
Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Last Update Feb 28, 2026
Total Questions : 726
We are offering FREE 350-701 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 350-701 free exam questions and then go for complete pool of Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) test questions that will help you more.



An organization wants to reduce their attach surface for cloud applications. They want to understand application communications, detect abnormal application Behavior, and detect vulnerabilities within the applications. Which action accomplishes this task?
Which two capabilities of Integration APIs are utilized with Cisco Catalyst Center? (Choose two.)
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
Which Cisco firewall solution supports configuration via Cisco Policy Language?
A hacker initiated a social engineering attack and stole username and passwords of some users within a company. Which product should be used as a solution to this problem?
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system’s applications. Which
vulnerability allows the attacker to see the passwords being transmitted in clear text?
Which Secure Email Gateway implementation method segregates inbound and outbound email?
An administrator is trying to determine which applications are being used in the network but does not want the
network devices to send metadata to Cisco Firepower. Which feature should be used to accomplish this?
Which two configurations must be made on Cisco ISE and on Cisco TrustSec devices to force a session to be adjusted after a policy change is made? (Choose two)
Which two behavioral patterns characterize a ping of death attack? (Choose two)
v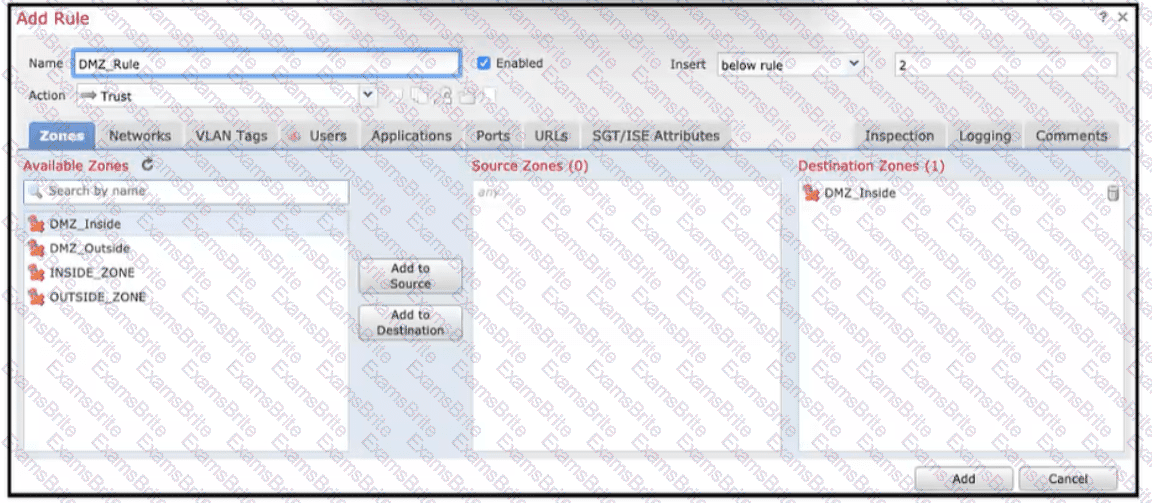
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?
For which type of attack is multifactor authentication an effective deterrent?
Which feature is used in a push model to allow for session identification, host reauthentication, and session termination?
A Cisco Secure Email Gateway network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Secure Email Gateway is not dropping files that have an undetermined verdict. What is causing this issue?
What is a benefit of using Cisco AVC (Application Visibility and Control) for application control?
A web hosting company must upgrade its older, unsupported on-premises servers. The company wants a cloud solution in which the cloud provider is responsible for:
Server patching
Application maintenance
Data center security
Disaster recovery
Which type of cloud meets the requirements?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.)
What must be configured in Cisco ISE to enforce reauthentication of an endpoint session when an endpoint is
deleted from an identity group?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which
probe must be enabled for this type of profiling to work?
An organization wants to secure users, data, and applications in the cloud. The solution must be API-based and
operate as a cloud-native CASB. Which solution must be used for this implementation?
Which technology provides a combination of endpoint protection endpoint detection, and response?
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
A large organization wants to deploy a security appliance in the public cloud to form a site-to-site VPN
and link the public cloud environment to the private cloud in the headquarters data center. Which Cisco
security appliance meets these requirements?
Refer to the exhibit.
