
Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
Last Update Mar 3, 2026
Total Questions : 277
We are offering FREE 300-430 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 300-430 free exam questions and then go for complete pool of Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI) test questions that will help you more.



The Cisco Hyperlocation detection threshold is currently set to -50 dBm. After reviewing the wireless user location, discrepancies have been noticed. To improve the Cisco Hyperlocation accuracy, an engineer attempts to change the detection threshold to -100 dBm. However, the Cisco Catalyst 9800 Series Wireless Controller does not allow this change to be applied. What actions should be taken to resolve this issue?
An engineer is implementing RADIUS to restrict administrative control to the network with the WLC management IP address of 192.168.1.10 and an AP subnet of 192.168.2.0/24. Which entry does the engineer define in the RADIUS server?
An engineer has successfully implemented 10 active RFID tags in an office environment. The tags are not visible when the location accuracy is tested on the Cisco CMX Detect and Locate window. Which setting on Cisco CMX allows the engineer to view the tags?
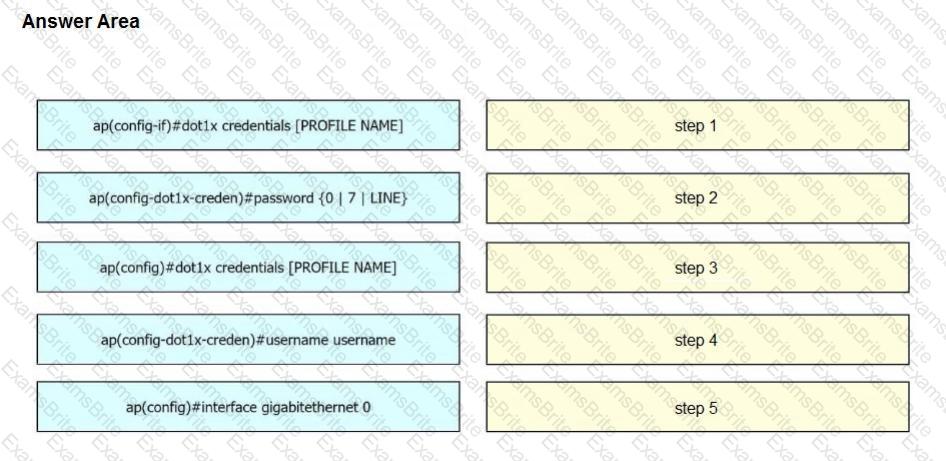
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.
A wireless engineer has performed a Wireshark ccapture on an 802.1x authentication process to troubleshoot a connectivity issue.
Which two types of packet does the EAP contain? (Choose two.)
Refer to the exhibit.
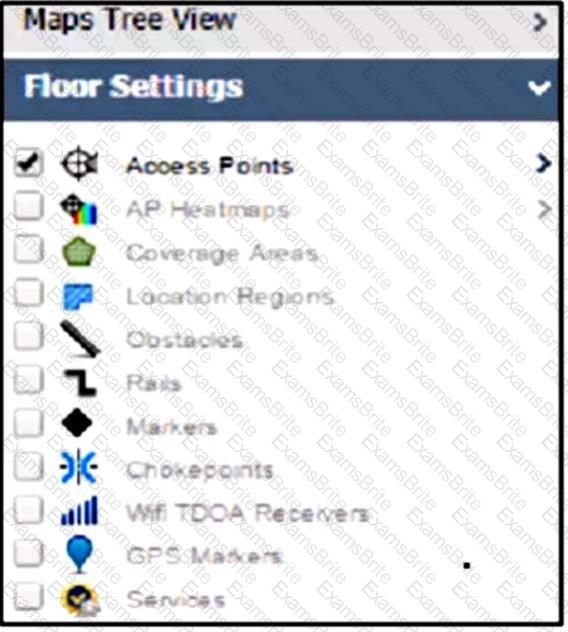
An engineer must provide a position of rogue APs on a floor map using Cisco PI 3.0, but no rogue AP options are showing on the left-hand navigation menu under Maps. What is the reason for this omission?
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
The security learn is concerned about the access to all network devices, including the Cisco WLC. To permit only the admin subnet to have access to management, a CPU ACL is created and applied. However, guest users cannot get to the web portal. What must be configured to permit only admins to have access?
