
Fortinet NSE 4 - FortiOS 7.6 Administrator
Last Update Feb 13, 2026
Total Questions : 60
We are offering FREE NSE4_FGT_AD-7.6 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare NSE4_FGT_AD-7.6 free exam questions and then go for complete pool of Fortinet NSE 4 - FortiOS 7.6 Administrator test questions that will help you more.



Refer to the exhibits.
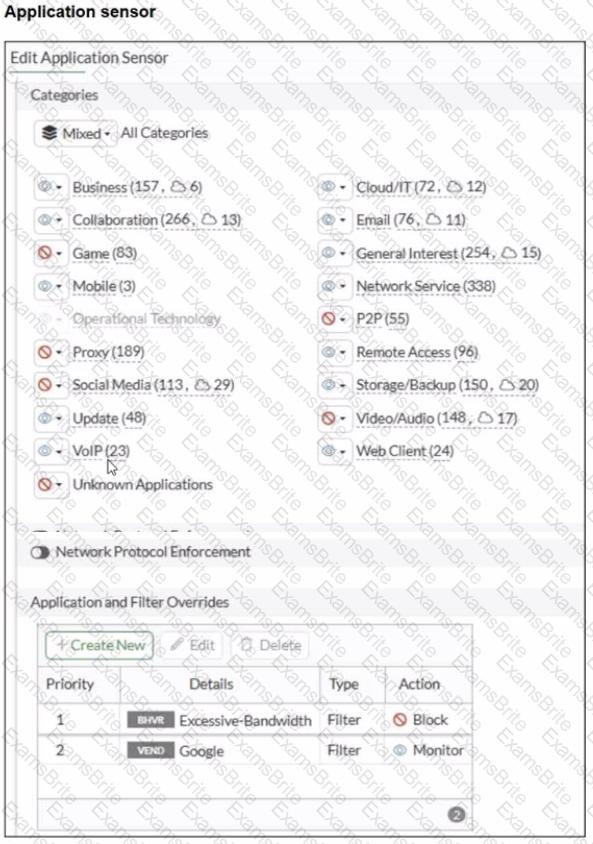
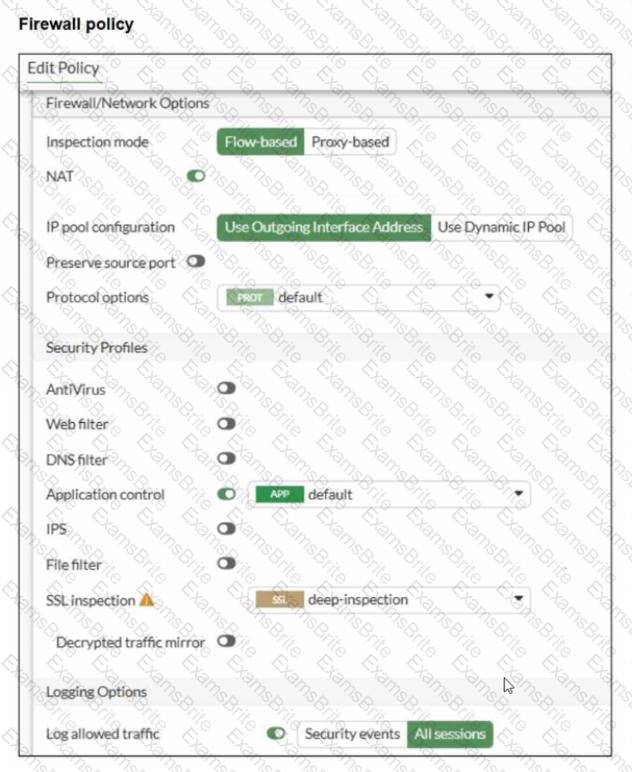
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
Refer to the exhibit
A firewall policy to enable active authentication is shown.
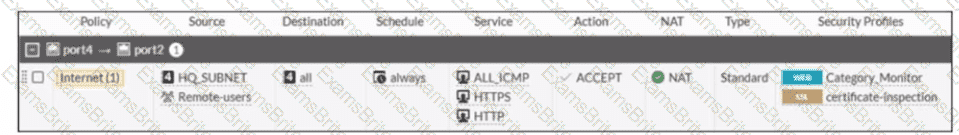
When attempting to access an external website using an active authentication method, the user is not presented with a login prompt. What is the most likely reason for this situation?
FortiGate is integrated with FortiAnalyzer and FortiManager.
When creating a firewall policy, which attribute must an administrator include to enhance functionality and enable log recording on FortiAnalyzer and FortiManager?
There are multiple dialup IPsec VPNs configured in aggressive mode on the HQ FortiGate. The requirement is to connect dial-up users to their respective department VPN tunnels.
