
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Last Update Feb 28, 2026
Total Questions : 476
We are offering FREE 200-201 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 200-201 free exam questions and then go for complete pool of Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) test questions that will help you more.



Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
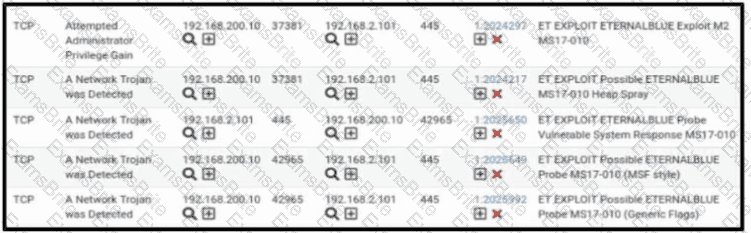
Refer to the exhibit. A security engineer receives several alerts from the SNORT IPS/IDS reporting malicious traffic. What should the engineer understand by examining the SNORT logs?
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
Refer to the exhibit.

An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
What is the impact of false negative alerts when compared to true negative alerts?
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data. The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
A data privacy officer at a marketing firm has received a request from a former client to delete all personally sensitive information held by the company. The firm operates globally and follows international data protection standards. The only information retained about the client is a unique customer ID, "051473912", which is not directly tied to the name, address, or any other identifiable details. Which action should the data privacy officer take?
What is the difference between deep packet inspection and stateful inspection?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Which security monitoring data type is associated with application server logs?
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
How does the approach of a behavioral detection system to identifying security threats compare to that of a rule-based detection system?
Refer to the exhibit.
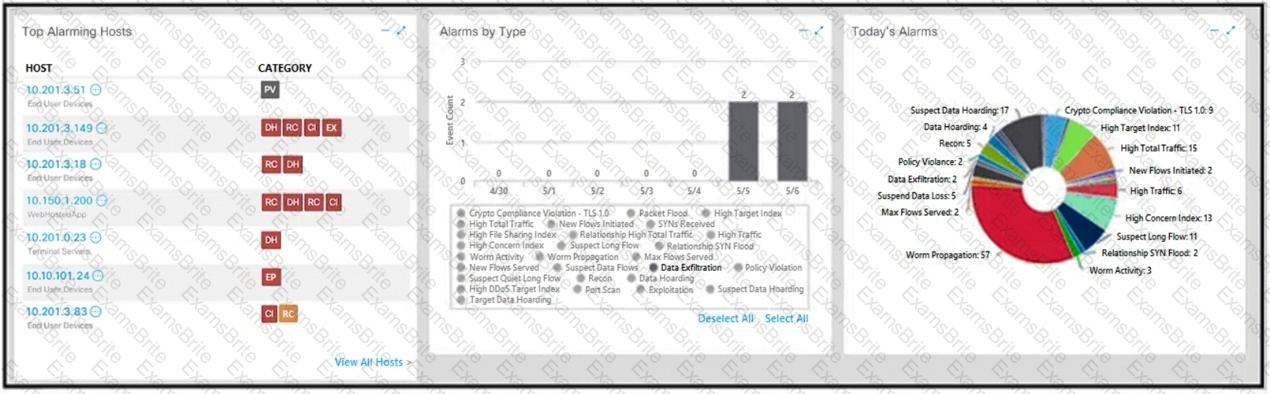
What is the potential threat identified in this Stealthwatch dashboard?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
A large load of data is being transferred to an external destination via UDP 53 port. Which obfuscation technique is used?
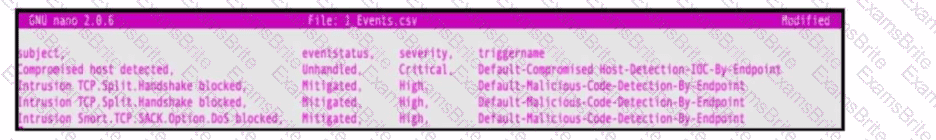
Refer to the exhibit. An engineer must map these events to the source technology that generated the event logs. To which technology do the generated logs belong?
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
Refer to the exhibit.
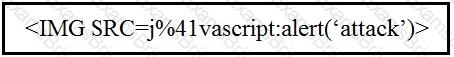
Which kind of attack method is depicted in this string?
What is the advantage of agent-based protection compared to agentless protection?
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
STION NO: 102
Refer to the exhibit.
