
Cisco Certified Design Expert (CCDE v3.1)
Last Update Feb 28, 2026
Total Questions : 349
We are offering FREE 400-007 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 400-007 free exam questions and then go for complete pool of Cisco Certified Design Expert (CCDE v3.1) test questions that will help you more.



You are tasked with the design of a high available network. Which two features provide fail closed environments? (Choose two.)
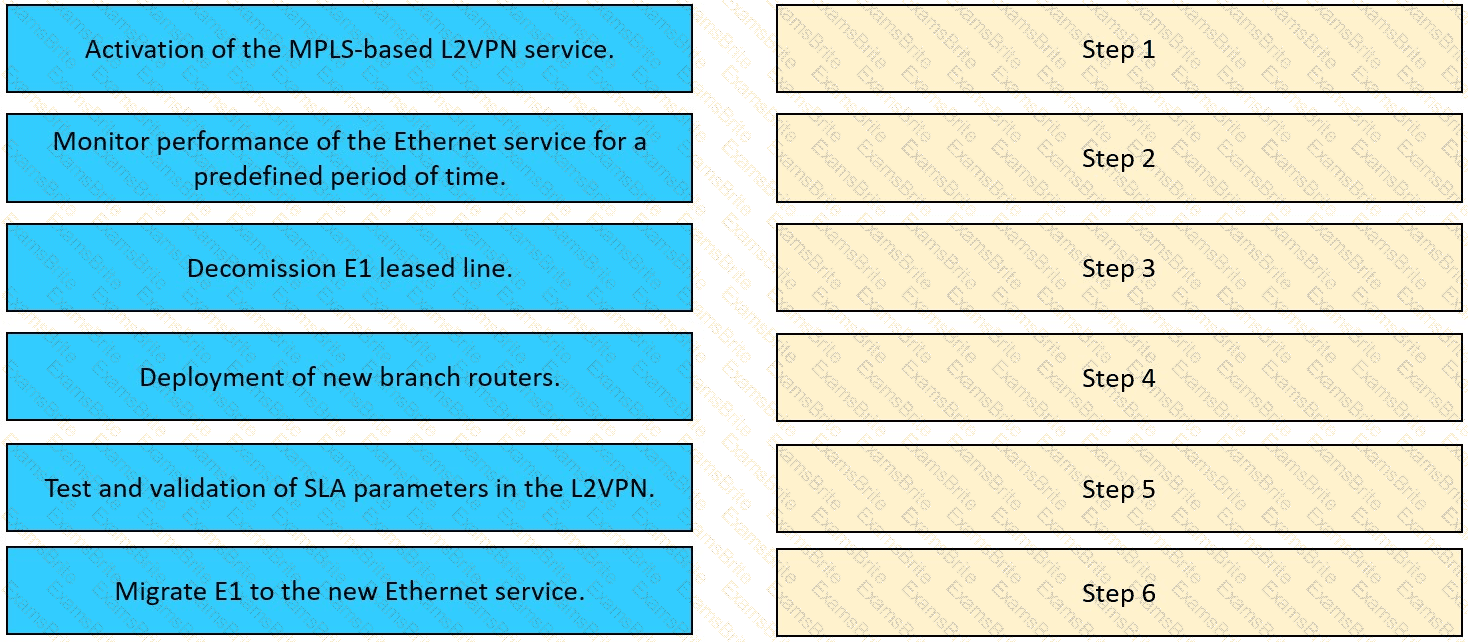
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
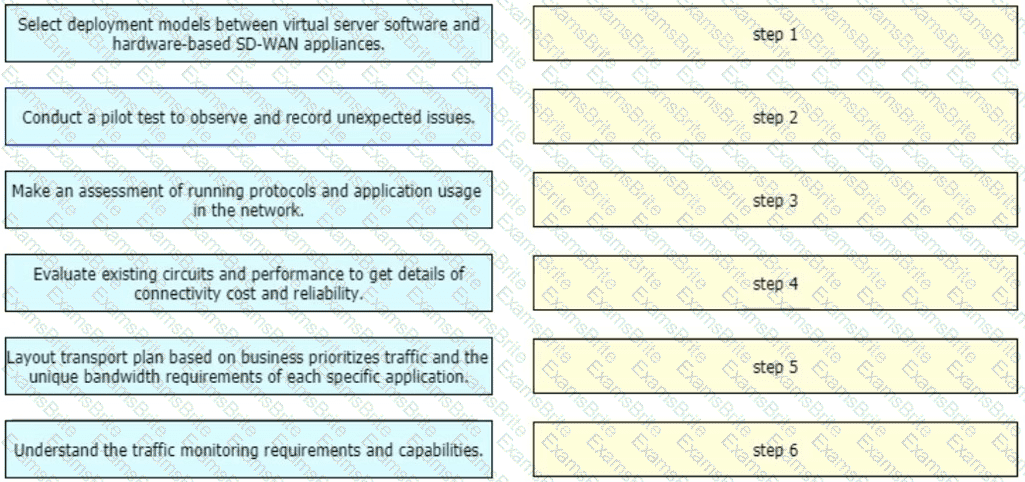
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?
