
Certified Ethical Hacker Exam (CEHv13)
Last Update Feb 28, 2026
Total Questions : 542
We are offering FREE 312-50v13 ECCouncil exam questions. All you do is to just go and sign up. Give your details, prepare 312-50v13 free exam questions and then go for complete pool of Certified Ethical Hacker Exam (CEHv13) test questions that will help you more.



You discover multiple NetBIOS responses during an nbtscan, but only one host returns a <1B> entry. What does this indicate?
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
Being a Certified Ethical Hacker (CEH), a company has brought you on board to evaluate the safety measures in place for their network system. The company uses a network time protocol server in the demilitarized zone.
During your enumeration, you decide to run a ntptrace command. Given the syntax: ntptrace [-n] [-m maxhosts] [servername/IP_address], which command usage would best serve your objective to find where the NTP server obtains the time from and to trace the list of NTP servers connected to the network?
You are performing a penetration test for a client and have gained shell access to a Windows machine on the internal network. You intend to retrieve all DNS records for the internal domain. If the DNS server is at 192.168.10.2 and the domain name is abccorp.local, what command would you type at the nslookup prompt to attempt a zone transfer?
This wireless security protocol allows 192-bit minimum-strength security protocols and cryptographic tools to protect sensitive data, such as GCMP-2S6. MMAC-SHA384, and ECDSA using a 384-bit elliptic curve. Which is this wireless security protocol?
A global media streaming platform experiences traffic surges every 10 minutes, with spikes over 300 Gbps followed by quiet intervals. Which DDoS attack explains this behavior?
What kind of detection technique is used in antivirus software that collects data from multiple protected systems and performs analysis in a cloud-based environment?
While testing a web application that relies on JavaScript-based client-side security controls, which method is most effective for bypassing these controls without triggering server-side alerts?
What is the main difference between ethical hacking and malicious hacking?
During a targeted phishing campaign, a malicious HTML attachment reconstructs malware locally using obfuscated JavaScript without making external network calls, bypassing firewalls and IDS inspection. Which evasion technique is being employed?
While browsing his Facebook feed, Matt sees a picture one of his friends posted with the caption, "Learn more about your friends!", along with a number of personal questions. Matt is suspicious and texts his friend, who confirms that he did indeed post it. With assurance that the post is legitimate, Matt responds to the questions in the post. A few days later, Matt's bank account has been accessed, and the password has been changed. What most likely happened?
One of your team members has asked you to analyze the following SOA record.
What is the TTL?
Rutgers.edu. SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A "Server-Side Includes" attack refers to the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary code remotely.
Which web-page file type, if it exists on the web server, is a strong indication that the server is vulnerable to this kind of attack?
Which of the following provides a security professional with most information about the system’s security posture?
A company’s Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?
Which type of security feature stops vehicles from crashing through the doors of a building?
You must map open ports and services while remaining stealthy and avoiding IDS detection. Which scanning technique is best?
A penetration tester targets a company's executive assistants by referencing upcoming board meetings in an email requesting access to confidential agendas. What is the most effective social engineering technique to obtain the necessary credentials without raising suspicion?
You are analyzing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command would you use?
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bob denies that he had ever sent a mail. What do you want to "know" to prove yourself that it was Bob who had sent the mail?
A known vulnerability exists on a production server, but patching is delayed due to operational constraints. What immediate action can reduce risk without disrupting operations?
An Internet Service Provider (ISP) has a need to authenticate users connecting via analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network.
Which AAA protocol is the most likely able to handle this requirement?
A future-focused security audit discusses risks where attackers collect encrypted data today, anticipating they will be able to decrypt it later using quantum computers. What is this threat commonly known as?
Within the context of Computer Security, which of the following statements describes Social Engineering best?
As a cybersecurity professional at XYZ Corporation, you are tasked with investigating anomalies in system logs that suggest potential unauthorized activity. System administrators have detected repeated failed login attempts on a critical server, followed by a sudden surge in outbound data traffic. These indicators suggest a possible compromise. Given the sensitive nature of the system and the sophistication of the threat, what should be your initial course of action?
Robin, an attacker, is attempting to bypass the firewalls of an organization through the DNS tunneling method in order to exfiltrate data. He is using the NSTX tool for bypassing the firewalls. On which of the following ports should Robin run the NSTX tool?
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
Which advanced session-hijacking technique is hardest to detect and mitigate?
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two. What would you call this attack?
The change of a hard drive failure is once every three years. The cost to buy a new hard drive is $300. It will require 10 hours to restore the OS and software to the new hard disk. It will require a further 4 hours to restore the database from the last backup to the new hard disk. The recovery person earns $10/hour. Calculate the SLE, ARO, and ALE. Assume the EF = 1(100%). What is the closest approximate cost of this replacement and recovery operation per year?
You are a Network Security Officer. You have two machines. The first machine (192.168.0.99) has Snort installed, and the second machine (192.168.0.150) has Kiwi Syslog installed. You perform a SYN scan in your network, and you notice that Kiwi Syslog is not receiving the alert message from Snort. You decide to run Wireshark on the Snort machine to check if the messages are going to the Kiwi Syslog machine. What Wireshark filter will show the connections from the Snort machine to Kiwi Syslog machine?
A multinational corporation recently survived a severe Distributed Denial-of-Service (DDoS) attack and has implemented enhanced security measures. During an audit, you discover that the organization uses both hardware- and cloud-based solutions to distribute incoming traffic in order to absorb and mitigate DDoS attacks while ensuring legitimate traffic remains available. What type of DDoS mitigation strategy is the company utilizing?
Harry. a professional hacker, targets the IT infrastructure of an organization. After preparing for the attack, he attempts to enter the target network using techniques such as sending spear-phishing emails and exploiting vulnerabilities on publicly available servers. Using these techniques, he successfully deployed malware on the target system to establish an outbound connection. What is the APT lifecycle phase that Harry is currently executing?
