
Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
Last Update Feb 28, 2026
Total Questions : 547
We are offering FREE 350-501 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 350-501 free exam questions and then go for complete pool of Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) test questions that will help you more.



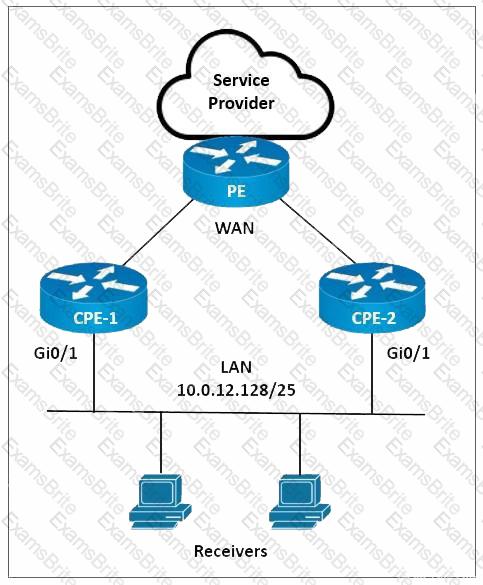
Refer to the exhibit. A network engineer is implementing multicast services on CPE-1 and CPE-2. CPE-1 must be configured as the preferred IGMP querier for the LAN segment. PIM-SM must be implemented on the LAN interfaces with an IGMP version that supports (*, G) joins only. Which configurations must the engineer implement on CPE-1 and CPE-2?
A router is advertising multiple networks to its BGP neighbor in AS 5200 with peer IP address 1.1.1.1. Which configuration must be applied so that the router permits updates only for networks with a prefix mask length less than or equal to 21?

Which feature will an operator use while implementing MPLS TE on customer's network, to prevent an LSP from using any overseas inks?
Refer the exhibit.

Users on a network connected to router R3 report slow speeds when they connect to the server connected to R2. After analyzing traffic on the network, a network engineer identified congestion on the link between R2 and R3 as the cause. Which QoS service must the engineer implement to drop traffic on the link when it exceeds a configured threshold?
router(config)# route-map blackhole-trigger
router(config-route-map)# match tag 777
router(config-route-map)# set ip next-hop 10.0.1.1
router(config-route-map)# set origin igp
router{config-route-map)# set community no-export
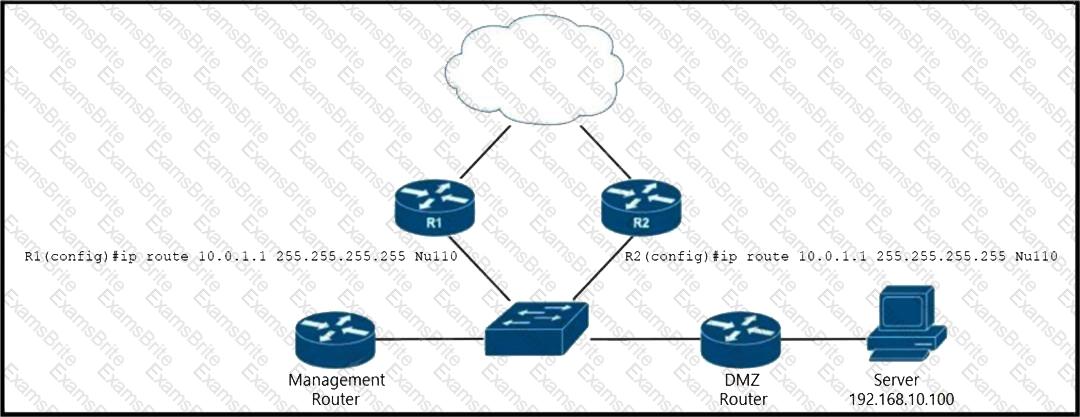
Refer to the exhibit. EIGRP is running across the core to exchange internal routes, and each router maintains iBGP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1, which is used as a black hole route as shown. Which configuration should the operator implement to the management router to create a route map that will redistribute tagged static routes into BGP and create a static route to blackhole traffic with tag 777 that is destined to the server at 192.168.10.100?
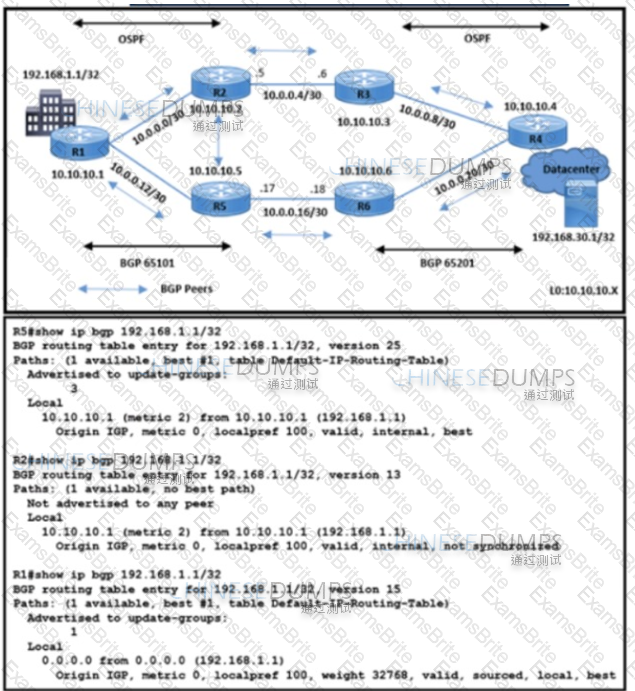
Refer to the exhibit. All BGP peering in AS 65101 and 65201 is enabled. The operations team is told that traffic destined to 192.168.1.1/32 from R4 does not use the path R3-R2-R1 as expected. An engineer debugs the issue and determines that 192.168.1.1/32 is advertised in the BGP routing table on R1. Which action resolves the issue?
Refer to the exhibit.
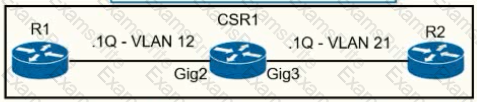
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
A)

B)

C)

D)

Why is the keyword none needed when implementing management plane security using TACACS?
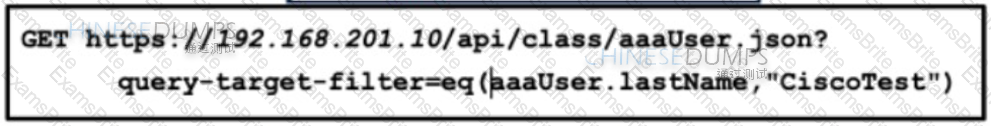
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
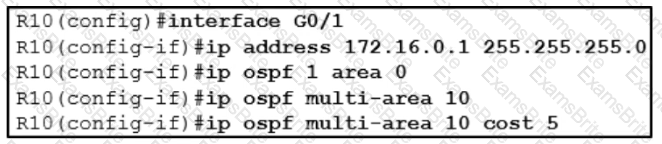
A network engineer is implementing OSPF multiarea. Which command on interface GO/1 resolves adjacency issues in the new area?

