
IBM Security QRadar SIEM V7.5 Analysis
Last Update Feb 28, 2026
Total Questions : 139
We are offering FREE C1000-162 IBM exam questions. All you do is to just go and sign up. Give your details, prepare C1000-162 free exam questions and then go for complete pool of IBM Security QRadar SIEM V7.5 Analysis test questions that will help you more.



An analyst is looking at flow payload. The analyst noted the payload is truncated.
|at default value size for the payload is exceeded where the payload might contain additional information that is not shown in the QRadar surface?
Which two (2) values are valid for the Offense Type field when a search is performed in the My Offenses or All Offenses tabs?
Which two (2) aggregation types ate available for the pie chart in the Pulse app?
What is the effect of toggling the Global/Local option to Global in a Custom Rule?
A new log source was configured to send events to QRadar to help detect a malware outbreak. A security analyst has to create an offense based on properties from this payload but not all the information is parsed correctly.
What is the sequence of steps to ensure that the correct information is pulled from the payload to use in a rule?
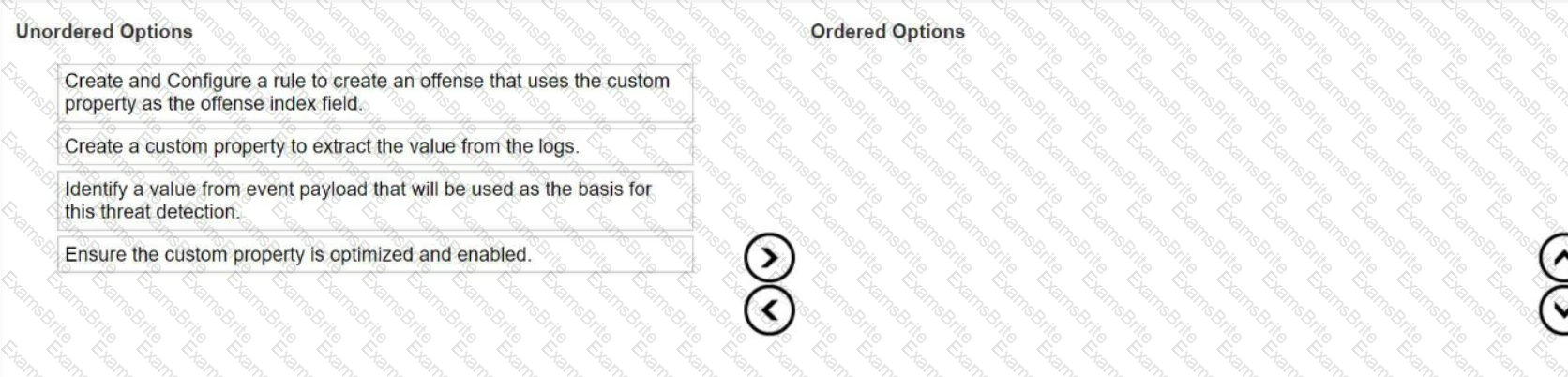
Which type of rule requires a saved search that must be grouped around a common parameter
Which two (2) aggregation types are available for the pie chart in the Pulse app?
How can adding indexed properties to QRadar improve the efficiency of searches?
Which two (2) statements regarding indexed custom event properties are true?
Which reference set data element attribute governs who can view its value?
After how much time will QRadar mark an Event offense dormant if no new events or flows occur?
Which two (2) components are necessary for generating a report using the QRadar Report wizard?
A QRadar analyst is using the Log Activity screen to investigate the events that triggered an offense.
How can the analyst differentiate events that are associated with an offense?
Which statement regarding the use of the internal structured language of the QRadar database is true?
What right-click menu option can an analyst use to find information about an IP or URL?
Which types of information does QRadar analyze to create an offense from the rule?
QRadar analysts can download different types of content extensions from the IBM X-Force Exchange portal. Which two (2) types of content extensions are supported by QRadar?
What does an analyst need to do before configuring the QRadar Use Case Manager app?
To test for authorized access to a patent, create a list that uses a custom event property for Patent id as the key, and the username parameter as the value. Data is stored in records that map a key to multiple values and every key is unique. Use this list to populate a list of authorized users.
The example above refers to what kind of reference data collections?
What is the primary use of viewing the Magnitude metric on the Offenses tab?
An analyst wishes to review an event which has a rules test against both event and flow data.
What kind of rule is this?
AQRadar analyst can check the rule coverage of MITRE ATT&CK tactics and techniques by using Use Case Manager.
In the Use Case Manager app, how can a QRadar analyst check the offenses triggered and mapped to MITRE ATT&CK framework?
What feature in QRadar uses existing asset profile data so administrators can define unknown server types and assign them to a server definition in building blocks and in the network hierarchy?
Which QRadar component provides the user interface that delivers real-time flow views?
To verify whether the login ID that was used to log in to QRadar is assigned to a user, create a list with the LoginlD parameter.
This example refers to what kind of reference data collections?
What is the benefit of using default indexed properties for searching in QRadar?
On the Dashboard tab in QRadar. dashboards update real-time data at what interval?
What two (2) guidelines should you follow when you define your network hierarchy?
The Use Case Manager app has an option to see MITRE heat map.
Which two (2) factors are responsible for the different colors in MITRE heat map?