
Certified in Planning and Inventory Management (CPIM 8.0)
Last Update Feb 28, 2026
Total Questions : 585
We are offering FREE CPIM-8.0 APICS exam questions. All you do is to just go and sign up. Give your details, prepare CPIM-8.0 free exam questions and then go for complete pool of Certified in Planning and Inventory Management (CPIM 8.0) test questions that will help you more.



An organization currently has a network with 55,000 unique Internet Protocol (IP) addresses in their private Internet Protocol version 4 (IPv4) network range and has acquired another organization and must integrate their 25,000 endpoints with the existing, flat network topology. If subnetting is not implemented, which network class is implied for the organization’s resulting private network segment?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
What is the BEST way to plan for power disruptions when implementing a Disaster Recovery Plan (DRP)?
Small, independent demands for components and subassemblies typically arise from which of the following sources?
Bad actors with little expense can easily make calls. Which social engineer strategy is a telecommunications ONLY risk concept?
Which of the below represent the GREATEST cloud-specific policy and organizational risk?
Which of the following are steps involved in the identity and access provisioning lifecycle?
The project manager has updated the project steering committee that a security vulnerability was found after applying the system security baseline, and remediation has been completed to close the vulnerability. What is the BEST next step for the project?
A company with stable demand that uses exponential smoothing to forecast demand would typically use a:
A planner has chosen to increase the order point for a raw material. Which of the following costs is most likely to increase?
What is an important countermeasure to consider when hardening network devices and servers to reduce the effectiveness of unauthorized network scanning?
Which of the following is MOST accurate when comparing patch management and vulnerability management?
Which of the following regarding authentication protocols is a PRIMARY consideration when designing an authentication and key management system?
An organization has network services in a data center that are provisioned only for internal use, and staff at offices and staff working from home both use the services to store sensitive customer data. The organization does not want the Internet Protocol (IP) address of the service to receive traffic from users not related to the organization. Which technology is MOST useful to the organization in protecting this network?
A semiconductor manufacturer is writing a physical asset handling policy. Which of the following is MOST likely to be the rationale for the policy?
One of the benefits of Integrating a poka-yoke into the production process is that it can be used to:
An organization has integrated its enterprise resource planning system into its centralized Identity and Access Management (IAM) system to automate provisioning of access. A security audit revealed that privileged access granted within the ERP system is not visible in the IAM system. Which of the following controls BEST mitigates this risk?
In a Discretionary Access Control (DAC) model, how is access to resources managed?
An organization is aiming to be System and Organization Controls (SOC) 2 certified by an audit organization to demonstrate its security and availability maturity to its sub service organizations. Which type of audit does this engagement BEST describe?
A company assembles kits of hand tools after receipt of the order from distributors and uses two-level master scheduling. The appropriate levels of detail for the forecasts that are input to master scheduling would be total number of kits and:
A financial institution is implementing an Information Technology (IT) asset management system. Which of the following capabilities is the MOST important to include?
What is the BEST protection method to ensure that an unauthorized entry attempt would fail when securing highly sensitive areas?
Which of the following systems would be the most cost-efficient for inventory management of a low value item?
In which of the following environments is capable-to-promise (CTP) more appropriate than available-to-promise (ATP)?
Which of the following security features is utilized to validate both user credentials and the health of the client device on a network?
Which of the following procedures should be defined when establishing information and asset handling requirements?
A large volume of outbound Transmission Control Protocol (TCP) connections from the same source Internet Protocol (IP) address was observed at a satellite office firewall. Which of the following is the MOST likely explanation?
Which specification enables organizations to ensure penetration test results are documented using open, machine-readable standards?
Which of the following is the MAIN element in achieving a successful security strategy?
If fixed costs are §200,000 and 20,000 units are produced, a unit's fixed cost is §10. This is an example of:
An organization needs a firewall that maps packets to connections and uses Transmission Control Protocol/Internet Protocol (TCP/IP) header fields to keep track of connections. Which type of firewall will be recommended?
Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
Which of the following techniques is BEST suited to preserve the confidentiality of a system’s data?
What is the FIRST element that must be evaluated in a security governance program?
Which of the following should Business Impact Analysis (BIA) reports always include?
Which of the following vulnerability types is also known as a serialization flaw and affects the integrity of two processes interacting with the same resource at the same time?
In restoring the entire corporate email system after a major outage and data loss, an email administrator reads a few email message exchanges between the human resources manager and a candidate for an open position. Which of the following BEST describes the behavior of the email administrator, and why?
Access Control Lists (ACL), protection bits, and file passwords are typical examples of which of the following access control methods?
An attacker was able to identify an organization’s wireless network, collect proprietary network resource information, and capture several user credentials. The attacker then used that information to conduct a more sophisticated and impactful attack against the organization. Which method did the attacker MOST likely use to gather the initial information?
An organization is implementing an enterprise resource planning system using the traditional waterfall Software development Life Cycle (SDLC) model. When is the BEST time to perform a code review to identity security gaps?
The development team wants new commercial software to Integrate into the current systems. What steps can the security office take to ensure the software has no vulnerabilities?
An organization wishes to utilize a managed Domain Name System (DNS) provider to reduce the risk of users accessing known malicious sites when web browsing. The organization operates DNS forwarders that forward queries for all external domains to the DNS provider. Which of the following techniques could enable the organization to identify client systems that have attempted to access known malicious domains?
A security professional is accessing an organization-issued laptop using biometrics to remotely log into a network resource. Which type of authentication method is described in this scenario?
An organization requires all passwords to include two uppercase characters, two numbers, and two special characters. After a security professional has successfully retrieved the hashed password file from a server, what would be the fastest attack to conduct on the file?
A bank recently informed a customer that their account has been overdrawn after their latest transaction. This transaction was not authorized by the customer. Upon further investigation, it was determined by the security team that a hacker was able to manipulate the customer's pre-authenticated session and force a wire transfer of funds to a foreign bank account. Which type of attack MOST likely occurred?
Which of the following describes the 3 MAIN roles of the identity-delegation model?
Which of the following provides for continuous improvement of the change control process?
An organization wants to control access at a high-traffic entrance using magnetic-stripe cards for identification. Which of the following is the BEST for the organization to utilize?
Which burden of proof has been applied when a workplace investigation has a 51 percent or greater certainty that allegations are true?
An organization has a call center that uses a Voice Over Internet Protocol (VoIP) system. The conversations are sensitive, and the organization is concerned about employees other than the call agents accessing these conversations. What is the MOST effective additional security measure to make?
A vendor has been awarded a contract to supply key business software. The vendor has declined all requests to have its security controls audited by customers. The organization insists the product must go live within 30 days. However, the security team is reluctant to allow the project to go live. What is the organization's BEST next step?
As a result of a fault at a cloud service provider’s data center, the customer accounts of a utility organization were corrupted. Under the European Union’s (EU) General Data Protection Regulation (GDPR), which entity bears responsibility for resolving this?
An organization has hired a new auditor to review its critical systems infrastructure for vulnerabilities. Which of the following BEST describes the methodology the auditor will use?
A part is sold as a service part, and It is also used as a component In another part. Which of the following statements about the planning for this part is true?
A plant uses a level production strategy due to the high costs of hiring and letting go of skilled employees. The constrained resource is due to be upgraded in the fourth month of the planning horizon, and that will reduce capacity for that month by 17%.
Which of the following actions would be appropriate in this situation to maintain current levels of customer service and gross margin?
According to best practice, at which step in the system lifecycle shall a security professional begin involvement?
When resolving conflicts, which canon within the ISC2 Code of Ethics requires members to consider duties to principals and Individuals?
