Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT)
Last Update Mar 1, 2026
Total Questions : 61
We are offering FREE 300-740 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 300-740 free exam questions and then go for complete pool of Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) test questions that will help you more.




Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?

Refer to the exhibit. An engineer must configure a global allow list in Cisco Umbrella for the cisco.com domain. All other domains must be blocked. After creating a new policy and adding the cisco.com domain, the engineer attempts to access a site outside of cisco.com and is successful. Which additional Security Settings action must be taken to meet the requirement?
Which mitigation technique does a web application firewall use to protect a web server against DDoS attacks?

Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?

Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is occurring?


Refer to the exhibit. An engineer must create a firewall policy to allow web server communication only. The indicated firewall policy was applied; however, a recent audit requires that all firewall policies be optimized. Which set of rules must be deleted?


Refer to the exhibit. An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work. Which two commands must be run on each firewall to meet the requirements? (Choose two.)

Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report. Which activity does the output verify?
An administrator received an incident report indicating suspicious activity of a user using a corporate device. The manager requested that the credentials of user user1@cisco.com be reset and synced via the Active Directory. Removing the account should be avoided and used for further investigation on data leak. Which configuration must the administrator apply on the Duo Admin Panel?
A security analyst detects an employee endpoint making connections to a malicious IP on the internet and downloaded a file named Test0511127691C.pdf. The analyst discovers the machine is infected by trojan malware. What must the analyst do to mitigate the threat using Cisco Secure Endpoint?

Refer to the exhibit. An engineer configured a default segmentation policy in Cisco Secure Workload to block SMTP traffic. During testing, it is observed that the SMTP traffic is still allowed. Which action must the engineer take to complete the configuration?

Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?
An administrator must deploy an endpoint posture policy for all users. The organization wants to have all endpoints checked against antimalware definitions and operating system updates and ensure that the correct Secure Client modules are installed properly. How must the administrator meet the requirements?
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and cloud services. The ACME Corporation already performs risk assessments for on-premises services and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings. What Cisco Umbrella function should be used to meet the requirement?


Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)

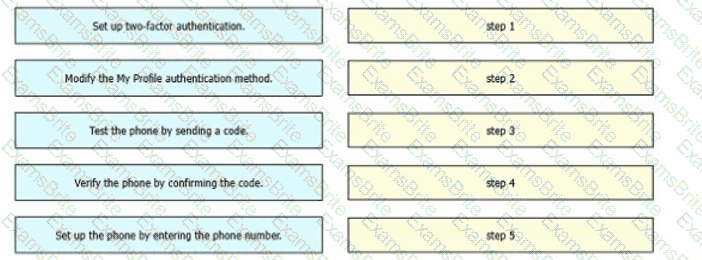
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile and received an activation code. Drag and drop the steps from left to right to complete the configuration.
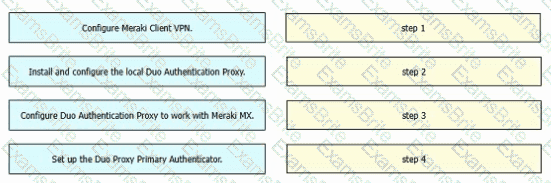
Drag and drop the tasks from the left into order on the right to implement adding Duo multifactor authentication to Meraki Client VPN login.