PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Last Update Feb 28, 2026
Total Questions : 418
We are offering FREE ISO-IEC-27001-Lead-Auditor PECB exam questions. All you do is to just go and sign up. Give your details, prepare ISO-IEC-27001-Lead-Auditor free exam questions and then go for complete pool of PECB Certified ISO/IEC 27001 2022 Lead Auditor exam test questions that will help you more.



Scenario 2:
Clinic, founded in the 1990s, is a medical device company that specializes in treatments for heart-related conditions and complex surgical interventions. Based in Europe, it serves both patients and healthcare professionals. Clinic collects patient data to tailor treatments, monitor outcomes, and improve device functionality. To enhance data security and build trust, Clinic is implementing an information security management system (ISMS) based on ISO/IEC 27001. This initiative demonstrates Clinic's commitment to securely managing sensitive patient information and proprietary technologies.
Clinic established the scope of its ISMS by solely considering internal issues, interfaces, dependencies between internal and outsourced activities, and the expectations of interested parties. This scope was carefully documented and made accessible. In defining its ISMS, Clinic chose to focus specifically on key processes within critical departments such as Research and Development, Patient Data Management, and Customer Support.
Despite initial challenges, Clinic remained committed to its ISMS implementation, tailoring security controls to its unique needs. The project team excluded certain Annex A controls from ISO/IEC 27001 while incorporating additional sector-specific controls to enhance security. The team evaluated the applicability of these controls against internal and external factors, culminating in the development of a comprehensive Statement of Applicability (SoA) detailing the rationale behind control selection and implementation.
As preparations for certification progressed, Brian, appointed as the team leader, adopted a self-directed risk assessment methodology to identify and evaluate the company’s strategic issues and security practices. This proactive approach ensured that Clinic’s risk assessment aligned with its objectives and mission.
Question:
According to Scenario 2, was the scope of Clinic’s ISMS determined correctly?
Which one of the following options describes the main purpose of a Stage 1 audit?
To determine readiness for Stage 2
Question
An organization scheduled an internal audit to evaluate the ISMS effectiveness. However, it did not define the audit scope and clear audit objectives. As a result, the internal auditor overlooked critical departments handling sensitive information.
What risk associated with the audit program was present in this scenario?
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services.
The next step in your audit plan is to verify the information security on ABC's healthcare mobile app
development, support, and lifecycle process. During the audit, you learned the organization outsourced the
mobile app development to a professional software development company with CMMI Level 5, ITSM (ISO/IEC
20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified. The IT Manager presented the software
security management procedure and summarised the process as follows:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a
minimum. The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report - details as follows:
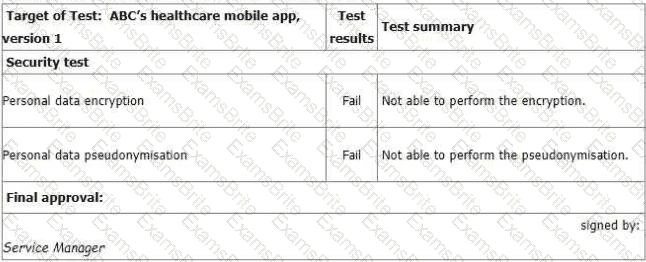
You ask the IT Manager why the organisation still uses the mobile app while personal data
encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to
approve the test.
The IT Manager explains the test results should be approved by him according to the software
security management procedure. The reason why the encryption and pseudonymization functions
failed is that these functions heavily slowed down the system and service performance. An extra
150% of resources are needed to cover this. The Service Manager agreed that access control is
good enough and acceptable. That's why the Service Manager signed the approval.
You sample one of the medical staff's mobile and found that ABC's healthcare mobile app, version
1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app
development company gave a free minor update on the tested software, performed an emergency
release of the updated software, and gave a verbal guarantee that there will be no impact on any
security functions. Based on his 20 years of information security experience, there is no need to re-
test.
You are preparing the audit findings Select two options that are correct.
Question:
During which stage of the audit do auditors identify key processes to be audited and prioritize based on materiality?
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
Should the auditor archive the copies of employee training records after the completion of the audit? Refer to scenario 7.
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
What factor did the audit team primarily consider when evaluating the reliability of evidence during the audit process? Refer to Scenario 4.
Scenario 1: Fintive is a distinguished security provider for online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive
offers services to companies that operate online and want to improve their information security, prevent fraud, and protect user information such as PII. Fintive centers
its decision-making and operating process based on previous cases. They gather customer data, classify them depending on the case, and analyze them. The company
needed a large number of employees to be able to conduct such complex analyses. After some years, however, the technology that assists in conducting such analyses
advanced as well. Now, Fintive is planning on using a modern tool, a chatbot, to achieve pattern analyses toward preventing fraud in real-time. This tool would also be
used to assist in improving customer service.
This initial idea was communicated to the software development team, who supported it and were assigned to work on this project. They began integrating the chatbot
on their existing system. In addition, the team set an objective regarding the chatbot which was to answer 85% of all chat queries.
After the successful integration of the chatbot, the company immediately released it to their customers for use. The chatbot, however, appeared to have some issues.
Due to insufficient testing and lack of samples provided to the chatbot during the training phase, in which it was supposed "to learn" the queries pattern, the chatbot
failed to address user queries and provide the right answers. Furthermore, the chatbot sent random files to users when it received invalid inputs such as odd patterns
of dots and special characters. Therefore, the chatbot was unable to properly answer customer queries and the traditional customer support was overwhelmed with
chat queries and thus was unable to help customers with their requests.
Consequently, Fintive established a software development policy. This policy specified that whether the software is developed in-house or outsourced, it will undergo a
black box testing prior to its implementation on operational systems.
Based on this scenario, answer the following question:
Based on scenario 1, the chatbot was unable to properly answer customer queries. Which principle of information security has been affected in this
case?
An organisation is looking for management system initial certification. Please identify the sequence of the activities to be undertaken by the organisation.
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank section.

Scenario 2:
Clinic, founded in the 1990s, is a medical device company that specializes in treatments for heart-related conditions and complex surgical interventions. Based in Europe, it serves both patients and healthcare professionals. Clinic collects patient data to tailor treatments, monitor outcomes, and improve device functionality. To enhance data security and build trust, Clinic is implementing an information security management system (ISMS) based on ISO/IEC 27001. This initiative demonstrates Clinic's commitment to securely managing sensitive patient information and proprietary technologies.
Clinic established the scope of its ISMS by solely considering internal issues, interfaces, dependencies between internal and outsourced activities, and the expectations of interested parties. This scope was carefully documented and made accessible. In defining its ISMS, Clinic chose to focus specifically on key processes within critical departments such as Research and Development, Patient Data Management, and Customer Support.
Despite initial challenges, Clinic remained committed to its ISMS implementation, tailoring security controls to its unique needs. The project team excluded certain Annex A controls from ISO/IEC 27001 while incorporating additional sector-specific controls to enhance security. The team evaluated the applicability of these controls against internal and external factors, culminating in the development of a comprehensive Statement of Applicability (SoA) detailing the rationale behind control selection and implementation.
As preparations for certification progressed, Brian, appointed as the team leader, adopted a self-directed risk assessment methodology to identify and evaluate the company’s strategic issues and security practices. This proactive approach ensured that Clinic’s risk assessment aligned with its objectives and mission.
Question:
Based on Scenario 2, Clinic initially defined its information security objectives and then conducted a risk assessment. Is this acceptable?
During a third-party certification audit you are presented with a list of issues by an auditee. Which four of the following constitute 'external' issues in the context of a management system to ISO/IEC 27001:2022?
Which one of the following options is the definition of an interested party?
A third party can appeal to an organisation when it perceives itself to be affected by a decision or activity
You have to carry out a third-party virtual audit. Which two of the following issues would you need to inform the auditee about before you start conducting the audit ?
You will ask to see the ID card of the person that is on the screen.
Scenario 3: NightCore is a multinational technology company based in the United States that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence. After having an information security management system (ISMS) implemented for over 8 months, they contracted a certification body to conduct a third party audit in order to get certified against ISO/IEC 27001.
The certification body set up a team of seven auditors. Jack, the most experienced auditor, was assigned as the audit team leader. Over the years, he received many well known certifications, such as the ISO/IEC 27001 Lead Auditor, CISA, CISSP, and CISM.
Jack conducted thorough analyses on each phase of the ISMS audit, by studying and evaluating every information security requirement and control that was implemented by NightCore. During stage 2 audit. Jack detected several nonconformities. After comparing the number of purchased invoices for software licenses with the software inventory, Jack found out that the company has been using the illegal versions of a software for many computers. He decided to ask for an explanation from the top management about this nonconformity and see whether they were aware about this. His next step was to audit NightCore's IT Department. The top management assigned Tom, NightCore's system administrator, to act as a guide and accompany Jack and the audit team toward the inner workings of their system and their digital assets infrastructure.
While interviewing a member of the Department of Finance, the auditors discovered that the company had recently made some unusual large transactions to one of their consultants. After gathering all the necessary details regarding the transactions. Jack decided to directly interview the top management.
When discussing about the first nonconformity, the top management told Jack that they willingly decided to use a copied software over the original one since it was cheaper. Jack explained to the top management of NightCore that using illegal versions of software is against the requirements of ISO/IEC 27001 and the national laws and regulations. However, they seemed to be fine with it.
Several months after the audit, Jack sold some of NightCore's information that he collected during the audit for a huge amount of money to competitors of NightCore.
Based on this scenario, answer the following question:
What type of audit evidence has Jack collected when he identified the first nonconformity regarding the software? Refer to scenario 3.
Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life insurance. The company was founded in North Carolina, but have recently expanded in other locations, including Europe and Africa.
Sinvestment is committed to complying with laws and regulations applicable to their industry and preventing any information security incident. They have implemented an ISMS based on ISO/IEC 27001 and have applied for ISO/IEC 27001 certification.
