
Security, Professional (JNCIP-SEC)
Last Update Feb 28, 2026
Total Questions : 115
We are offering FREE JN0-637 Juniper exam questions. All you do is to just go and sign up. Give your details, prepare JN0-637 free exam questions and then go for complete pool of Security, Professional (JNCIP-SEC) test questions that will help you more.



You are deploying a large-scale VPN spanning six sites. You need to choose a VPN technology that satisfies the following requirements:
All sites must have secure reachability to all other sites.
New spoke sites can be added without explicit configuration on the hub site.
All spoke-to-spoke communication must traverse the hub site.Which VPN technology will satisfy these requirements?
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
Exhibit:
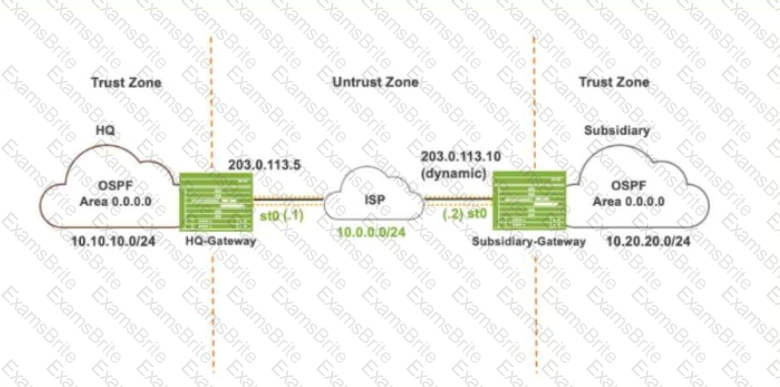
Referring to the exhibit, which IKE mode will be configured on the HQ-Gateway and Subsidiary-Gateway?
Which two statements about transparent mode and Ethernet switching mode on an SRX series
device are correct.
You have deployed automated threat mitigation using Security Director with Policy Enforcer, Juniper ATP Cloud, SRX Series devices, Forescout, and third-party switches.
In this scenario, which device is responsible for communicating directly to the third-party switches when infected hosts need to be blocked?
You need to set up source NAT so that external hosts can initiate connections to an internal device, but only if a connection to the device was first initiated by the internal device.
Which type of NAT solution provides this functionality?
Click the Exhibit button.

You have configured a CoS-based VPN that is not functioning correctly.
Referring to the exhibit, which action will solve the problem?
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
Exhibit:
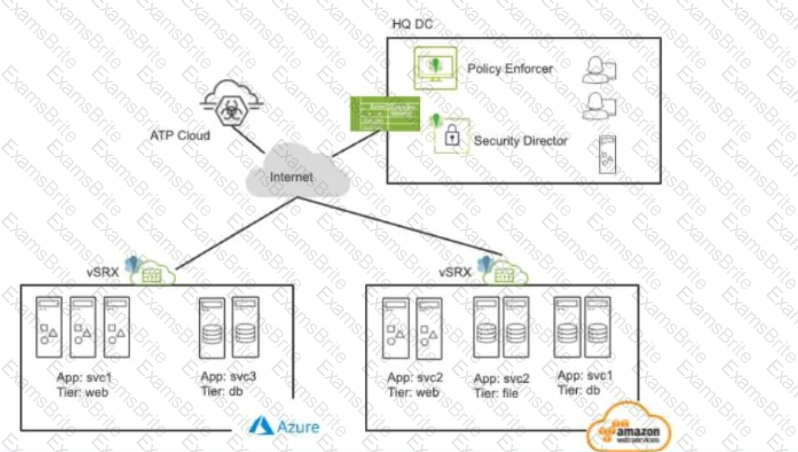
Referring to the exhibit, what do you use to dynamically secure traffic between the Azure and AWS clouds?
You want to use a security profile to limit the system resources allocated to user logical systems.
In this scenario, which two statements are true? (Choose two.)
Exhibit:

Your company uses SRX Series devices to establish an IPsec VPN that connects Site-1 and the HQ networks. You want VoIP traffic to receive priority over data traffic when it is forwarded across the VPN.
Which three actions should you perform in this scenario? (Choose three.)
You want to create a connection for communication between tenant systems without using physical revenue ports on the SRX Series device.
What are two ways to accomplish this task? (Choose two.)