An organization uses SHA-256 for data integrity checks but still experiences unauthorized data modification. Which cryptographic tool can help resolve this issue?
A penetration tester discovers that a web application is vulnerable to Local File Inclusion (LFI) due to improper input validation in a URL parameter. Which approach should the tester take to exploit this vulnerability?
Louis, a professional hacker, had used specialized tools or search engines to encrypt all his browsing activity and navigate anonymously to obtain sensitive/hidden information about official government or federal databases. After gathering the information, he successfully performed an attack on the target government organization without being traced. Which of the following techniques is described in the above scenario?
In the context of password security, a simple dictionary attack involves loading a dictionary file into a cracking application such as L0phtCrack or John the Ripper. The brute force method is slow but exhaustive. If you use both brute force and dictionary methods combined to vary words, what would you call such an attack?
The security team of Debry Inc. decided to upgrade Wi-Fi security to thwart attacks such as dictionary attacks and key recovery attacks. For this purpose, the security team started implementing cutting-edge technology that uses a modern key establishment protocol called the simultaneous authentication of equals (SAE), also known as dragonfly key exchange, which replaces the PSK concept.
What is the Wi-Fi encryption technology implemented by Debry Inc.?
Which wireless security protocol replaces the personal pre-shared key (PSK) authentication with Simultaneous Authentication of Equals (SAE) and is therefore resistant to offline dictionary attacks?
A penetration tester evaluates a secure web application using HTTPS, secure cookies, and multi-factor authentication. To hijack a legitimate user’s session without triggering alerts, which technique should be used?
What is the most common method to exploit the “Bash Bug” or “Shellshock” vulnerability?
Your company performs penetration tests and security assessments for small and medium-sized businesses in the local area. During a routine security assessment, you discover information that suggests your client is involved with human trafficking.
What should you do?
A cyber attacker has initiated a series of activities against a high-profile organization following the Cyber Kill
Chain Methodology. The attacker is presently in the “Delivery” stage. As an Ethical Hacker, you are trying to
anticipate the adversary's next move. What is the most probable subsequent action from the attacker based on
the Cyber Kill Chain Methodology?
Security administrator John Smith has noticed abnormal amounts of traffic coming from local computers at night. Upon reviewing, he finds that user data have been exfilltrated by an attacker. AV tools are unable to find any malicious software, and the IDS/IPS has not reported on any non-whitelisted programs, what type of malware did the attacker use to bypass the company's application whitelisting?
A penetration tester is hired to legally assess the security of a company's network by identifying vulnerabilities and attempting to exploit them. What type of hacker is this?
A penetration tester is assessing a company’s vulnerability to advanced social engineering attacks targeting its legal department. Using detailed knowledge of mergers and legal proceedings, the tester crafts a highly credible pretext to deceive legal employees into sharing confidential case documents. What is the most effective technique?
Shiela is an information security analyst working at HiTech Security Solutions. She is performing service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
Your network infrastructure is under a SYN flood attack. The attacker has crafted an automated botnet to
simultaneously send 's' SYN packets per second to the server. You have put measures in place to manage ‘f
SYN packets per second, and the system is designed to deal with this number without any performance issues.
If 's' exceeds ‘f', the network infrastructure begins to show signs of overload. The system's response time
increases exponentially (24k), where 'k' represents each additional SYN packet above the ff limit. Now, considering 's=500' and different 'f values, in which scenario is the server most likely to experience overload and significantly increased response times?
Nedved is an IT Security Manager of a bank. One day, he found out there is a security breach involving a suspicious connection from the email server to an unknown IP. What is the first thing Nedved should do before contacting the incident response team?
As a part of an ethical hacking exercise, an attacker is probing a target network that is suspected to employ various honeypot systems for security. The attacker needs to detect and bypass these honeypots without alerting the target. The attacker decides to utilize a suite of techniques. Which of the following techniques would NOT assist in detecting a honeypot?
A penetration tester performs a vulnerability scan on a company’s web server and identifies several medium-risk vulnerabilities related to misconfigured settings. What should the tester do to verify the vulnerabilities?
You have been hired as an intern at a start-up company. Your first task is to help set up a basic web server for the company’s new website. The team leader has asked you to make sure the server is secure from common - threats. Based on your knowledge from studying for the CEH exam, which of the following actions should be
your priority to secure the web server?
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
A web server experienced a DDoS attack that specifically targeted the application layer. Which type of DDoS attack was most likely used?
A WPA2-PSK wireless network is tested. Which method would allow identification of a key vulnerability?
An organization decided to harden its security against web-application and web-server attacks. John, a security personnel in the organization, employed a security scanner to automate web-application security testing and to guard the organization's web infrastructure against web-application threats. Using that tool, he also wants to detect XSS, directory transversal problems, fault injection, SQL injection, attempts to execute commands, and several other attacks. Which of the following security scanners will help John perform the above task?
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, small sized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
which of the following Bluetooth hacking techniques refers to the theft of information from a wireless device through Bluetooth?
You are a cybersecurity consultant for a healthcare organization that utilizes Internet of Medical Things (loMT) devices, such as connected insulin pumps and heart rate monitors, to provide improved patientcare. Recently, the organization has been targeted by ransomware attacks. While the IT infrastructure was unaffected due to robust security measures, they are worried that the loMT devices could be potential entry points for future
attacks. What would be your main recommendation to protect these devices from such threats?
Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to perform port scanning on a target host in the network. While performing the given task, Sam sends FIN/ACK probes and determines that an RST packet is sent in response by the target host, indicating that the port is closed.
What is the port scanning technique used by Sam to discover open ports?
A penetration tester suspects that a web application's login form is vulnerable to SQL injection due to improper sanitization of user input. What is the most appropriate approach to test for SQL injection in the login form?