Two auditors were assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment. they started the audit activities. First, they reviewed the documentation required by the standard, including the declaration of the ISMS scope, information security policies, and internal audits reports. The review process was not easy because, although Sinvestment stated that they had a documentation procedure in place, not all documents had the same format.
Then, the audit team conducted several interviews with Sinvestment's top management to understand their role in the ISMS implementation. All activities of the stage 1 audit were performed remotely, except the review of documented information, which took place on-site, as requested by Sinvestment.
During this stage, the auditors found out that there was no documentation related to information security training and awareness program. When asked, Sinvestment's representatives stated that the company has provided information security training sessions to all employees. Stage 1 audit gave the audit team a general understanding of Sinvestment's operations and ISMS.
The stage 2 audit was conducted three weeks after stage 1 audit. The audit team observed that the marketing department (which was not included in the audit scope) had no procedures in place to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the information security policy of the company, the issue was included in the audit report. In addition, during stage 2 audit, the audit team observed that Sinvestment did not record logs of user activities. The procedures of the company stated that "Logs recording user activities should be retained and regularly reviewed," yet the company did not present any evidence of the implementation of such procedure.
During all audit activities, the auditors used observation, interviews, documented information review, analysis, and technical verification to collect information and evidence. All the audit findings during stages 1 and 2 were analyzed and the audit team decided to issue a positive recommendation for certification.
Based on scenario 6, during stage 1 audit, the auditor found out that some documents regarding the ISMS had different format. What should the auditor do in this case?
Scenario 6: Cyber ACrypt is a cybersecurity company that provides endpoint protection by offering anti-malware and device security, asset life cycle management, and device encryption. To validate its ISMS against ISO/IEC 27001 and demonstrate its commitment to cybersecurity excellence, the company underwent a meticulous audit process led by John, the appointed audit team leader.
Upon accepting the audit mandate, John promptly organized a meeting to outline the audit plan and team roles This phase was crucial for aligning the team with the audit's objectives and scope However, the initial presentation to Cyber ACrypt’s staff revealed a significant gap in understanding the audit's scope and objectives, indicating potential readiness challenges within the company
As the stage 1 audit commenced, the team prepared for on-site activities. They reviewed Cyber ACrypt's documented information, including the information security policy and operational procedures ensuring each piece conformed to and was standardized in format with author identification, production date, version number, and approval date Additionally, the audit team ensured that each document contained the information required by the respective clause of the standard This phase revealed that a detailed audit of the documentation describing task execution was unnecessary, streamlining the process and focusing the team's efforts on critical areas During the phase of conducting on-site activities, the team evaluated management responsibility for the Cyber Acrypt's policies This thorough examination aimed to ascertain continual improvement and adherence to ISMS requirements Subsequently, in the document, the stage 1 audit outputs phase, the audit team meticulously documented their findings, underscoring their conclusions regarding the fulfillment of the stage 1 objectives. This documentation was vital for the audit team and Cyber ACrypt to understand the preliminary audit outcomes and areas requiring attention.
The audit team also decided to conduct interviews with key interested parties. This decision was motivated by the objective of collecting robust audit evidence to validate the management system’s compliance with ISO/IEC 27001 requirements. Engaging with interested parties across various levels of Cyber ACrypt provided the audit team with invaluable perspectives and an understanding of the ISMS's implementation and effectiveness.
The stage 1 audit report unveiled critical areas of concern. The Statement of Applicability (SoA) and the ISMS policy were found to be lacking in several respects, including insufficient risk assessment, inadequate access controls, and lack of regular policy reviews. This prompted Cyber ACrypt to take immediate action to address these shortcomings. Their prompt response and modifications to the strategic documents reflected a strong commitment to achieving compliance.
The technical expertise introduced to bridge the audit team's cybersecurity knowledge gap played a pivotal role in identifying shortcomings in the risk assessment methodology and reviewing network architecture. This included evaluating firewalls, intrusion detection and prevention systems, and other network security measures, as well as assessing how Cyber ACrypt detects, responds to, and recovers from external and internal threats. Under John's supervision, the technical expert communicated the audit findings to the representatives of Cyber ACrypt. However, the audit team observed that the expert s objectivity might have been compromised due to receiving consultancy fees from the auditee. Considering the behavior of the technical expert during the audit, the audit team leader decided to discuss this concern with the certification body.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 6, was the objective of the interviews during the Stage 1 audit accordingly set by the audit team?
You are an experienced audit team leader conducting a third-party surveillance audit of an organisation that designs websites for its clients. You are currently reviewing the organisation's Statement of Applicability.
Based on the requirements of ISO/IEC 27001, which two of the following observations about the Statement of Applicability are true?
You are performing an ISMS audit at a residential nursing home railed ABC that provides healthcare services. The next step in your audit plan is to verify the effectiveness of the continual improvement process. During the audit, you learned most of the residents' family members (90%) receive WeCare medical device promotional advertisements through email and SMS once a week via ABC's healthcare mobile app. All of them do not agree on the use of the collected personal data (or marketing or any other purposes than nursing and medical care on the signed service agreement with ABC. They have very strong reason to believe that ABC is leaking residents' and family members' personal information to a non-relevant third party and they have filed complaints.
The Service Manager says that all these complaints have been treated as nonconformities, and the corrective actions have been planned and implemented according to the Nonconformity and Corrective management procedure. The corrective action involved stopping working with WeCare the medical device manufacturer immediately and asking them to delete all personal data received as well as sending an apology email to all residents and their family members.
You are preparing the audit findings. Select one option of the correct finding.
Question:
An organization is evaluating the materiality of different processes within its ISMS. It is assessing the direct expenses involved with personnel, third-party services, and general fees. Which factor of materiality is the company primarily considering?
Please match the roles to the following descriptions:
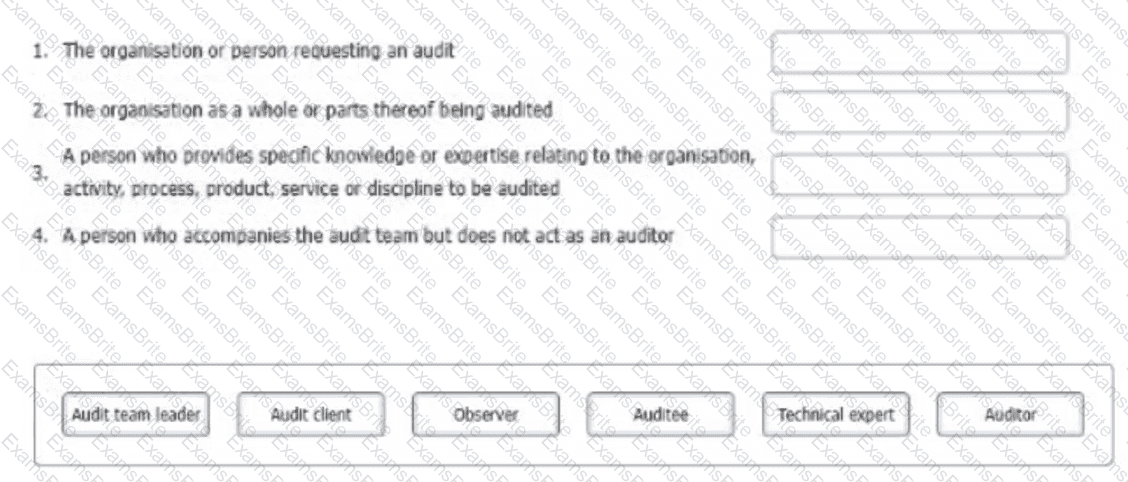
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable test from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
Based on Scenario 6, when evaluating documented information, what action should the auditor have taken during the stage 1 audit?
The scope of an organization certified against ISO/IEC 27001 states that they provide editing and web hosting services. However, due to some changes in the organization, the technical support related to the web hosting services has been outsourced. Should a change in the scope be initiated in this case?
Costs related to nonconformities and failures to comply with legal and contractual requirements are assessed when defining:
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
According to Scenario 6, was it appropriate for the audit team to include in the audit report the observed deficiency in the marketing department's access rights control procedures?
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
Based on Scenario 4, is the involvement of all the parties acceptable during the auditing of the outsourced operations?
Question:
What type of sampling was used when the auditor used probability-based sampling for event log reviews?
An organisation has ISO/IEC 27001 Information Security Management System (ISMS) certification from a third-party certification body. Which one of the following represents an advantage of having accredited certification?
You are an experienced ISMS audit team leader. You are currently conducting a third-party surveillance audit of an
international haulage organisation. You have sampled four internal audit reports which state:
Report 1 - Auditor: Mr James.
Over the year the organisation has failed to meet its promised delivery dates on 23 occasions out of 100. This is against a target of '95% of deliveries on time'.
Grading - Minor
Corrective Action due: Within 9 months.
Report 2 - Auditor: Mr James.
Between January and March, it was noted 125 complaints were received about the Service Desk Team. Clients
accused them of being rude and unresponsive.
Grading - Minor
Corrective Action due: Within 12 months.
Report 3 - Auditor: Mr James.
Of the 40 customer orders received last month, 38 were correctly processed. Of the remaining 2, one was missing a
signature and one was missing a date.
Grading -
Corrections due: Within 3 weeks
Report 4 - Auditor: Mr Rogers.
Of the 30 personnel records examined, 26 were found to be fully completed whilst the remaining 4 were all missing
the individual's start date.
Grading – Major
Corrections due: Within 1 week
Which four of the options demonstrate the concerns you would have about these reports?
You see a blue color sticker on certain physical assets. What does this signify?
Scenario 5: Data Grid Inc. is a well-known company that delivers security services across the entire information technology infrastructure. It provides cybersecurity software, including endpoint security, firewalls, and antivirus software. For two decades, Data Grid Inc. has helped various companies secure their networks through advanced products and services. Having achieved reputation in the information and network security field, Data Grid Inc. decided to obtain the ISO/IEC 27001 certification to better secure its internal and customer assets and gain competitive advantage.