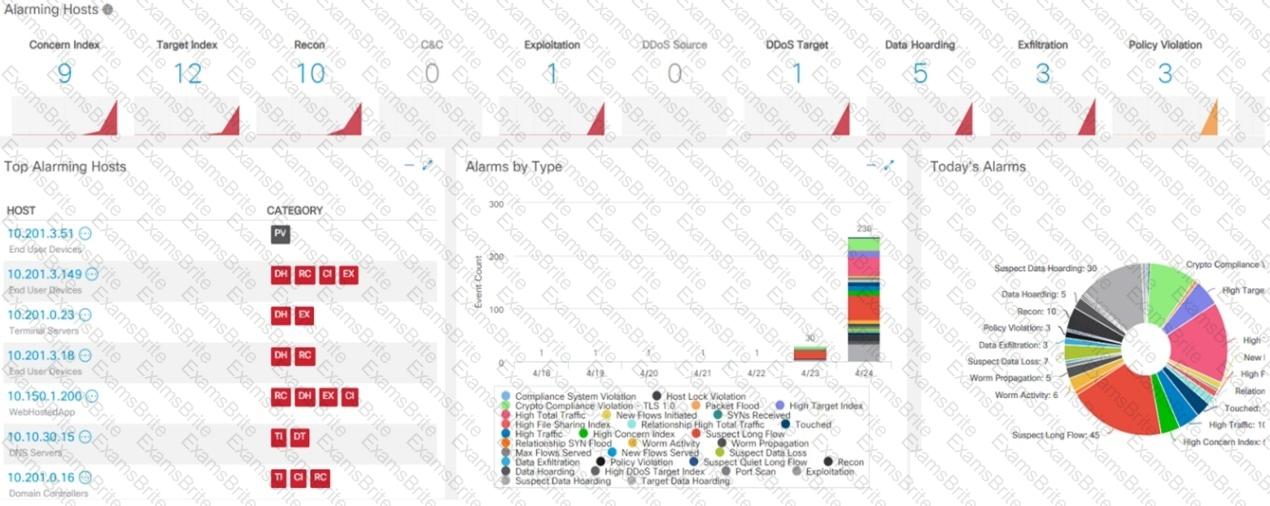
What is the potential threat identified in this Stealthwatch dashboard?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
An organization that develops high-end technology is going through an internal audit The organization uses two databases The main database stores patent information and a secondary database stores employee names and contact information A compliance team is asked to analyze the infrastructure and identify protected data Which two types of protected data should be identified? (Choose two)
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
Which technology on a host is used to isolate a running application from other applications?
Which access control should a chief information security officer select to protect extremely sensitive data categorized at various levels of confidentiality?
Exhibit.
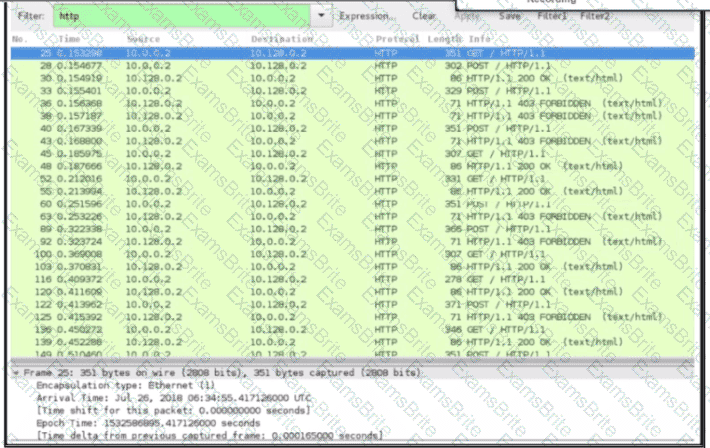
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
Refer to the exhibit.