Company XYZ recently migrated from AireOS to IOS XE 9800 WLCs. The Internet bandwidth must be limited to 5 Mbps for each guest client as per the global standard. In which configuration on the Cisco Catalyst 9800 WLC must the QoS requirement be added?
A network administrator managing a Cisco Catalyst 9800 WLC must place all iOS-connected devices to the guest SSID on VLAN 101. The rest of the clients must connect on VLAN 102 to distribute load across subnets. To achieve this configuration, the administrator configures a local policy on the WLC. Which two configurations are required? (Choose two.)
An engineer is troubleshooting rogue access points that are showing up in Cisco Prime Infrastructure.
What is maximum number of APS the engineer can use to contain an identified rogue access point in the WLC?
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
A Cisco 8540 WLC manages Cisco Aironet 4800 Series Aps and sends AoA data to a Cisco CMX 3375 Appliance for Hyperlocation. The load from the WLC is distributed to another virtual CMX server using CMX grouping. The virtual CMX server shows location RSSI data and not Hyperlocation. No AoA metrics are shown on the metrics page of the CMX virtual appliance under System > Metrics > Location Metrics. How must the network administrator resolve this issue?
Which two protocols are used to communicate between the Cisco MSE and the Cisco Prime Infrastructure network management software? (Choose two.)
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
Refer to the exhibit.
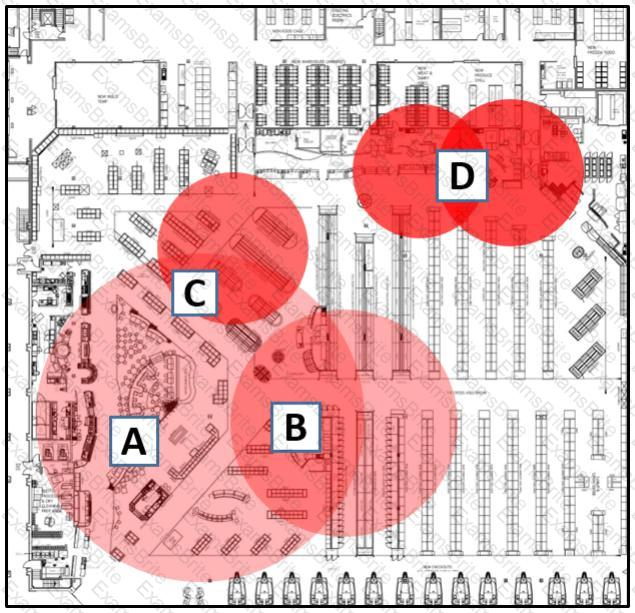
Which area indicates the greatest impact on the wireless network when viewing the Cisco CleanAir Zone of Impact map of interferers?
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
An enterprise has two WLANs configured on WLC. It is reported that when converting APs to FlexConnect mode, WLAN A works but WLAN B does not. When converting APs to local mode, WLAN B works, but WLAN A does not. Which action is needed to complete this configuration?
In a Cisco WLAN deployment, it is required that all Aps from branch1 remain operational even if the control plane CAPWAP tunnel is down because of a WAN failure to headquarters. Which operational mode must be configured on the APs?
An engineer is implementing Cisco Identity-Based Networking on a Cisco AireOS controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy. What is the resulting ACL when a Human Resources user connects?
Refer to the exhibit. A network administrator must automate notifications for Security Advisories Data reports on the Cisco Catalyst Center v2.3.7 using the Report notification feature. Preferring a programmable approach over UI/CLI, the administrator decides to create a webhook via the Cisco DNA Center API to send real-time HTTP notifications to an external application. The webhook URL https://example.com/webhook uses HTTPS with a self-signed certificate, which requires a specific configuration in the payload to ensure the webhook functions correctly. Which code snippet must be placed onto the box in the code to complete the Python script that configures the webhook to use the self-signed certificate to extract the Security Advisories Data report?

A corporation has recently implemented a BYOD policy at their HQ. Which two risks should the security director be concerned about? (Choose two.)
Refer to the exhibit.