Data Grid Inc. appointed the audit team, who agreed on the terms of the audit mandate. In addition, Data Grid Inc. defined the audit scope, specified the audit criteria, and proposed to close the audit within five days. The audit team rejected Data Grid Inc.'s proposal to conduct the audit within five days, since the company has a large number of employees and complex processes. Data Grid Inc. insisted that they have planned to complete the audit within five days, so both parties agreed upon conducting the audit within the defined duration. The audit team followed a risk-based auditing approach.
To gain an overview of the main business processes and controls, the audit team accessed process descriptions and organizational charts. They were unable to perform a deeper analysis of the IT risks and controls because their access to the IT infrastructure and applications was restricted. However, the audit team stated that the risk that a significant defect could occur to Data Grid Inc.'s ISMS was low since most of the company's processes were automated. They therefore evaluated that the ISMS, as a whole, conforms to the standard requirements by asking the representatives of Data Grid Inc. the following questions:
•How are responsibilities for IT and IT controls defined and assigned?
•How does Data Grid Inc. assess whether the controls have achieved the desired results?
•What controls does Data Grid Inc. have in place to protect the operating environment and data from malicious software?
•Are firewall-related controls implemented?
Data Grid Inc.'s representatives provided sufficient and appropriate evidence to address all these questions.
The audit team leader drafted the audit conclusions and reported them to Data Grid Inc.'s top management. Though Data Grid Inc. was recommended for certification by the auditors, misunderstandings were raised between Data Grid Inc. and the certification body in regards to audit objectives. Data Grid Inc. stated that even though the audit objectives included the identification of areas for potential improvement, the audit team did not provide such information.
Based on this scenario, answer the following question:
What would prevent the misunderstanding between the certification body and the Data Grid Inc.?
Refer to scenario 5.
Scenario 5: Cobt. an insurance company in London, offers various commercial, industrial, and life insurance solutions. In recent years, the number of Cobt's clients has increased enormously. Having a huge amount of data to process, the company decided that certifying against ISO/IEC 27001 would bring many benefits to securing information and show its commitment to continual improvement. While the company was well-versed in conducting regular risk assessments, implementing an ISMS brought major changes to its daily operations. During the risk assessment process, a risk was identified where significant defects occurred without being detected or prevented by the organizations internal control mechanisms.
The company followed a methodology to implement the ISMS and had an operational ISMS in place after only a few months After successfully implementing the ISMS, Cobt applied for ISO/IEC 27001 certification Sarah, an experienced auditor, was assigned to the audit Upon thoroughly analyzing the audit offer, Sarah accepted her responsibilities as an audit team leader and immediately started to obtain general information about Cobt She established the audit criteria and objective, planned the audit, and assigned the audit team members' responsibilities.
Sarah acknowledged that although Cobt has expanded significantly by offering diverse commercial and insurance solutions, it still relies on some manual processes Therefore, her initial focus was to gather information on how the company manages its information security risks Sarah contacted Cobt's representatives to request access to information related to risk management for the off-site review, as initially agreed upon for part of the audit However, Cobt later refused, claiming that such information is too sensitive to be accessed outside of the company This refusal raised concerns about the audit's feasibility, particularly regarding the availability and cooperation of the auditee and access to evidence Moreover, Cobt raised concerns about the audit schedule, stating that it does not properly reflect the recent changes the company made It pointed out that the actions to be performed during the audit apply only to the initial scope and do not encompass the latest changes made in the audit scope
Sarah also evaluated the materiality of the situation, considering the significance of the information denied for the audit objectives. In this case, the refusal by Cobt raised questions about the completeness of the audit and its ability to provide reasonable assurance. Following these situations, Sarah decided to withdraw from the audit before a certification agreement was signed and communicated her decision to Cobt and the certification body. This decision was made to ensure adherence to audit principles and maintain transparency, highlighting her commitment to consistently upholding these principles.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 5, Sarah decided to withdraw from the audit before a certification agreement was signed. Is this acceptable?
Select two of the following options that are the responsibility of a legal technical expert on the audit team during a certification audit.
Evaluating the auditee's legal knowledge
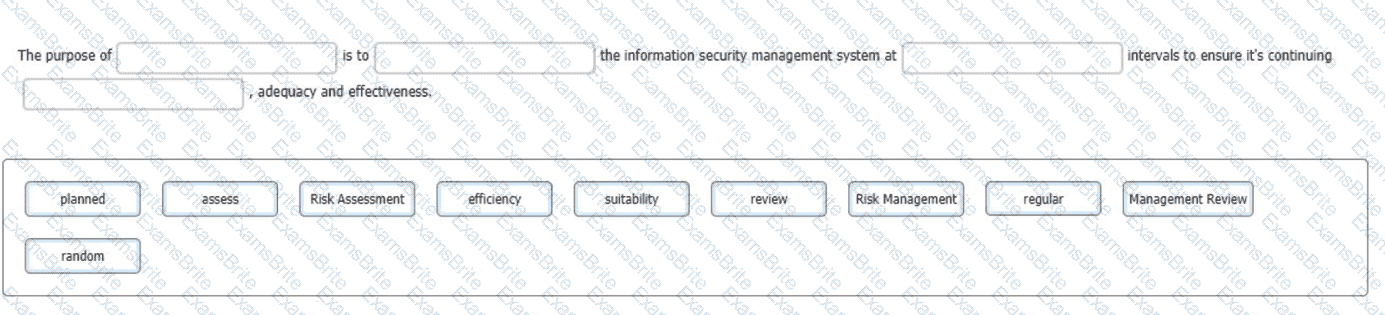
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company's risk management process.
He is attempting to update the current documentation to make it easier for other managers to understand, however, it is clear from your discussion he is confusing several key terms.
You ask him to match each of the descriptions with the appropriate risk term. What should the correct answers be?
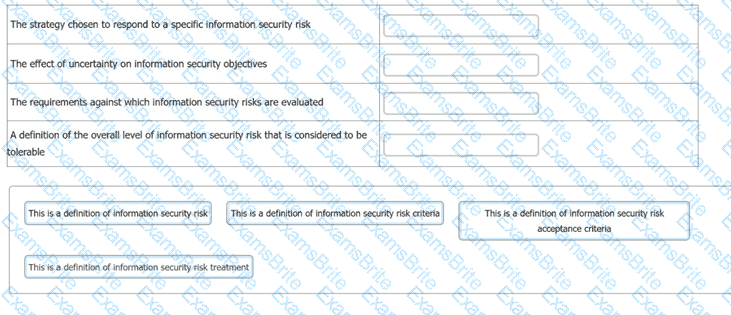
Question
To verify conformity to control 8.15 Logging of ISO/IEC 27001 Annex A, the audit team studied a sample of server logs to determine if they could be edited or deleted. Which audit procedure did the audit team use?
Scenario 8: Tessa. Malik, and Michael are an audit team of independent and qualified experts in the field of security, compliance, and business planning and strategies. They are assigned to conduct a certification audit in Clastus, a large web design company. They have previously shown excellent work ethics, including impartiality and objectiveness, while conducting audits. This time, Clastus is positive that they will be one step ahead if they get certified against ISO/IEC 27001.
Tessa, the audit team leader, has expertise in auditing and a very successful background in IT-related issues, compliance, and governance. Malik has an organizational planning and risk management background. His expertise relies on the level of synthesis and analysis of an organization's security controls and its risk tolerance in accurately characterizing the risk level within an organization On the other hand, Michael is an expert in the practical security of controls assessment by following rigorous standardized programs.
After performing the required auditing activities, Tessa initiated an audit team meeting They analyzed one of Michael s findings to decide on the issue objectively and accurately. The issue Michael had encountered was a minor nonconformity in the organization's daily operations, which he believed was caused by one of the organization's IT technicians As such, Tessa met with the top management and told them who was responsible for the nonconformity after they inquired about the names of the persons responsible
To facilitate clarity and understanding, Tessa conducted the closing meeting on the last day of the audit. During this meeting, she presented the identified nonconformities to the Clastus management. However, Tessa received advice to avoid providing unnecessary evidence in the audit report for the Clastus certification audit, ensuring that the report remains concise and focused on the critical findings.
Based on the evidence examined, the audit team drafted the audit conclusions and decided that two areas of the organization must be audited before the certification can be granted. These decisions were later presented to the auditee, who did not accept the findings and proposed to provide additional information. Despite the auditee's comments, the auditors, having already decided on the certification recommendation, did not accept the additional information. The auditee's top management insisted that the audit conclusions did not represent reality, but the audit team remained firm in their decision.
Based on the scenario above, answer the following question:
Question:
The audit team did not accept Clastus's additional information because they had already made the certification recommendation. Is this acceptable?
You are performing an ISMS audit at a European-based residential nursing home called ABC that provides healthcare services. The next step in your audit plan is to verify the effectiveness of the continual improvement process.
During the audit, you learned most of the residents' family members (90%) receive WeCare medical devices promotion advertisements through email and SMS once a week via ABC's healthcare mobile app. All of them do not agree on the use of the collected personal data for marketing or any other purposes than nursing and medical care on the signed service agreement with ABC. They have very strong reason to believe that ABC is leaking residents' and family members' personal information to a non-relevant third party and they have filed complaints.
The Service Manager says that, after investigation, all these complaints have been treated as nonconformities. The corrective actions have been planned and implemented according to the nonconformity and corrective management procedure (Document reference ID: ISMS_L2_10.1, version 1).