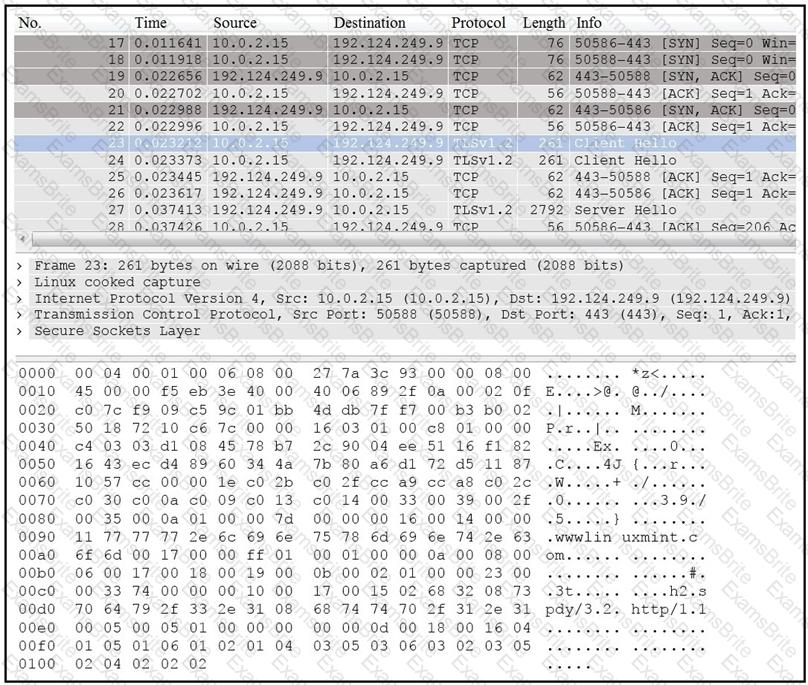
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Which principle reduces the risk of attackers gaining access to sensitive data by compromising a low-level user account?
An engineer must gather data for monitoring purposes from different network devices. The engineer needs to collect events from the local network and use that information for packet sniffing. The solution must create an exact copy of traffic and provide full fidelity. Which solution should the engineer use?
Which step in the incident response process researches an attacking host through logs in a SIEM?

Refer to the exhibit. A SOC team member receives a case from his colleague with notes attached. The artifacts and alerts associated with the case must be analyzed and a conclusion must be provided. What is the cause of the alert?
What describes the impact of false-positive alerts compared to false-negative alerts?
Refer to the exhibit.
An analyst receives an IDS alert pertaining to a possible data exfiltration attempt. An additional set of logs is collected from different systems and analyzed. Which type of evidence do the logs provide in relation to the primary alert from the IDS?
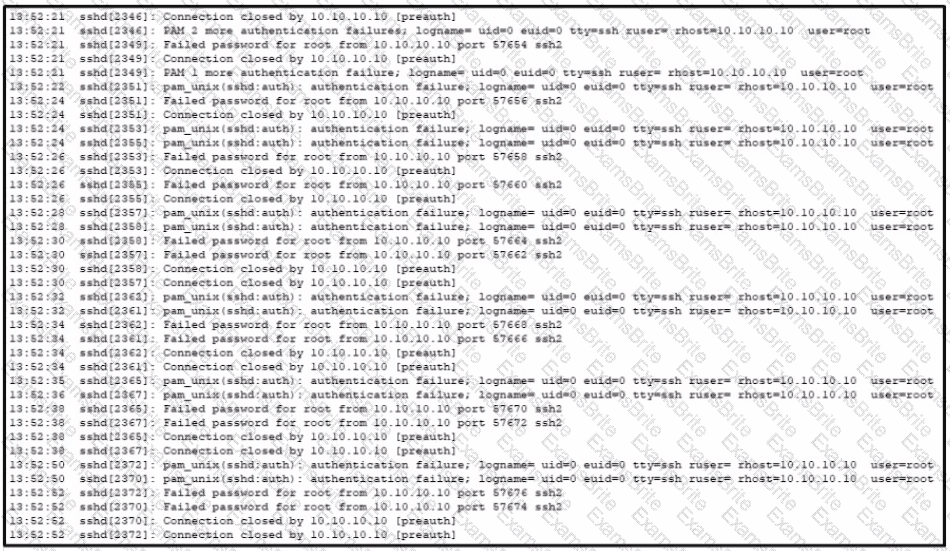
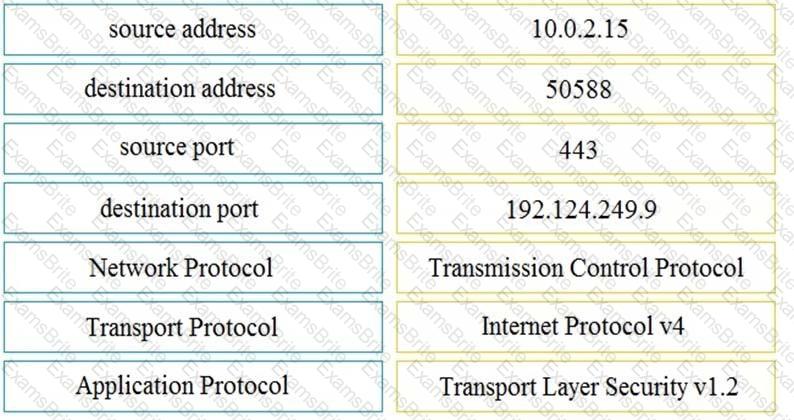
Refer to the exhibit A SOC analyst is examining the Auth.log file logs of one the breached systems What is the possible reason for this event log?