Refer to the exhibit. An engineer started to configure a router for OSPF. Which configuration must the engineer perform on the router without changing any interface configuration so that the router establishes an OSPF neighbor relationship with its peer?
Refer to the exhibit.
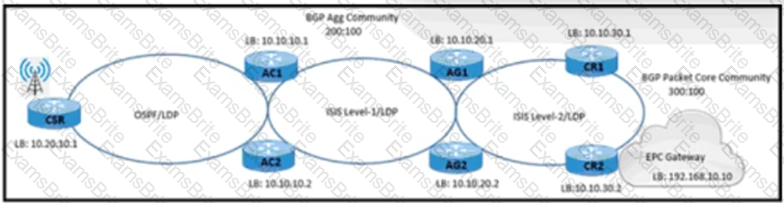
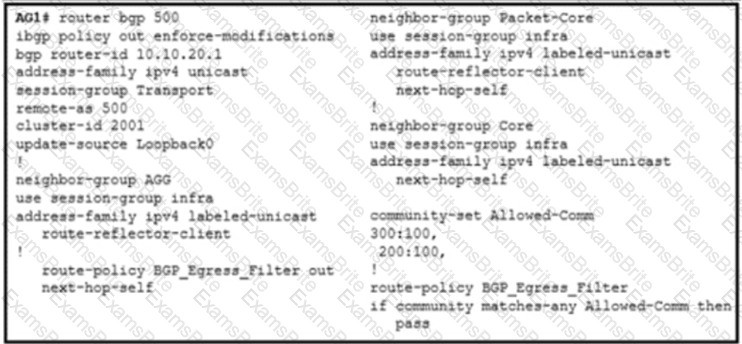
A NOC engineer is configuring label-based forwarding from CSR to the EPC gateway. Cell-site operation and maintenance for IPv4 traffic between 10.20.10.1 and 192.168.10.10 is already up. CR1 and CR2 are configured as route reflectors for AG1 and AG2. Which action completes the configuration?
After troubleshooting multiple outages on the network due to repeated configuration errors, the network architect asked an engineer to enable NETCONF to facilitate future configurations. The configuration must enable syslog messaging to record NETCONF notifications from each of the numerous devices on the network. Which configuration must the engineer apply?
Which action does the ingress VTEP perform on traffic between EVPN VXLAN overlays?
An engineer needs to implement QOS mechanism on customer's network as some applications going over the internet are slower than others are. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
Refer to the exhibit.
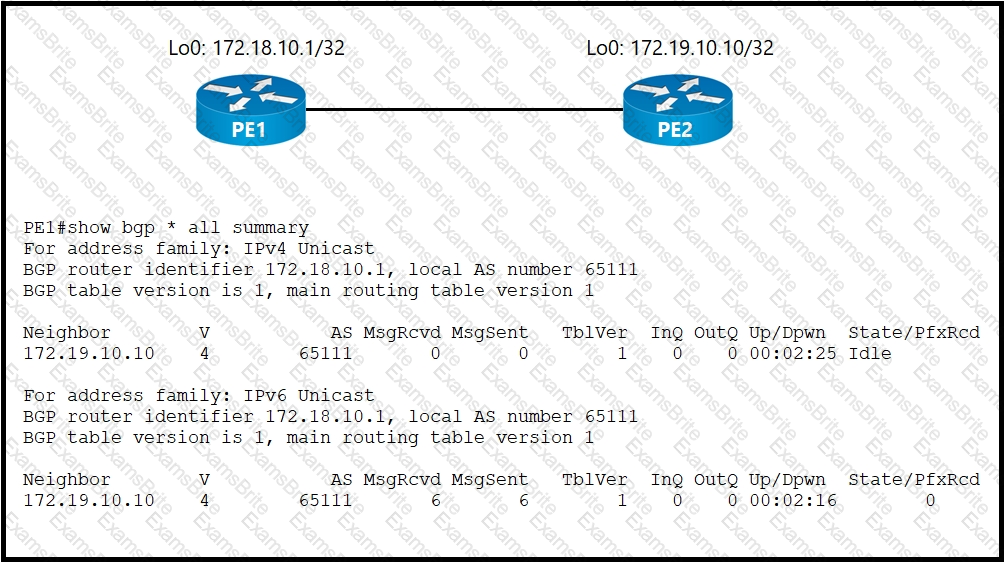
An administrator working for large ISP must connect its two POP sites to provide internet connectivity to its customers. Which configuration must the administrator perform to establish an iBGP session between routers PE1 on POP site 1 and PE2 on POP site 2?
Refer to the exhibit:
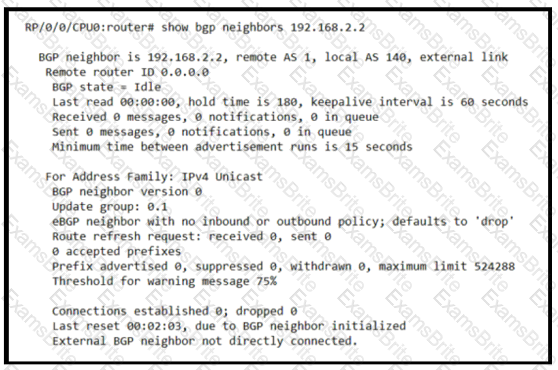
Based on the show/ command output, which result m true after BGP session is established?
Refer to the exhibit.
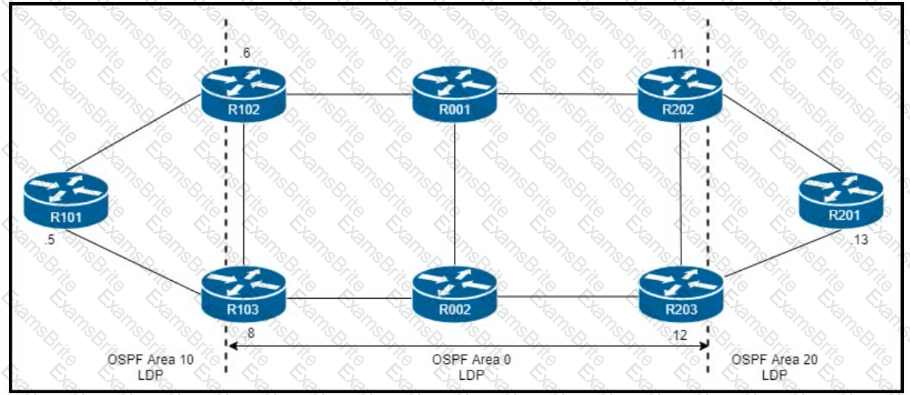
R101 is peering with R102 and R103, and R201 is peering with R202 and R203 using iBGP Labeled Unicast address families. The OSPF area 0 border routers are in a full iBGP Labeled Unicast mesh, and VPNv4 routes are exchanged directly between PE routers R101 and R201 through iBGP Which address family-level configuration must be applied on ABR R102 on ABR R102 to support a Unified MPLS routing architecture with partitioned IGP domains?
A)
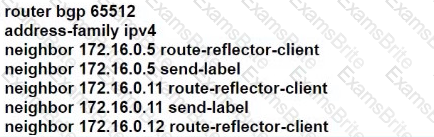
B)
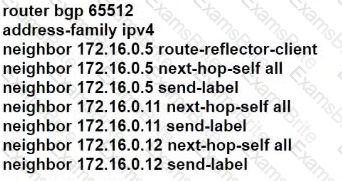
C)
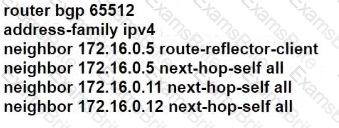
D)
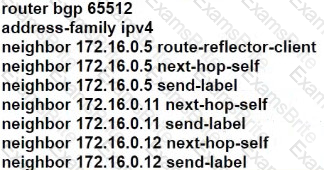
How does Inter-AS Option-A function when two PE routers in different autonomous systems are directly connected?
Refer to the exhibit.
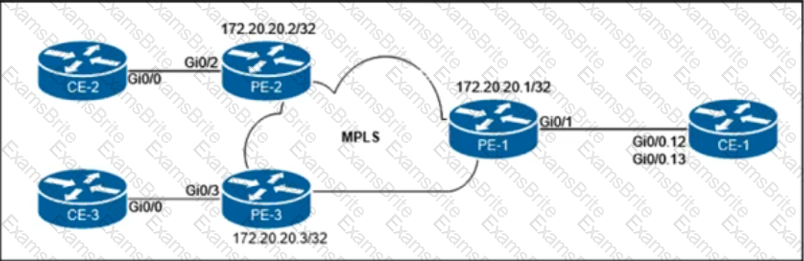
The customer that owns the CE-1, CE-2, and CE-3 routers purchased point-to-point E-Line services from the Carrier Ethernet provider. The service provider is delivering multiplexed UNI at the customer HQ location on PE-1 and untagged UNIs at the PE-2 and PE-3 locations. Additionally, the customer provided these VLAN to EVC mapping requirements:
• EVC 1 between CE-1 and CE-2 must be provisioned with C-VLAN 12 at the HQ location.
• EVC 2 between CE-1 and CE-3 must be provisioned with C-VLAN 13 at the HQ location.
Which configuration must the network engineer implement on the PE routers to provide end-to-end Carrier Ethernet service to the customer?
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
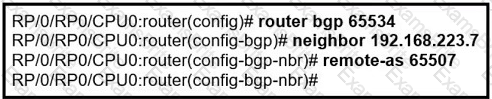
Which CLI mode must be used to configure the BGP keychain in Cisco IOS XR software?
Which technology enables the addition of new wavelengths in a fiber-optic network?
A network engineer is configuring a router to send multicast traffic for the 239.10.10.10 group. Which configuration must an .... forward the traffic?
Refer to the exhibit.
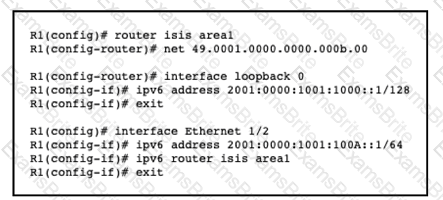
A network engineer with an employee id: 3812:12:993 has started to configure router R1 for IS-IS as shown. Which additional configuration must be applied to configure the IS-IS instance to advertise only network prefixes associated to passive interfaces?

Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
Refer to the exhibit.
An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
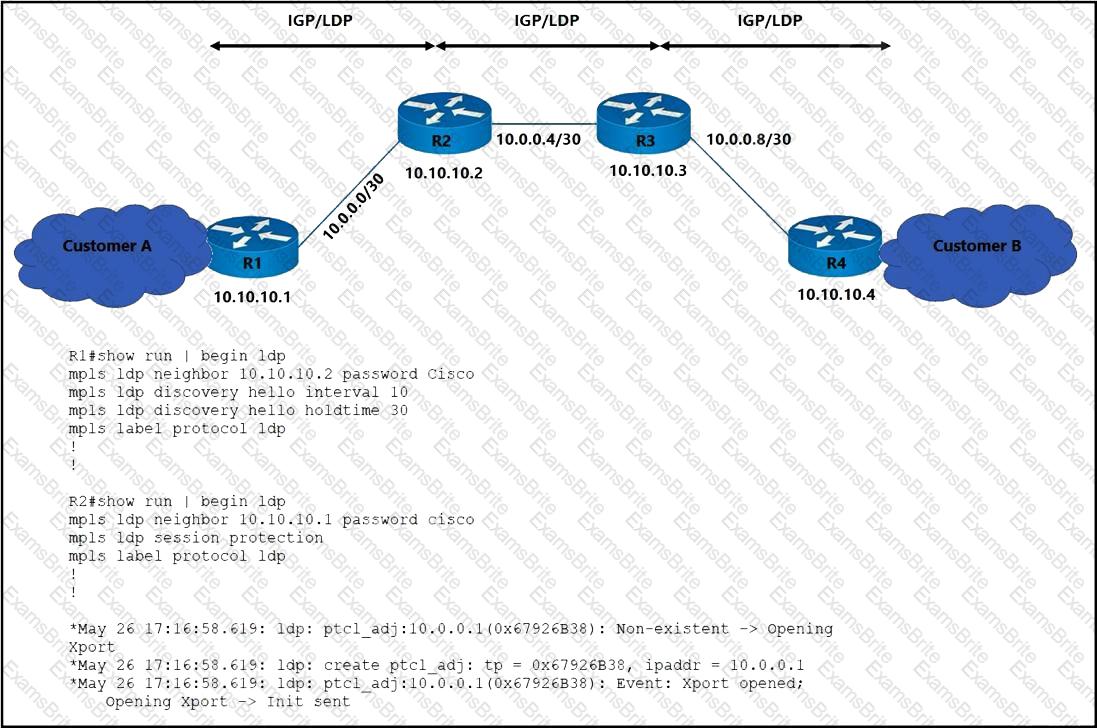
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service provider core network with these requirements:
R1 must establish LDP peering with the loopback IP address as its Router-ID.
Session protection must be enabled on R2.
How must the team update the network configuration to successfully enable LDP peering between R1 and R2?
According to RFC5305 on IS-IS extensions for traffic engineering, what is the 4-octet sub-TLV type 10 of extended IS-IS reachability TLV type 22?
Refer to the exhibit:
You are configuring an administrative domain implement so that devices can dynamically learn the RP?
Refer to the exhibit.
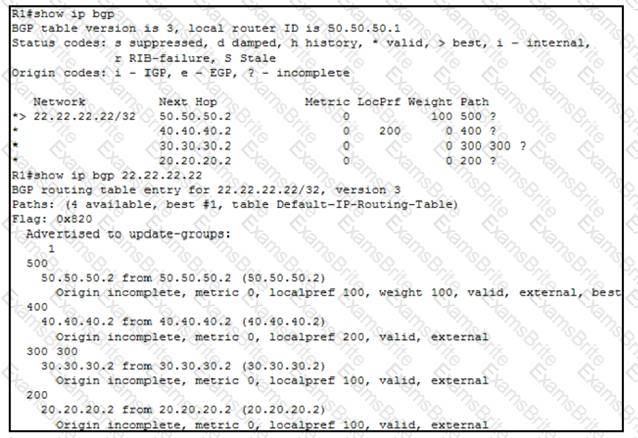
An engineer wants to determine which paths are best, second best, third best, and fourth best. Drag and drop the peer addresses on the left to the corresponding BGP best-path selection order on the right.
Refer to the exhibit.
If RC is a stub router, which entry must be injected so that it will send traffic outside the OSPF domain?
While implementing TTL security, an engineer issues the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command. After issuing this command, which BGP packets does the PE accept?
Refer to the exhibit:
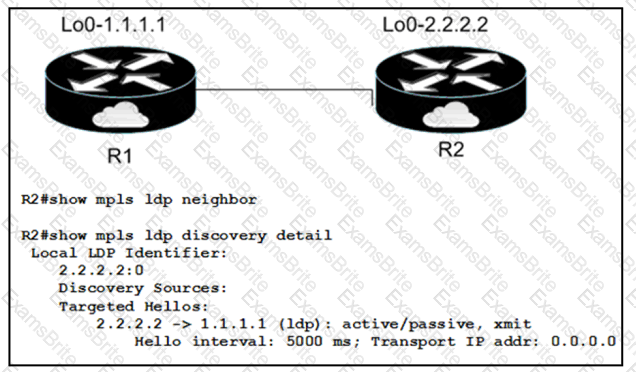
When implementing an LDP protocol, an engineer experienced an issue between two directly connected routers and noticed that no LDP neighbor exists for 1.1.1.1.
Which factor should be the reason for this situation?
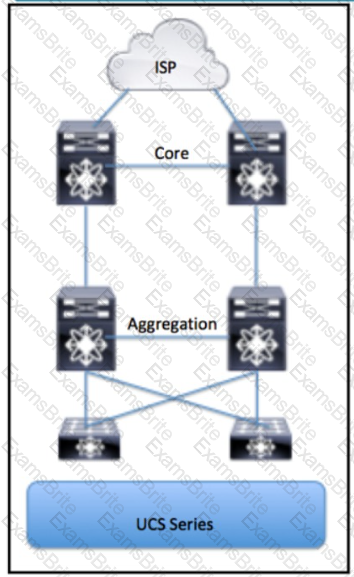
Refer to the exhibit. Which part of the diagram will host OpenStack components?
An engineer working for a private telecommunication company with an employe id:3948:613 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
A)

B)

C)

D)

Refer to the exhibit:

Export statistics received do not include the BGP next hop.
Which statement about the NetFlow export statistics is true?
Refer to the exhibit.
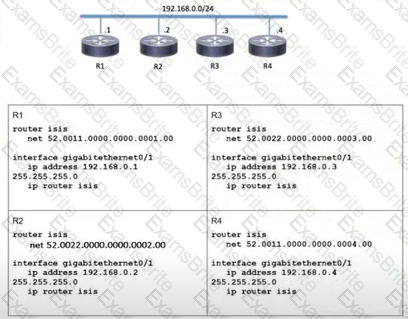
Which two topology changes happen to the IS-IS routers? (Choose two.)
Which core component of MDT describes the data that an MDT-capable device streams to a collector?
After a series of unexpected device failures on the network. a Cisco engineer is deploying NSF on the network devices so that packets continue to be forwarded during switchovers The network devices reside in the same holding, but they are physically separated into two different data centers Which task must the engineer perform as part of the deployment?
Refer to the exhibit:
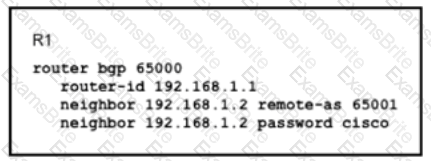
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
The NOC team must update the BGP forwarding configuration on the network with these requirements:
BGP peers must establish a neighborship with NSF capability and restart the session for the capability to be exchanged after 120 seconds.
BGP peers must delete routes after 360 seconds of inactivity.
Which action meets these requirements?

Refer to the exhibit. A network engineer must configure XR-PE1 for uninterruptible failover from active RP to the standby RP Neither peer devices CGW1 nor the network of ASN 64512 support restart extensions Which configuration must the engineer apply to XR PEI to complete tasks?
A)

B)

C)

D)

Refer to the exhibit.

A network engineer must implement SNMPv3 on a Cisco IOS XR router running BGP. The engineer configures SNMPv3 to use SHA for authentication and AES for privacy on the routers, which are in a different data center in the same exchange as other routers. The engineer must also verify the associated MIB view family name, storage type, and status. Which set of actions meets these requirements?
Refer to the exhibit:
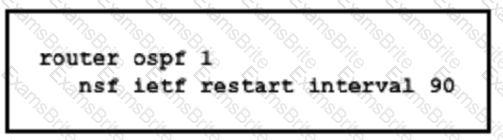
Which purpose of implementing NSF with this configuration is true?
Refer to the exhibit.
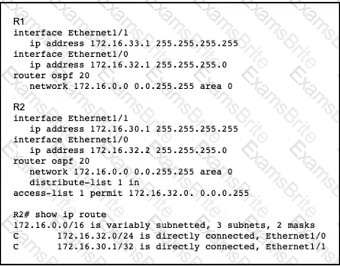
A network engineer notices that router R2 is failing to install network 172.16.33.1/32 in the routing table. Which configuration must the engineer apply to R2 to fix the problem?
Refer to the exhibit:

R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
Refer to the exhibit.
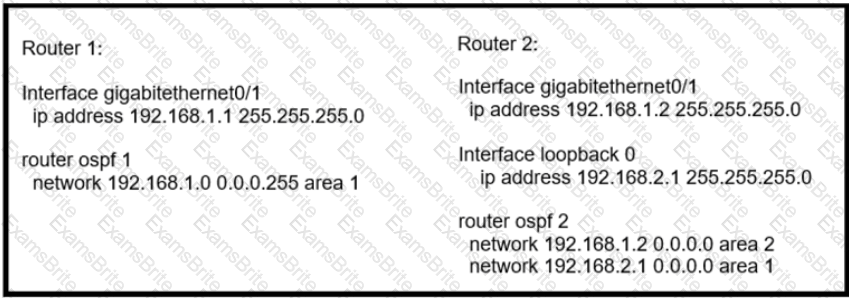
Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
What is an enhancement that Cisco IOS XE Software has over Cisco IOS Software?
Drag and drop the OSPF and IS-IS Cisco MPLS TE extensions from the left to their functional descriptions on the right.
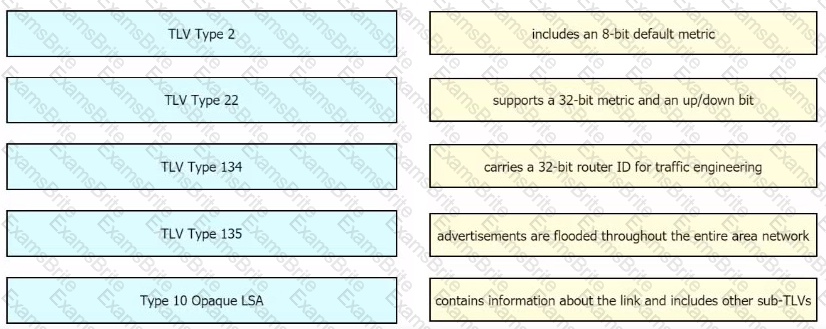
Refer to the exhibit: 
BGPsec is implemented on R1. R2. R3. and R4 BGP peering is established between neighboring autonomous systems Which statement about implementation is true?
Refer to the exhibit A network engineer is in the process of implementing IS-IS Area 1 and Area 2 on this network to segregate traffic between different segments of the network The hosts in the two new areas must maintain the ability to communicate with one another In both directions. Which additional change must be applied?
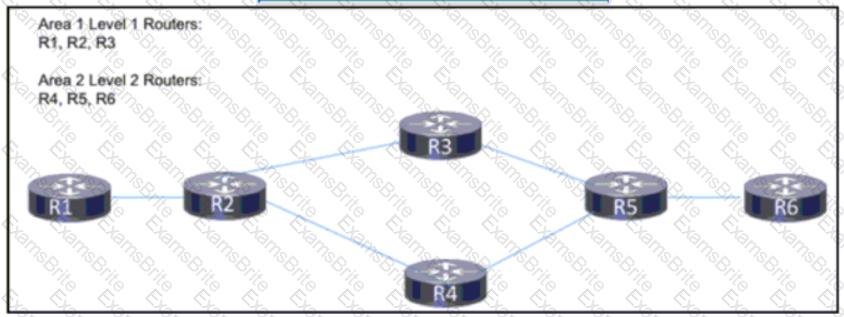
The engineering team at a large ISP has been alerted a customer network is experiencing high traffic congestion. After a discussion between the ISP and technical personnel at the customer site, the team agrees that traffic to the customer network that exceeds a specific threshold will be dropped. Which task must the engineer perform on the network to implement traffic policing changes?
A network operator needs to implement PIM-SSM multicast configuration on customer's network so that users in different domains are able to access and stream live traffic. Which two actions must the engineer perform on the network
to make the streaming work? (Choose two.)
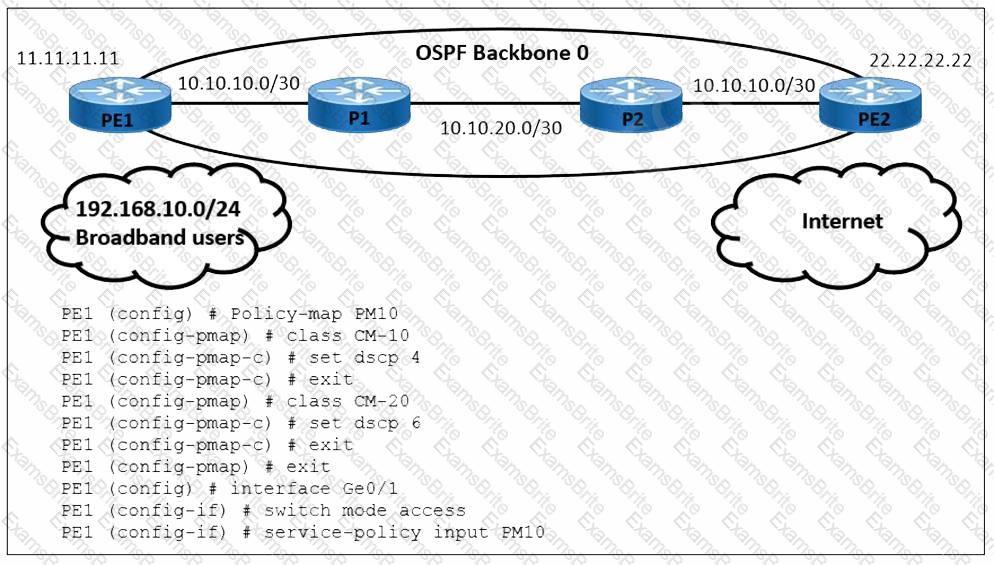
Refer to the exhibit A user is performing QoS marking on internet traffic and sending it with IPv4 and IPv6 headers on the provider edge device PE1. IPv4 traffic is classified with DSCP 4 and IPv6 traffic is classified with DSCP 6. Which action must the engineer take to begin implementing a QoS configuration on PE1 for the IPv6 traffic?
A network operator working for a private outsourcing company with an employee id: 4261:72:778 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
Which fact must a network engineer consider when planning to deploy RSVP-TE FRR?
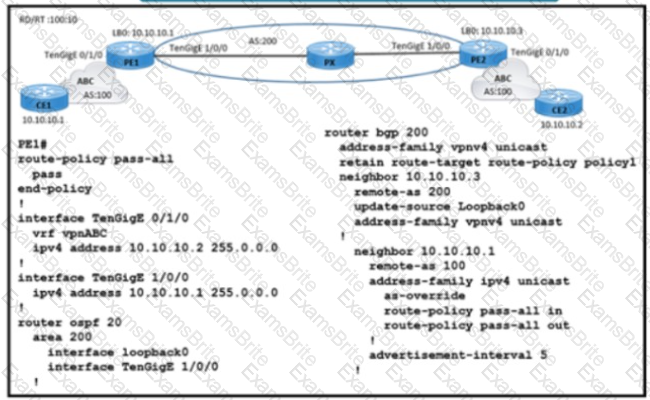
Refer to the exhibit. A service provider engineer Is configuring the connection between CE1 and CE2. AS 200 of the service provider and AS 100 of enterprise ABC should connect using BGP. The engineer already completed the configuration of VRF RT 100:10 of enterprise ABC. Which configuration must the engineer apply on PE1 to meet the requirement?
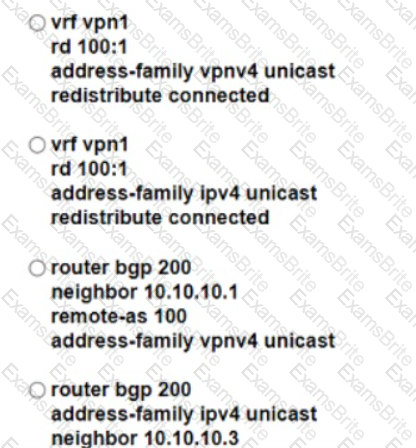
Refer to the exhibit.
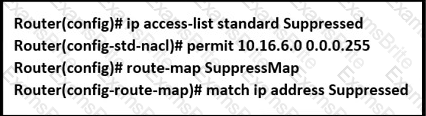
An engineer is implementing BGP selective prefix suppression. The router must advertise only 10.16.4.0/24,10.16.5.0/24. and summarized route 10.16.0.0/21. and suppress 10.16.6.0/24. Which configuration must the engineer apply to the router?
A)

B)

C)
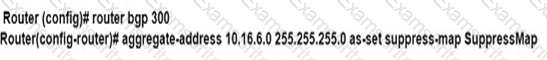
D)

Refer to the exhibit.
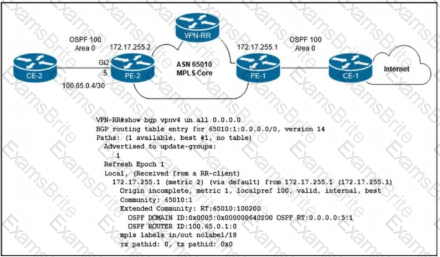
The network engineer who manages ASN 65010 is provisioning a customer VRF named CUSTOMER-ABC on PE-2. The PE-CE routing protocol is OSPF Internet reachability is available via the OSPF 0 0 0.0/0 route advertised by CE-1 to PE-1 In the customer VRF Which configuration must the network engineer Implement on PE-2 so that CE-2 has connectivity to the Internet?
A)

B)

C)

D)