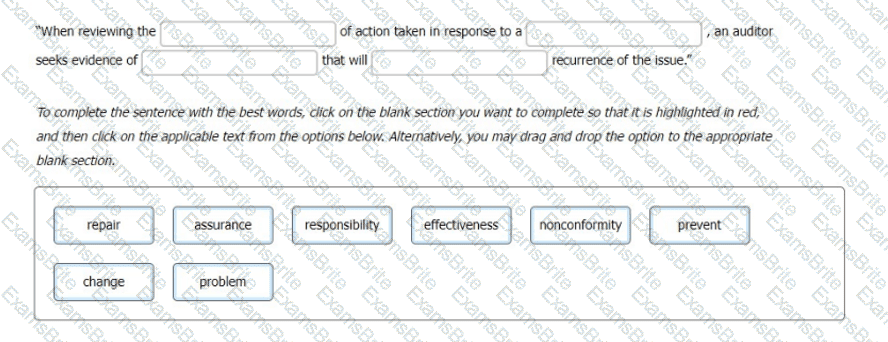
You write a nonconformity which you will follow up on later. Select the words that best complete the sentence:
You are carrying out a third-party surveillance audit of a client's ISMS. You are currently in the secure storage area of the data centre where the organisation's customers are able to temporarily locate equipment coming into or going out of the site. The equipment is contained within locked cabinets and each cabinet is allocated to a single, specific client.
Out of the corner of your eye you spot movement near the external door of the storage area. This is followed by a loud noise. You ask the guide what is going on. They tell you that recent high rainfall has raised local river levels and caused an infestation of rats. The noise was a specialist pest control stunning device being triggered. You check the device in the corner and find there is a large immobile rat contained within it.
What three actions would be appropriate to take next?
You are the person responsible for managing the audit programme and deciding the size and composition of the audit team for a specific audit. Select the two factors that should be considered.
The audit scope and criteria
Which one of the following options best describes the main purpose of a Stage 2 third-party audit?
An auditor of organisation A performs an audit of supplier B. Which two of the following actions is likely to represent a breach of confidentiality by the auditor after having identified findings in B's information security management system?
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet announced that the ISMS certification scope encompasses the whole company once ensuring that the new department also complies with the ISO/IEC 27001 requirements. How would you classify this situation illustrated in scenario 9?
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including mis-addressed labels and, in 15% of company cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SH: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity. Referencing the scenario, which six of the following Appendix A controls would you expect the auditee to have implemented when you conduct the follow-up audit?
Scenario 9
CloudFort, a small networking company, provides network security, cloud computing, and virtualization solutions. The company has recently been certified in an information security management system (ISMS) based on the ISO/IEC 27001 standard, which has resulted in a spike in its recognition, confirming the maturity of CloudFort’s operation.
CloudFort continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. Due to its size and desire for greater objectivity, the top management decided to outsource the internal audit function to ensure the internal audit is independent of the audited activities and holds an advisory role in the continual improvement of the ISMS.
After the initial certification audit, the company created a new department specializing in data storage solutions. It offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. Because of the new department, CloudFort initiated a risk assessment process and an internal audit. Following the internal audit results, the company confirmed the effectiveness and efficiency of the new processes and controls.
After determining that the new department fully complies with ISO/IEC 27001 requirements, top management decided to include it in the certification scope. They submitted a request to the certification body for an extension of the certification scope to ensure that the department’s processes and security measures fully align with the overall ISMS.
One year after the initial certification audit, the certification body conducted another audit of CloudFort's ISMS. This audit aimed to determine CloudFort’s ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS fulfills the standard requirements. Nonetheless, the new department introduced changes that significantly affected how the overall management system was governed, requiring updates to existing processes and controls.
Moreover, although CloudFort requested an extension of the certification scope, they failed to provide timely updates on the impact of the new department on the ISMS to the certification body. Thus, CloudFort’s certification was suspended.
Question
CloudFort requested an extension of the certification scope to include the new department. How would you classify this situation? Refer to Scenario 9.
Scenario 3
NightCore, a multinational technology enterprise headquartered in the United States, specializes in e-commerce, cloud computing, digital streaming, and artificial intelligence (AI). After having an information security management system (ISMS) implemented for over a year, NightCore contracted a certification body to perform an audit for ISO/IEC 27001 certification.
The certification body formed a team of five auditors, with Jack as a team leader. Jack is renowned for his extensive auditing experience in risk management, information security controls, and incident management. His skill set aligns well with the requirements of auditing principles and processes, enabling him to effectively comprehend the audit scope and apply relevant criteria effectively. Jack also demonstrates a solid understanding of NightCore’s organizational structure, purpose, and management practices and the statutory and regulatory requirements applicable to its activities.
The audit carried out by the audit team followed a rational method to reach reliable and reproducible conclusions systematically. The audit team recognized that only information capable of being verified to some extent should be considered valid evidence. In some rare instances during the audit where the verification of certain information posed challenges and where its degree of verifiability was low, the auditors exercised their professional judgment to assess the reliability and determine the level of reliance that could be placed on such evidence.
During the audit, the auditors documented their observations and inspection notes regarding the operational planning and control of NightCore’s ISMS operations. They also recorded observations of NightCore’s inventory of information and associated assets. Additionally, the auditors reviewed the configuration of firewalls implemented to secure connections to network services.
As the audit approached its final stages, NightCore’s commitment to upholding the highest levels of information security became evident. With ISO/IEC 27001 certification within reach, NightCore is well-positioned to achieve ISO/IEC 27001 certification, enhancing its reputation in the technology sector.
Question
During the audit at NightCore, the auditors focused on key areas of ISMS operations, including operational planning, asset inventory, and firewall configurations. What type of evidence did the auditors collect during the audit conducted at NightCore?
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
Which type of evidence did the auditors utilize to validate various aspects of SendPay’s ISMS during the audit process? Refer to Scenario 4.
You receive the following mail from the IT support team: Dear User,Starting next week, we will be deleting all inactive email accounts in order to create spaceshare the below details in order to continue using your account. In case of no response,
Name:
Email ID:
Password:
DOB:
Kindly contact the webmail team for any further support. Thanks for your attention.
Which of the following is the best response?
During an opening meeting of a Stage 2 audit, the Managing Director of the client organisation invites the audit team to view a new organisation video lasting 45 minutes.
Which two of the following responses should the audit team leader make?
Scenario 8
Trustingo has been providing banking and financial services in Estonia since 2010. The company has a network of 30 branches with over 100 ATMs nationwide. To meet strict data security and privacy regulations, Trustingo implemented an information security management system (ISMS) based on ISO/IEC 27001, ensuring better security, improved risk management, and compliance with legal requirements.
Nine months after the successful implementation of the ISMS, Trustingo decided to pursue certification for their ISMS based on ISO/IEC 27001 by an independent certification body. The certification audit included Trustingo's systems, processes, and technologies.
The audit team conducted the Stage 1 and Stage 2 audits jointly, and several nonconformities were detected. The first nonconformity was related to Trustingo's labeling of information. The company had an information classification scheme but no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently.
The nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information can be stored in removable media, whereas storing sensitive information is strictly prohibited.
The audit team drafted the nonconformity report and discussed the audit conclusions with Trustingo's representatives, who agreed to submit an action plan for the detected nonconformities within two months. Since the certification recommendation is conditional upon filing corrective actions, Trustingo must submit corrective action plans to show how they will address and resolve these nonconformities. Trustingo accepted the audit team leader's proposed solution and addressed the nonconformities by drafting an information labeling procedure and updating the removable media procedure.
Two weeks after the audit completion, Trustingo submitted a general action plan. Although the plan addressed the detected nonconformities and corrective actions taken, it lacked detailed action steps for each nonconformity and did not include specific details on the impacted systems, controls, or operations. The audit team evaluated the action plan. Nevertheless, Trustingo received an unfavorable recommendation for certification.
Question
Which option justifies the unfavorable recommendation for certification? Refer to Scenario 8.
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the ORGANISATIONAL controls listed in the Statement of Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
A property of Information that has the ability to prove occurrence of a claimed event.
During an audit, the audit team leader reached timely conclusions based on logical reasoning and analysis. What professional behaviour was displayed by the audit team leader?
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
By drafting a procedure for information labeling, EsBank has:
You are conducting a third-party surveillance audit when another member of the audit team approaches you seeking clarification. They have been asked to assess the organisation's application of control 5.7 - Threat Intelligence. They are aware that this is one of the new controls introduced in the 2022 edition of ISO/IEC 27001, and they want to make sure they audit the control correctly.
They have prepared a checklist to assist them with their audit and want you to confirm that their planned activities are aligned with the control's requirements.
Which three of the following options represent valid audit trails?
During an opening meeting of a Stage 2 audit, the Managing Director of the client organisation invites the audit team to view a new company video lasting 45 minutes. Which two of the following responses should the audit team leader make?
Question:
According to ISO/IEC 27001, Clause 5.1 (Leadership and Commitment), which of the following is NOT a responsibility of top management?