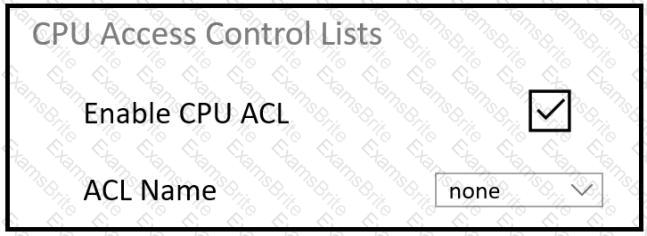
An engineer must restrict some subnets to have access to the WLC. When the CPU ACL function is enabled, no ACLs in the drop-down list are seen. What is the cause of the problem?
An SSID is set up with central web authentication using Cisco ISE The new SSID uses guest tunneling from the foreign controller to the anchor controller. Which device must be configured ISE as the one performing the RADIUS authentication requests for the web authentication method?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A wireless administrator receives this information to complete a CMX deployment in high availability by using version 10.6 to gather analytics.
IP address of the primary server
IP address of the secondary server
failover mode to be configured as automatic
root password of the secondary server
email ID for NOC notifications
Enabling high availability fails when these parameters are used. Which action resolves the issue?
Refer to the exhibit.
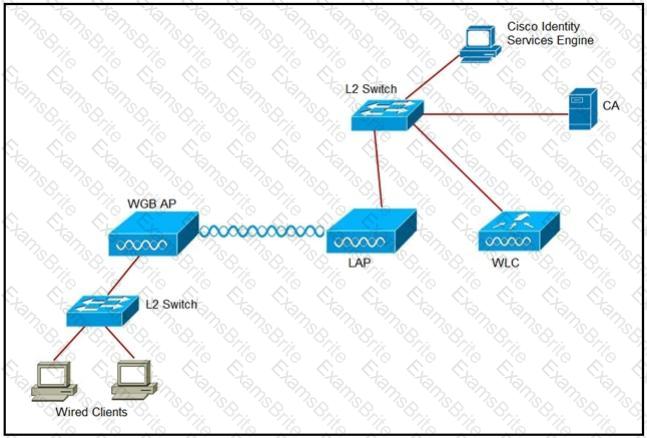
An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.)
An engineer has many different WLANs on a WLC but does not want to broadcast them to every AP in the building. Which group must be configured on the WLC to allow different WLANs on the different APs without creating new interfaces?
Refer to the exhibit.
An engineer needs to configure location services in an office. The requirement is to use FastLocate and achieve higher locations refresh rates. Which location-based technique should be implemented?
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
Which CLI command do you use to shut down the 2.4 GHz radio of the Floor1_AP1 AP on a Cisco 3850 Switch?
A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
A network is set up to support wired and wireless clients. Both types must authenticate using 802.1X before connecting to the network. Different types of client authentication must be separated on a Cisco ISE deployment. Which two configuration items achieve this task? (Choose two.)
The marketing department creates a promotion video for the branch store. Only interested hosts must receive the video over wireless multicast. What allows this feature?
A customer has a distributed wireless deployment model where the WLCs are located in the data centers. Because the file servers are located in the data center, the traffic from the corporate WLAN “Corp-401266017” must go through the controllers, where the guest WLAN “Guest-19283746” traffic must use the local Internet line installed in each office. Which configuration will accomplish this task?
CMX Facebook Wi-Fi allows access to the network before authentication. Which two elements are available? (Choose two.)
A customer wants to allow employees to easily onboard their personal devices to the wireless network. The visitors also must be able to connect to the same network without the need to engage with anyone from the reception desk. Which process must be configured on Cisco ISE to support this requirement?
A network is set up to support wired and wireless clients. Both types must authenticate using 802.1X before connecting to the network. Different types of client authentication must be separated on a Cisco ISE deployment. Which two configuration items achieve this task? (Choose two.)
An engineer is deploying a virtual MSE. The network has 3000 APs and needs 7000 IPS licenses.
To which size server does the engineer scale it?
A network engineer created a new wireless network that will be used for guest access. The corporate network must utilize all rates. The guest network must use only lower rates instead of 802.11n data rates. To what must the WMM policy of the WLAN be set to accomplish this task?
Refer to the exhibit.