Which phase 1 setting you can configure to match the user to the tunnel?
Refer to the exhibit.
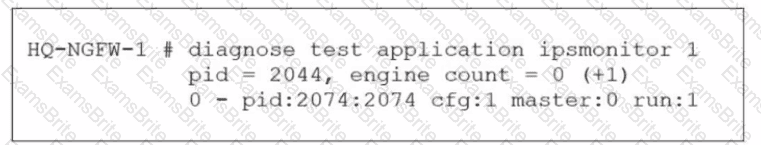
As an administrator you have created an IPS profile, but it is not performing as expected. While testing you got the output as shown in the exhibit What could be the possible reason of the diagnose output shown in the exhibit?
Refer to the exhibit.
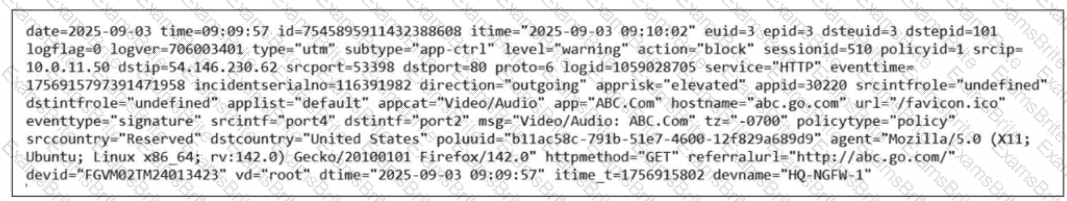
Which two ways can you view the log messages shown in the exhibit? (Choose two.)
Refer to the exhibit.
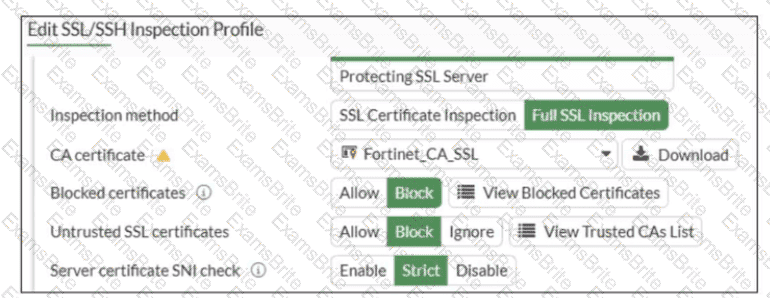
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
What are two characteristics of HA cluster heartbeat IP addresses in a FortiGate device? (Choose two.)
Refer to the exhibit.
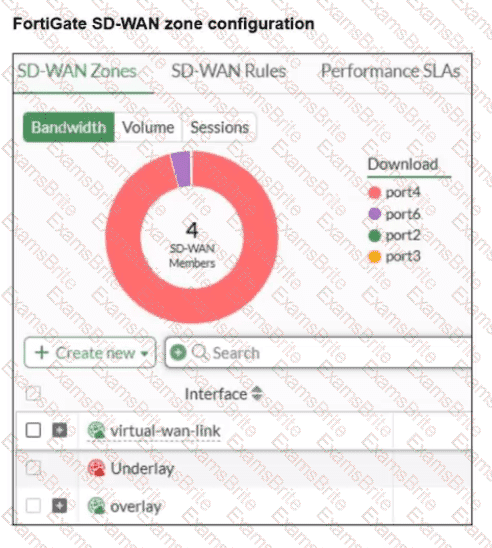
An SD-WAN zone configuration on the FortiGate GUI is shown. Based on the exhibit, which statement is true?
Refer to the exhibit.
A RADIUS server configuration is shown.
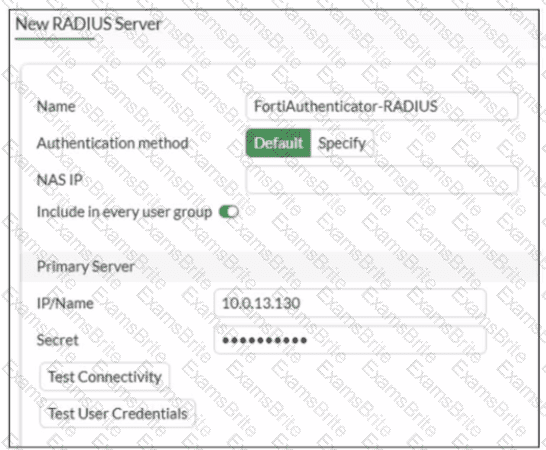
An administrator added a configuration for a new RADIUS server While configuring, the administrator enabled Include in every user group What is the impact of enabling Include in every user group in a RADIUS configuration?
