
Fortinet NSE 5 - FortiAnalyzer 7.6 Analyst
Last Update Feb 28, 2026
Total Questions : 67
We are offering FREE FCP_FAZ_AN-7.6 Fortinet exam questions. All you do is to just go and sign up. Give your details, prepare FCP_FAZ_AN-7.6 free exam questions and then go for complete pool of Fortinet NSE 5 - FortiAnalyzer 7.6 Analyst test questions that will help you more.



After a generated a repot, you notice the information you were expecting to see in not included in it. However, you confirm that the logs are there:
Which two actions should you perform? (Choose two.)
What are the two methods you can use to send notifications when an event is generated by an event handler? (Choose two answers)
You discover that a few reports are taking a long tine lo generate. Which two steps can you Like to troubleshoot? (Choose two.)
(Refer to the exhibit.
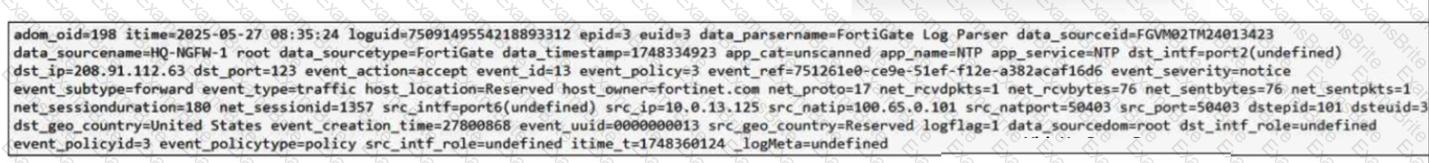
Which two observations can you make after reviewing this log entry? (Choose two answers))
Which two statements about local logs on FortiAnalyzer are true? (Choose two.)
(In a FortiAnalyzer Fabric deployment, which three modules from Fabric members are available for analysis on the supervisor? (Choose three answers))
What is the purpose of using data selectors when configuring event handlers?
Exhibit.
Laptop1 is used by several administrators to manage FotiAnalyzer. You want to configure a generic text filter that matches all login attempts to the web interface generated by any user other than admin’’, and coming from Laptop1.
Which filter will achieve the desired result?
(Refer to the exhibit.
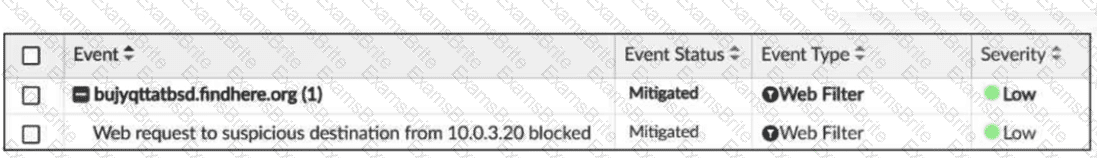
Which statement about the displayed event is correct? (Choose one answer))
You are trying to configure a task in the playbook editor to run a report.
However, when you try to select the desired playbook, you do to see it listed.
What is the reason?
Aplaybook contains five tasks in total. An administrator runs the playbook and four out of five tasks finish successfully, but one task fails.
What will be the status of the playbook after it is run?
Which two actions should an administrator take to vide Compromised Hosts on FortiAnalyzer? (Choose two.)
You created a playbook on FortiAnalyzer that uses a FortiOS connector.
When configuring the FortiGate side, which type of trigger must be used so that the actions in an automation stich are available in the FortiOS connector?
Which statement correctly describes one Difference between templates and reports?