An engineer configured a BYOD policy that allows for printing on the WLAN using Bonjour services. However, the engineer cannot get printing to work. The WLC firmware is 8.x. What must be implemented on the controller?
Refer to the exhibit.
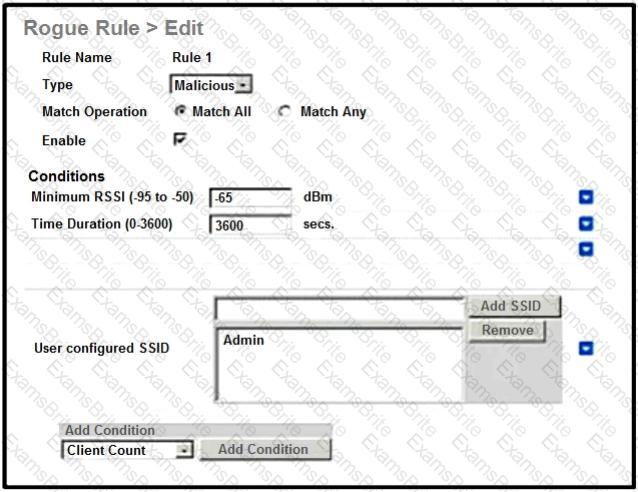
An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
Refer to the exhibit.

Which area indicates the greatest impact on the wireless network when viewing the Cisco CleanAir Zone of Impact map of interferers?
A customer requires wireless traffic from the branch to be routed through the firewall at corporate headquarters. A RADIUS server is in each branch location. Which Cisco FlexConnect configuration must be used?
An engineer wants to configure WebEx to adjust the precedence and override the QoS profile on the WLAN. Which configuration is needed to complete this task?
An engineer must run a Client Traffic Stream Metrics report in Cisco Prime Infrastructure. Which task must be run before the report?
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
An engineer configures the wireless LAN controller to perform 802.1x user authentication. Which configuration must be enabled to ensure that client devices can connect to the wireless, even when WLC cannot communicate with the RADIUS?
Refer to the exhibit.

An engineer must provide a position of rogue APs on a floor map using Cisco PI 3.0, but no rogue AP options are showing on the left-hand navigation menu under Maps. What is the reason for this omission?
A customer wants the APs in the CEO’s office to have different usernames and passwords for administrative support than the other APs deployed throughout the facility. Which feature must be enabled on the WLC and APs to achieve this goal?
An engineer must implement intrusion protection on the WLAN. The AP coverage is adequate and on-channel attacks are the primary concern. The building is historic, which makes adding APs difficult. Which AP mode and submode must be implemented?
An engineer is planning an image upgrade of the WLC, and hundreds of APs are spread across remote sites with limited WAN bandwidth. The engineer must minimize the WAN utilization for this upgrade. Which approach must be used for the AP image upgrade?
Refer to the exhibit.
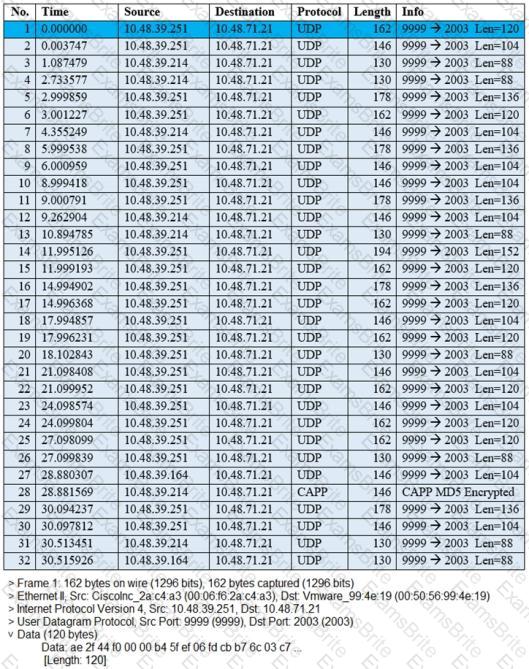
The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
An engineer added more APs to newly renovated areas in building. The engineer is now receiving Out-of-Sync alarms on Cisco Prime Infrastructure. Which two actions resolve this issue? (Choose two.)