Refer to the exhibit.
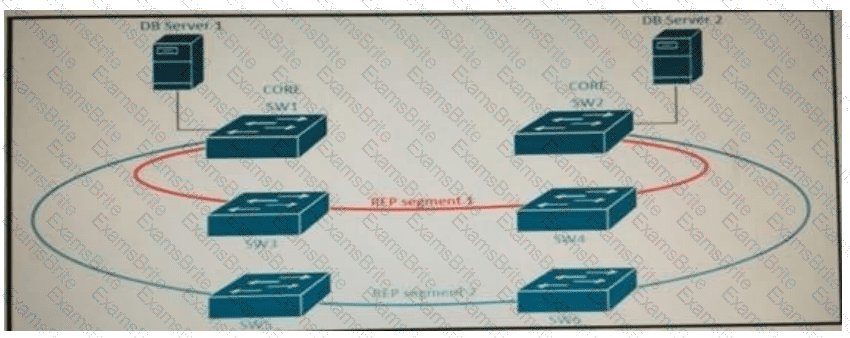
Refer to the exhibit. A new high availability DB server cluster is installed in the network. These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements?
Company XYZ wants to secure the data plane of their network. Which two technologies can be included in the security design? (Choose two)
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
The SD-WAN architecture is composed of separate orchestration, management, control, and data planes. Which activity happens at the orchestration plane?
Refer to the exhibit.
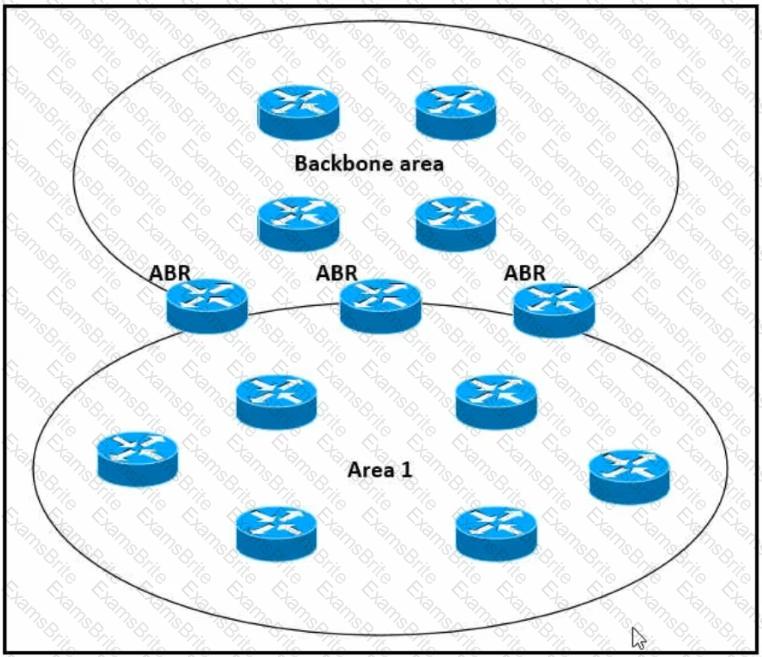
Which impact of using three or more ABRs between the backbone area and area 1 is true?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
An enterprise network has two core routers that connect to 200 distribution routers and uses full-mesh IBGP peering between these routers as its routing method. The distribution routers are experiencing high CPU utilization due to the BGP process. Which design solution is the most cost effective?
You have been tasked with designing a data center interconnect as part of business continuity. You want to use FCoE over this DCI to support synchronous replication. Which two technologies allow for FCoE via lossless Ethernet or data center bridging? (Choose two.)