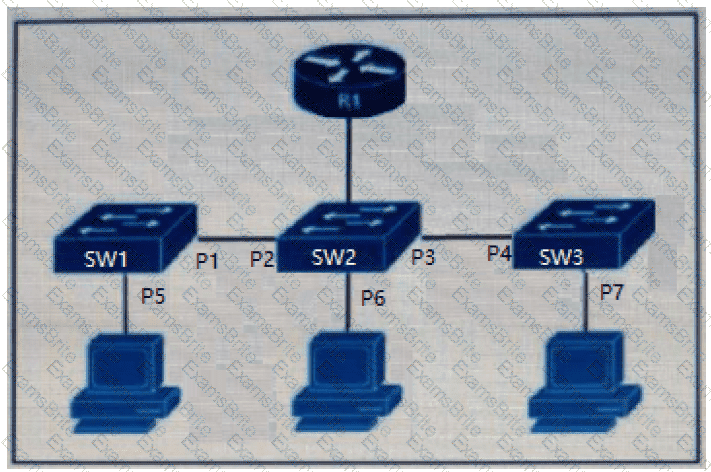
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
What is the function of the crypto is a kmp key cisc406397954 address 0.0.0.0 0.0.0.0 command when establishing an IPsec VPN tunnel?
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats,
which allows the SOC to proactively automate responses to those threats?
Which posture assessment requirement provides options to the client for remediation and requires the
remediation within a certain timeframe?
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance?
(Choose two)
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
Which interface mode does a Cisco Secure IPS device use to block suspicious traffic?

Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
Which parameter is required when configuring a Netflow exporter on a Cisco Router?
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
After deploying a Cisco ESA on your network, you notice that some messages fail to reach their destinations.
Which task can you perform to determine where each message was lost?
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
An engineer needs to detect and quarantine a file named abc424400664 zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints The configured detection method must work on files of unknown disposition Which Outbreak Control list must be configured to provide this?
An engineer is configuring Cisco WSA and needs to enable a separated email transfer flow from the Internet and from the LAN. Which deployment mode must be used to accomplish this goal?
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
Why should organizations migrate to a multifactor authentication strategy?
How does Cisco Workload Optimization Manager help mitigate application performance issues?
Which two preventive measures are used to control cross-site scripting? (Choose two)
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing
authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
Which technology reduces data loss by identifying sensitive information stored in public computing
environments?
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined threshold, to
address this issue?
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively u: of the default policy elements. What else must be done to accomplish this task?
When MAB is configured for use within the 802.1X environment, an administrator must create a policy that allows the devices onto the network. Which information is used for the username and password?
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead. Which solution meets these requirements?
With Cisco AMP for Endpoints, which option shows a list of all files that have been executed in your
environment?
Refer to the exhibit. A network engineer must configure a Cisco router to send traps using SNMPv3. The engineer configures a remote user to receive traps and sets the security level to use authentication without privacy. Which command completes the configuration?
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
Which Cisco AMP feature allows an engineer to look back to trace past activities, such as file and process activity on an endpoint?
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
Which two activities are performed using Cisco Catalyst Center? (Choose two.)
A company identified a phishing vulnerability during a pentest. What are two ways the company can protect employees from the attack? (Choose two.)
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.

Which Cisco cloud security software centrally manages policies on multiple platforms such as Cisco ASA, Cisco Firepower, Cisco Meraki, and AWS?
An organization configures Cisco Umbrella to be used for its DNS services. The organization must be able to block traffic based on the subnet that the endpoint is on but it sees only the requests from its public IP address instead of each internal IP address. What must be done to resolve this issue?
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two)
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however it is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the
ASA be added on the Cisco UC Manager platform?
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
An engineer configures new features within the Cisco Umbrella dashboard and wants to identify and proxy traffic that is categorized as risky domains and may contain safe and malicious content. Which action accomplishes these objectives?
What provides total management for mobile and PC including managing inventory and device tracking, remote view, and live troubleshooting using the included native remote desktop support?
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls?
Which two authentication protocols are supported by the Cisco WSA? (Choose two.)
Refer to the exhibit.
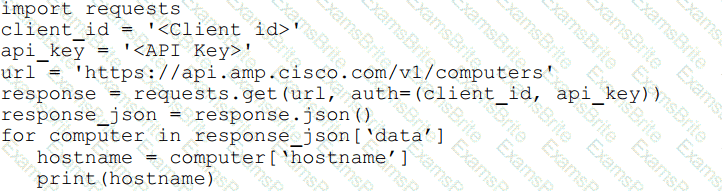
What will happen when the Python script is executed?
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement?