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
A network engineer wants to implement QoS across the network that supports multiple VLANs. All the APs are connected to switch ports and are configured in local mode. Which trust model must be configured on the switch ports to which the APs are connected?
An engineer is configuring multicast for wireless for an all-company video meeting on a network using EIGRP and BGP within a single domain from a single source. Which type of multicast routing should be implemented?
A network engineer has been hired to perform a new MSE implementation on an existing network. The MSE must be installed in a different network than the Cisco WLC. Which configuration allows the devices to communicate over NMSP?
What must be configured on the Global Configuration page of the WLC for an AP to use 802.1x to authenticate to the wired infrastructure?
Refer to the exhibit.
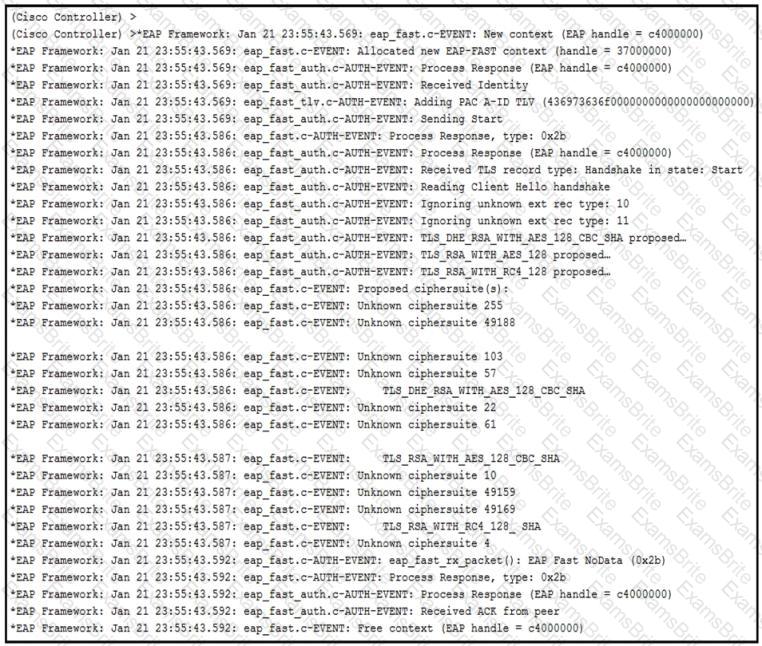
An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
A wireless network has been implemented to enable multicast video to be streamed reliably over the wireless link to the wireless users. After a client reports that the video is unable to stream, the administrator determines that the client is connecting at a data rate of 12 Mbps and is trying to stream to a valid multicast address on the network. Which two actions must be applied? (Choose two.)
What is an important consideration when implementing a dual SSID design for BYOD?
Refer to the exhibit.

An engineer configured a BYOD policy that allows for printing on the WLAN using Bonjour services. However, the engineer cannot get printing to work. The WLC firmware is 8.x. What must be implemented on the controller?
After installing and configuring Cisco CMX, an administrator must change the NTP server on the Cisco CMX server. Which action accomplishes this task?
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?
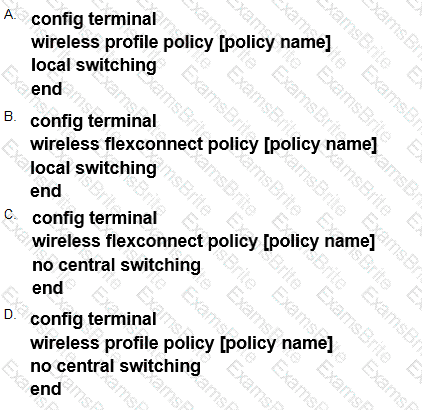
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
What is characteristic of Multicast mode that affects the wireless network when configured on a Cisco WLC?
Refer to the exhibit.

An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
An engineer needs to configure an autonomous AP for 802.1x authentication. To achieve the highest security an authentication server is used for user authentication. During testing, the AP fails to pass the user authentication request to the authentication server. Which two details need to be configured on the AP to allow communication between the server and the AP? (Choose two.)
An engineer is using Cisco Prime Infrastructure reporting to monitor the state of security on the WLAN. Which output is produced when the Adaptive wIPS Top 10 AP report is run?
