
Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Last Update Mar 1, 2026
Total Questions : 131
We are offering FREE 300-215 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 300-215 free exam questions and then go for complete pool of Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) test questions that will help you more.



Which type of record enables forensics analysts to identify fileless malware on Windows machines?
An investigator notices that GRE packets are going undetected over the public network. What is occurring?
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
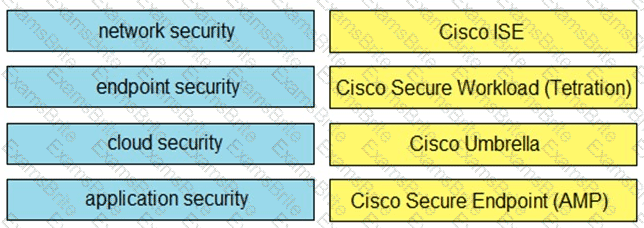
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Refer to the exhibit.
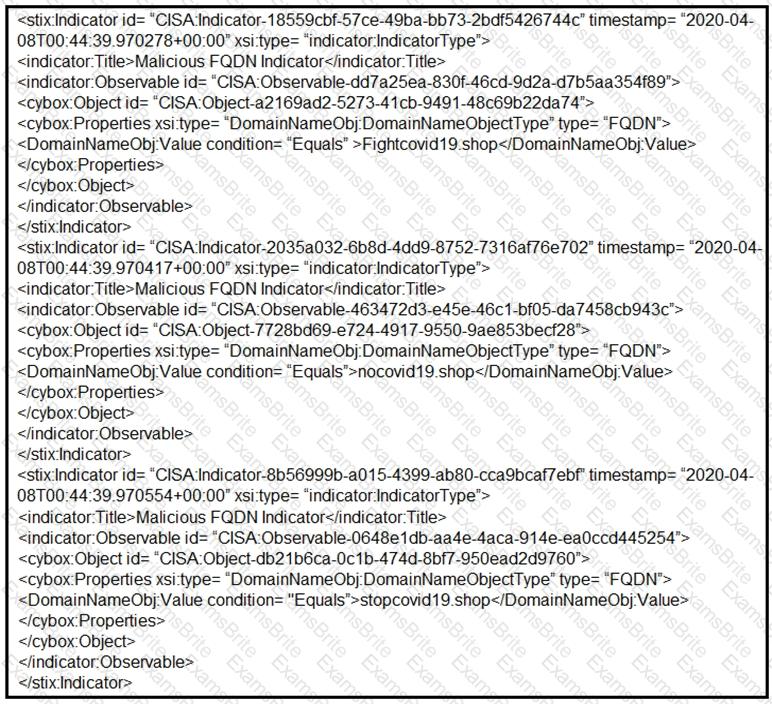
Which two actions should be taken based on the intelligence information? (Choose two.)
What can the blue team achieve by using Hex Fiend against a piece of malware?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
Refer to the exhibit.

Which encoding method is used to obfuscate the script?
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
Which issue is associated with gathering evidence from virtualized environments provided by major cloud vendors?
An organization fell victim to a ransomware attack that successfully infected 256 hosts within its network. In the aftermath of this incident, the organization's cybersecurity team must prepare a thorough root cause analysis report. This report aims to identify the primary factor or factors that led to the successful ransomware attack and to develop strategies for preventing similar incidents in the future. In this context, what should the cybersecurity engineer include in the root cause analysis report to demonstrate the underlying cause of the incident?
During an overnight shift, a cybersecurity team at a global trading firm detects irregular activity The network intrusion system flags an encrypted traffic spike from high-value transaction servers to an anonymous Tor exit node Simultaneously, internal surveillance tools report unusual database queries and access patterns resembling exfiltration techniques Which focused action should the team take first to analyze and address these potential security threats?
A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)
An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
An insider scattered multiple USB flash drives with zero-day malware in a company HQ building. Many employees connected the USB flash drives to their workstations. An attacker was able to get access to endpoints from outside, steal user credentials, and exfiltrate confidential information from internal web resources. Which two steps prevent these types of security incidents in the future? (Choose two.)
Refer to the exhibit.
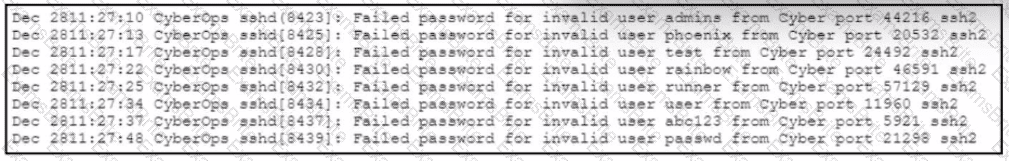
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities. Which attack vector is used and what mitigation can the analyst suggest?
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?
A financial company handling international transactions recently experienced a complex security incident The incident involves simultaneous DDoS attacks, suspected internal data leakage and the discovery of sophisticated malware implants that have remained dormant until triggered remotely During the incident it became clear that the current procedures are inadequate and plans to tackle issues were created on the go To counter this problem going forward, the IR team is developing an incident playbook to be used if a similar incident reoccurs Which set of elements of the playbook must be introduced?
Refer to the exhibit.
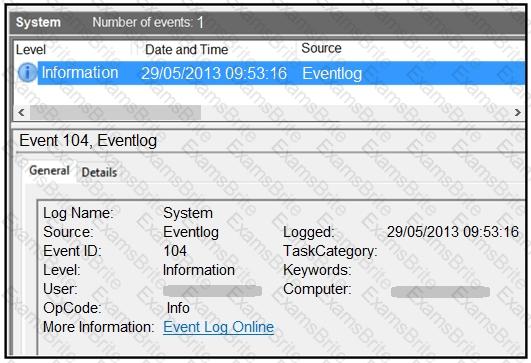
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
Refer to the exhibit.
Which two actions should be taken as a result of this information? (Choose two.)
An engineer received a report of a suspicious email from an employee. The employee had already opened the attachment, which was an empty Word document. The engineer cannot identify any clear signs of compromise but while reviewing running processes, observes that PowerShell.exe was spawned by cmd.exe with a grandparent winword.exe process. What is the recommended action the engineer should take?
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
In a secure government communication network, an automated alert indicates the presence of anomalous DLL files injected into the system memory during a routine update of communication protocols. These DLL files are exhibiting beaconing behavior to a satellite IP known for signal interception risks. Concurrently, there is an uptick in encrypted traffic volumes that suggests possible data exfiltration. Which set of actions should the security engineer prioritize?
What is the purpose of YARA rules in malware analysis and now do the rules atd in identifying, classifying, and documenting malware?
Refer to the exhibit.
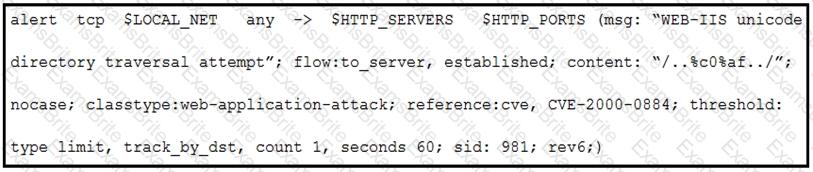
A company that uses only the Unix platform implemented an intrusion detection system. After the initial configuration, the number of alerts is overwhelming, and an engineer needs to analyze and classify the alerts. The highest number of alerts were generated from the signature shown in the exhibit. Which classification should the engineer assign to this event?
A security team received an alert of suspicious activity on a user’s Internet browser. The user’s anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)