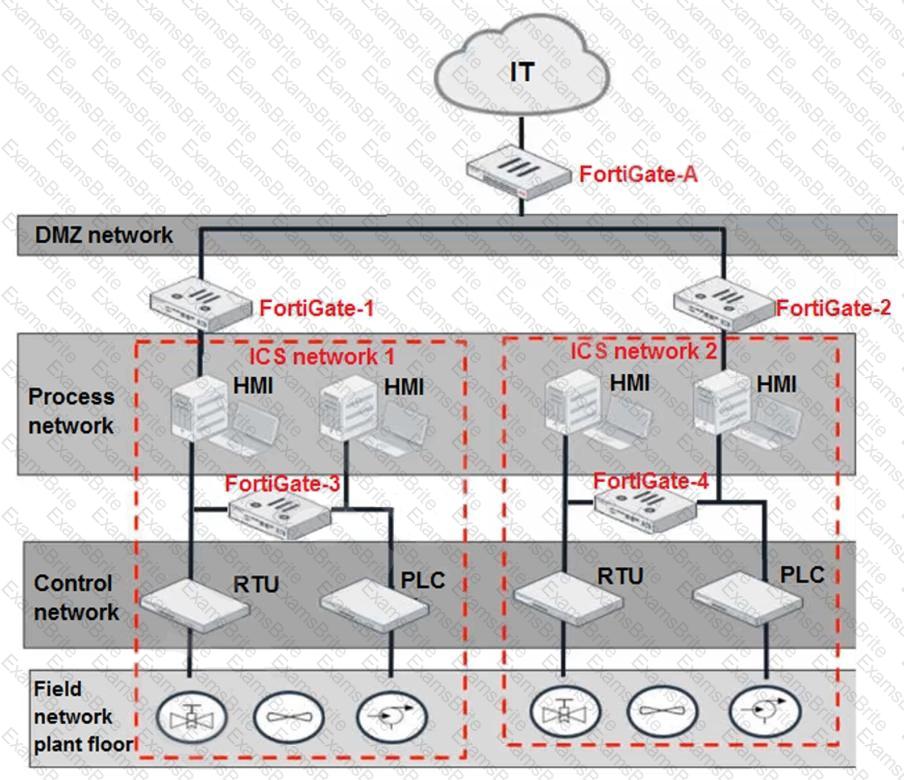
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Refer to the exhibit.
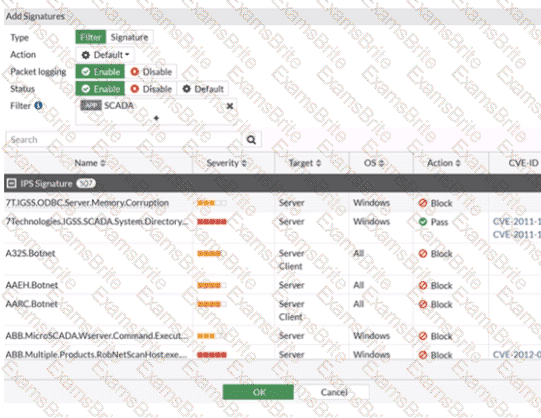
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?