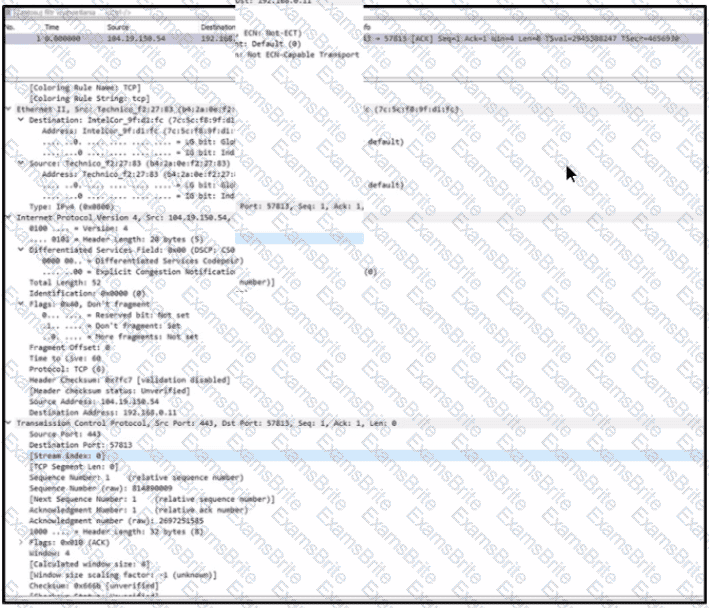
Refer to the exhibit. An engineer must use a 5-tuple approach to isolate a compromised host in a grouped set of logs.
Which data must the engineer use?
Refer to the exhibit.
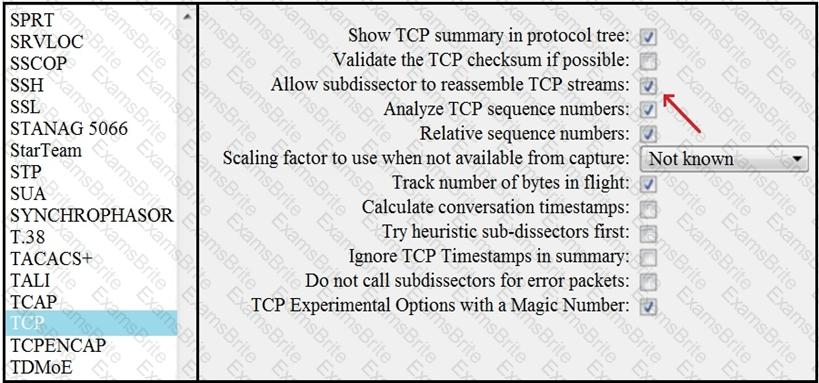
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Refer to the exhibit.
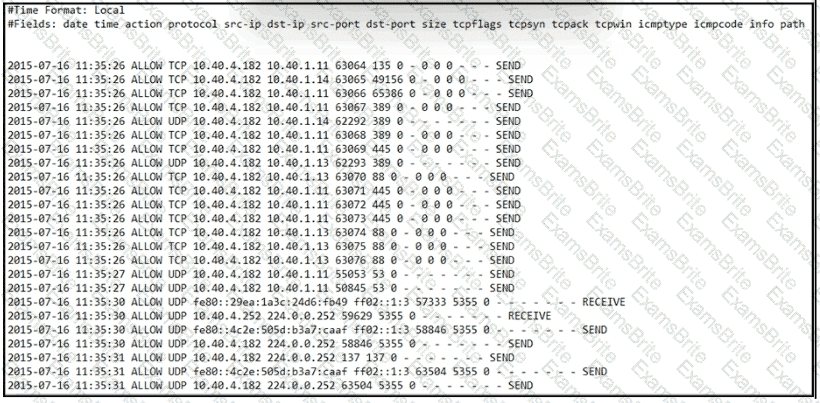
An engineer received an event log file to review. Which technology generated the log?
An engineer must configure network systems to detect command-and-control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology must be used to accomplish this task?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
What is the impact of false positive alerts on business compared to true positive?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
What is the difference between statistical detection and rule-based detection models?
An employee of a company receives an email with an attachment. They notice that this email is from a suspicious source, and they decide not to open the attached file. After further investigation, a security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model does this event belong?
Refer to the exhibit.
