
Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect
Last Update Mar 1, 2026
Total Questions : 54
We are offering FREE NSE7_CDS_AR-7.6 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE7_CDS_AR-7.6 free exam questions and then go for complete pool of Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect test questions that will help you more.



An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?
Refer to the exhibit.
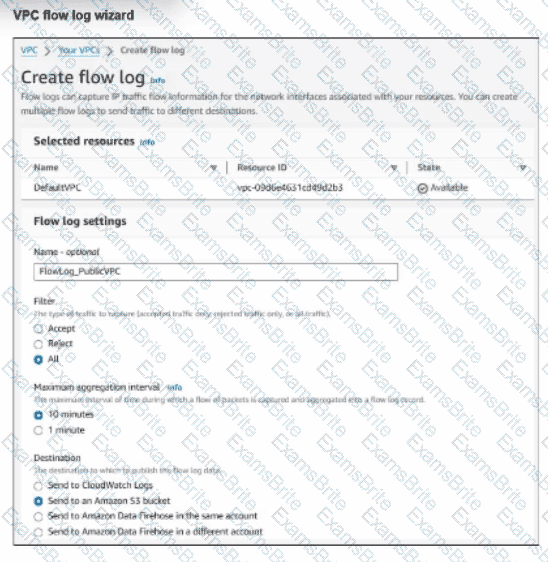
An experienced AWS administrator is creating a new virtual public cloud (VPC) flow log with the settings shown in the exhibit.
What is the purpose of this configuration?
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
Refer to the exhibit.
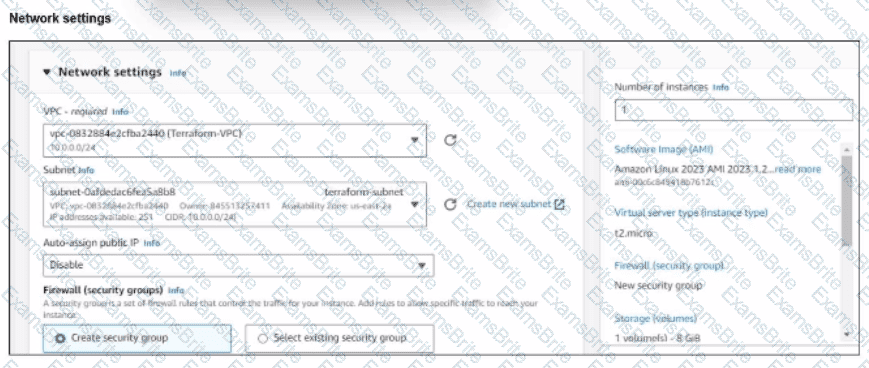
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit.
What next step must the administrator take to access this instance from the internet?
Refer to the exhibit.
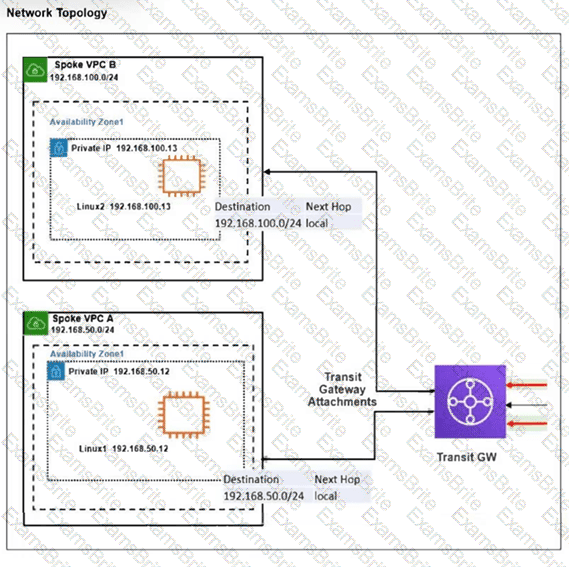
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments. Which two steps are required to route traffic from Linux instances to the TGW? (Choose two answers)
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
Refer to the exhibit.
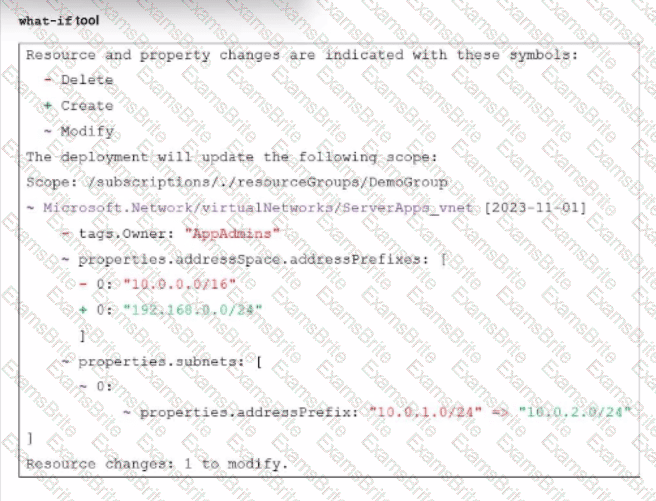
An administrator used the what-if tool to preview changes to an Azure Bicep file.