An ethical hacker is scanning a target network. They initiate a TCP connection by sending an SYN packet to a target machine and receiving a SYN/ACK packet in response. But instead of completing the three-way handshake with an ACK packet, they send an RST packet. What kind of scan is the ethical hacker likely performing and what is their goal?
During a black-box penetration test, an attacker runs the following command:
nmap -p25 --script smtp-enum-users --script-args EXPN,RCPT
The script successfully returns multiple valid usernames. Which server misconfiguration is being exploited?
Which of the following steps for risk assessment methodology refers to vulnerability identification?
SQL injection (SQLi) attacks attempt to inject SQL syntax into web requests, which may Bypass authentication and allow attackers to access and/or modify data attached to a web application.
Which of the following SQLI types leverages a database server's ability to make DNS requests to pass data to an attacker?
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
An ethical hacker is conducting a penetration test on a company’s network with full knowledge and permission from the organization. What is this type of hacking called?
A malicious user has acquired a Ticket Granting Service from the domain controller using a valid user's Ticket Granting Ticket in a Kerberoasting attack. He exhorted the TGS tickets from memory for offline cracking. But the attacker was stopped before he could complete his attack. The system administrator needs to investigate and remediate the potential breach. What should be the immediate step the system administrator takes?
Malware infecting multiple systems remains dormant until triggered and changes its code or encryption with each infection to evade detection. Which malware type best fits this description, and what is the most effective mitigation?
Morris, a professional hacker, performed a vulnerability scan on a target organization by sniffing the traffic on the network lo identify the active systems, network services, applications, and vulnerabilities. He also obtained the list of the users who are currently accessing the network. What is the type of vulnerability assessment that Morris performed on the target organization?
In the process of implementing a network vulnerability assessment strategy for a tech company, the security
analyst is confronted with the following scenarios:
1) A legacy application is discovered on the network, which no longer receives updates from the vendor.
2) Several systems in the network are found running outdated versions of web browsers prone to distributed
attacks.
3) The network firewall has been configured using default settings and passwords.
4) Certain TCP/IP protocols used in the organization are inherently insecure.
The security analyst decides to use vulnerability scanning software. Which of the following limitations of vulnerability assessment should the analyst be most cautious about in this context?
What would be the fastest way to perform content enumeration on a given web server by using the Gobuster tool?
An ethical hacker is testing a web application of a financial firm. During the test, a 'Contact Us' form's input field is found to lack proper user input validation, indicating a potential Cross-Site Scripting (XSS) vulnerability. However, the application has a stringent Content Security Policy (CSP) disallowing inline scripts and scripts from external domains but permitting scripts from its own domain. What would be the hacker's next step to confirm the XSS vulnerability?
Which action would most effectively increase the security of a virtual-hosted web server?
Attacker Lauren has gained the credentials of an organization's internal server system, and she was often logging in during irregular times to monitor the network activities. The organization was skeptical about the login times and appointed security professional Robert to determine the issue. Robert analyzed the compromised device to find incident details such as the type of attack, its severity, target, impact, method of propagation, and vulnerabilities exploited. What is the incident handling and response (IH&R) phase, in which Robert has determined these issues?
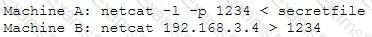
An attacker runs the netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
A penetration tester discovers that a web application uses unsanitized user input to dynamically generate file paths. The tester identifies that the application is vulnerable to Remote File Inclusion (RFI). Which action should the tester take to exploit this vulnerability?
Which social engineering attack involves impersonating a co-worker or authority figure to extract confidential information?
A penetration tester is evaluating a web application that does not properly validate the authenticity of HTTP requests. The tester suspects the application is vulnerable to Cross-Site Request Forgery (CSRF). Which approach should the tester use to exploit this vulnerability?
During a penetration testing assignment, a Certified Ethical Hacker (CEH) used a set of scanning tools to create a profile of the target organization. The CEH wanted to scan for live hosts, open ports, and services on a target network. He used Nmap for network inventory and Hping3 for network security auditing. However, he wanted to spoof IP addresses for anonymity during probing. Which command should the CEH use to perform this task?
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
In an intricate web application architecture using an Oracle database, you, as a security analyst, have identified a potential SQL Injection attack surface. The database consists of 'x' tables, each with y columns. Each table contains z1 records. An attacker, well-versed in SQLi techniques, crafts 'u' SQL payloads, each attempting to extract maximum data from the database. The payloads include UNION SELECT' statements and 'DBMS_XSLPPOCESSOR.READ2CLOB' to read sensitive files. The attacker aims to maximize the total data extracted E=xyz'u'. Assuming 'x=4\ y=2\ and varying z' and 'u\ which situation is likely to result in the highest extracted data volume?
A penetration tester is conducting an external assessment of a corporate web server. They start by accessing https://www.targetcorp.com/robots.txt and observe multiple Disallow entries that reference directories such as /admin-panel/, /backup/, and /confidentialdocs/. When the tester directly visits these paths via a browser, they find that access is not restricted by authentication and gain access to sensitive files, including server configuration and unprotected credentials. Which stage of the web server attack methodology is demonstrated in this scenario?
which of the following information security controls creates an appealing isolated environment for hackers to prevent them from compromising critical targets while simultaneously gathering information about the hacker?
What is the known plaintext attack used against DES which gives the result that encrypting plaintext with one DES key followed by encrypting it with a second DES key is no more secure than using a single key?
An ethical hacker is hired to evaluate the defenses of an organization's database system which is known to employ a signature-based IDS. The hacker knows that some SQL Injection evasion techniques may allow him
to bypass the system's signatures. During the operation, he successfully retrieved a list of usernames from the database without triggering an alarm by employing an advanced evasion technique. Which of the following
could he have used?