How does an untrusted interface at the boundary of an administrative domain handle incoming packets?
A router is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization to a neighbor to establish an LDP session? (Choose three)
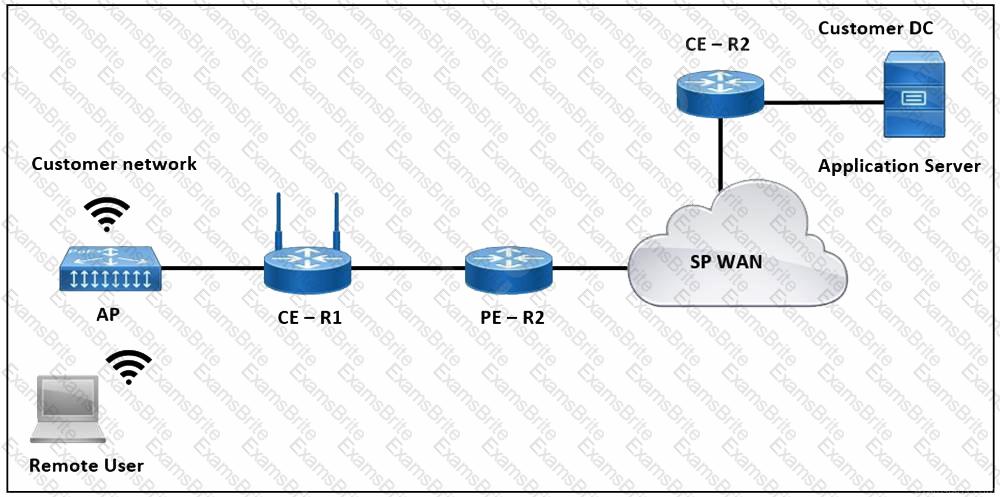
Refer to the exhibit. The application server in the data center hosts voice, video, and data applications over the internet. The data applications run more slowly than the voice and video applications. To ensure that all applications run smoothly, the service provider decided to implement a QoS policy on router PER 2 to apply traffic shaping. Which two actions must an engineer take to implement the task? (Choose two.)
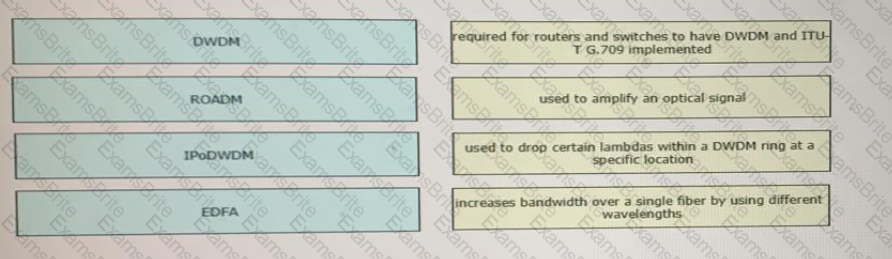
Drag and drop the technologies from the left onto the correct definitions on the right.
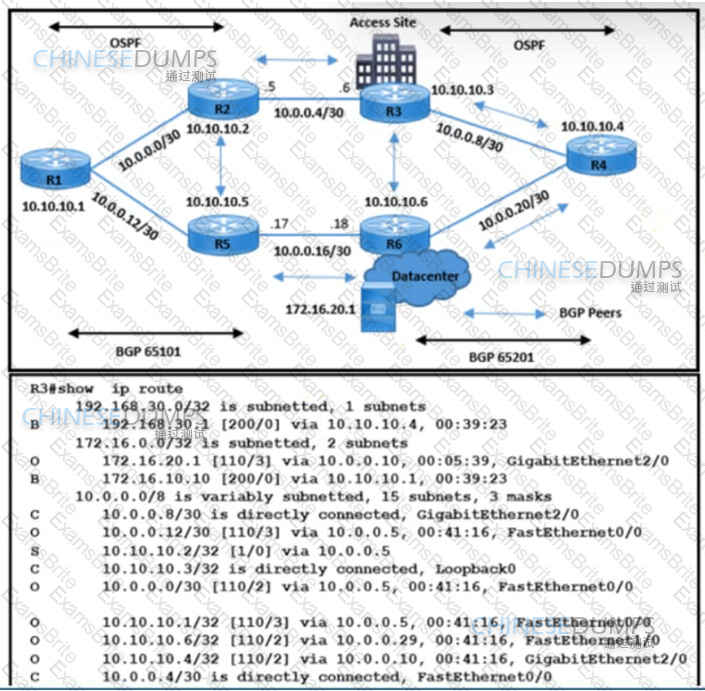
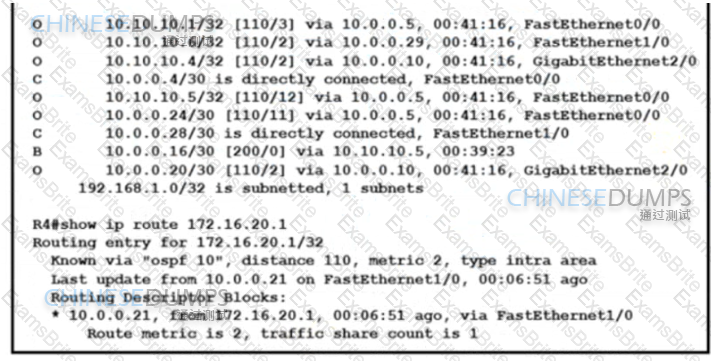
Refer to the exhibit. The network operations team reported that the access site that is connected to R3 is not connecting to the application server in the data center and that all packets that are sent from the application server to the access site are dropped. The team verified that OSPF and BGP peerings are up in BGP AS 65101 and BGP AS 65201. R4 is expected to receive traffic from the application server route via OSPF. Which action resolves this issue?
Refer to the exhibit:
Which configuration prevents the OSPF neighbor from establishing?
Guidelines -
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology:
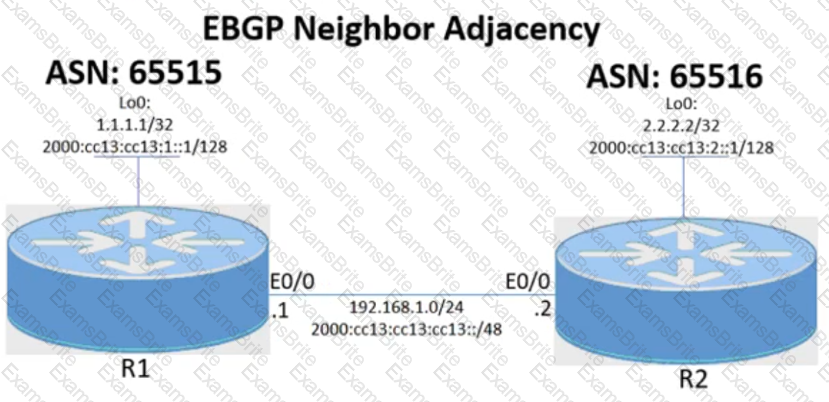
Tasks -
Configure the BGP routing protocol for R1 and R2 according to the topology to achieve these goals:
1. Configure EBGP neighbor adjacency for the IPv4 and IPv6 address family between R1 and R2 using Loopback0 IPv4 and IPv6 addresses. All BGP updates must come from the Loopback0 interface as the source. Do not use IGP routing protocols to complete this task.
2. Configure MD5 Authentication for the EBGP adjacency between R1 and R2. The password is clear text C1sc0!.
An engineer is trying to implement BGP in a multihomed architecture. What must the engineer configure to influence inbound path selection?
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
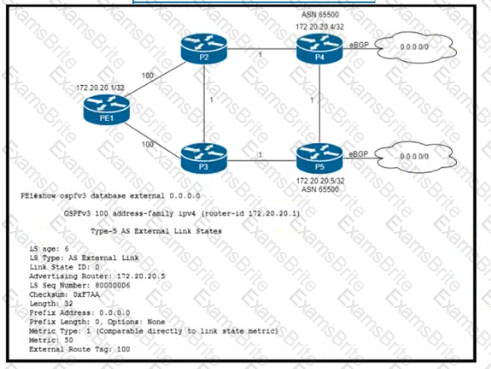
Refer to the exhibit. Router P4 and P5 receive the 0.0.0.0/0 route from the ISP via eBGP peering P4 is the primary Internet gateway router, and P5 is its Backup. P5 is already advertising a default route into OSPF domain. Which configuration must Be applied to P4 so that advertises a default route Into OSPF and Becomes me primary internet gateway for the network?

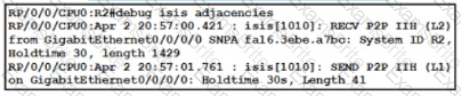
Refer to the exhibit. A network operator is attempting to configure an IS-IS adjacency between two routers, but the adjacency cannot be established. To troubleshoot the problem, the operator collects this debugging output. Which interface are misconfigured on these routers?