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
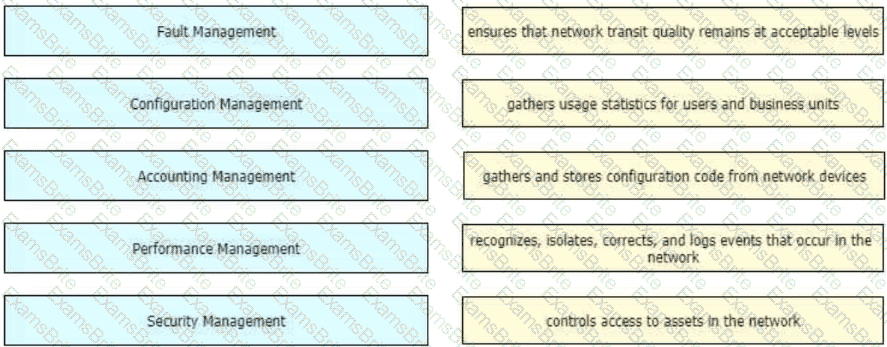
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
An enterprise organization currently provides WAN connectivity to their branch sites using MPLS technology, and the enterprise network team is considering rolling out SD-WAN services for all sites.
With regards to the deployment planning, drag and drop the actions from the left onto the corresponding steps on the right.
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
Which two actions ensure voice quality in a branch location with a low-speed, high-latency WAN connection? (Choose two.)
Refer to the exhibit.
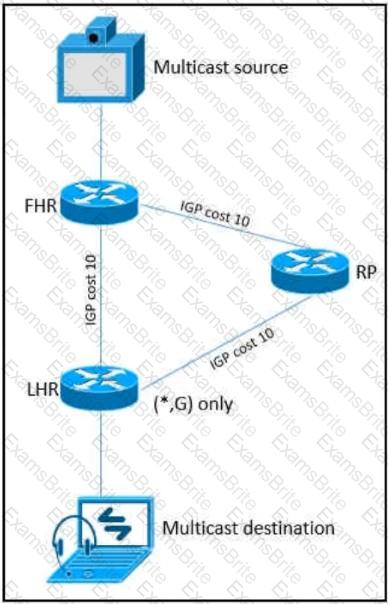
As part of a redesign project, you must predict multicast behavior. What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated?
A Service Provider is designing a solution for a managed CE service to a number of local customers using a single CE platform and wants to have logical separation on the CE platform using Virtual Routing and Forwarding (VRF) based on IP address ranges or packet length. Which is the most scalable solution to provide this type of VRF Selection process on the CE edge device?
A BGP route reflector in the network is taking longer than expected to converge during large network changes. Troubleshooting shows that the router cannot handle all the TCP acknowledgements during route updates. Which action can be performed to tune the device performance?
Which design consideration is valid when you contrast FabricPath and TRILL?
Refer to the exhibit.
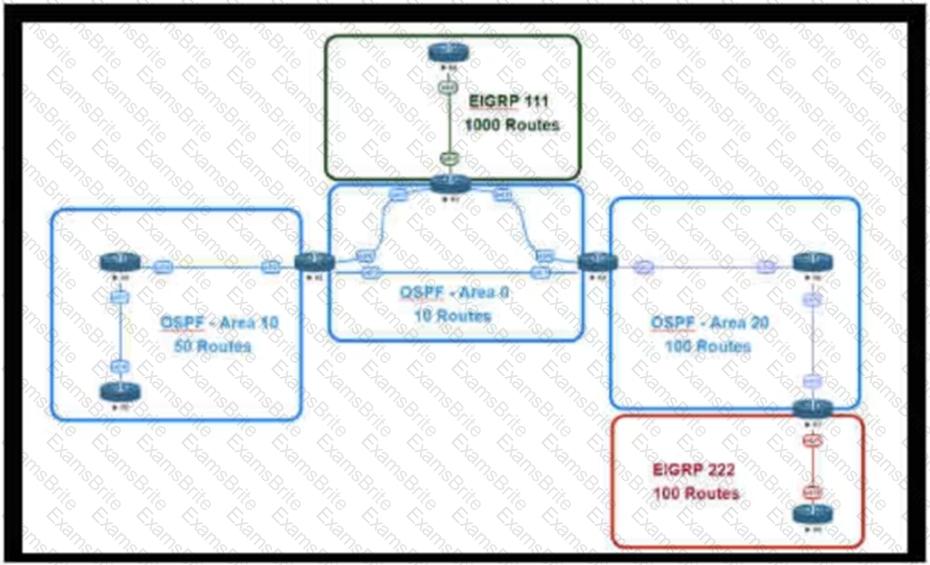
This network is running OSPF and EIGRP as the routing protocols. Mutual redistribution of the routing protocols has been configured on the appropriate ASBRs. The OSPF network must be designed so that flapping routes in EIGRP domains do not affect the SPF runs within OSPF. The design solution must not affect the way EIGRP routes are propagated into the EIGRP domains. Which technique accomplishes the requirement?