A penetration tester observes that traceroutes to various internal devices always show 10.10.10.1 as the second-to-last hop, regardless of the destination subnet. What does this pattern most likely indicate?
A penetration tester is tasked with mapping an organization's network while avoiding detection by sophisticated intrusion detection systems (IDS). The organization employs advanced IDS capable of recognizing common scanning patterns. Which scanning technique should the tester use to effectively discover live hosts and open ports without triggering the IDS?
Which type of attack attempts to overflow the content-addressable memory (CAM) table in an Ethernet switch?
Ron, a security professional, was pen testing web applications and SaaS platforms used by his company. While testing, he found a vulnerability that allows hackers to gain unauthorized access to API objects and perform actions such as view, update, and delete sensitive data of the company. What is the API vulnerability revealed in the above scenario?
James is working as an ethical hacker at Technix Solutions. The management ordered James to discover how vulnerable its network is towards footprinting attacks. James took the help of an open-source framework for performing automated reconnaissance activities. This framework helped James in gathering information using free tools and resources.
What is the framework used by James to conduct footprinting and reconnaissance activities?
John, a professional hacker, performs a network attack on a renowned organization and gains unauthorized access to the target network. He remains in the network without being detected for a long time and obtains sensitive information without sabotaging the organization. Which of the following attack techniques is used by John?
Which regulation defines security and privacy controls for Federal information systems and organizations?
A company’s online service is under a multi-vector DoS attack using SYN floods and HTTP GET floods. Firewalls and IDS cannot stop the outage. What advanced defense should the company implement?
Which access control mechanism allows for multiple systems to use a central authentication server (CAS) that permits users to authenticate once and gain access to multiple systems?
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities In the DNS server software and modified the original IP address of the target website to that of a fake website. What is the technique employed by Steve to gather information for identity theft?
in this form of encryption algorithm, every Individual block contains 64-bit data, and three keys are used, where each key consists of 56 bits. Which is this encryption algorithm?
You are a cybersecurity analyst at a global banking corporation and suspect a backdoor attack due to abnormal outbound traffic during non-working hours, unexplained reboots, and modified system files. Which combination of measures would be most effective to accurately identify and neutralize the backdoor while ensuring system integrity?
A government agency trains a group of cybersecurity experts to carry out covert cyber missions against foreign threats and gather intelligence without being detected. These experts work exclusively for national interests. What classification best describes them?
You are a security analyst conducting a footprinting exercise for a new client to gather information without direct interaction. After using search engines and public databases, you consider using Google Hacking (Google Dorking) techniques to uncover further vulnerabilities. Which option best justifies this decision?
A web server is overwhelmed by many slow, incomplete HTTP connections. What attack is occurring?
Which advanced session hijacking technique is the most difficult to detect and mitigate?
A penetration tester is assessing a web application that does not properly sanitize user input in the search field. The tester suspects the application is vulnerable to a SQL injection attack. Which approach should the tester take to confirm the vulnerability?
An attacker extracts the initial bytes from an encrypted file container and uses a tool to iterate through numeric combinations. What type of cryptanalytic technique is being utilized?
Sam is working as a system administrator In an organization. He captured the principal characteristics of a vulnerability and produced a numerical score to reflect Its severity using CVSS v3.0 to property assess and prioritize the organization's vulnerability management processes. The base score that Sam obtained after performing cvss rating was 4.0. What is the CVSS severity level of the vulnerability discovered by Sam in the above scenario?
Which of the following program infects the system boot sector and the executable files at the same time?
During an attempt to perform an SQL injection attack, a certified ethical hacker is focusing on the
identification of database engine type by generating an ODBC error. The ethical hacker, after injecting various payloads, finds that the web application returns a standard, generic error message that does not reveal any detailed database information. Which of the following techniques would the hacker consider next to obtain useful information about the underlying database?
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
env x='(){ :;};echo exploit' bash –c 'cat /etc/passwd'
What is the Shellshock bash vulnerability attempting to do on a vulnerable Linux host?
An attacker plans to compromise IoT devices to pivot into OT systems. What should be the immediate action?
A penetration tester is performing the footprinting process and is reviewing publicly available information about an organization by using the Google search engine.
Which of the following advanced operators would allow the pen tester to restrict the search to the organization’s web domain?
An experienced cyber attacker has created a fake Linkedin profile, successfully impersonating a high-ranking official from a well-established company, to execute a social engineering attack. The attacker then connected with other employees within the organization, receiving invitations to exclusive corporate events and gaining
access to proprietary project details shared within the network. What advanced social engineering technique has the attacker primarily used to exploit the system and what is the most likely immediate threat to the organization?
As part of a college project, you have set up a web server for hosting your team's application. Given your interest in cybersecurity, you have taken the lead in securing the server. You are aware that hackers often attempt to exploit server misconfigurations. Which of the following actions would best protect your web server from potential misconfiguration-based attacks?
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall?
Gregory, a professional penetration tester working at Sys Security Ltd., is tasked with performing a security test of web applications used in the company. For this purpose, Gregory uses a tool to test for any security loopholes by hijacking a session between a client and server. This tool has a feature of intercepting proxy that can be used to inspect and modify the traffic between the browser and target application. This tool can also perform customized attacks and can be used to test the randomness of session tokens. Which of the following tools is used by Gregory in the above scenario?
Josh has finished scanning a network and has discovered multiple vulnerable services. He knows that several of these usually have protections against external sources but are frequently susceptible to internal users. He decides to draft an email, spoof the sender as the internal IT team, and attach a malicious file disguised as a financial spreadsheet. Before Josh sends the email, he decides to investigate other methods of getting the file onto the system. For this particular attempt, what was the last stage of the cyber kill chain that Josh performed?
Every company needs a formal written document that outlines acceptable usage of systems, prohibited actions, and disciplinary consequences. Employees must sign this policy before using company systems.