Exhibit:
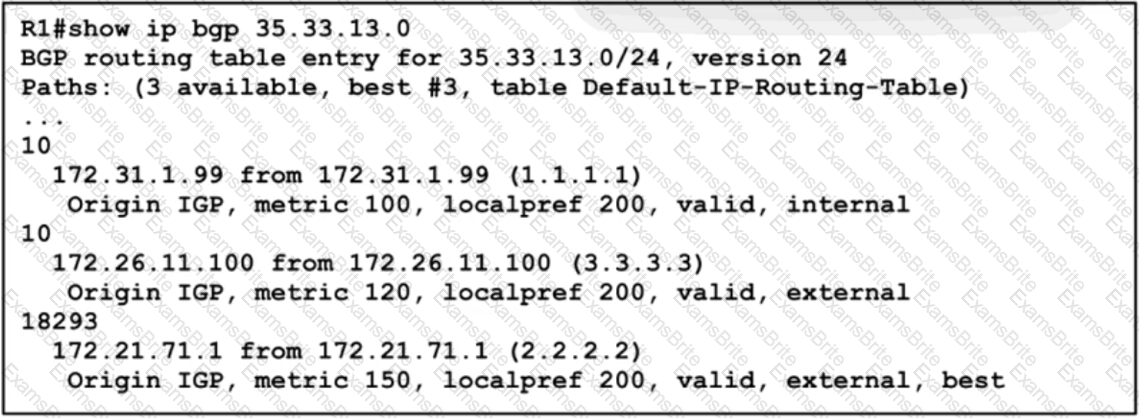
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?
While an engineer deploys a new Cisco device to redistribute routes from OSPF to BGP, they notice that not all OSPF routes are getting advertised into BGP. Which action must the engineer perform so that the device allows O, OIA, OE1, and OE2 OSPF routes into other protocols?
An engineer is implementing a router redistribution within BGP. The route map must be configured to permit all unmatched routes. Which action must the engineer perform to complete this task?

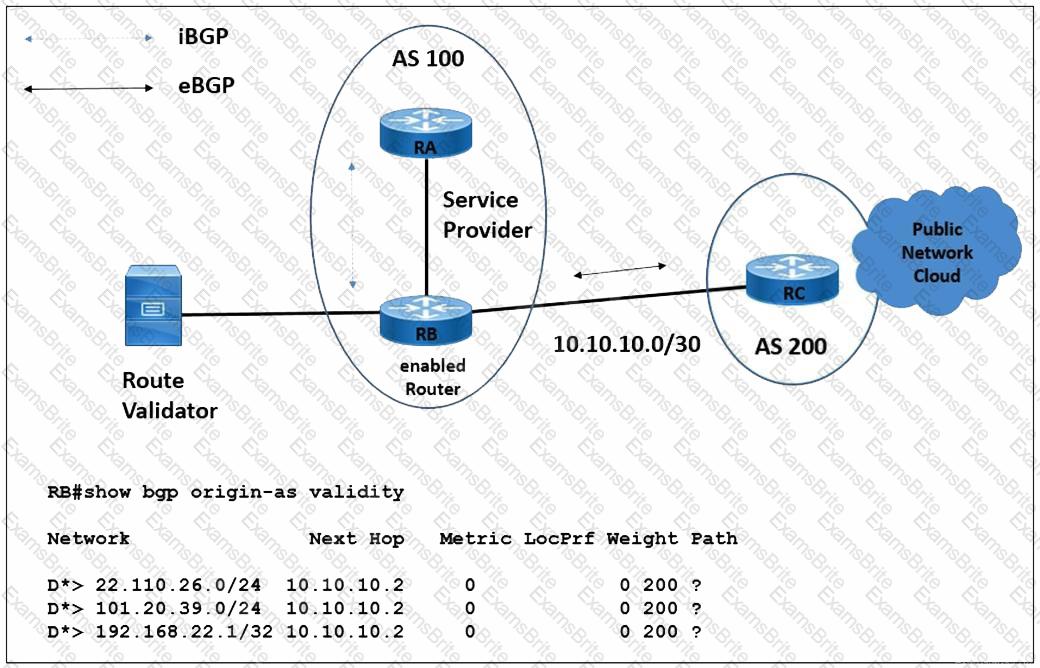
Refer to the exhibit. A network engineer is configuring router RB to secure BGP advertisements against route hijacking activity. RB must validate all prefixes that it receives from origin AS 200 before installing them in the BGP route table. Which configuration meets the requirement?
A network engineer is configuring RIP as the routing protocol between multiple PEs and CEs. The engineer must avoid advertising the same routes back to their sources. Which action should be performed on the routers to accomplish this task?
The administrator of a small company network notices that intermittent network issues occasionally cause inbound notifications to its SNMP servers to be lost. Which configuration must the administrator apply so that the SNMP servers acknowledge the notifications that they receive?
A network operator working for a telecommunication company with an employee Id: 4065 96080 it trying to implement BFD configuration on an existing network of Cisco devices Which task must the engineer perform to enable BFD on the interfaces?
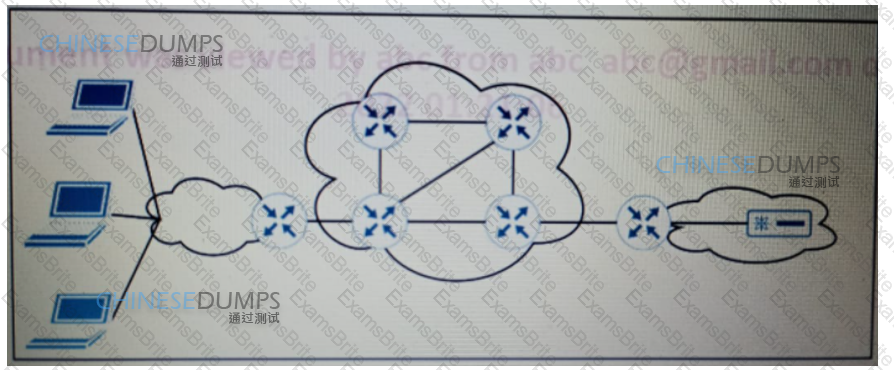
Refer to the exhibit. ISP A provides VPLS services and DDoS protection to Company XYZ to connect their branches across the North America and Europe regions. The uplink from the data center to the ISP is Mbps. The company XYZ security team asked the ISP to redirect ICMP requests which are currently going to the web server to a new local security appliance which configuration must an ISPP engineer apply to router R2 to redirect the ICMP traffic?
A)
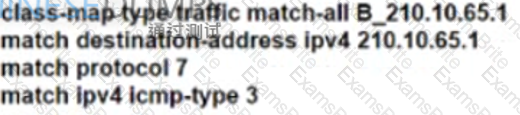
B)

C)
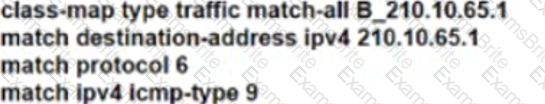
D)

An engineer implemented LDP protocol on the ISP network. The engineer must ensure that there are no packet loss issues when IGP and LDP protocols are not synchronized. Which configuring must the engineer implement so that the IGP routing protocol will wait until LDP convergence is completed?
Refer to the exhibit. After a networking team configured this MPLS topology, the supervisor wants to view MPLS labels to verify the path that packets take from router R1 to router R7 The team already Issued an ICMP ping to verify connectivity between the devices. Which task must the team perform to allow the supervisor to view the label switch path?
 l
l
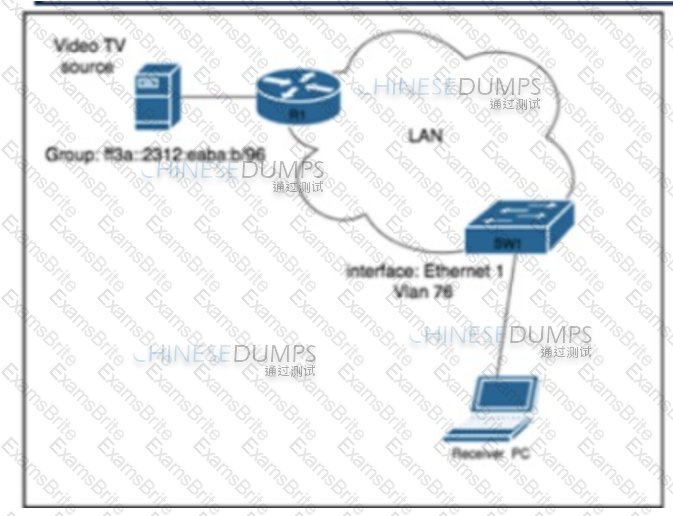
Refer to the exhibit. A network engineer working for a telecommunication company with an employee ID: 4602:62:646 is configuring security controls for the IPv6 multicast group, which is used for video TV. The solution from the engineer should reduce network usage and minimize the leave latency for the user that is connected to VLAN 76. Which two configurations meet this goal? (Choose two.)
A)
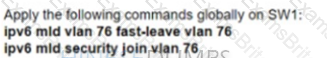
B)
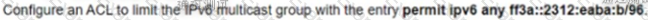
C)

D)

E)