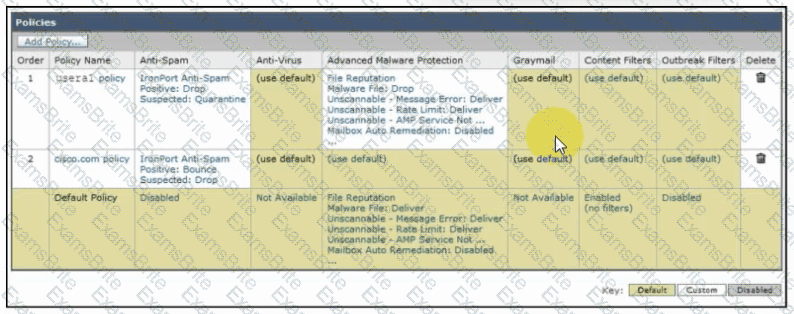
Refer to the exhibit. An engineer must configure an incoming mail policy so that each email sent from usera1@example.com to a domain of @cisco.com is scanned for antispam and advanced malware protection. All other settings will use the default behavior. What must be configured in the incoming mail policy to meet the requirements?
Which metric is used by the monitoring agent to collect and output packet loss and jitter information?
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two)
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
An engineer recently completed the system setup on a Cisco WSA Which URL information does the system send to SensorBase Network servers?
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a
connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal?
Which baseline form of telemetry is recommended for network infrastructure devices?
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data?
Refer to the exhibit.

What is the result of this Python script of the Cisco DNA Center API?
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code?
Refer to the exhibit.
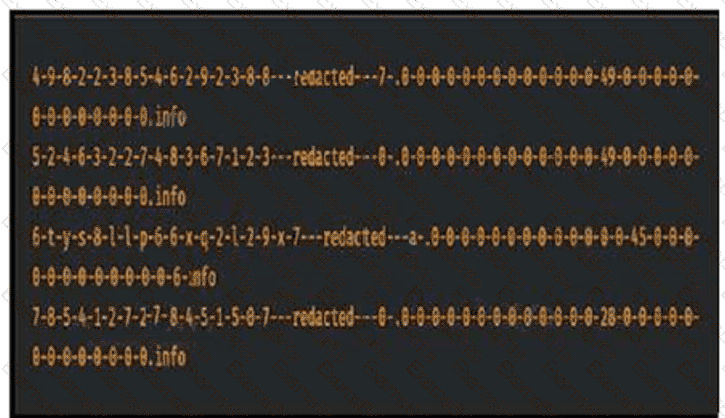
Consider that any feature of DNS requests, such as the length off the domain name
and the number of subdomains, can be used to construct models of expected behavior to which
observed values can be compared. Which type of malicious attack are these values associated with?
On Cisco Firepower Management Center, which policy is used to collect health modules alerts from managed
devices?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
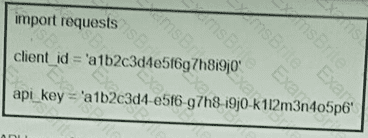
Refer to the exhibit. What function does the API key perform while working with https://api.amp.cisco.com/v1/computers?
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
Using Cisco Firepower’s Security Intelligence policies, upon which two criteria is Firepower block based?
(Choose two)
An administrator needs to configure the Cisco ASA via ASDM such that the network management system
can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration?
(Choose two.)
An organization wants to provide visibility and to identify active threats in its network using a VM. The
organization wants to extract metadata from network packet flow while ensuring that payloads are not retained
or transferred outside the network. Which solution meets these requirements?
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists?
A network administrator is modifying a remote access VPN on an FTD managed by an FMC. The administrator wants to offload traffic to certain trusted domains. The administrator wants this traffic to go out of the client's local internet and send other internet-bound traffic over the VPN Which feature must the administrator configure?
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
Which two Cisco Umbrella security categories are used to prevent command-and-control callbacks on port 53 and protect users from being tricked into providing confidential information? (Choose two.)
Which SNMPv3 configuration must be used to support the strongest security possible?
Email security has become a high priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10 00 to -6 00) on the Cisco ESA Which action will the system perform to disable any links in messages that match the filter?
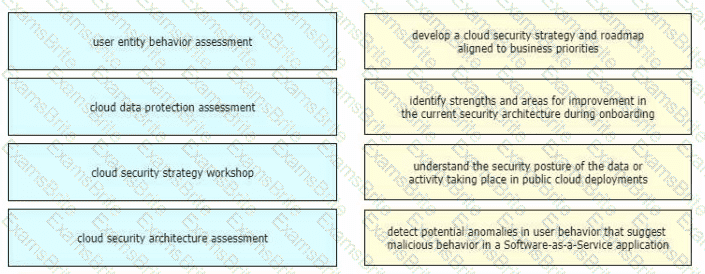
Drag and drop the cloud security assessment components from the left onto the definitions on the right.