What is this document called?
Consider the following Nmap output:
What command-line parameter could you use to determine the type and version number of the web server?
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert. You are starting an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to analyze?
During a security assessment, an attacker identifies a flaw in a multi-user file system. The system first verifies access rights to a temporary file created by a user. However, immediately after this verification, and before the file is processed, the attacker manages to swap the original file with a malicious version. This manipulation happens in the brief interval between the system's access verification and the moment it handles the file, resulting in the malicious file being treated as legitimate. Which vulnerability is the attacker exploiting?
A BLE attack captured LL_ENC_REQ and LL_ENC_RSP packets but not the LTK. What is the next step?
Gerard, a disgruntled ex-employee of Sunglass IT Solutions, targets this organization to perform sophisticated attacks and bring down its reputation in the market. To launch the attacks process, he performed DNS footprinting to gather information about ONS servers and to identify the hosts connected in the target network. He used an automated tool that can retrieve information about DNS zone data including DNS domain names, computer names. IP addresses. DNS records, and network Who is records. He further exploited this information to launch other sophisticated attacks. What is the tool employed by Gerard in the above scenario?
Geena, a cloud architect, uses a master component in the Kubernetes cluster architecture that scans newly generated pods and allocates a node to them. This component can also assign nodes based on factors such as the overall resource requirement, data locality, software/hardware/policy restrictions, and internal workload interventions.
Which of the following master components is explained in the above scenario?
Fleet vehicles with smart locking systems were compromised after attackers captured unique signals from key fobs. What should the security team prioritize to confirm and prevent this attack?
While using your bank’s online servicing you notice the following string in the URL bar:
"http://www.MyPersonalBank.com/account?id=368940911028389 &Damount=10980&Camount=21"
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
You discover an unpatched Android permission-handling vulnerability on a device with fully updated antivirus software. What is the most effective exploitation approach that avoids antivirus detection?
What piece of hardware on a computer's motherboard generates encryption keys and only releases a part of the key so that decrypting a disk on a new piece of hardware is not possible?
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
Ethical hacker jane Smith is attempting to perform an SQL injection attach. She wants to test the response time of a true or false response and wants to use a second command to determine whether the database will return true or false results for user IDs. which two SQL Injection types would give her the results she is looking for?
Attacker Rony Installed a rogue access point within an organization's perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
What hacking attack is challenge/response authentication used to prevent?
A penetration tester is tasked with gathering information about the subdomains of a target organization's website. The tester needs a versatile and efficient solution for the task. Which of the following options would be the most effective method to accomplish this goal?
An organization is performing a vulnerability assessment tor mitigating threats. James, a pen tester, scanned the organization by building an inventory of the protocols found on the organization's machines to detect which ports are attached to services such as an email server, a web server or a database server. After identifying the services, he selected the vulnerabilities on each machine and started executing only the relevant tests. What is the type of vulnerability assessment solution that James employed in the above scenario?
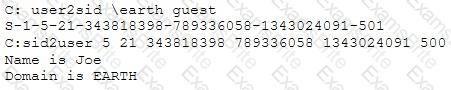
What did the following commands determine?
[Image Output of USER2SID and SID2USER showing that SID ending in -500 corresponds to user Joe on domain EARTH]
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
You perform a SYN (half-open) scan and receive a SYN/ACK packet in response. How should this result be interpreted?
Why should the security analyst disable/remove unnecessary ISAPI filters?
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
Which advanced session hijacking technique is hardest to detect and mitigate in a remote-access environment?
Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool to discover the OS of the target system. As a result, he obtained a TTL value, which Indicates that the target system is running a Windows OS. Identify the TTL value Henry obtained, which indicates that the target OS is Windows.
Don, a student, came across a gaming app in a third-party app store and Installed it. Subsequently, all the legitimate apps in his smartphone were replaced by deceptive applications that appeared legitimate. He also received many advertisements on his smartphone after Installing the app. What is the attack performed on Don in the above scenario?
You are the lead cybersecurity analyst at a multinational corporation that uses a hybrid encryption system to secure inter-departmental communications. The system uses RSA encryption for key exchange and AES for data encryption, taking advantage of the strengths of both asymmetric and symmetric encryption. Each RSA key pair has a size of 'n' bits, with larger keys providing more security at the cost of slower performance. The
time complexity of generating an RSA key pair is O(n*2), and AES encryption has a time complexity of O(n). An attacker has developed a quantum algorithm with time complexity O((log n)*2) to crack RSA encryption. Given *n=4000' and variable ‘AES key size’, which scenario is likely to provide the best balance of security and
performance? which scenario would provide the best balance of security and performance?
Mirai malware targets IoT devices. After infiltration, it uses them to propagate and create botnets that are then used to launch which types of attack?
Daniel Is a professional hacker who Is attempting to perform an SQL injection attack on a target website. www.movlescope.com. During this process, he encountered an IDS that detects SQL Injection attempts based on predefined signatures. To evade any comparison statement, he attempted placing characters such as ‘ 'or '1'='1" In any bask injection statement such as "or 1=1." Identify the evasion technique used by Daniel in the above scenario.
Which technique is most likely used to evade detection by an Intrusion Detection System (IDS)?
During a review for DoS threats, several IP addresses generate excessive traffic. Packet inspection shows the TCP three-way handshake is never completed, leaving many connections in a SYN_RECEIVED state and consuming server resources without completing sessions. What type of DoS attack is most likely occurring?
Peter, a system administrator working at a reputed IT firm, decided to work from his home and login remotely. Later, he anticipated that the remote connection could be exposed to session hijacking. To curb this possibility, he implemented a technique that creates a safe and encrypted tunnel over a public network to securely send and receive sensitive information and prevent hackers from decrypting the data flow between the endpoints.
What is the technique followed by Peter to send files securely through a remote connection?