Refer to the exhibit.
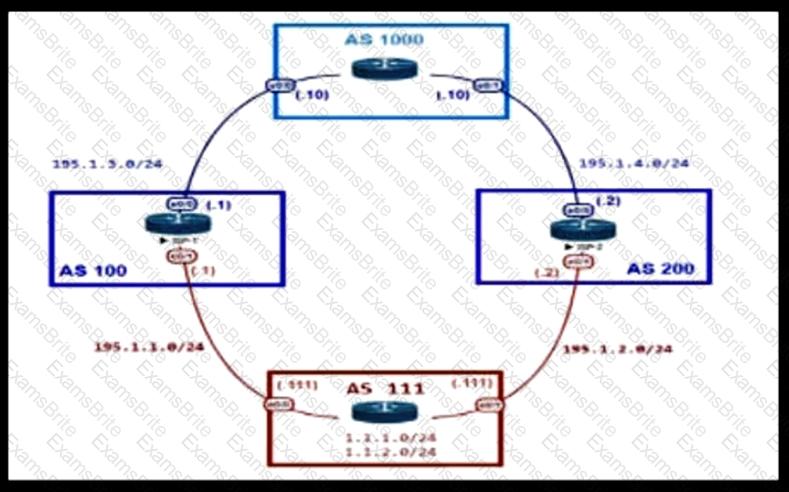
An engineer is designing the network for a multihomed customer running in AS 111. The AS does not have any other ASs connected to it. Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
Company XYZ has a hub-and-spoke topology over an SP-managed infrastructure. To measure traffic performance metrics, they implemented IP SLA senders on all spoke CE routers and an IP SLA responder on the hub CE router. What must they monitor to have visibility on the potential performance impact due to the constantly increasing number of spoke sites?
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
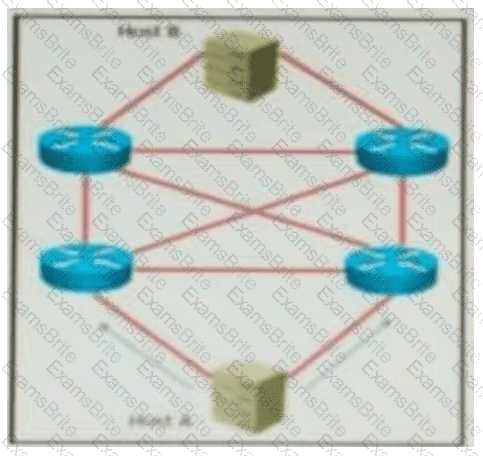
Refer to the exhibit. All links are P2P Layer 3. A high availability application is synchronizing data between Host A and Host B. To increase the chance of delivery, the same data is sent twice from Host A on two different NICs toward the two NICs on Host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on Host B?
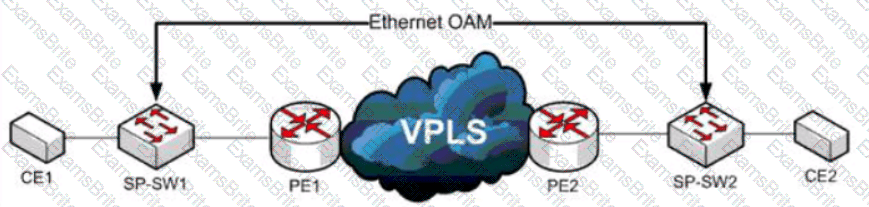
Refer to the exhibit. A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP-SW2. Which two ways to design this solution are true? (Choose two)
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
Company XYZ has 30 sites running a legacy private WAN architecture that connects to the Internet via multiple high-speed connections. The company is now redesigning their network and must comply with these design requirements:
Use a private WAN strategy that allows the sites to connect to each other directly and caters for future expansion.
Use the Internet as the underlay for the private WAN.
Securely transfer the corporate data over the private WAN.
Which two technologies should be incorporated into the design of this network? (Choose two.)
An enterprise solution team is analyzing multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
A Tier-3 Service Provider is evolving into a Tier-2 Service Provider due to the amount of Enterprise business it is receiving. The network engineers are re-evaluating their IP/MPLS design considerations in order to support duplicate/overlapping IP addressing from their Enterprise customers within each Layer3 VPN. Which concept would need to be reviewed to ensure stability in their network?