An engineer must implement a BYOD policy with these requirements:
Onboarding unknown machines
Easily scalable
Low overhead on the wireless network
Which method satisfies these requirements?
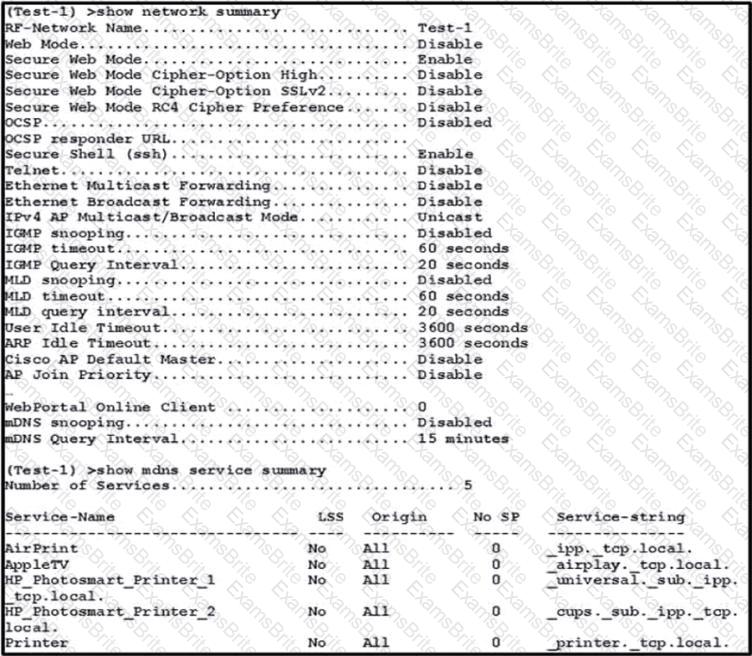
A WLC must be configured to allow multiple mDNS profiles based on a user authentication profile configured in Cisco ISE. Which WLAN setting must be configured?
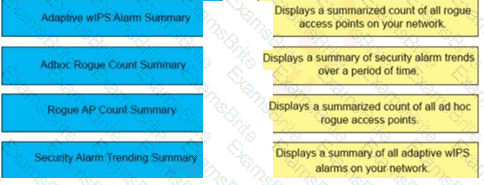
A wireless engineer wants to schedule monthly security reports in Cisco Prime infrastructure. Drag and drop the report the from the left onto the expected results when the report is generated on the right.
Which two restrictions are in place with regards to configuring mDNS? (Choose two.)
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
Refer to the exhibit.
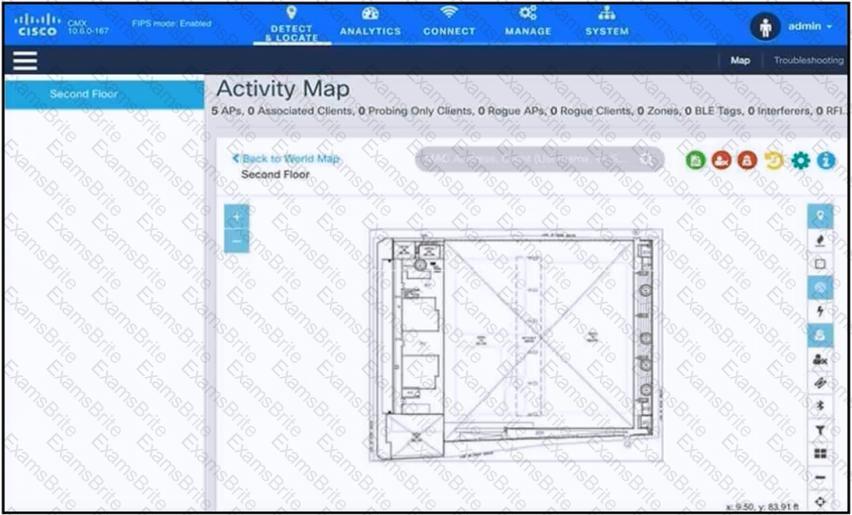
An engineer has deployed the Cisco CMX solution to track and detect the number of users who visit the office each day. The CMX dashboard is not showing any data. Which action resolves this issue?