Refer to the exhibit.
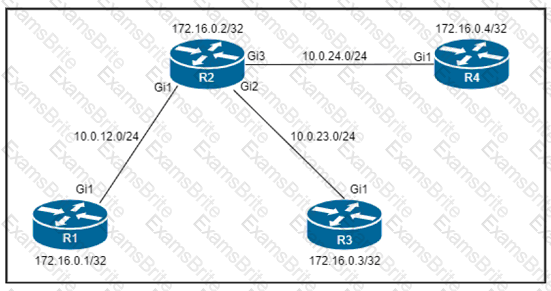
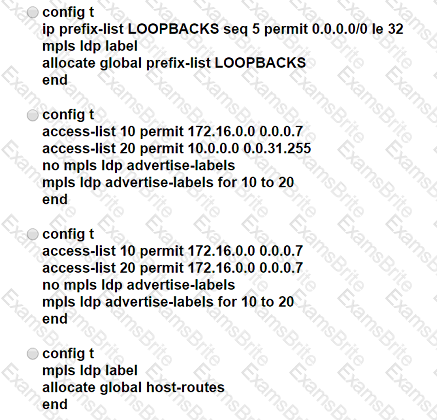
Which configuration must be applied to each of the four routers on the network to reduce LDP LIB size and advertise label bindings for the /32 loopback IP space only?
A network architect must implement CSC VPN services for a new backbone carrier. Which two benefits does the architecture provide? (Choose two.)
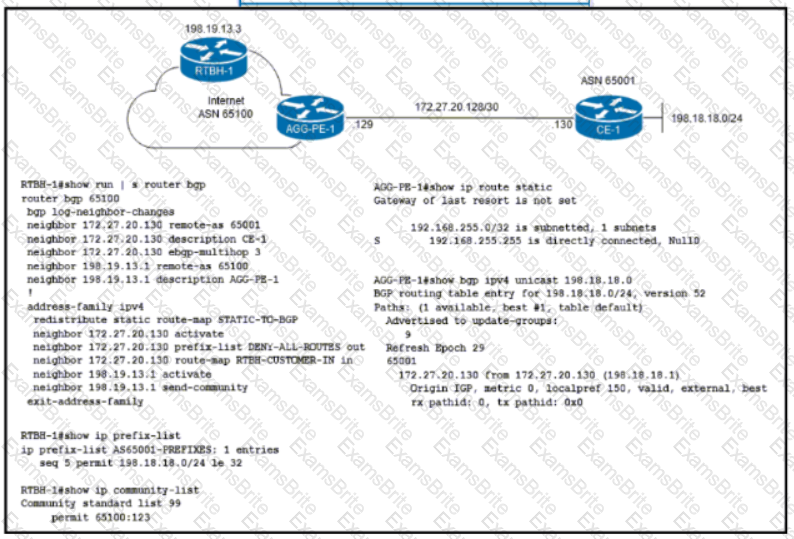
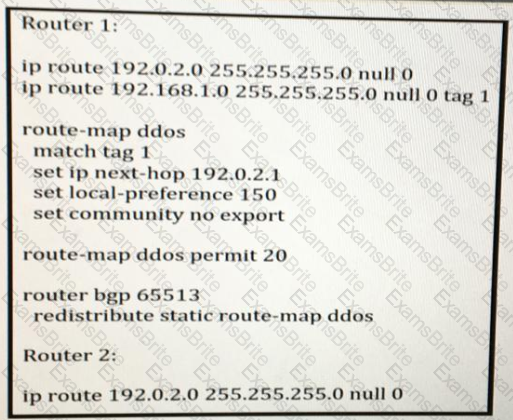
Refer to the exhibit. ISP ASN 65100 provides Internet services to router CE-1 and receives customer prefix 198.18.18.0/24 via eBGP. An administrator for the ISP is now provisioning RTBH services to provide on-demand data-plane security for the customer’s IP space. Which route-map configuration must the administrator apply to router RTBH-1 to complete the implementation of RTBH services to CE-1?
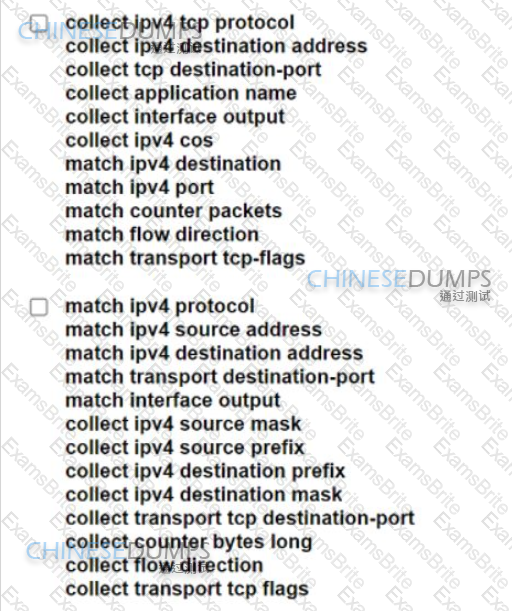
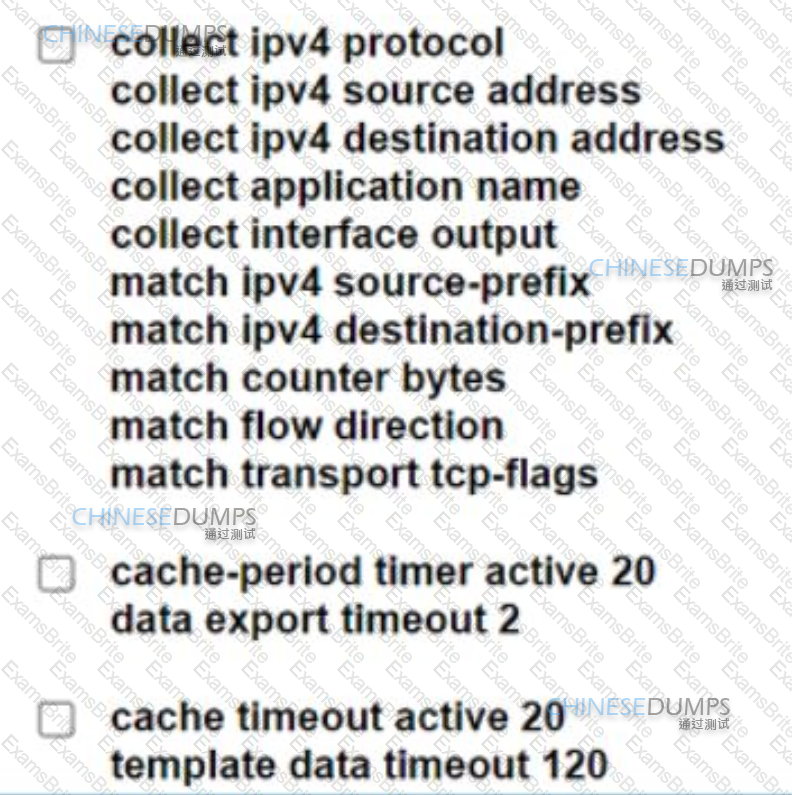
A network engineer must collect traffic statistics for an internal LAN toward the internet The sample must include the source and destination IP addresses, the destination ports, the total number of bytes from each flow using a 64-bit counter, and all transport flag information. Because of CPU limits, the flow collector processes samples that are a maximum of 20 seconds long. Which two configurations must the network engineer apply to the router? (Choose two.)
Refer to me exhibit.
Refer to the exhibit. A network engineer notices PE-21 convergence degradation due to the growing LSDB size of Level 2 areas in the network. The engineer decides to migrate router PE-21 from an inter-area design to an intra-area implementation. Inter-area routing must be accomplished via an ATT-bit set by the Level 1/Level 2 router. Which configuration must the engineer implement on PE-21 to complete the migration?
Which configuration mode do you use to apply the mpls Idp graceful-restart command in IOS XE Software? MPLS
In an MPLS network, which protocol can be used to distribute a Segment Prefix?
Refer to the exhibit.