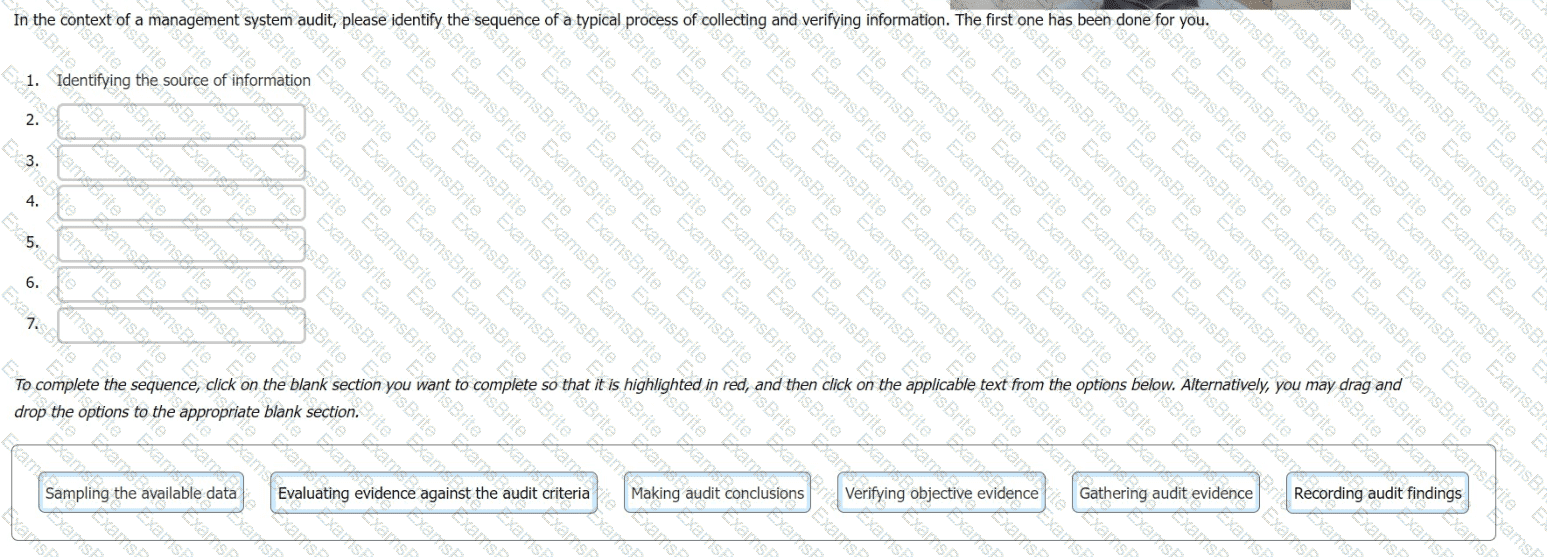
In the context of a management system audit, please identify the sequence of a typical process of collecting and verifying information. The first one has been done for you.
Audit methods can be either with or without interaction with individuals representing the auditee. Which two of the following methods are with interaction?
Which statement below best describes the relationship between information security aspects?
After completing Stage 1 and in preparation for a Stage 2 initial certification audit, the auditee informs the audit team leader that they wish to extend the audit scope to include two additional sites that have recently been acquired by the organisation.
Considering this information, what action would you expect the audit team leader to take?
Scenario 4: SendPay is a financial company that provides its services through a network of agents and financial institutions. One of their main services is transferring money worldwide. SendPay, as a new company, seeks to offer top quality services to its clients. Since the company offers international transactions, it requires from their clients to provide personal information, such as their identity, the reason for the transactions, and other details that might be needed to complete the transaction. Therefore, SendPay has implemented security measures to protect their clients' information, including detecting, investigating, and responding to any information security threats that may emerge. Their commitment to offering secure services was also reflected during the ISMS implementation where the company invested a lot of time and resources.
Last year, SendPay unveiled their digital platform that allows money transactions through electronic devices, such as smartphones or laptops, without requiring an additional fee. Through this platform, SendPay's clients can send and receive money from anywhere and at any time. The digital platform helped SendPay to simplify the company's operations and further expand its business. At the time, SendPay was outsourcing its software operations, hence the project was completed by the software development team of the outsourced company. The same team was also responsible for maintaining the technology infrastructure of SendPay.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year. They contracted a certification body that fit their criteria. Soon after, the certification body appointed a team of four auditors to audit SendPay's ISMS.
During the audit, among others, the following situations were observed:
1.The outsourced software company had terminated the contract with SendPay without prior notice. As a result, SendPay was unable to immediately bring the services back in-house and its operations were disrupted for five days. The auditors requested from SendPay's representatives to provide evidence that they have a plan to follow in cases of contract terminations. The representatives did not provide any documentary evidence but during an interview, they told the auditors that the top management of SendPay had identified two other software development companies that could provide services immediately if similar situations happen again.
2.There was no evidence available regarding the monitoring of the activities that were outsourced to the software development company. Once again, the representatives of SendPay told the auditors that they regularly communicate with the software development company and that they are appropriately informed for any possible change that might occur.
3.There was no nonconformity found during the firewall testing. The auditors tested the firewall configuration in order to determine the level of security provided by
these services. They used a packet analyzer to test the firewall policies which enabled them to check the packets sent or received in real-time.
Based on this scenario, answer the following question:
Regarding the third situation observed, auditors themselves tested the configuration of firewalls implemented in SendPay's network. How do you describe this situation? Refer to scenario 4.
You are an experienced ISMS audit team leader, assisting an auditor in training to write their first audit report.
You want to check the auditor in training's understanding of terminology relating to the contents of an audit report and chose to do this by presenting the following examples.
For each example, you ask the auditor in training what the correct term is that describes the activity
Match the activity to the description.

Scenario:
Northstorm is an online retail shop offering unique vintage and modern accessories. It initially entered a small market but gradually grew thanks to the development of the overall e-commerce landscape. Northstorm works exclusively online and ensures efficient payment processing, inventory management, marketing tools, and shipment orders. It uses prioritized ordering to receive, restock, and ship its most popular products.
Northstorm has traditionally managed its IT operations by hosting its website and maintaining full control over its infrastructure, including hardware, software, and data administration. However, this approach hindered its growth due to the lack of responsive infrastructure. Seeking to enhance its e-commerce and payment systems, Northstorm opted to expand its in-house data centers, completing the expansion in two phases over three months. Initially, the company upgraded its core servers, point-of-sale, ordering, billing, database, and backup systems. The second phase involved improving mail, payment, and network functionalities. Additionally, during this phase, Northstorm adopted an international standard for personally identifiable information (PII) controllers and PII processors regarding PII processing to ensure its data handling practices were secure and compliant with global regulations.
Despite the expansion, Northstorm's upgraded data centers failed to meet its evolving business demands. This inadequacy led to several new challenges, including issues with order prioritization. Customers reported not receiving priority orders, and the company struggled with responsiveness. This was largely due to the main server's inability to process orders from YouDecide, an application designed to prioritize orders and simulate customer interactions. The application, reliant on advanced algorithms, was incompatible with the new operating system (OS) installed during the upgrade.
Faced with urgent compatibility issues, Northstorm quickly patched the application without proper validation, leading to the installation of a compromised version. This security lapse resulted in the main server being affected and the company's website going offline for a week. Recognizing the need for a more reliable solution, the company decided to outsource its website hosting to an e-commerce provider. The company signed a confidentiality agreement concerning product ownership and conducted a thorough review of user access rights to enhance security before transitioning.
Question:
Based on Scenario 1, which international standard did Northstorm adopt during the second phase of expansion?
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
Is the internal auditor responsible for following up on action plans resulting from external audits?
Question
Which statement best describes how internal audits and external audits complement each other in an organization?
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
Which option justifies the unfavorable recommendation for certification? Refer to scenario 8.
You are an experienced ISMS audit team leader conducting a third-party surveillance visit.
You notice that although the auditee is claiming conformity with ISO/IEC 27001:2022 they are still referring to Improvement as clause 10.2 (as it was in the 2013 edition) when this is now clause 10.1 in
the 2022 edition. You have confirmed they are meeting all of the 2022 requirements set out in the standard.
Select one option of the action you should take.
Scenario 3: NightCore is a multinational technology company based in the United States that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence. After having an information security management system (ISMS) implemented for over 8 months, they contracted a certification body to conduct a third party audit in order to get certified against ISO/IEC 27001.
The certification body set up a team of seven auditors. Jack, the most experienced auditor, was assigned as the audit team leader. Over the years, he received many well known certifications, such as the ISO/IEC 27001 Lead Auditor, CISA, CISSP, and CISM.
Jack conducted thorough analyses on each phase of the ISMS audit, by studying and evaluating every information security requirement and control that was implemented by NightCore. During stage 2 audit. Jack detected several nonconformities. After comparing the number of purchased invoices for software licenses with the software inventory, Jack found out that the company has been using the illegal versions of a software for many computers. He decided to ask for an explanation from the top management about this nonconformity and see whether they were aware about this. His next step was to audit NightCore's IT Department. The top management assigned Tom, NightCore's system administrator, to act as a guide and accompany Jack and the audit team toward the inner workings of their system and their digital assets infrastructure.
While interviewing a member of the Department of Finance, the auditors discovered that the company had recently made some unusual large transactions to one of their consultants. After gathering all the necessary details regarding the transactions. Jack decided to directly interview the top management.
When discussing about the first nonconformity, the top management told Jack that they willingly decided to use a copied software over the original one since it was cheaper. Jack explained to the top management of NightCore that using illegal versions of software is against the requirements of ISO/IEC 27001 and the national laws and regulations. However, they seemed to be fine with it.
Several months after the audit, Jack sold some of NightCore's information that he collected during the audit for a huge amount of money to competitors of NightCore.
Based on this scenario, answer the following question:
Does ISO/IEC 27001 require organizations to comply with national laws and regulations?
You are an experienced ISMS audit team leader providing instruction to an auditor in training. They are unclear in their understanding of risk processes and ask you to provide them with an example of each of the processes detailed below.
Match each of the descriptions provided to one of the following risk management processes.
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.

Scenario 9
CloudFort, a small networking company, provides network security, cloud computing, and virtualization solutions. The company has recently been certified in an information security management system (ISMS) based on the ISO/IEC 27001 standard, which has resulted in a spike in its recognition, confirming the maturity of CloudFort’s operations.
CloudFort continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. Due to its size and desire for greater objectivity, top management decided to outsource the internal audit function to ensure the internal audit is independent of the audited activities and holds an advisory role in the continual improvement of the ISMS.
After the initial certification audit, the company created a new department specializing in data storage solutions. It offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. Because of the new department, CloudFort initiated a risk assessment process and an internal audit. Following the internal audit results, the company confirmed the effectiveness and efficiency of the new processes and controls.
After determining that the new department fully complies with ISO/IEC 27001 requirements, top management decided to include it in the certification scope. They submitted a request to the certification body for an extension of the certification scope to ensure that the department’s processes and security measures fully align with the overall ISMS.