Company XYZ network runs IPv4 and IPv6 and they want to introduce a multidomain, multicast-based network. The new design should use a flavor of PIM that forwards traffic using SPT. Which technology meets this requirement?
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection. Which technology meets the updated requirements and can be incorporated into the design?
Refer to the exhibit.
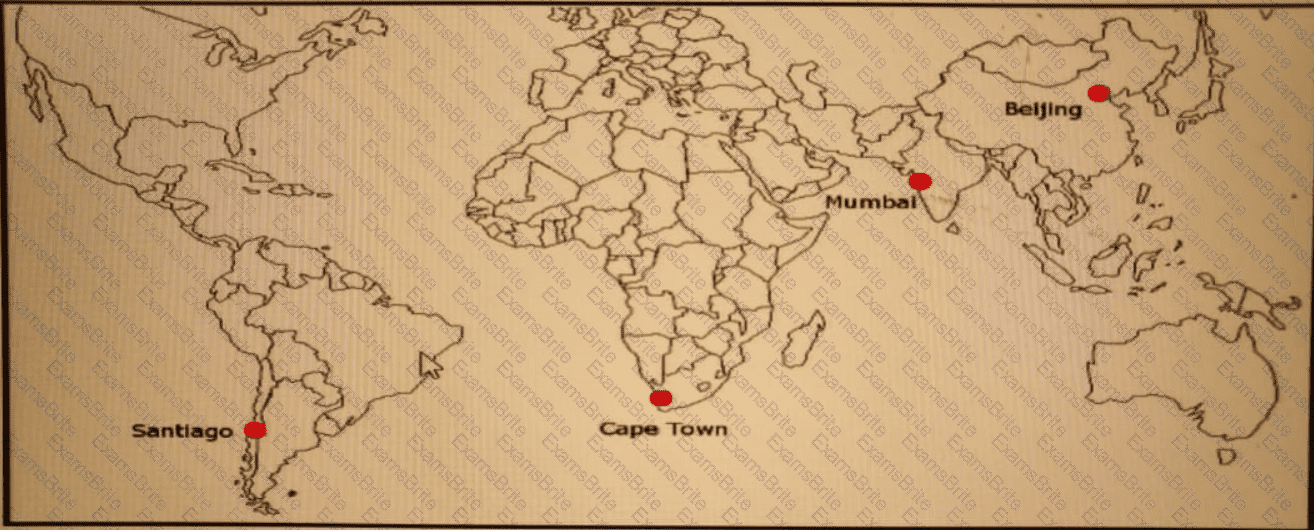
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
clusterheartbeat2Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
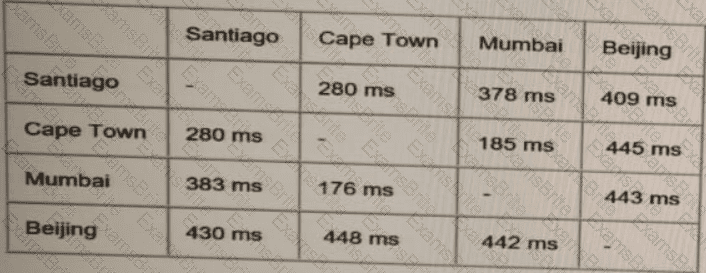
Which hosting data center pair can host the new application?
Refer to the exhibit.
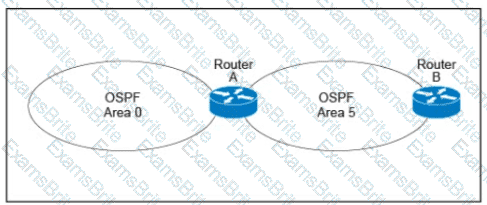
A customer runs OSPF with Area 5 between its aggregation router and an internal router. When a network change occurs in the backbone, Area 5 starts having connectivity issues due to the SPF algorithm recalculating an abnormal number of times in Area 5. You are tasked to redesign this network to increase resiliency on the customer network with the caveat that Router B does not support the stub area. How can you accomplish this task?
A multicast network is using Bidirectional PIM. Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
Company XYZ wants to use the FCAPS ISO standard for network management design, focusing on minimizing outages through detection, isolation, and corrective actions. Which layer accomplishes this design requirement?
You are designing a large-scale DMVPN network with more than 500 spokes using EIGRP as the IGP protocol. Which design option eliminates potential tunnel down events on the spoke routers due to the holding time expiration?