AN engineer is configuring segment routing on an ISP to simplify traffic engineering and management across network domains. What should the engineer do to complete the implementation of segment routing?
Refer to the exhibit.
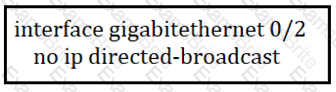
Which type of DDoS attack will be mitigated by this configuration?
Which two IS-IS parameters must match before two Level 2 peers can form an adjacency? (Choose two)
Refer to the exhibit:
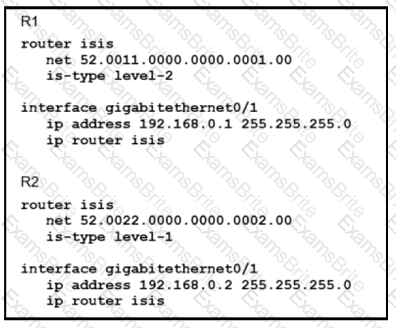
Which statement about the status of the neighbor relationship between R1 and R2 is true?
You are configuring MPLS traffic-engineering tunnels in the core.
Which two ways exist for the tunnel path across the core? (Choose two )
Refer to the exhibit.
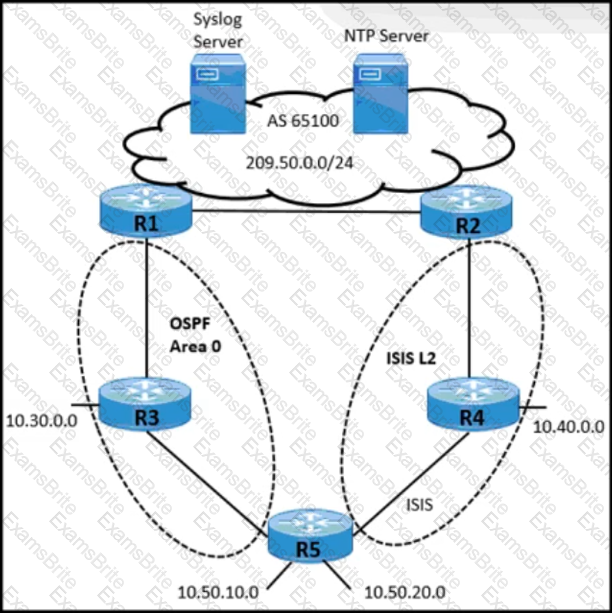
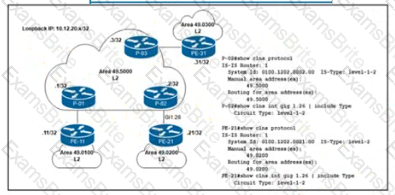
A network operator working for a telecommunication company with an employee ID: 4350:47:853 must implement an IGP solution based on these requirements:
• Subnet 10.50.10.0 traffic must exit through the R1 router to connect with the Syslog server.
• Subnet 10.50.20.0 traffic must exit through the R2 router to connect with the NTP server.
• In case of link failure between R2 and R4, traffic must be routed via R1 and R3.
Which two configurations must be implemented on R5 to meet these requirements? (Choose two.)
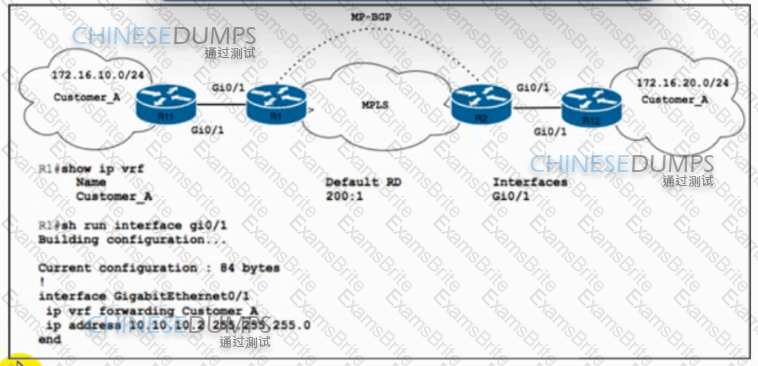
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A 172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?

Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology
Tasks
-
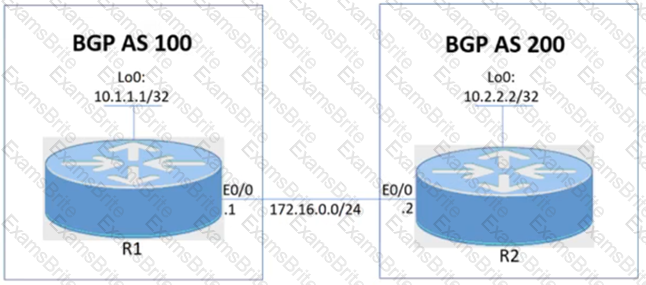
R1 and R2 are having issues forming an eBGP neighbor relationship. Troubleshoot and resolve the issue to achieve these goals:
1. Configure R1 and R2 to form a BGP neighborship using their Loopback interfaces.
2. Form the neighbor relationship using a BGP multihop mechanism. Use minimal values to solve the issue.
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices. Which configuration must the engineer apply on the network?
A)
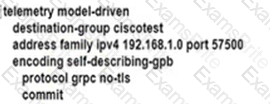
B)

C)
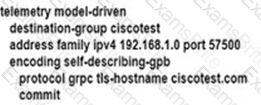
D)

Refer to the exhibit.
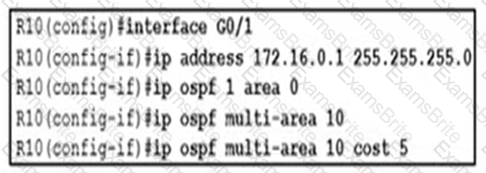
A network engineer Is implementing OSPF multiarea. Which command on interface G0/1 resolves adjacency Issues in the new area?
Refer to the exhibit:
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
How can shared services in an MPLS Layer 3 VPN provide Internet access to the customers of a central service provider?
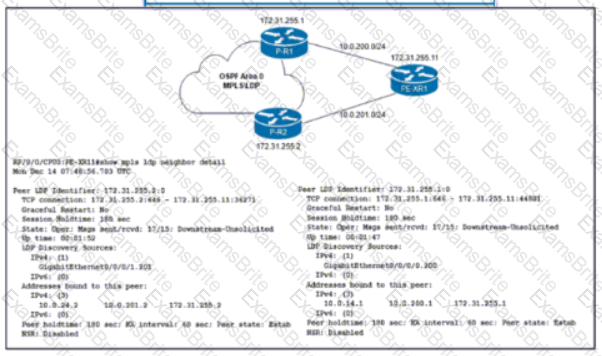
Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services For which reason do you make this decision?
A network engineer has configured TE tunnels in the MPLS provider core. Which two steps ensure traffic traverse? (Choose two.)
Refer to the exhibit:
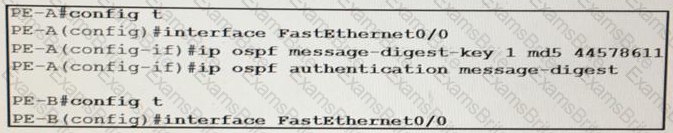
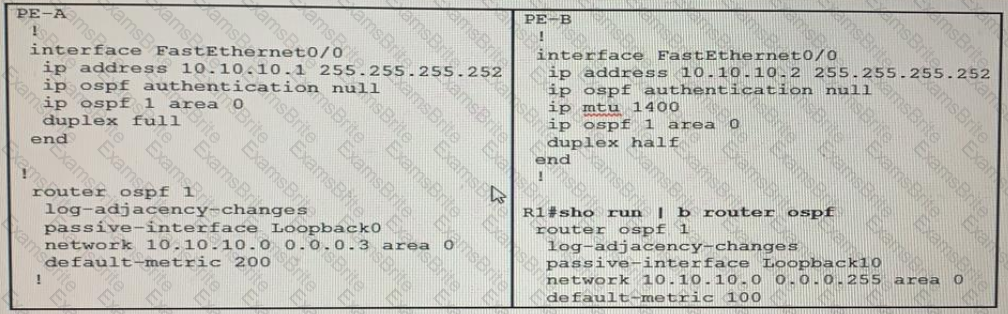
An engineer wants to authenticate the OSPF neighbor between PEA and PE-B using MD5.
Which command on PE-B successfully completes the configuration?
A)

B)

C)

D)

Refer to the exhibit:

A network engineer is implementing a BGP routing policy.
Which effect of this configuration is true?
What are two factors to consider when implementing NSR High Availability on an MPLS PE router? (Choose two.)
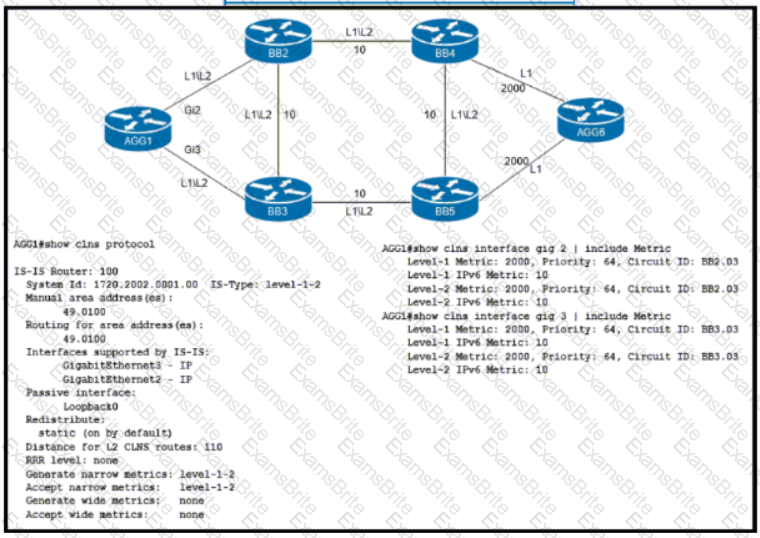
Refer to the exhibit. An engineer is configuring IS-IS on ISP network. Which IS-IS configuration must an engineer implement on router AGG1 so that it establishes connectivity to router AGG6 via the BB3 core router?
The service provider is serving hosts with two different multicast streams from source X and source Y. Source X is multicast group 224.0.0.0/8, and source Y is multicast group 226.0.0.0/8. Multicast source X should send its stream through bidirectional RP address 10.20.1.1, and multicast source Y should send its stream through RP address 10.20.2.1. Which configuration meets these requirements?