An organization is working to secure its Supervisory Control And Data Acquisition (SCADA) system, Which monitors water supply to the city. What type of security should the organization ensure FIRST?
The trade-off of increasing safety stock to improve customer fill rate would be a decrease in:
The primary reason for tracing a component with scheduling problems to Its master production schedule (MPS) item is to:
At which Open Systems Interconnection (OSI) layer does User Datagram Protocol (UDP) function?
An effective approach to projecting requirements for materials with long lead times Includes which of the following options?
Which of the following is the BEST way to identify the various types of software installed on an endpoint?
The Data Loss Prevention (DLP) team in a major financial institution discovered network traffic that involved movement of sensitive material to a Cloud Service Provider (CSP). What action should be taken FIRST in this situation?
A security practitioner notices that workforce members retain access to information systems after transferring to new roles within the organization, which could lead to unauthorized changes to the information systems.
This is a direct violation of which common security model?
Long lead-time items with stable demand would best be supported by a supply chain:
An organization uses an external Identity Provider (IdP) to secure internal, external, or third-party applications. Which of the following is the GREATEST risk to the organization?
To mitigate risk related to natural disasters, an organization has a separate location with systems and communications in place. Data must be restored on the remote systems before they are ready for use. What type of remote site is this?
Which assessing whether real-world threats to the security of an application have been mitigated, what is MOST effective source to confirm that sufficient security controls are in place for both end users and customers?
Which of the following trade-offs should be evaluated when determining where to place inventory in a multi-echelon supply chain network?
Which of the following statements correctly describes the relationship between the strategic plan and the business plan?
A company can easily change Its workforce, but inventory carrying costs are high. Which of the following strategies would be most appropriate during times of highly fluctuating demand?
Which of the following should be performed FIRST in the course of a digital forensics investigation?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
An organization has been struggling to improve their security posture after a recent breach.
Where should the organization focus their efforts?
An agency has the requirement to establish a direct data connection with another organization for the purpose of exchanging data between the agency and organization systems. There is a requirement for a formal agreement between the agency and organization. Which source of standards can the system owners use to define the roles and responsibilities along with details for the technical and security requirements?
Up-to-date Information about production order status is required to do which of the following tasks?
Disaster Recovery (DR) training plan outcomes should have which KEY quality?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
Which of the following methods places a replenishment order when the quantity on hand falls below a predetermined level?
Which of the following attributes describes a company with a global strategy?
Which of the following presents the GREATEST benefit to an organization's security posture when a change management process is implemented?
Which of the following tools shows process changes and random variation over time?
An organization is planning to streamline its Identity and Access Management (IAM) processes and platform. The executive team mandated a compact platform to efficiently manage identities for internal and third-party services access. What is the BEST platform choice?
An organization is implementing improvements to secure the Software Development Life Cycle (SDLC). When should defensive three modeling occur?
What General Data Protection Regulation (GDPR) principle says that data should be collected lawfully and with the person’s consent?
A third-party vendor is procured to conduct a non-financial audit. Which report evaluates the effectiveness of the controls?
Following the go-live of a new financial software, an organization allowed the Information Technology (IT) officer to maintain all rights and access permissions to help the organization staff should they have challenges in their day-to-day work. What is the BEST way to categorize the situation?
Substituting capital equipment in place of direct labor can be economically Justified for which of the following scenarios?
Which of the following is the MOST significant flaw when using Federated Identity Management (FIM)?
A financial services organization wants to deploy a wireless network. Which of the following is the WEAKEST option for ensuring a secure network?
An independent risk assessment determined that a hospital's existing policies did not have a formal process in place to address system misuse, abuse, or fraudulent activity by internal users. Which of the following would BEST address this deficiency in the Corrective Action Plan?
Which of the following design considerations would offer the BEST protection against unauthorized access to the facility?
Which of the following controls should a financial Institution have in place in order to prevent a trader from both entering and executing a trade?