An engineer is adding a Cisco router to an existing environment. NTP authentication is configured on all devices in the environment with the command ntp authentication-key 1 md5 Clsc427128380. There are two routers on the network that are configured as NTP servers for redundancy, 192.168.1.110 and 192.168.1.111. 192.168.1.110 is configured as the authoritative time source. What command must be configured on the new router to use 192.168.1.110 as its primary time source without the new router attempting to offer time to existing devices?
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized
solution. The organization does not have a local VM but does have existing Cisco ASAs that must migrate over
to Cisco FTDs. Which solution meets the needs of the organization?
How does the Cisco WSA enforce bandwidth restrictions for web applications?
An administrator has been tasked with configuring the Cisco Secure Email Gateway to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two.)
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization
needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of
172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
An engineer must implement a file transfer solution between a company's data center and branches. The company has numerous servers hosted in a hybrid cloud implementation. The file transfer protocol must support authentication, protect the data against unauthorized access, and ensure that users cannot list directories or remove files remotely. Which protocol must be used?
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
Which Cisco security solution protects remote users against phishing attacks when they are not connected to
the VPN?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
Which Cisco security solution integrates with cloud applications like Dropbox and Office 365 while protecting data from being exfiltrated?
Email security has become a high-priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10.00 to -6.00) on the Cisco Secure Email Gateway. Which action will the system perform to disable any links in messages that match the filter?
Why is it important for the organization to have an endpoint patching strategy?
Which technology must De used to Implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
A company discovered an attack propagating through their network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file. In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise. What must be done in order to ensure that the created is functioning as it should?
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
Refer to the exhibit.
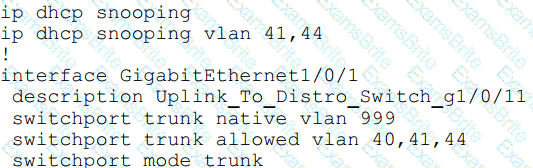
An organization is using DHCP Snooping within their network. A user on VLAN 41 on a new switch is
complaining that an IP address is not being obtained. Which command should be configured on the switch
interface in order to provide the user with network connectivity?
How does Cisco Workload Optimization portion of the network do EPP solutions solely performance issues?
Which risk is created when using an Internet browser to access cloud-based service?
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
Which two actions does the Cisco identity Services Engine posture module provide that ensures endpoint security?(Choose two.)
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this
requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
Refer to the exhibit.
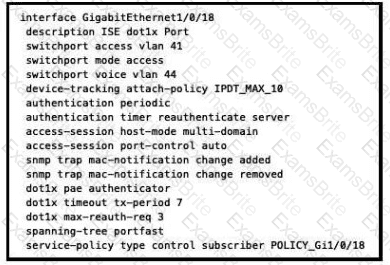
What will occur when this device tries to connect to the port?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
How many interfaces per bridge group does an ASA bridge group deployment support?
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch?
A Cisco FTD engineer is creating a new IKEv2 policy called s2s00123456789 for their organization to allow for additional protocols to terminate network devices with. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this?
Which attack is commonly associated with C and C++ programming languages?
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
Refer to the exhibit,
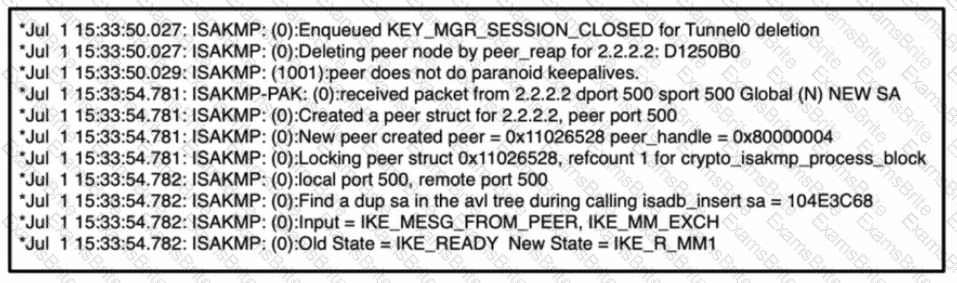
which command results in these messages when attempting to troubleshoot an iPsec VPN connection?