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient’s consent, similar to email spamming?
When a security analyst prepares for the formal security assessment, what of the following should be done in order to determine inconsistencies in the secure assets database and verify that system is compliant to the minimum security baseline?
jane invites her friends Alice and John over for a LAN party. Alice and John access Jane's wireless network without a password. However. Jane has a long, complex password on her router. What attack has likely occurred?
An ethical hacker is testing the security of a website's database system against SQL Injection attacks. They discover that the IDS has a strong signature detection mechanism to detect typical SQL injection patterns.
Which evasion technique can be most effectively used to bypass the IDS signature detection while performing a SQL Injection attack?
Study the following log extract and identify the attack.
[Image shows an HTTP GET request with encoded traversal strings, such as
Richard, an attacker, aimed to hack loT devices connected to a target network. In this process. Richard recorded the frequency required to share information between connected devices. After obtaining the frequency, he captured the original data when commands were initiated by the connected devices. Once the original data were collected, he used free tools such as URH to segregate the command sequence. Subsequently, he started injecting the segregated command sequence on the same frequency into the loT network, which repeats the captured signals of the devices. What Is the type of attack performed by Richard In the above scenario?
During a security assessment, a consultant investigates how the application handles requests from authenticated users. They discover that once a user logs in, the application does not verify the origin of subsequent requests. To exploit this, the consultant creates a web page containing a malicious form that submits a funds transfer request to the application. A logged-in user, believing the page is part of a promotional campaign, fills out the form and submits it. The application processes the request successfully without any reauthentication or user confirmation, completing the transaction under the victim’s session. Which session hijacking technique is being used in this scenario?
The Heartbleed bug was discovered in 2014 and is widely referred to under MITRE’s Common Vulnerabilities and Exposures (CVE) as CVE-2014-0160. This bug affects the OpenSSL implementation of the Transport Layer Security (TLS) protocols defined in RFC6520.
What type of key does this bug leave exposed to the Internet making exploitation of any compromised system very easy?
Allen, a professional pen tester, was hired by xpertTech solutWns to perform an attack simul-ation on the organization's network resources. To perform the attack, he took advantage of the NetBIOS API and targeted the NetBIOS service. B/enumerating NetBIOS, he found that port 139 was open and could see the resources that could be accessed or viewed on a remote system. He came across many NetBIOS codes during enumeration.
identify the NetBIOS code used for obtaining the messenger service running for the logged-in user?
During LDAP-based enumeration, you observe that some critical information cannot be retrieved. What is the most likely reason?
As an IT security analyst, you perform network scanning using ICMP Echo Requests. During the scan, several IP addresses do not return Echo Replies, yet other network services remain operational. How should this situation be interpreted?
Given the complexities of an organization’s network infrastructure, a threat actor has exploited an unidentified vulnerability, leading to a major data breach. As a Certified Ethical Hacker (CEH), you are tasked with enhancing
the organization's security stance. To ensure a comprehensive security defense, you recommend a certain security strategy. Which of the following best represents the strategy you would likely suggest and why?
You are a cybersecurlty consultant for a smart city project. The project involves deploying a vast network of loT devices for public utilities like traffic control, water supply, and power grid management The city administration is concerned about the possibility of a Distributed Denial of Service (DDoS) attack crippling these critical services. They have asked you for advice on how to prevent such an attack. What would be your primary recommendation?
Which of the following statements about a zone transfer is correct? (Choose three.)
A penetration tester evaluates an industrial control system (ICS) that manages critical infrastructure. The tester discovers that the system uses weak default passwords for remote access. What is the most effective method to exploit this vulnerability?
John is investigating web-application firewall logs and observers that someone is attempting to inject the following:
char buff[10];
buff[>o] - 'a':
What type of attack is this?
While evaluating a smart card implementation, a security analyst observes that an attacker is measuring fluctuations in power consumption and timing variations during encryption operations on the chip. The attacker uses this information to infer secret keys used within the device. What type of exploitation is being carried out?
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A user on your Windows 2000 network has discovered that he can use L0phtCrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems.
However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
A penetration tester is running a vulnerability scan on a company’s network. The scan identifies an open port with a high-severity vulnerability linked to outdated software. What is the most appropriate next step for the tester?
What is the most plausible attack vector an APT group would use to compromise an IoT-based environmental control system?
When configuring wireless on his home router, Javik disables SSID broadcast. He leaves authentication “open” but sets the SSID to a 32-character string of random letters and numbers.
What is an accurate assessment of this scenario from a security perspective?
A technician is resolving an issue where a computer is unable to connect to the Internet using a wireless access point. The computer is able to transfer files locally to other machines, but cannot successfully reach the Internet. When the technician examines the IP address and default gateway they are both on the 192.168.1.0/24. Which of the following has occurred?
Repeated failed login attempts are followed by a sudden surge in outbound data traffic from a critical server. What should be your initial course of action?
During a reconnaissance mission, an ethical hacker uses Maltego, a popular footprinting tool, to collect information about a target organization. The information includes the target's Internet infrastructure details (domains, DNS names, Netblocks, IP address information). The hacker decides to use social engineering
techniques to gain further information. Which of the following would be the least likely method of social engineering to yield beneficial information based on the data collected?
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML code to embed a malicious applet in all HTTP connections. When users accessed any page, the applet ran and exploited many machines. Which one of the following tools the hacker probably used to inject HTML code?
John is an incident handler at a financial institution. His steps in a recent incident are not up to the standards of the company. John frequently forgets some steps and procedures while handling responses as they are very stressful to perform. Which of the following actions should John take to overcome this problem with the least administrative effort?
Mary, a penetration tester, has found password hashes in a client system she managed to breach. She needs to use these passwords to continue with the test, but she does not have time to find the passwords that correspond to these hashes. Which type of attack can she implement in order to continue?