A customer asks you to perform a high-level review of their upcoming WAN refresh for remote sites. The review is specially focused on their retail store operations consisting of 500+ locations connected via multipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
Which two actions must be taken when assessing an existing wireless network implementation for its readiness to support voice traffic? (Choose two.)
A senior network designer suggests that you should improve network convergence times by reducing BGP timers between your CE router and the PE router of the service provider. Which two factors should you consider to adjust the timer values? (Choose two.)
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
Company XYZ wants to deploy OSPF. The design plan requires that two OSPF networks be mutually redistributed at multiple locations and ensure end-to-end connectivity to all of the company's networks. Which technology can be used to fulfill the requirements while avoiding the creation of routing loops?
An Agile for Infrastructure transition often means dismantling traditional IT hierarchies and rebuilding it to align with business objectives and workflows. Organizations are seeing the benefits of using automation tools in the network such as faster, more efficient, and more effective delivery of products and services. Which two components help increase overall productivity and improve company culture? (Choose two.)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Which action must be taken before new VoIP systems are implemented on a network to ensure that the network is ready to handle the traffic?
A service provider recently migrated to an SD-WAN solution for delivering WAN connections to its customers. One of the main challenges with the SD-WAN deployment is that branch site volume increases every year, which causes management complexity. Which action resolves the issue?
The goal for any network designer is to strive to build a resilient network that adapts to changing conditions rapidly with minimal impact on the services running over the network. A resilient network can adapt to failures, but which soft failure can be harder to define and detect?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Which two pain points are the most common for container technology adoption? (Choose two)
Company XYZ is running BGP as their routing protocol. An external design consultant recommends that TCP Path MTU Discovery be enabled. Which effect will this have on the network?
As part of a new network design documentation, you are required to explain the reason for choosing Cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network? (Choose two)
The General Bank of Greece plans to upgrade its legacy end-of-life WAN network with a new flexible, manageable, and scalable solution. The main requirements are ZTP support, end-to-end encryption, application awareness, and segmentation. The CTO states that the main goal of the bank is CAPEX reduction. Which WAN technology should be used for the solution?
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
In outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
You are designing the routing design for two merging companies that have overlapping IP address space. Which of these must you consider when developing the routing and NAT design?
Which protocol does an SD-Access wireless Access Point use for its fabric data plane?
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization. Which IETF standard technology can provide this requirement?
What is a country-specific requirement that data is subject to the laws of the country in which it is collected or processed and must remain within its borders?
Refer to the exhibit.
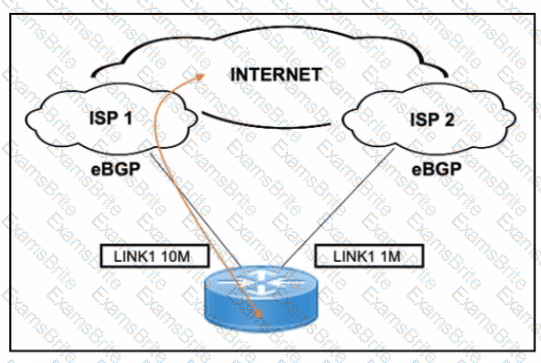
A customer has two eBGP internet links: one primary high-speed (10 Mbps) and one backup low-speed (1 Mbps). The requirement is to use the 10M link (ISP 1) for all inbound/outbound traffic and only use the 1M link (ISP 2) during failure.
What is the correct BGP-based design solution?
You are tasked to design a QoS policy for a service provider so they can include it in the design of their MPLS core network. If the design must support an MPLS network with six classes, and CEs will be managed by the service provider, which QoS policy should be recommended?
Network changes due to mergers, acquisitions, and divestitures can be highly disruptive if not carefully planned. When an organization sells part of its business, it must detach those parts of the network with minimal risk and downtime.
Which network design approach is appropriate to minimize the impact and risks as the divested parts of the network are detached?
You are designing a network running both IPv4 and IPv6 to deploy QoS. Which consideration is correct about the QoS for IPv4 and IPv6?
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?
As a network designer, you need to support an enterprise with hundreds of remote sites connected over a single WAN network that carries different types of traffic, including VoIP, video, and data applications. Which of the following design considerations will not impact design decision?
Which extensions to GRE tunneling provide session tracking and in-order packet delivery in exchange for additional state stored in tunnel endpoints?
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. They want to extend the existing IP CCTV network to a new branch without routing changes or IP address changes. What is the best approach?