Exhibit:
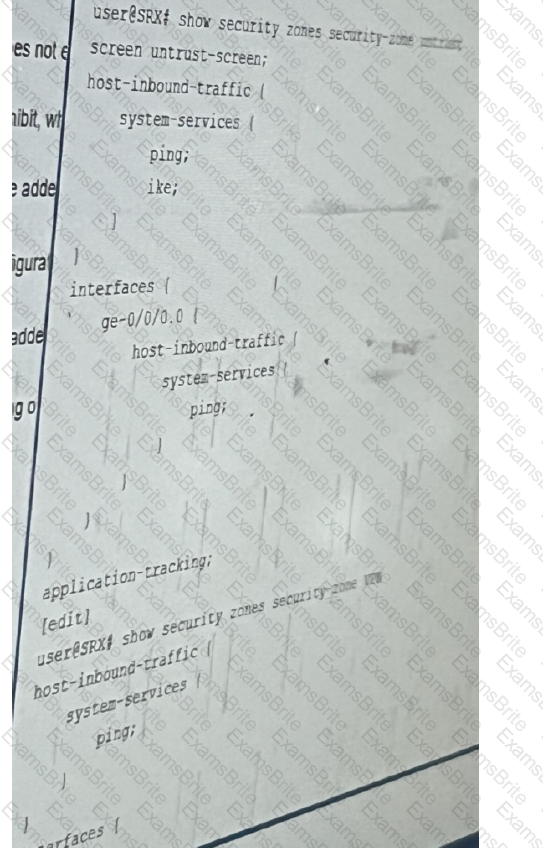
The Ipsec VPN does not establish when the peer initiates, but it does establish when the SRX
series device initiates. Referring to the exhibit, what will solve this problem?
Referring to the exhibit,
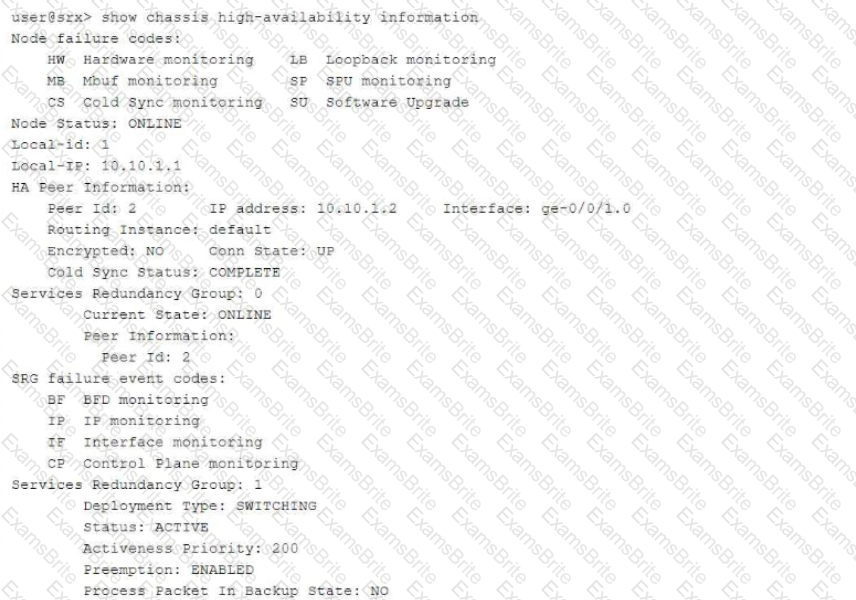
which three statements about the multinode HA environment are true? (Choose three.)
You are asked to establish IBGP between two nodes, but the session is not established. To troubleshoot this problem, you configured trace options to monitor BGP protocol message exchanges.

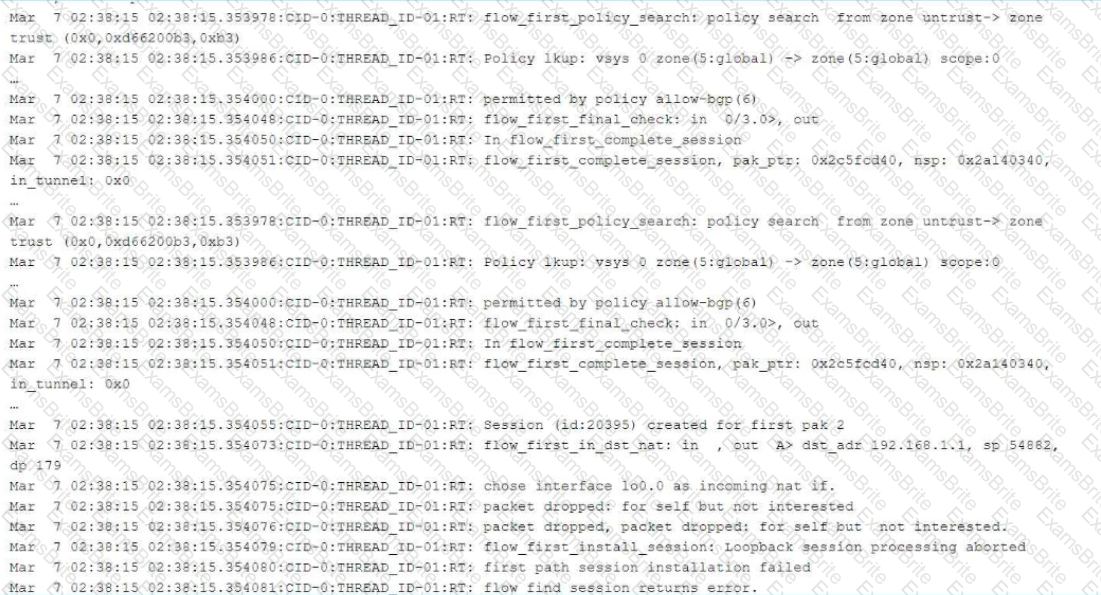
Referring to the exhibit, which action would solve the problem?