Jacob works as a system administrator in an organization. He wants to extract the source code of a mobile application and disassemble the application to analyze its design flaws. Using this technique, he wants to fix any bugs in the application, discover underlying vulnerabilities, and improve defense strategies against attacks.
What is the technique used by Jacob in the above scenario to improve the security of the mobile application?
During a cloud security assessment, it was discovered that a former employee still had access to critical resources months after leaving the organization. Which practice would have most effectively prevented this issue?
An attacker exploits medical imaging protocols to intercept patient data. Which sniffing technique is most challenging?
A penetration tester is attempting to gain access to a wireless network that is secured with WPA2 encryption. The tester successfully captures the WPA2 handshake but now needs to crack the pre-shared key. What is the most effective method to proceed?
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking the hashed passwords?
An attacker examines differences in ciphertext outputs resulting from small changes in the input to deduce key patterns in a symmetric algorithm. What method is being employed?
You are investigating unauthorized access to a web application using token-based authentication. Tokens expire after 30 minutes. Server logs show multiple failed login attempts using expired tokens within a short window, followed by successful access with a valid token. What is the most likely attack scenario?
Which countermeasure best mitigates brute-force attacks on Bluetooth SSP?
A penetration tester suspects that a web application's product search feature is vulnerable to SQL injection. The tester needs to confirm this by manipulating the SQL query. What is the best technique to test for SQL injection?
Firewalk has just completed the second phase (the scanning phase), and a technician receives the output shown below. What conclusions can be drawn based on these scan results?
TCP port 21 no response
TCP port 22 no response
TCP port 23 Time-to-live exceeded
A penetration tester identifies malware on a system that hides its presence and gives an attacker access to administrative functions without being detected. What type of malware is this?
A city’s power management system relies on SCADA infrastructure. Recent anomalies include inconsistent sensor readings and intermittent outages. Security analysts suspect a side-channel attack designed to extract sensitive information covertly from SCADA devices. Which investigative technique would best confirm this type of attack?
Jack, a disgruntled ex-employee of Incalsol Ltd., decided to inject fileless malware into Incalsol's systems. To deliver the malware, he used the current employees' email IDs to send fraudulent emails embedded with malicious links that seem to be legitimate. When a victim employee clicks on the link, they are directed to a fraudulent website that automatically loads Flash and triggers the exploit. What is the technique used byjack to launch the fileless malware on the target systems?
Juliet, a security researcher in an organization, was tasked with checking for the authenticity of images to be used in the organization's magazines. She used these images as a search query and tracked the original source and details of the images, which included photographs, profile pictures, and memes. Which of the following footprinting techniques did Rachel use to finish her task?
Under what conditions does a secondary name server request a zone transfer from a primary name server?
Your company, SecureTech Inc., is planning to transmit some sensitive data over an unsecured communication channel. As a cyber security expert, you decide to use symmetric key encryption to protect the data. However,
you must also ensure the secure exchange of the symmetric key. Which of the following protocols would you recommend to the team to achieve this?
Calvin, a software developer, uses a feature that helps him auto-generate the content of a web page without manual involvement and is integrated with SSI directives. This leads to a vulnerability in the developed web application as this feature accepts remote user inputs and uses them on the page. Hackers can exploit this feature and pass malicious SSI directives as input values to perform malicious activities such as modifying and erasing server files. What is the type of injection attack Calvin's web application is susceptible to?
A CEH has mirrored a website, identified session hijacking risk, and wants to minimize detection. What is the most appropriate next step?
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A senior executive receives a personalized email titled “Annual Performance Review 2024.” The email includes a malicious PDF that installs a backdoor when opened. The message appears to originate from the CEO and uses official company branding. Which phishing technique does this scenario best illustrate?
Ricardo has discovered the username for an application in his targets environment. As he has a limited amount of time, he decides to attempt to use a list of common passwords he found on the Internet. He compiles them into a list and then feeds that list as an argument into his password-cracking application, what type of attack is Ricardo performing?
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
in an attempt to increase the security of your network, you Implement a solution that will help keep your wireless network undiscoverable and accessible only to those that know It. How do you accomplish this?
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, DELETE, PUT, TRACE) using NMAP script engine. What Nmap script will help you with this task?
An attacker performs DNS cache snooping using the dig command with the +norecurse flag against a known DNS server. The server returns NOERROR but provides no answer to the query. What does this most likely suggest?
A DDOS attack is performed at layer 7 to take down web infrastructure. Partial HTTP requests are sent to the web infrastructure or applications. Upon receiving a partial request, the target servers opens multiple connections and keeps waiting for the requests to complete.
Which attack is being described here?
An ethical hacker is hired to conduct a comprehensive network scan of a large organization that strongly suspects potential intrusions into their internal systems. The hacker decides to employ a combination of scanning tools to obtain a detailed understanding of the network. Which sequence of actions would provide the most comprehensive information about the network's status?
Alice needs to send a confidential document to her coworker. Bryan. Their company has public key infrastructure set up. Therefore. Alice both encrypts the message and digitally signs it. Alice uses_______to encrypt the message, and Bryan uses__________to confirm the digital signature.
A large media-streaming company receives complaints that its web application is timing out or failing to load. Security analysts observe the web server is overwhelmed with a large number of open HTTP connections, transmitting data extremely slowly. These connections remain open indefinitely, exhausting server resources without consuming excessive bandwidth. The team suspects an application-layer DoS attack. Which attack is most likely responsible?
If executives are found liable for not properly protecting their company’s assets and information systems, what type of law would apply in this situation?
A cybersecurity team identifies suspicious outbound network traffic. Investigation reveals malware utilizing the Background Intelligent Transfer Service (BITS) to evade firewall detection. Why would attackers use this service to conceal malicious activities?