Hybrid cloud computing allows organizations to take advantage of public and private cloud models. Which best practice should organizations follow to ensure data security in the private cloud?
Which two points must network designers consider when designing a new network design or when evaluating an existing network design to help them understand the high-level design direction with regards to the security aspects? (Choose two)
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
SD-WAN can be used to provide secure connectivity to remote offices, branch offices, campus networks, data centers, and the cloud over any type of IP-based underlay transport network. Which two statements describe SD-WAN solutions? (Choose two.)
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
You are designing a network for a branch office. In order to improve convergence time, you are required to use the BFD feature. Which four routing protocols can you use to facilitate this? (Choose four.)
As technologies such as big data, cloud, and loT continue to grow, so will the demand for network bandwidth Business strategies must be flexible to accommodate these changes when it comes to priorities and direction and the network design strategy also must be agile and adaptable Drag and drop the benefits from the left onto the corresponding strategic approaches on the right as they relate to network design and management.
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries? (Choose two.)
Refer to the exhibit.
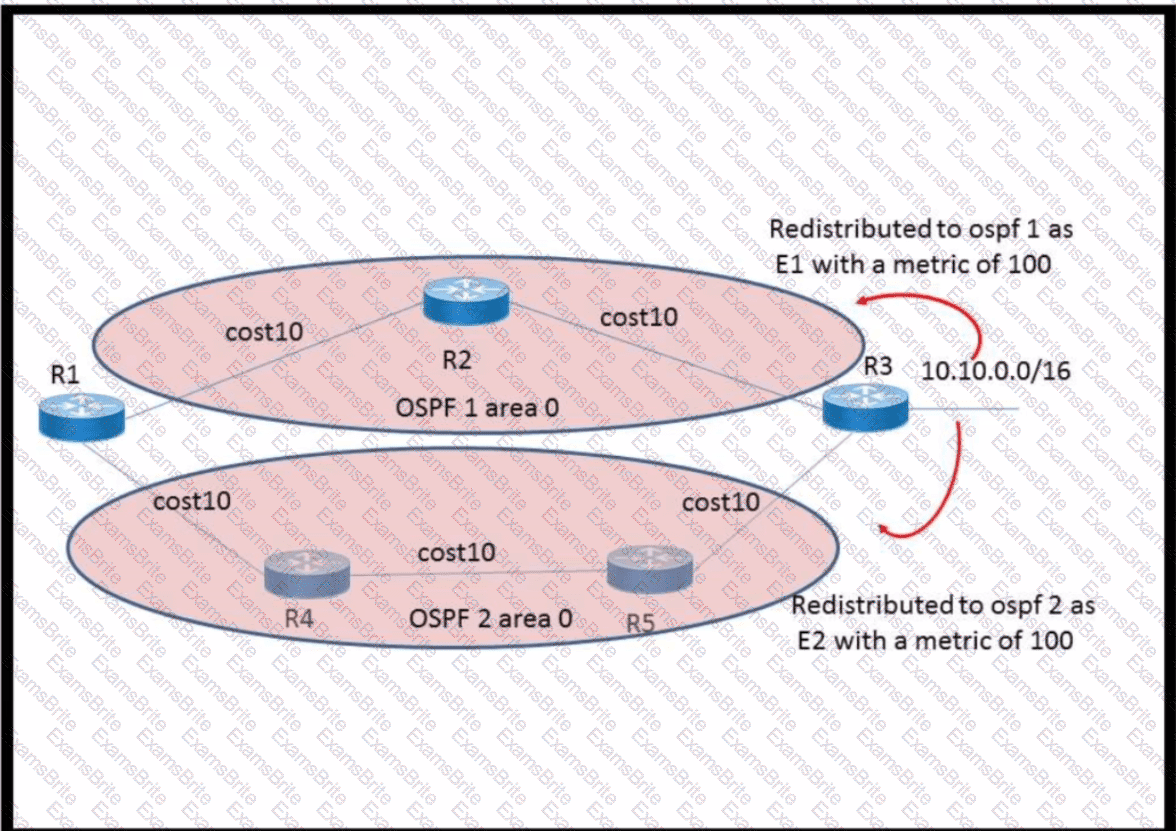
The network 10.10.0.0/16 has been redistributed to OSPF processes and the best path to the destination from R1 has been chosen as R1–R2–R3. A failure occurred on the link between R2 and R3 and the path was changed to R1–R4–R5–R3. What happens when the link between R2 and R3 is restored?