One year after the initial certification audit, the certification body conducted another audit of CloudFort's ISMS. This audit aimed to determine CloudFort’s ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure continual improvement. The audit team confirmed that the certified ISMS fulfills the standard requirements. Nonetheless, the new department introduced changes that significantly affected how the overall management system was governed, requiring updates to existing processes and controls.
Moreover, although CloudFort requested an extension of the certification scope, they failed to provide timely updates on the impact of the new department on the ISMS to the certification body. Thus, CloudFort’s certification was suspended.
Question
Based on Scenario 9, why was CloudFort’s certification suspended?
Scenario 7: Webvue. headquartered in Japan, is a technology company specializing in the development, support, and maintenance of computer software. Webvue provides solutions across various technology fields and business sectors. Its flagship service is CloudWebvue, a comprehensive cloud computing platform offering storage, networking, and virtual computing services. Designed for both businesses and individual users. CloudWebvue is known for its flexibility, scalability, and reliability.
Webvue has decided to only include CloudWebvue in its ISO/IEC 27001 certification scope. Thus, the stage 1 and 2 audits were performed simultaneously Webvue takes pride in its strictness regarding asset confidentiality They protect the information stored in CloudWebvue by using appropriate cryptographic controls. Every piece of information of any classification level, whether for internal use. restricted, or confidential, is first encrypted with a unique corresponding hash and then stored in the cloud
The audit team comprised five persons Keith. Sean. Layla, Sam. and Tina. Keith, the most experienced auditor on the IT and information security auditing team, was the audit team leader. His responsibilities included planning the audit and managing the audit team. Sean and Layla were experienced in project planning, business analysis, and IT systems (hardware and application) Their tasks included audit planning according to Webvue’s internal systems and processes Sam and Tina, on the other hand, who had recently completed their education, were responsible for completing the day-to-day tasks while developing their audit skills
While verifying conformity to control 8.24 Use of cryptography of ISO/IEC 27001 Annex A through interviews with the relevant staff, the audit team found out that the cryptographic keys have been initially generated based on random bit generator (RBG) and other best practices for the generation of the cryptographic keys. After checking Webvue's cryptography policy, they concluded that the information obtained by the interviews was true. However, the cryptographic keys are still in use because the policy does not address the use and lifetime of cryptographic keys.
As later agreed upon between Webvue and the certification body, the audit team opted to conduct a virtual audit specifically focused on verifying conformity to control 8.11 Data Masking of ISO/IEC 27001 within Webvue, aligning with the certification scope and audit objectives. They examined the processes involved in protecting data within CloudWebvue. focusing on how the company adhered to its policies and regulatory standards. As part of this process. Keith, the audit team leader, took screenshot copies of relevant documents and cryptographic key management procedures to document and analyze the effectiveness of Webvue's practices.
Webvue uses generated test data for testing purposes. However, as determined by both the interview with the manager of the QA Department and the procedures used by this department, sometimes live system data are used. In such scenarios, large amounts of data are generated while producing more accurate results. The test data is protected and controlled, as verified by the simulation of the encryption process performed by Webvue's personnel during the audit
While interviewing the manager of the QA Department, Keith observed that employees in the Security Training Department were not following proper procedures, even though this department fell outside the audit scope. Despite the exclusion in the audit scope, the non conformity in the Security Training Department has potential implications for the processes within the audit scope, specifically impacting data security and cryptographic practices in CloudWebvue. Therefore, Keith incorporated this finding into the audit report and accordingly informed the auditee.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 7, the audit team checked Webvue’s cryptography policy to obtain reasonable assurance of the information obtained during interviews. Which type of audit procedure has been used?
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
Did the audit at SendPay include all the necessary steps for auditing outsourced operations?
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the TECHNOLOGICAL controls listed in
the Statement of Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
The audit team photocopied the examined employee training records to support their conclusion. Should the audit team obtain an approval from Lawsy before taking this action? Refer to scenario 7.
Scenario 1: Fintive is a distinguished security provider for online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive
offers services to companies that operate online and want to improve their information security, prevent fraud, and protect user information such as PII. Fintive centers
its decision-making and operating process based on previous cases. They gather customer data, classify them depending on the case, and analyze them. The company
needed a large number of employees to be able to conduct such complex analyses. After some years, however, the technology that assists in conducting such analyses
advanced as well. Now, Fintive is planning on using a modern tool, a chatbot, to achieve pattern analyses toward preventing fraud in real-time. This tool would also be
used to assist in improving customer service.
This initial idea was communicated to the software development team, who supported it and were assigned to work on this project. They began integrating the chatbot
on their existing system. In addition, the team set an objective regarding the chatbot which was to answer 85% of all chat queries.
After the successful integration of the chatbot, the company immediately released it to their customers for use. The chatbot, however, appeared to have some issues.
Due to insufficient testing and lack of samples provided to the chatbot during the training phase, in which it was supposed "to learn" the queries pattern, the chatbot
failed to address user queries and provide the right answers. Furthermore, the chatbot sent random files to users when it received invalid inputs such as odd patterns
of dots and special characters. Therefore, the chatbot was unable to properly answer customer queries and the traditional customer support was overwhelmed with
chat queries and thus was unable to help customers with their requests.
Consequently, Fintive established a software development policy. This policy specified that whether the software is developed in-house or outsourced, it will undergo a
black box testing prior to its implementation on operational systems.
Based on this scenario, answer the following question:
The chatbot was supposed "to learn" the queries pattern to address user queries and provide the right answers. What type of technology enables
this?
Question:
A marketing agency has developed its risk assessment approach as part of the ISMS implementation. Is this acceptable?
Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life insurance. The company was founded in North Carolina, but have recently expanded in other locations, including Europe and Africa.
Sinvestment is committed to complying with laws and regulations applicable to their industry and preventing any information security incident. They have implemented an ISMS based on ISO/IEC 27001 and have applied for ISO/IEC 27001 certification.
Two auditors were assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment. they started the audit activities. First, they reviewed the documentation required by the standard, including the declaration of the ISMS scope, information security policies, and internal audits reports. The review process was not easy because, although Sinvestment stated that they had a documentation procedure in place, not all documents had the same format.
Then, the audit team conducted several interviews with Sinvestment's top management to understand their role in the ISMS implementation. All activities of the stage 1 audit were performed remotely, except the review of documented information, which took place on-site, as requested by Sinvestment.
During this stage, the auditors found out that there was no documentation related to information security training and awareness program. When asked, Sinvestment's representatives stated that the company has provided information security training sessions to all employees. Stage 1 audit gave the audit team a general understanding of Sinvestment's operations and ISMS.
The stage 2 audit was conducted three weeks after stage 1 audit. The audit team observed that the marketing department (which was not included in the audit scope) had no procedures in place to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the information security policy of the company, the issue was included in the audit report. In addition, during stage 2 audit, the audit team observed that Sinvestment did not record logs of user activities. The procedures of the company stated that "Logs recording user activities should be retained and regularly reviewed," yet the company did not present any evidence of the implementation of such procedure.
During all audit activities, the auditors used observation, interviews, documented information review, analysis, and technical verification to collect information and evidence. All the audit findings during stages 1 and 2 were analyzed and the audit team decided to issue a positive recommendation for certification.
During stage 1 audit, the audit team found out that Sinvestment did not have records on information security training and awareness. What Sinvestment do in this case? Refer to scenario 6.
Scenario 4: Branding is a marketing company that works with some of the most famous companies in the US. To reduce internal costs. Branding has outsourced the software development and IT helpdesk operations to Techvology for over two years. Techvology. equipped with the necessary expertise, manages Branding's software, network, and hardware needs. Branding has implemented an information security management system (ISMS) and is certified against ISO/IEC 27001, demonstrating its commitment to maintaining high standards of information security. It actively conducts audits on Techvology to ensure that the security of its outsourced operations complies with ISO/IEC 27001 certification requirements.
During the last audit. Branding's audit team defined the processes to be audited and the audit schedule. They adopted an evidence based approach, particularly in light of two information security incidents reported by Techvology in the past year The focus was on evaluating how these incidents were addressed and ensuring compliance with the terms of the outsourcing agreement
The audit began with a comprehensive review of Techvology's methods for monitoring the quality of outsourced operations, assessing whether the services provided met Branding's expectations and agreed-upon standards The auditors also verified whether Techvology complied with the contractual requirements established between the two entities This involved thoroughly examining the terms and conditions in the outsourcing agreement to guarantee that all aspects, including information security measures, are being adhered to.
Furthermore, the audit included a critical evaluation of the governance processes Techvology uses to manage its outsourced operations and other organizations. This step is crucial for Branding to verify that proper controls and oversight mechanisms are in place to mitigate potential risks associated with the outsourcing arrangement.
The auditors conducted interviews with various levels of Techvology's personnel and analyzed the incident resolution records. In addition, Techvology provided the records that served as evidence that they conducted awareness sessions for the staff regarding incident management. Based on the information gathered, they predicted that both information security incidents were caused by incompetent personnel. Therefore, auditors requested to see the personnel files of the employees involved in the incidents to review evidence of their competence, such as relevant experience, certificates, and records of attended trainings.
Branding's auditors performed a critical evaluation of the validity of the evidence obtained and remained alert for evidence that could contradict or question the reliability of the documented information received. During the audit at Techvology, the auditors upheld this approach by critically assessing the incident resolution records and conducting thorough interviews with employees at different levels and functions. They did not merely take the word of Techvology's representatives for facts; instead, they sought concrete evidence to support the representatives' claims about the incident management processes.
Based on the scenario above, answer the following question:
Question:
According to Scenario 4, what type of audit evidence did the auditors collect to determine the source of the information security incidents?
Question
Which statement below best describes the relationship between information security elements?
You are an experienced audit team leader guiding an auditor in training.
