
VMware NSX 4.X Professional V2
Last Update Feb 28, 2026
Total Questions : 115
We are offering FREE 2V0-41.24 VMware exam questions. All you do is to just go and sign up. Give your details, prepare 2V0-41.24 free exam questions and then go for complete pool of VMware NSX 4.X Professional V2 test questions that will help you more.



What are two valid options when configuring the scope of a distributed firewall rule? (Choose two.)
Where can an administrator see a visual overview of network connections between different VMs and different networks, within the NSX domain?
An NSX administrator is using ping to check connectivity between VM1 running on ESXi1 to VM2 running on ESXi2. The ping tests fail. The administrator knows the maximum transmission unit size on the physical switch is 1600.
Which command does the administrator use to check the VMware kernel ports for tunnel end point communication?
Which of the following exist only on Tler-1 Gateway firewall configurations and not on Tier-0?
An NSX administrator would like to export syslog events that capture messages related to NSX host preparation events.
Which message ID (msgid) should be used in the syslog export configuration command as a filter?
Which CLI command would an administrator use to allow syslog on an ESXi transport node when using the esxcli utility?
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
Refer to the exhibits.
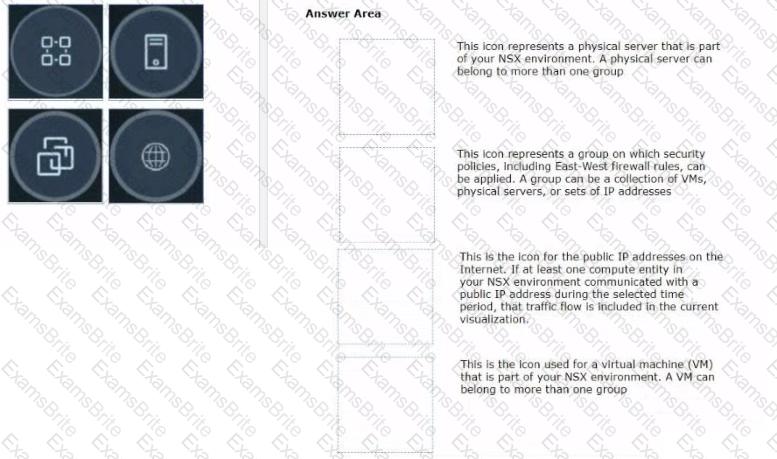
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
A customer is preparing to deploy a VMware Kubernetes solution in an NSX environment.
What is the minimum MTU size for the UPLINK profile?
An architect receives a request to apply distributed firewall in a customer environment without making changes to the network and vSphere environment. The architect decides to use Distributed Firewall on VDS.
Which two of the following requirements must be met in the environment? (Choose two.)
What is VMware’s recommendation for the minimum MTU requirements when planning an NSX deployment?
An administrator has been tasked with implementing the SSL certificates for the NSX Manager Cluster VIP.
Which is the correct way to implement this change?
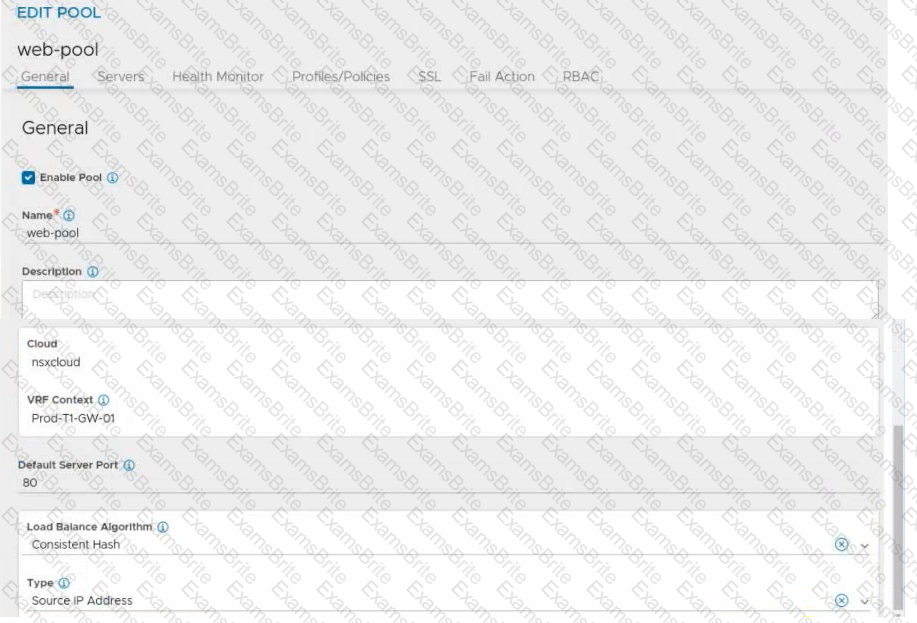
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to redistribute the traffic between the web servers. However, requests are sent to only one server
Which of the following pool configuration settings needs to be adjusted to resolve the problem? Mark the correct answer by clicking on the image.
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
What are the four types of role-based access control (RBAC) permissions? (Choose four.)
Which two of the following are used to configure Distributed Firewall on VDS? (Choose two.)
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
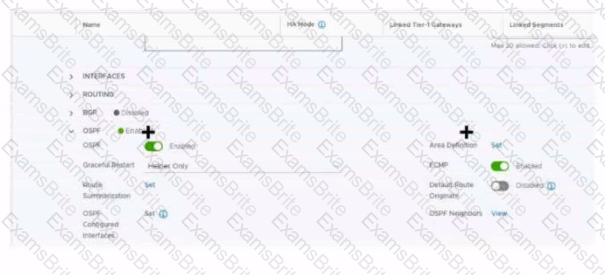
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
Which is the only supported mode in NSX Global Manager when using Federation?
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
An NSX administrator wants to create a Tier-0 Gateway to support equal cost multi-path (ECMP) routing.
Which failover detection protocol must be used to meet this requirement?
A company Is deploying NSX micro-segmentation in their vSphere environment to secure a simple application composed of web. app, and database tiers.
The naming convention will be:
• WKS-WEB-SRV-XXX
• WKY-APP-SRR-XXX
• WKI-DB-SRR-XXX
What is the optimal way to group them to enforce security policies from NSX?
Which three protocols could an NSX administrator use to transfer log messages to a remote log server? (Choose three.)
Which two tools are used for centralized logging in VMware NSX? (Choose two.)