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
During a red team test, a web application dynamically builds SQL queries using a numeric URL parameter. The tester sends the following request:
http://vulnerableapp.local/view.php?id=1; DROP TABLE users;
The application throws errors and the users table is deleted. Which SQL injection technique was used?
A penetration tester evaluates the security of an iOS mobile application that handles sensitive user information. The tester discovers that the application is vulnerable to insecure data transmission. What is the most effective method to exploit this vulnerability?
#!/usr/bin/python
import socket
buffer=["A"]
counter=50
while len(buffer)<=100:
buffer.append("A"*counter)
counter=counter+50
commands=["HELP","STATS","RTIME","LTIME","SRUN","TRUN","GMON","GDOG","KSTET","GTER","HTER","LTER","KSTAN"]
for command in commands:
for buffstring in buffer:
print "Exploiting " + command + ": " + str(len(buffstring))
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('127.0.0.1', 9999))
s.recv(50)
s.send(command + buffstring)
s.close()
What is the code written for?
Maria is conducting passive reconnaissance on a competitor without interacting with their systems. Which method would be least appropriate and potentially risky?
Insecure direct object reference is a type of vulnerability where the application does not verify if the user is authorized to access the internal object via its name or key. Suppose a malicious user Rob tries to get access to the account of a benign user Ned.
Which of the following requests best illustrates an attempt to exploit an insecure direct object reference vulnerability?
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host
10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he
applied his ACL configuration in the router, nobody can access the ftp, and the permitted hosts cannot access
the Internet. According to the next configuration, what is happening in the network?
access-list 102 deny tcp any any
access-list 104 permit udp host 10.0.0.3 any
access-list 110 permit tcp host 10.0.0.2 eq www any
access-list 108 permit tcp any eq ftp any
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
Which is the first step followed by Vulnerability Scanners for scanning a network?
“........is an attack type for a rogue Wi-Fi access point that appears to be a legitimate one offered on the premises, but actually has been set up to eavesdrop on wireless communications. It is the wireless version of the phishing scam. An attacker fools wireless users into connecting a laptop or mobile phone to a tainted hot-spot by posing as a legitimate provider. This type of attack may be used to steal the passwords of
unsuspecting users by either snooping the communication link or by phishing, which involves setting up a fraudulent web site and luring people there.”
Fill in the blank with appropriate choice.
A penetration tester is conducting an assessment of a web application for a financial institution. The application uses form-based authentication and does not implement account lockout policies after multiple failed login attempts. Interestingly, the application displays detailed error messages that disclose whether the username or password entered is incorrect. The tester also notices that the application uses HTTP headers to prevent clickjacking attacks but does not implement Content Security Policy (CSP). With these observations, which of the following attack methods would likely be the most effective for the penetration tester to exploit these vulnerabilities and attempt unauthorized access?
in this attack, an adversary tricks a victim into reinstalling an already-in-use key. This is achieved by manipulating and replaying cryptographic handshake messages. When the victim reinstall the key, associated parameters such as the incremental transmit packet number and receive packet number are reset to their initial values. What is this attack called?
DHCP snooping is a great solution to prevent rogue DHCP servers on your network. Which security feature on switchers leverages the DHCP snooping database to help prevent man-in-the-middle attacks?
A penetration tester is tasked with assessing the security of a smart home IoT device that communicates with a mobile app over an unencrypted connection. The tester wants to intercept the communication and extract sensitive information. What is the most effective approach to exploit this vulnerability?
John, a disgruntled ex-employee of an organization, contacted a professional hacker to exploit the organization. In the attack process, the professional hacker Installed a scanner on a machine belonging to one of the vktims and scanned several machines on the same network to Identify vulnerabilities to perform further exploitation. What is the type of vulnerability assessment tool employed by John in the above scenario?
An attacker scans a host with the below command. Which three flags are set?
# nmap -sX host.domain.com
During security awareness training, which scenario best describes a tailgating social engineering attack?
Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications. He installed a fake communication tower between two authentic endpoints to mislead the victim. Bobby used this virtual tower to interrupt the data transmission between the user and real tower, attempting to hijack an active session, upon receiving the users request. Bobby manipulated the traffic with the virtual tower and redirected the victim to a malicious website. What is the attack performed by Bobby in the above scenario?
A security analyst investigates unusual east-west traffic on a corporate network. A rogue device has been physically inserted between a workstation and the switch, enabling unauthorized access while inheriting the workstation’s authenticated network state. Which evasion technique is being used?
Packet fragmentation is used as an evasion technique. Which IDS configuration best counters this?
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
An attacker identified that a user and an access point are both compatible with WPA2 and WPA3 encryption. The attacker installed a rogue access point with only WPA2 compatibility in the vicinity and forced the victim to go through the WPA2 four-way handshake to get connected. After the connection was established, the attacker used automated tools to crack WPA2-encrypted messages. What is the attack performed in the above scenario?
During a security assessment of a cloud-hosted application using SOAP-based web services, a red team operator intercepts a valid SOAP request, duplicates the signed message body, inserts it into the same envelope, and forwards it. Due to improper validation, the server accepts the duplicated body and executes unauthorized code. What type of attack does this represent?
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network’s external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file.
What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
Elante company has recently hired James as a penetration tester. He was tasked with performing enumeration on an organization's network. In the process of enumeration, James discovered a service that is accessible to external sources. This service runs directly on port 21.
What is the service enumerated by James in the above scenario?
Which advanced mobile hacking technique is the hardest to detect and mitigate in a healthcare environment?
When conducting a penetration test, it is crucial to use all means to get all available information about the target network. One of the ways to do that is by sniffing the network. Which of the following cannot be performed by passive network sniffing?
A large company intends to use BlackBerry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SYN ping scan?
Peter extracts the SIDs list from a Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:

[Image showing multiple user accounts with their Security Identifiers (SIDs)]
From the above list identify the user account with System Administrator privileges.