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
You have deployed a new site as shown in the exhibit. Hosts in the 10.10.10.0/24 network
must access the DB1 server. The DB1 server must also have internet access the DB1 server encrypted.
Which two configuration statements will be required as part of the configuration on SRX1 to satisfy this requirement? (Choose two)
You have deployed an SRX Series device at your network edge to secure Internet-bound sessions for your local hosts using source NAT. You want to ensure that your users are able to interact with applications on the Internet that require more than one TCP session for the same application session.
Which two features would satisfy this requirement? (Choose two.)
Exhibit:
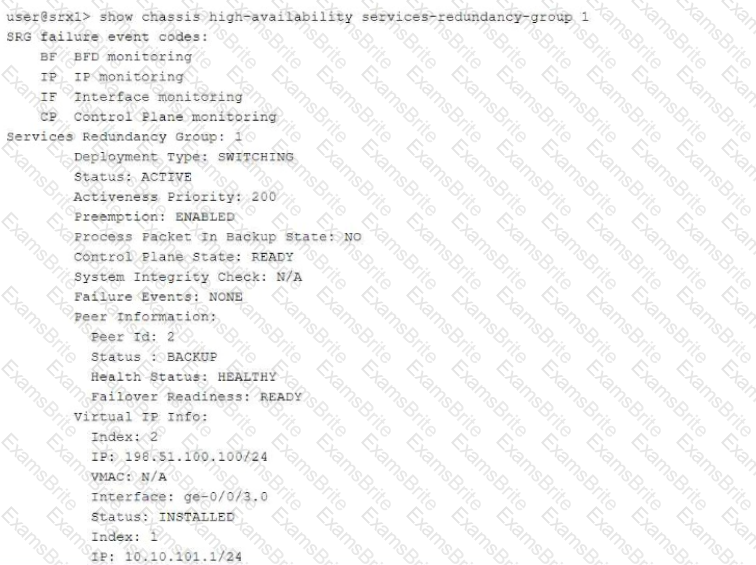
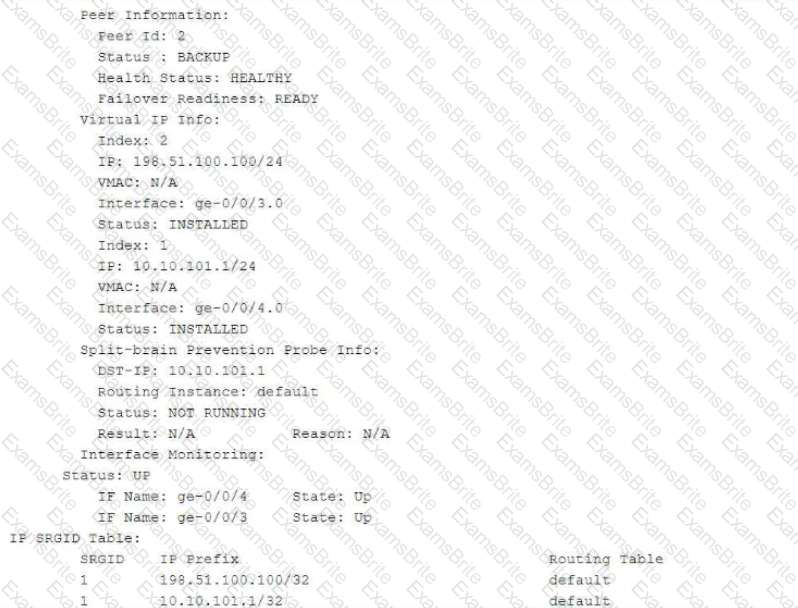
Referring to the exhibit, which two statements are correct? (Choose two.)
You are experiencing problem with your ADVPN tunnels getting established. The tunnel
and egress interface are located in different zone. What are two reasons for these problems? (Choose two.)