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the PHYSICAL controls listed in the Statement of Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
Scenario 5: Cobt. an insurance company in London, offers various commercial, industrial, and life insurance solutions. In recent years, the number of Cobt's clients has increased enormously. Having a huge amount of data to process, the company decided that certifying against ISO/IEC 27001 would bring many benefits to securing information and show its commitment to continual improvement. While the company was well-versed in conducting regular risk assessments, implementing an ISMS brought major changes to its daily operations. During the risk assessment process, a risk was identified where significant defects occurred without being detected or prevented by the organizations internal control mechanisms.
The company followed a methodology to implement the ISMS and had an operational ISMS in place after only a few months After successfully implementing the ISMS, Cobt applied for ISO/IEC 27001 certification Sarah, an experienced auditor, was assigned to the audit Upon thoroughly analyzing the audit offer, Sarah accepted her responsibilities as an audit team leader and immediately started to obtain general information about Cobt She established the audit criteria and objective, planned the audit, and assigned the audit team members' responsibilities.
Sarah acknowledged that although Cobt has expanded significantly by offering diverse commercial and insurance solutions, it still relies on some manual processes Therefore, her initial focus was to gather information on how the company manages its information security risks Sarah contacted Cobt's representatives to request access to information related to risk management for the off-site review, as initially agreed upon for part of the audit However, Cobt later refused, claiming that such information is too sensitive to be accessed outside of the company This refusal raised concerns about the audit's feasibility, particularly regarding the availability and cooperation of the auditee and access to evidence Moreover, Cobt raised concerns about the audit schedule, stating that it does not properly reflect the recent changes the company made It pointed out that the actions to be performed during the audit apply only to the initial scope and do not encompass the latest changes made in the audit scope
Sarah also evaluated the materiality of the situation, considering the significance of the information denied for the audit objectives. In this case, the refusal by Cobt raised questions about the completeness of the audit and its ability to provide reasonable assurance. Following these situations, Sarah decided to withdraw from the audit before a certification agreement was signed and communicated her decision to Cobt and the certification body. This decision was made to ensure adherence to audit principles and maintain transparency, highlighting her commitment to consistently upholding these principles.
Based on the scenario above, answer the following question:
Question:
What type of risk did Cobt identify during the last risk assessment?
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
Lawsy lacks a procedure regarding the use of laptops outside the workplace and it relies on employees' common knowledge to protect the confidentiality of information stored in the laptops. This presents:
Scenario 2: Knight is an electronics company from Northern California, US that develops video game consoles. Knight has more than 300 employees worldwide. On the
fifth anniversary of their establishment, they have decided to deliver the G-Console, a new generation video game console aimed for worldwide markets. G-Console is
considered to be the ultimate media machine of 2021 which will give the best gaming experience to players. The console pack will include a pair of VR headset, two
games, and other gifts.
Over the years, the company has developed a good reputation by showing integrity, honesty, and respect toward their customers. This good reputation is one of the
reasons why most passionate gamers aim to have Knight's G-console as soon as it is released in the market. Besides being a very customer-oriented company, Knight
also gained wide recognition within the gaming industry because of the developing quality. Their prices are a bit higher than the reasonable standards allow.
Nonetheless, that is not considered an issue for most loyal customers of Knight, as their quality is top-notch.
Being one of the top video game console developers in the world, Knight is also often the center of attention for malicious activities. The company has had an
operational ISMS for over a year. The ISMS scope includes all departments of Knight, except Finance and HR departments.
Recently, a number of Knight's files containing proprietary information were leaked by hackers. Knight's incident response team (IRT) immediately started to analyze
every part of the system and the details of the incident.
The IRT's first suspicion was that Knight's employees used weak passwords and consequently were easily cracked by hackers who gained unauthorized access to their
accounts. However, after carefully investigating the incident, the IRT determined that hackers accessed accounts by capturing the file transfer protocol (FTP) traffic.
FTP is a network protocol for transferring files between accounts. It uses clear text passwords for authentication.
Following the impact of this information security incident and with IRT's suggestion, Knight decided to replace the FTP with Secure Shell (SSH) protocol, so anyone
capturing the traffic can only see encrypted data.
Following these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. The results of
the process were approved by the ISMS project manager who claimed that the level of risk after the implementation of new controls was in accordance with the
company's risk acceptance levels.
Based on this scenario, answer the following question:
Based on scenario 2, the ISMS project manager approved the results of risk assessment. Is this acceptable?
You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leader. You are presently in
the auditee's data centre with another member of your audit team.
You are currently in a large room that is subdivided into several smaller rooms, each of which has a numeric
combination lock and swipe card reader on the door. You notice two external contractors using a swipe card and
combination number provided by the centre's reception desk to gain access to a client's suite to carry out authorised electrical repairs.
You go to reception and ask to see the door access record for the client's suite. This indicates only one card was
swiped. You ask the receptionist and they reply, "yes it's a common problem. We ask everyone to swipe their
cards but with contractors especially, one tends to swipe and the rest simply 'tailgate' their way in" but we know who they are from the reception sign-in.
Based on the scenario above which one of the following actions would you now take?
Scenario 6: Cyber ACrypt is a cybersecurity company that provides endpoint protection by offering anti-malware and device security, asset life cycle management, and device encryption. To validate its ISMS against ISO/IEC 27001 and demonstrate its commitment to cybersecurity excellence, the company underwent a meticulous audit process led by John, the appointed audit team leader.
Upon accepting the audit mandate, John promptly organized a meeting to outline the audit plan and team roles This phase was crucial for aligning the team with the audit's objectives and scope However, the initial presentation to Cyber ACrypt’s staff revealed a significant gap in understanding the audit's scope and objectives, indicating potential readiness challenges within the company
As the stage 1 audit commenced, the team prepared for on-site activities. They reviewed Cyber ACrypt's documented information, including the information security policy and operational procedures ensuring each piece conformed to and was standardized in format with author identification, production date, version number, and approval date Additionally, the audit team ensured that each document contained the information required by the respective clause of the standard This phase revealed that a detailed audit of the documentation describing task execution was unnecessary, streamlining the process and focusing the team's efforts on critical areas During the phase of conducting on-site activities, the team evaluated management responsibility for the Cyber Acrypt's policies This thorough examination aimed to ascertain continual improvement and adherence to ISMS requirements Subsequently, in the document, the stage 1 audit outputs phase, the audit team meticulously documented their findings, underscoring their conclusions regarding the fulfillment of the stage 1 objectives. This documentation was vital for the audit team and Cyber ACrypt to understand the preliminary audit outcomes and areas requiring attention.
The audit team also decided to conduct interviews with key interested parties. This decision was motivated by the objective of collecting robust audit evidence to validate the management system’s compliance with ISO/IEC 27001 requirements. Engaging with interested parties across various levels of Cyber ACrypt provided the audit team with invaluable perspectives and an understanding of the ISMS's implementation and effectiveness.
The stage 1 audit report unveiled critical areas of concern. The Statement of Applicability (SoA) and the ISMS policy were found to be lacking in several respects, including insufficient risk assessment, inadequate access controls, and lack of regular policy reviews. This prompted Cyber ACrypt to take immediate action to address these shortcomings. Their prompt response and modifications to the strategic documents reflected a strong commitment to achieving compliance.
The technical expertise introduced to bridge the audit team's cybersecurity knowledge gap played a pivotal role in identifying shortcomings in the risk assessment methodology and reviewing network architecture. This included evaluating firewalls, intrusion detection and prevention systems, and other network security measures, as well as assessing how Cyber ACrypt detects, responds to, and recovers from external and internal threats. Under John's supervision, the technical expert communicated the audit findings to the representatives of Cyber ACrypt. However, the audit team observed that the expert s objectivity might have been compromised due to receiving consultancy fees from the auditee. Considering the behavior of the technical expert during the audit, the audit team leader decided to discuss this concern with the certification body.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 6, is the audit team leader’s decision regarding the technical expert’s behavior acceptable?
You are an experienced ISMS audit team leader. During the conducting of a third-party surveillance audit, you decide to test your auditee's knowledge of ISO/IEC 27001's risk management requirements.
You ask her a series of questions to which the answer is either 'that is true' or 'that is false'. Which four of the following should she answer 'that is true'?
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
What steps should Sinvestment take in regard to the missing information security training and awareness procedures during the stage 1 audit? Refer to Scenario 6.
In the context of a third-party certification audit, confidentiality is an issue in an audit programme. Select two options which correctly state the function of confidentiality in an audit
After completing Stage 1 and in preparation for a Stage 2 initial certification audit, the auditee informs the audit team leader that they wish to extend the audit scope to include two additional sites that have recently been acquired by the organisation.
Considering this information, what action would you expect the audit team leader to take?
Scenario 1: Fintive is a distinguished security provider for online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive
offers services to companies that operate online and want to improve their information security, prevent fraud, and protect user information such as PII. Fintive centers
its decision-making and operating process based on previous cases. They gather customer data, classify them depending on the case, and analyze them. The company
needed a large number of employees to be able to conduct such complex analyses. After some years, however, the technology that assists in conducting such analyses
advanced as well. Now, Fintive is planning on using a modern tool, a chatbot, to achieve pattern analyses toward preventing fraud in real-time. This tool would also be
used to assist in improving customer service.
This initial idea was communicated to the software development team, who supported it and were assigned to work on this project. They began integrating the chatbot
on their existing system. In addition, the team set an objective regarding the chatbot which was to answer 85% of all chat queries.
After the successful integration of the chatbot, the company immediately released it to their customers for use. The chatbot, however, appeared to have some issues.
Due to insufficient testing and lack of samples provided to the chatbot during the training phase, in which it was supposed "to learn" the queries pattern, the chatbot
failed to address user queries and provide the right answers. Furthermore, the chatbot sent random files to users when it received invalid inputs such as odd patterns
of dots and special characters. Therefore, the chatbot was unable to properly answer customer queries and the traditional customer support was overwhelmed with
chat queries and thus was unable to help customers with their requests.
