
Security, Associate (JNCIA-SEC)
Last Update Feb 28, 2026
Total Questions : 65
We are offering FREE JN0-232 Juniper exam questions. All you do is to just go and sign up. Give your details, prepare JN0-232 free exam questions and then go for complete pool of Security, Associate (JNCIA-SEC) test questions that will help you more.



Which two statements about global security policies are correct? (Choose two.)
You want to verify the effectiveness of Web filtering on the SRX Series Firewall.
How would you accomplish this task?
Content filtering supports which two of the following protocols? (Choose two.)
Click the Exhibit button.

Referring to the exhibit, which two statements are correct about the traffic flow shown in the exhibit? (Choose two.)
What are two system-defined zones created on the SRX Series Firewalls? (Choose two.)
Which two characteristics of destination NAT and static NAT are correct? (Choose two.)
When traffic enters an interface, which two results does a route lookup determine? (Choose two.)
Which statement is correct about capturing transit packets on an SRX Series Firewall?
What must also be enabled when using source NAT if the address pool is in the same subnet as the interface?
Which two statements about the host-inbound-traffic parameter in a zone configuration are correct? (Choose two.)
You have a situation where legitimate traffic is incorrectly identified as malicious by your screen options.
In this scenario, what should you do?
Which two statements are correct about the processing of NAT rules within a rule set? (Choose two.)
You are modifying the NAT rule order and you notice that a new NAT rule has been added to the bottom of the list.
In this situation, which command would you use to reorder NAT rules?
Click the Exhibit button.
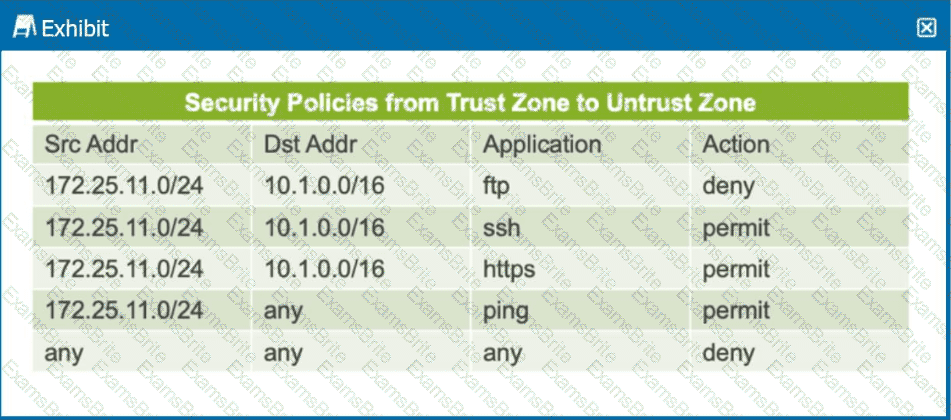
The exhibit shows a table representing security policies from the trust zone to the untrust zone.
In this scenario, which two statements are correct? (Choose two.)
Click the Exhibit button.

Referring to the exhibit, which two statements are correct? (Choose two.)
Your company is acquiring a smaller company that uses the same private address range that your company currently uses in its North America division. You have a limited number of public IP addresses to use for the acquisition. You want to allow the new acquisition's users to connect to the existing services in North America.
Which two features would you enable on your SRX Series Firewall to accomplish this task? (Choose two.)
Click the Exhibit button.
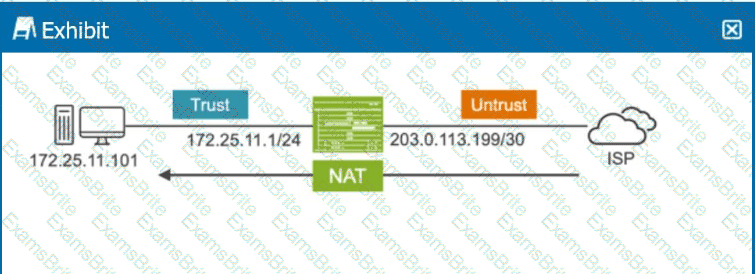
You must ensure that sessions can only be established from the external device.
Referring to the exhibit, which type of NAT is being performed?