You are asked to connect two hosts that are directly connected to an SRX Series device. The traffic should flow unchanged as it passes through the SRX, and routing or switch lookups should not be performed. However, the traffic should still be subjected to security policy checks.
What will provide this functionality?
You are attempting to ping the IP address that is assigned to the loopback interface on the
SRX series device shown in the exhibit.
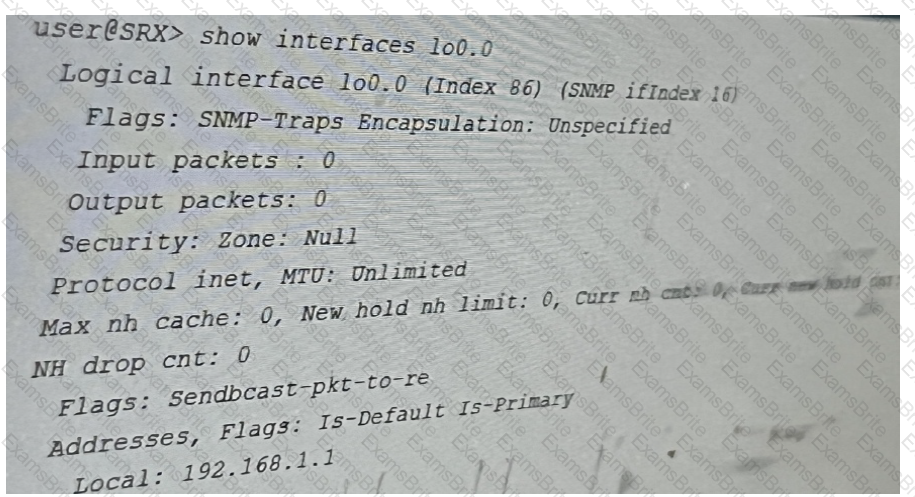
What is causing this problem?
You have deployed two SRX Series devices in an active/passive multimode HA scenario.
In this scenario, which two statements are correct? (Choose two.)
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
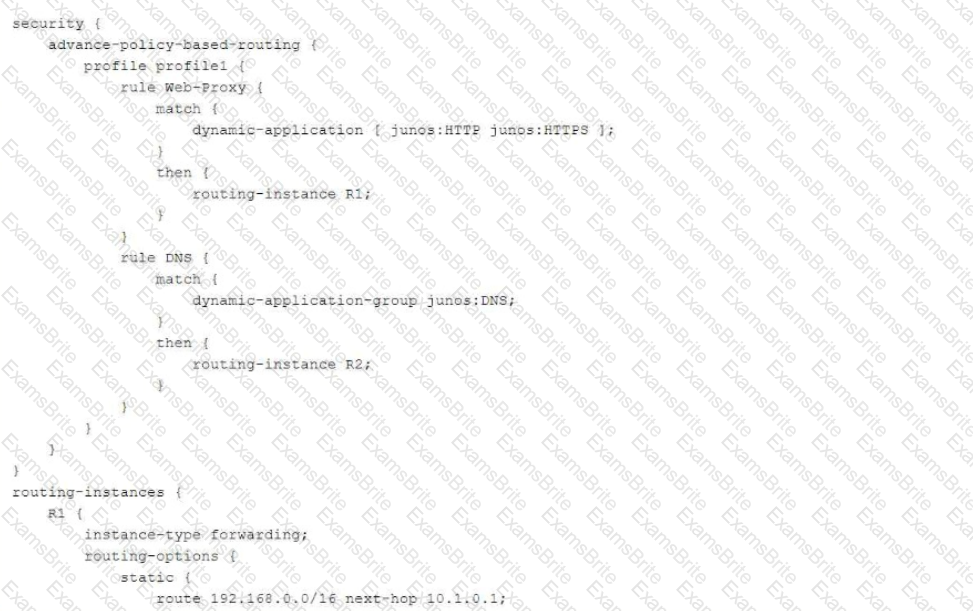
You are enabling advanced policy-based routing. You have configured a static route that has a next hop from the inet.0 routing table. Unfortunately, this static route is not active in your routing instance.
In this scenario, which solution is needed to use this next hop?
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
You are asked to select a product offered by Juniper Networks that can collect and assimilate data from all probes and determine the optimal links for different applications to maximize the full potential of AppQoE.
Which product provides this capability?
Which two statements describe the behavior of logical systems? (Choose two.)
Referring to the exhibit,
which statement about TLS 1.2 traffic is correct?
Exhibit:

You have configured a CoS-based VPN that is not functioning correctly.
Referring to the exhibit, which action will solve the problem?
What are three requirements to run OSPF over GRE over IPsec? (Choose Three)
A customer wants to be able to initiate a return connection to an internal host from a specific
Server.
Which NAT feature would you use in this scenario?