SDN is still maturing. Throughout the evolution of SDN, which two things will play a key role in enabling a successful deployment and avoiding performance visibility gaps in the infrastructure? (Choose two.)
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
Which mechanism enables small, unmanaged switches to plug into ports of access switches without risking switch loops?
Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
Refer to the exhibit.
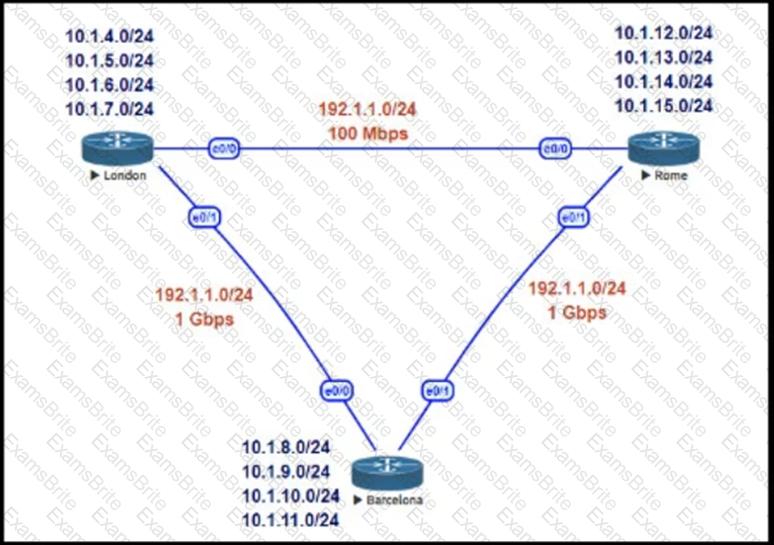
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
Refer to the exhibit.
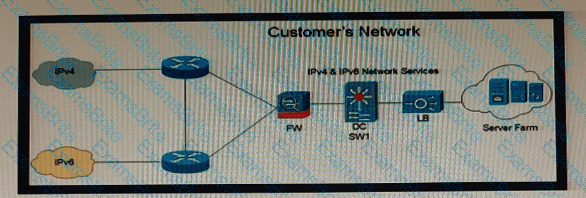
Company XYZ is currently running IPv4 but has decided to start the transition into IPv6. The initial objective is to allow communication based on IPv6 wherever possible, and there should still be support in place for devices that only support IPv4. These devices must be able to communicate to IPv6 devices as well. Which solution must be part of the design?
An architect receives a business requirement from a CTO that states the RTO and RPO for a new system should be as close as possible to zero. Which replication method and data center technology should be used?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
What are two examples of components that are part of an SDN architecture? (Choose two.)
Refer to the exhibit.
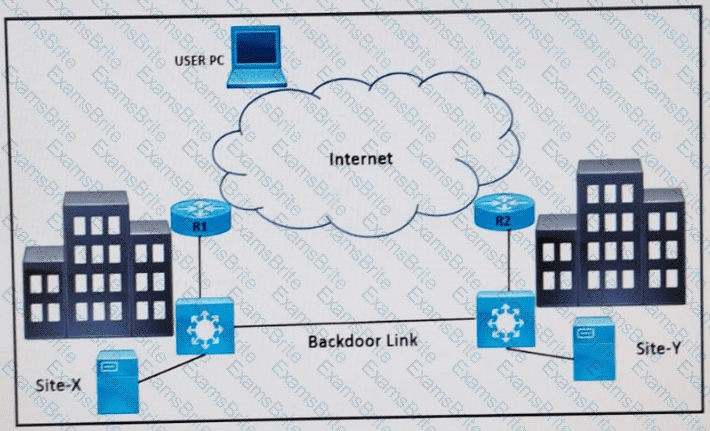
Refer to the exhibit. Two data center sites (X and Y) connect to the Internet and each other using a backdoor link. Both advertise the same IP prefix (100.75.10.0/23) to the Internet. Firewalls are behind R1 and R2.
Problem: When users attempt to reach 100.75.10.0/23, the return traffic is routed to Site-Y, regardless of where the session originated. This results in asymmetric traffic and potentially broken sessions due to firewall behavior.
Which design resolves the issue?
Which two possible drawbacks should you consider when introducing Network Functions Virtualization in a network design? (Choose two.)
An attacker exploits application flaws to obtain data and credentials. What is the next step after application discovery in Zero Trust networking?
Which relationship between IBGP and the underlying physical topology is true?
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
Which two statements describe the functionality of OSPF packet-pacing timers? (Choose two.)