An organizational policy requires that any data from organization-issued devices be securely destroyed before disposal. Which method provides the BEST assurance of data destruction?
A manufacturer has a primary assembly line supported by output from several subassembly lines. Which of the following scenarios would be the best argument for a multilevel master scheduling process?
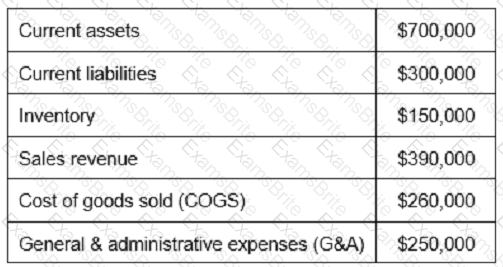
Based on the values reported in the table below, what is the inventory turnover?
Capacity requirements planning (CRP) is applicable primarily In companies operating In an environment where:
Which of the following statements characterizes a pull system In distribution management?
An organization has a legacy application used in production. Security updates are no longer provided, which makes the legacy application vulnerable. The legacy application stores Social Security numbers and credit card numbers. Which actions will BEST reduce the risk?
Which of the following capabilities BEST distinguishes a Next-Generation Firewall (NGFW) from a traditional firewall?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
Which of the following statements best characterizes enterprise resources planning (ERP) systems?
Which of the following should be done FIRST when implementing an Identity and Access Management (IAM) solution?
An organization's security policy requires sensitive information to be protected when being transmitted to external sources via would be the BEST security solution to choose?
Which of the following documents is the BEST reference to describe application functionality?
When designing a production cell, which of the following items would be the most important consideration?
An information system containing Protected Health Information (PHI) will be accessed by doctors, nurses, and others working in a hospital. The same application will be used by staff in the pharmacy department only for dispensing prescribed medication. Additionally, patients can log in to view medical history. The system owner needs to propose an access control model that considers environment, situation, compliance, and security policies while dynamically granting the required level of access. Which access control model is the MOST suitable?
Business management should be engaged in the creation of Business Continuity (BC) and Disaster Recovery plans (DRP) because they need to
A large retail organization will be creating new Application Programming Interfaces (API) as part of a customer-facing shopping solution. The solution will accept information from users both inside and outside of the organization. What is the safest software development practice the team can follow to protect the APIs against Structured Query Language Injection (SQLi) attacks?
Which of the following circumstances would cause a move from acceptance sampling to 100% inspection?
Increased use of third-party logistics (3PL) services is likely to have which of the following effects on a firm's balance sheet?
After a recent threat modeling workshop, the organization has requested that the Chief Information Security Officer (CISO) implement zero trust (ZT) policies. What was the MOST likely threat identified in the workshop?
Who is ultimately responsible for ensuring that specific data is protected?
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
Which of the following BEST describes an individual modifying something the individual is not supposed to?
Which of the following is the BEST option for a security director to use in order to mitigate the risk of inappropriate use of credentials by individuals with administrative rights?
A company that uses concurrent engineering is likely to experience which of the following outcomes in the first period of a product's life cycle?
In the context of mobile device security, which of the following BEST describes why a walled garden should be implemented?
Endpoint security needs to be established after an organization procured 1,000 industrial Internet Of Things (IoT) sensors. Which of the following challenges are the security engineers MOST likely to face?
Which authentication method is used by an email server to verify that a sender’s Internet Protocol (IP) address is authorized to send messages by the sending domain?
A potentially life-threatening vulnerability is found in vendor software that is used to manage critical systems. Which of the following is generally considered the BEST method to disclose the vulnerability from an ethical hacking perspective?
A security engineer is implementing an authentication system for a new web application. The authentication requirements include the ability for a server to authenticate the client and for the client to authenticate the server. Which of the following choices BEST supports this requirement?
While doing a penetration test, auditors found an old credential hash for a privileged user. To prevent a privileged user's hash from being cached, what is the MOST appropriate policy to mandate?