Refer to the exhibit.
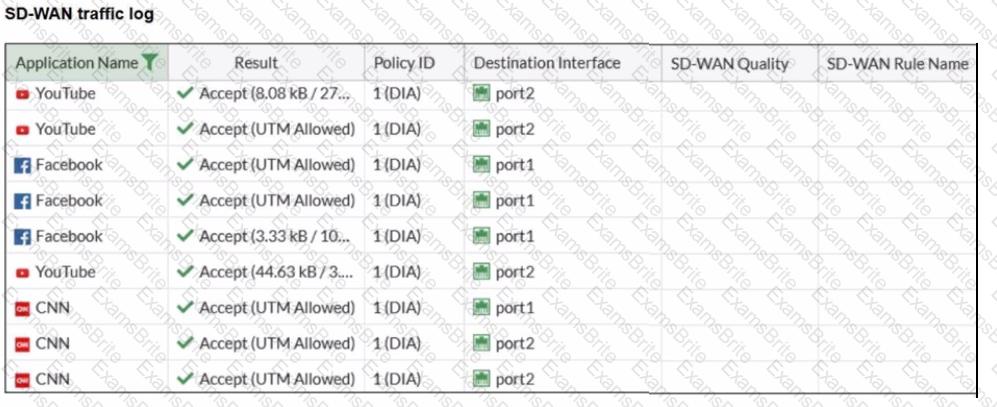
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name
FortiGate allows the traffic according to policy ID 1 placed at the top. This is the policy that allows SD-WAN traffic. Despite these settings, the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows
What could be the reason?
Refer to the exhibits.
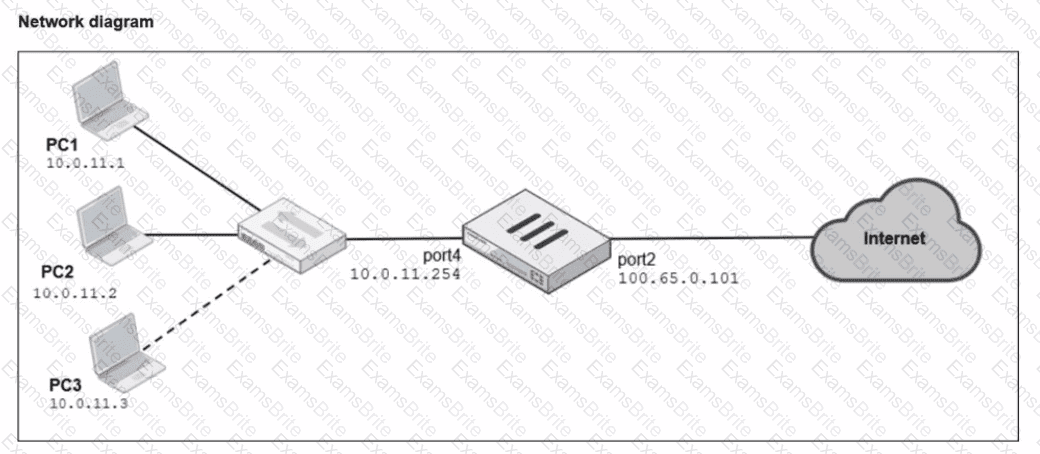
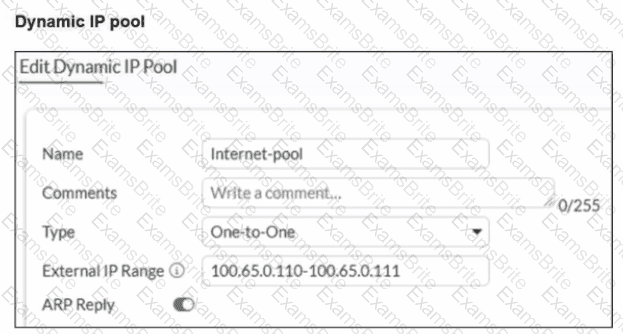
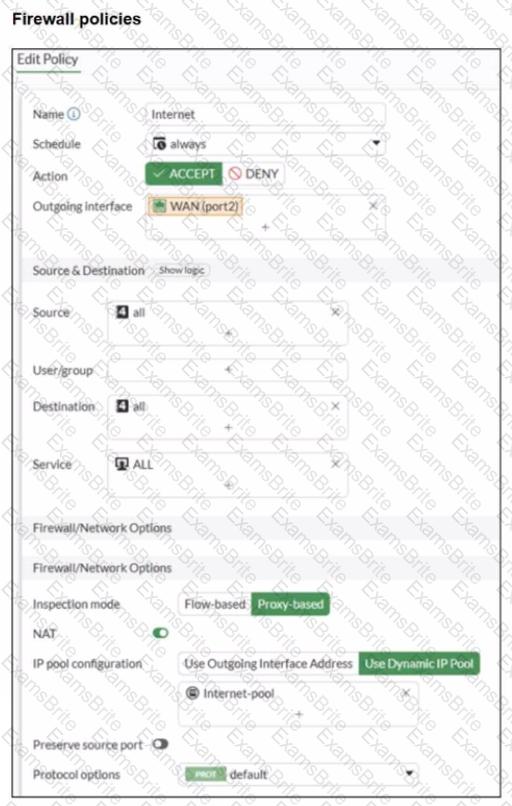
A diagram of a FortiGate device connected to the network, as well as the firewall policy and IP pool configuration on the FortiGate device are shown.