What will happen if the administrator decides to apply these changes in Azure?
Exhibit.
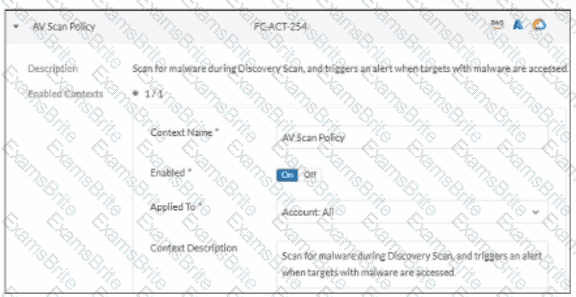
In which type of FortiCNP insights can an administrator examine the findings triggered by this policy?
How does an administrator secure container environments in Amazon AWS from newly emerged security threats? (Choose one answer)
Refer to the exhibit.
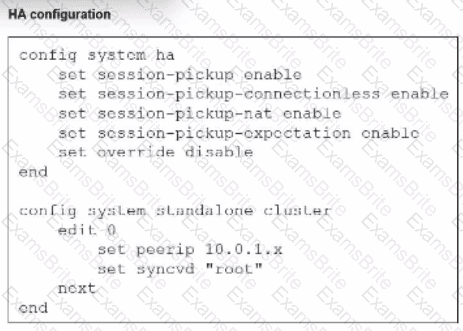
You deployed an HA active-active load balance sandwich with two FortiGate VMs in Microsoft Azure.
After the deployment, you prefer to use FGSP to synchronize sessions, and allow asymmetric return traffic. In the environment, FortiGate port 1 and port 2 are facing external and internal load balancers respectively.
What IP address must you use in the peerip configuration?
Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
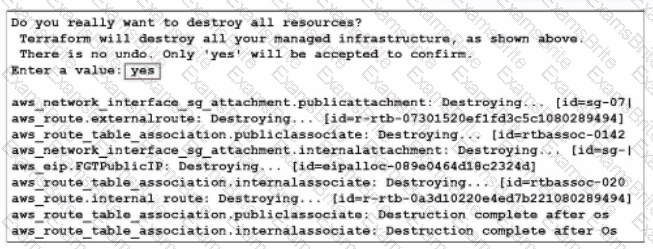
What would be the impact of confirming to delete all the resources in Terraform?
An administrator is trying to implement FortiCNP with Microsoft Azure Security integration. However, FortiCNP is not able to extract any cloud integration data from Azure; therefore, real-time cloud security monitoring is not possible.
What is causing this issue?
Refer to the exhibit.
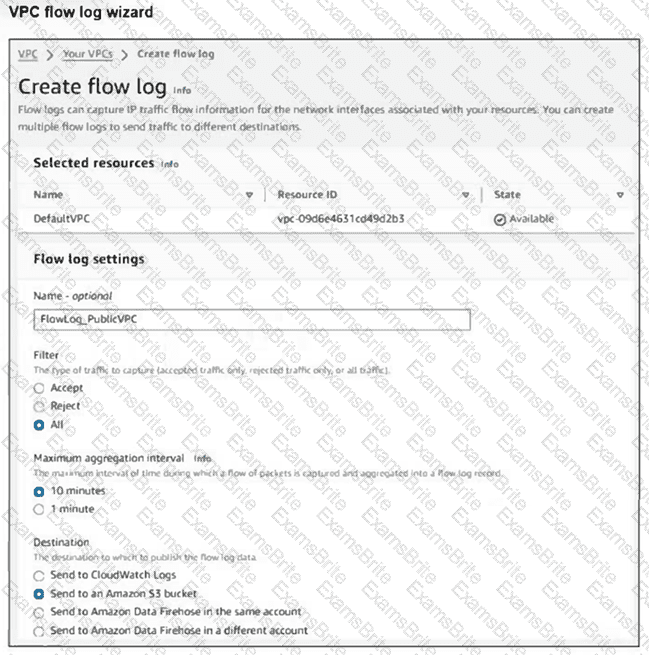
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)