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from
Cisco and other vendors to share data and interoperate with each other?
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is
authenticated?
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP addressing in this command issued for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
Which solution stops unauthorized access to the system if a user's password is compromised?
An engineer is configuring Cisco WSA and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal?
A security engineer must create a policy based on the reputation verdict of a file from a Cisco Secure Email Gateway. The file with an undetermined verdict must be dropped. Which action must the security engineer take to meet the requirement?
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication?
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
Which Cisco ISE service checks the compliance of endpoints before allowing the endpoints to connect to
the network?
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains IPs, and flies, and helps to pinpoint attackers' infrastructures and predict future threat?
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
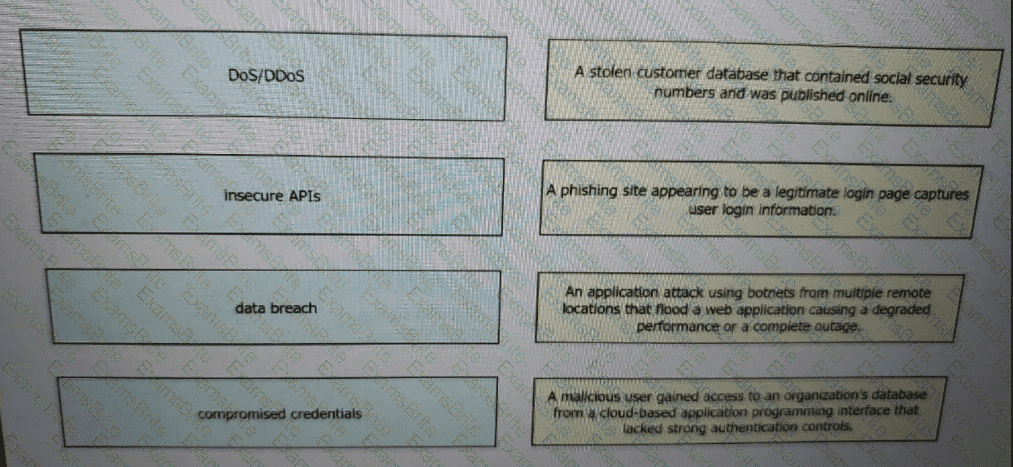
Drag and drop the threats from the left onto examples of that threat on the right
Based on the NIST 800-145 guide, which cloud architecture may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises?
A university policy must allow open access to resources on the Internet for research, but internal workstations are exposed to malware. Which Cisco AMP feature allows the engineering team to determine whether a file is installed on a selected few workstations?
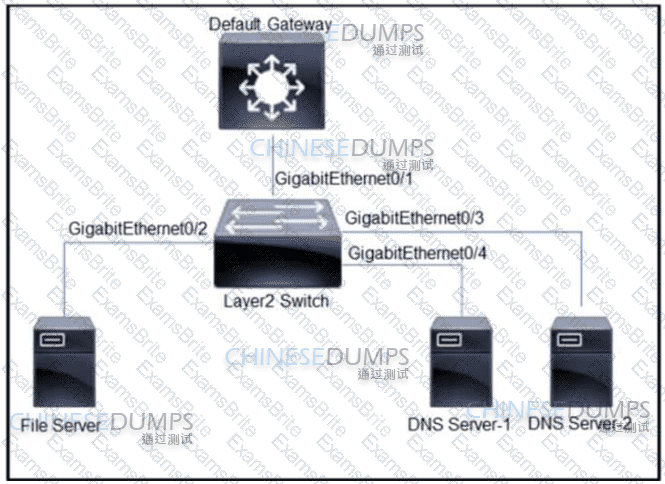
Refer to the exhibit. All servers are in the same VLAN/Subnet. DNS Server-1 and DNS Server-2 must communicate with each other, and all servers must communicate with default gateway multilayer switch. Which type of private VLAN ports should be configured to prevent communication between DNS servers and the file server?
An organization is selecting a cloud architecture and does not want to be responsible for patch management of the operating systems. Why should the organization select either Platform as a Service or Infrastructure as a Service for this environment?
An engineer must modify an existing remote access VPN using a Cisco AnyConnect Secure Mobility client solution and a Cisco Secure Firewall. Currently, all the traffic generate by the user Is sent to the VPN tunnel and the engineer must now exclude some servers and access them directly instead. Which element must be modified to achieve this goat?
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
Which deployment model is the most secure when considering risks to cloud adoption?