In order to meet retention requirements, it may be necessary to migrate digital records to different media because of which of the following issues?
A cloud-based web application requires the use of cryptographic keys to encrypt user-uploaded files at rest. Where is the safest place to store these cryptographic keys?
Which Virtual Private Network (VPN) protocol provides a built-in encryption?
An organization is designing a new Disaster Recovery (DR) site. What is the BEST option to harden security of the site?
An organization provides customer call center operations for major financial services organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
Health information stored in paper form may be destroyed using which of the following methods?
An organization implemented a threat modeling program focusing on key assets. However, after a short time it became clear that the organization was having difficulty executing the threat modeling program.
Which approach will MOST likely have been easier to execute?
After a recent cybersecurity incident, a manufacturing organization is interested in further hardening its Identity and Access Management (IAM) solution. Knowing that the organization limits the use of personal devices in the facility, which could BEST be implemented to enhance the manufacturing organization's IAM solution?
If organizational leadership determines that its required continuous monitoring plan is too costly for the organization, what action should be taken by leadership and the Authorizing Official (AO)?
Open Authorized (OAuth) has been chosen as technology to use across applications in the enterprise. Which of the following statements is TRUE about an OAuth token?
A cybersecurity professional has been tasked with instituting a risk management function at a new organization. Which of the following is the MOST important step the professional should take in this endeavor?
Which of the following actions provides the BEST evidence for forensic analysis of powered-off device?
The results of a threat campaign show a high risk of potential intrusion. Which of the following parameters of the Common Vulnerability Scoring System (CVSS) will MOST likely provide information on threat conditions for the organization to consider?
Which Open Systems Interconnection (OSI) layer is concerned with Denial-Of-Service (DoS) SYN flood attacks?
Which of the following threats MUST be included while conducting threat modeling for a Cloud Service Provider (CSP)?
During an emergency management and planning session, an organization is discussing how to identify, prevent, prepare for, or respond to emergencies. Which of the following will provide the BEST possible outcome?
APerform drills on a recurring basis.
B.Harden all critical facilities.
C.Outsource to an external organization.
D.Allocate 100% of required funds.
A forecasting method that responds slowly to changes in demand would be most appropriate when the historical demand pattern shows a:
Which of the following items does the master scheduler have the authority to change in the master scheduling process?
The Business Continuity Plan (BCP) has multiple components. The information security plan portion must prioritize its efforts. Which 3 aspects of information security MUST be prioritized?
A security consultant is recommending the implementation of a security-focused Configuration Management (CM) process in an organization. What would be the BEST benefit the security consultant would include in the recommendation?
To ensure the quality of its newly developed software, an organization is aiming to deploy an automated testing tool that validates the source code. What type of testing BEST supports this capability?
Which of the following MUST exist for an activity to be considered an audit?
A systems engineer has been tasked by management to provide a recommendation with a prioritized, focused set of actions to help the organization stop high-risk cyber attacks and ensure data security. What should the systems engineer recommend the organization use to accomplish this?
What is the PRIMARY benefit an organization obtains by adapting a cybersecurity framework to their cybersecurity program?
A contractor hacked into an unencrypted session on an organization's wireless network. Which authentication configuration is MOST likely to have enabled this?
Which of the following terms below BEST describes the measure of confidence that the security features, practices, procedures, and architecture of an information system accurately mediates and enforces security policy?
When conducting a vulnerability test using a scanner tool, which unintended consequence can occur?
An organization’s computer incident response team PRIMARILY responds to which type of control?
An organization is concerned that if an employee’s mobile device is lost or stolen and does not reconnect to the carrier network, the data on the device may still be at risk. Consequently, the organization has implemented a control on all mobile devices to require an eight-character passcode for unlock and login. What should happen after multiple incorrect passcode attempts?
Which of the following is an access control method that organizations can use to prevent unauthorized access?