Two PCs. PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
Based on the information shown in the exhibit, which two configuration options can the administrator use to fix the connectivity issue for PC3? (Choose two.)
Refer to the exhibits.
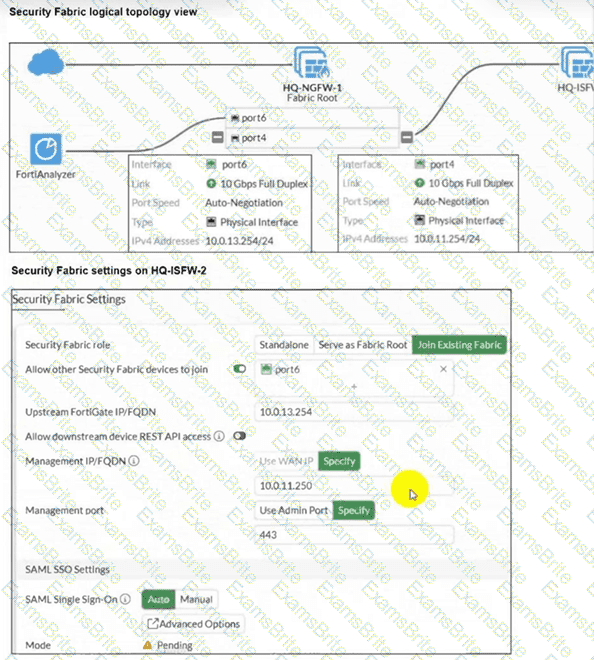
An administrator wants to add HQ-ISFW-2 in the Security Fabric. HQ-ISFW-2 is in the same subnet as HQ-ISFW. After configuring the Security Fabric settings on HQ-ISFW-2, the status stays Pending. What can be the two possible reasons? (Choose two answers)
Refer to the exhibits.
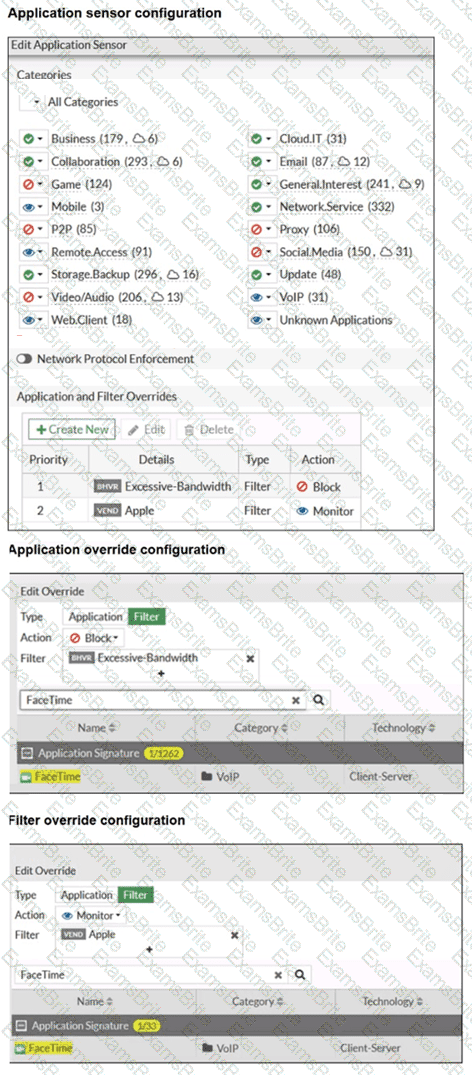
The exhibits show the application sensor configuration and the Excessive-Bandwidth and Apple filter details. Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming? (Choose one answer)
A new administrator is configuring FSSO authentication on FortiGate using DC Agent Mode. Which step is not part of the expected process?
You have configured an application control profile, set peer-to-peer traffic to Block under the Categories tab. and applied it to the firewall policy. However, your peer-to-peer traffic on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)