Consequently, Fintive established a software development policy. This policy specified that whether the software is developed in-house or outsourced, it will undergo a
black box testing prior to its implementation on operational systems.
According to scenario 1, the chatbot sent random files to users when it received invalid inputs. What impact might that lead to?
Objectives, criteria, and scope are critical features of a third-party ISMS audit. Which two issues are audit objectives?
Evaluate customer processes and functions
When an organisation needs to determine the resources required for the internal audit programme, which one of the following issues does not impact on the achievement of its intended results?
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
Is the purpose of reviewing previous surveillance audit reports in the recertification activity for Techmanic appropriately defined?
You are an experienced ISMS internal auditor.
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company's Statement of Applicability.
The IT Manager is attempting to update the ISO/IEC 27001:2013 based Statement of Applicability to a Statement aligned to the 4 control themes present in ISO/IEC 27001:2022 (Organizational controls, People Controls, Physical Controls, Technical Controls).
The IT Manager is happy with their reassignment of controls, with the following exceptions. He asks you which of the four control categories each of the following should appear under.
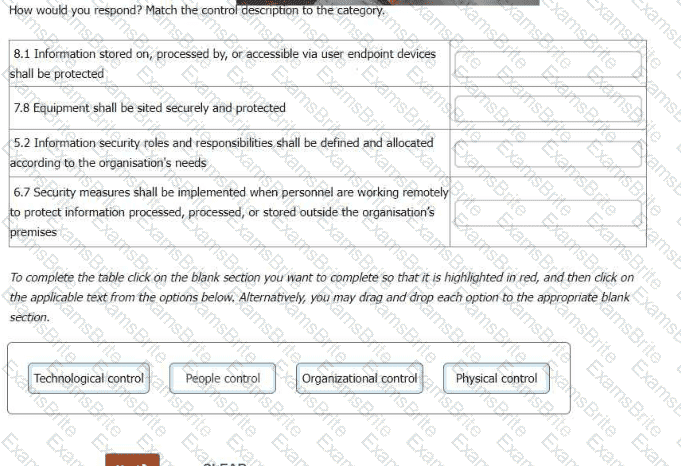
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including misaddressed labels and, in 15% of cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SM: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to
implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity. Referencing the scenario, which three of the following Annex A controls would you expect the auditee to have implemented when you conduct the follow-up audit?
5.11 Return of assets
Which one of the following options best describes the purpose of a Stage 2 audit?
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information security incident management procedure and explains that the process is based on ISO/IEC 27035-1:2016.
You review the document and notice a statement "any information security weakness, event, and incident should be reported to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences in the understanding of the meaning of "weakness, event, and incident".
You sample incident report records from the event tracking system for the last 6 months with summarized results in the following table.
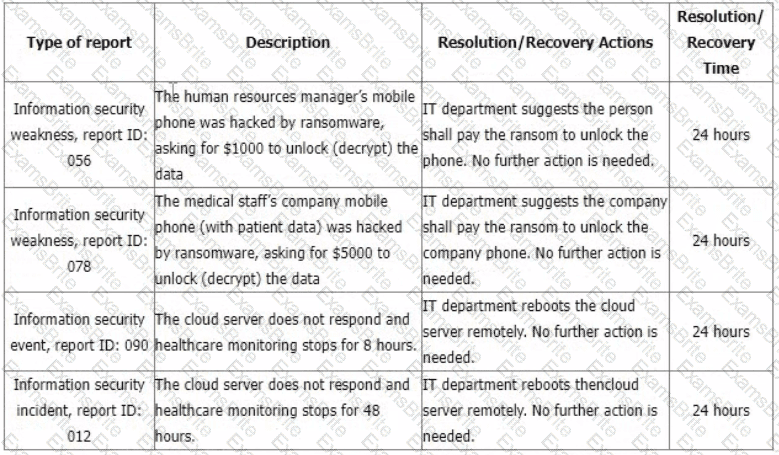
You would like to further investigate other areas to collect more audit evidence. Select two options that will not be in your audit trail.
Auditors should have certain knowledge and skills; while audit team leaders should have some additional knowledge and skills. From the following list, select two that only apply to audit team leaders.
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
Which of the options below does an internal audit program NOT allow?
Which two of the following options do not participate in a first-party audit?
Information or data that are classified as ______ do not require labeling.
Scenario 3
NightCore, a multinational technology enterprise headquartered in the United States, specializes in e-commerce, cloud computing, digital streaming, and artificial intelligence (AI). After having an information security management system (ISMS) implemented for over a year, NightCore contracted a certification body to perform an audit for ISO/IEC 27001 certification.
The certification body formed a team of five auditors, with Jack as a team leader. Jack is renowned for his extensive auditing experience in risk management, information security controls, and incident management. His skill set aligns well with the requirements of auditing principles and processes, enabling him to effectively comprehend the audit scope and apply relevant criteria effectively. Jack also demonstrates a solid understanding of NightCore’s organizational structure, purpose, and management practices, as well as the statutory and regulatory requirements applicable to its activities.
The audit carried out by the audit team followed a rational method to reach reliable and reproducible conclusions systematically. The audit team recognized that only information capable of being verified to some extent should be considered valid evidence. In some rare instances during the audit where the verification of certain information posed challenges and where its degree of verifiability was low, the auditors exercised their professional judgment to assess the reliability and determine the level of reliance that could be placed on such evidence.
During the audit, the auditors documented their observations and inspection notes regarding the operational planning and control of NightCore’s ISMS operations. They also recorded observations of NightCore’s inventory of information and associated assets. Additionally, the auditors reviewed the configuration of firewalls implemented to secure connections to network services.
As the audit approached its final stages, NightCore’s commitment to upholding the highest levels of information security became evident. With ISO/IEC 27001 certification within reach, NightCore is well-positioned to achieve ISO/IEC 27001 certification, enhancing its reputation in the technology sector.
Question
Does Jack possess the necessary knowledge and skills required of an auditor? Refer to Scenario 3.
The auditor was unable to identify that Company A hid their insecure network architecture. What type of audit risk is this?
Question
Another auditor appointed by the certification body reviews the audit team leader’s working documents before the audit conclusions are finalized. According to good auditing practice, which statement is correct?
Question:
How does predictive analytics help auditors in identifying potential risks?
Which two options are benefits of third-party accredited certification of information security management systems to ISO/IEC 27001:2022 for organisations and interested parties?
Select the words that best complete the sentence:
To complete the sentence with the word(s) click on the blank section you want to complete so that it is highlighted in red, and then click on the application text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.

You are performing an ISO 27001 ISMS surveillance audit at a residential nursing home, ABC Healthcare Services. ABC uses a healthcare mobile app designed and maintained by a supplier, WeCare, to monitor residents' well-being. During the audit, you learn that 90% erf the residents' family members regularly receive medical device advertisements from WeCare, by email and SMS once a week. The service agreement between ABC and WeCare prohibits the supplier from using residents' personal data. ABC has received many complaints from residents and their family members.
The Service Manager says that the complaints were investigated as an information security incident which found that they were justified. Corrective actions have been planned and implemented according to the nonconformity and corrective action management procedure.
You write a nonconformity "ABC failed to comply with information security control A.5.34 (Privacy and protection of PII) relating to the personal data of residents' and their family members. A supplier, WeCare, used residents' personal information to send advertisements to family members"
Select three options of the corrections and corrective actions listed that you would expect ABC to make in response to the nonconformity
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
Based on scenario 9, why was UpNefs certification suspended?
You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leader. You are presently in the auditee's data centre with another member of your audit team.
Your colleague seems unsure as to the difference between an information security event and an information security incident. You attempt to explain the difference by providing examples.
Which three of the following scenarios can be defined as information security incidents?
Scenario 7
Lawsy is a leading law firm with offices in Bangkok, Thailand. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implementing information security best practices and remaining up to date with technological developments.
Lawsy has rigorously implemented, evaluated, and conducted internal audits for the information security management system (ISMS) for two years. Now, they have applied for ISO/IEC 27001 certification at ISMA, a well-known and trusted certification body.
During the stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation phase. They also reviewed and evaluated the records from management reviews and internal audits. Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing insight into the internal audit plan and procedures.
The audit team continued verifying strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing the governance framework and the procedures. Following the completion of stage 1, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During the stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Later, the audit team found that Lawsy did not have procedures for using laptops outside the workplace, even though employees were allowed to take laptops outside the workplace. The company only provided general information about the use of laptops and relied on employees’ common knowledge to protect the confidentiality and integrity of information stored on the laptops.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets the requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, the auditor photocopied and archived the examined employee training records after completing the audit.
Question
Lawsy lacks a procedure for using laptops outside the workplace and relies on employees' common knowledge to protect the confidentiality of information stored on the laptops. What does this present?
An organization does not check the source code of the updated version of an application when it is updated automatically. Thus, the application may be open to
unauthorized modifications. This represents a _________________ that may impact information ___________________
You are an experience ISMS audit team leader carrying out a third-party certification audit of an organization specialising in the secure disposal of confidential documents and removable media. Both documents and media are shredded in military grade devices which make it impossible to reconstruct the original.
The audit has gone well and you are just about to start to write the audit report, 30 minutes before the closing meeting. At
this point one of the organization's employees knocks on your door and asks if they can speak to you. They tell you that when things get busy her manager tells her to use a lower grade industrial shredder instead as the organisation has more of these and they operate faster. You were not informed about the existence or use of these machines by the auditee.
Select three options for how you should respond to this information.
Which two of the following options do not participate in a second-party audit to ISO/IEC 27001?
You are an experienced ISMS audit team leader, talking to an Auditor in training who has been assigned to your audit team. You want to ensure that they understand the importance of the Check stage of the Plan-Do-Check-Act cycle in respect of the operation of the information security management system.
You do this by asking him to select the words that best complete the sentence:
To complete the sentence with the best word(s), click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.