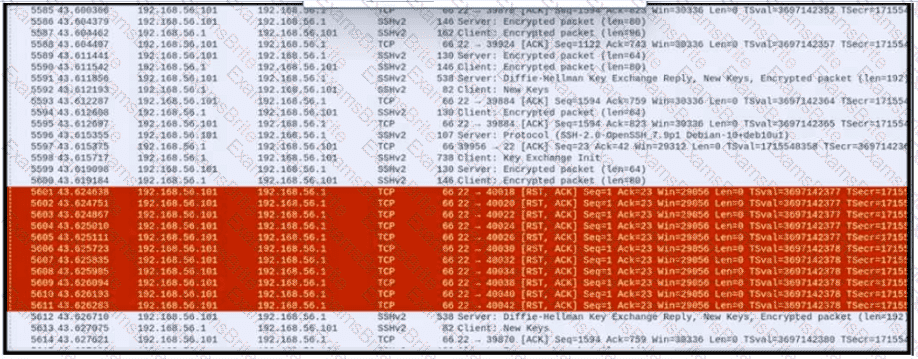
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
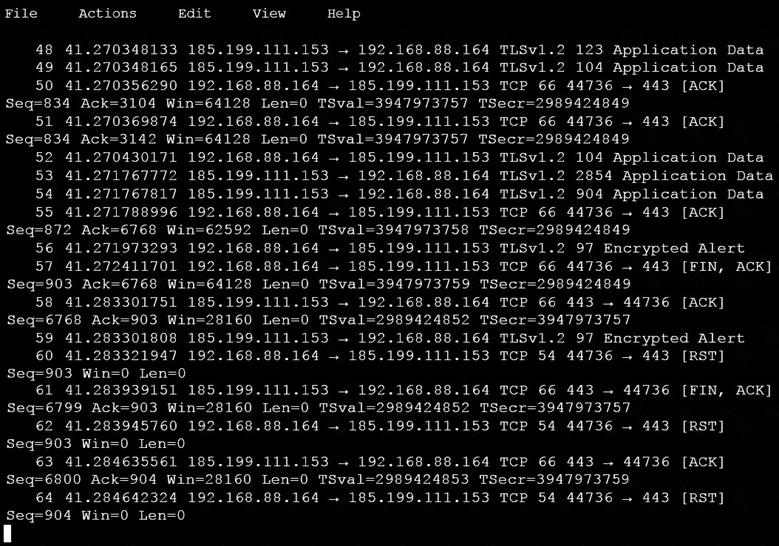
Which obfuscation technique is the attacker using?
What are the two differences between stateful and deep packet inspection? (Choose two )
What is a benefit of agent-based protection when compared to agentless protection?
An engineer received a ticket to investigate a potentially malicious file detected by a malware scanner that was trying to execute multiple commands. During the initial review, the engineer discovered that the file was created two days prior. Further analyses show that the file was downloaded from a known malicious domain after a successful phishing attempt on an asset owner. At which phase of the Cyber Kill Chain was this attack mitigated?
An organization's security team detected network spikes coming from the internal network. An investigation concluded that the spike in traffic was from intensive network scanning. How must the analyst collect the traffic to isolate the suspicious host?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
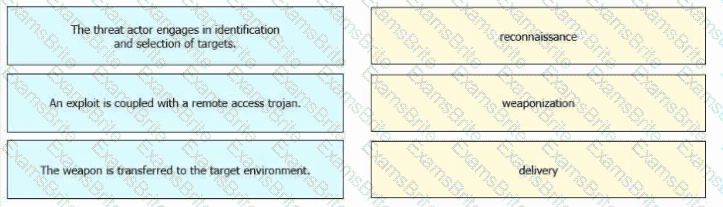
Refer to exhibit.
An engineer is Investigating an Intrusion and Is analyzing the pcap file. Which two key elements must an engineer consider? (Choose two.)
A compliance analyst receives a complaint from a customer regarding personal data being unlawfully retained despite a deletion request. The company is based in Europe and must comply with GDPR. The only data collected is the email address 0524l9i75@gmail.com. How should the compliance analyst act?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
What is a difference between rule-based and role-based access control mechanisms?
Refer to the exhibit.
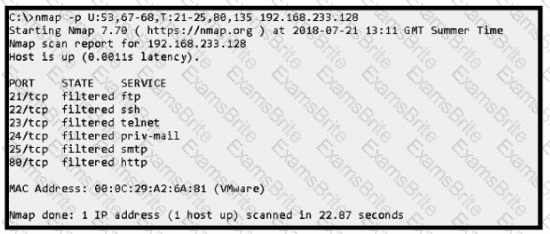
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?
Refer to the exhibit.
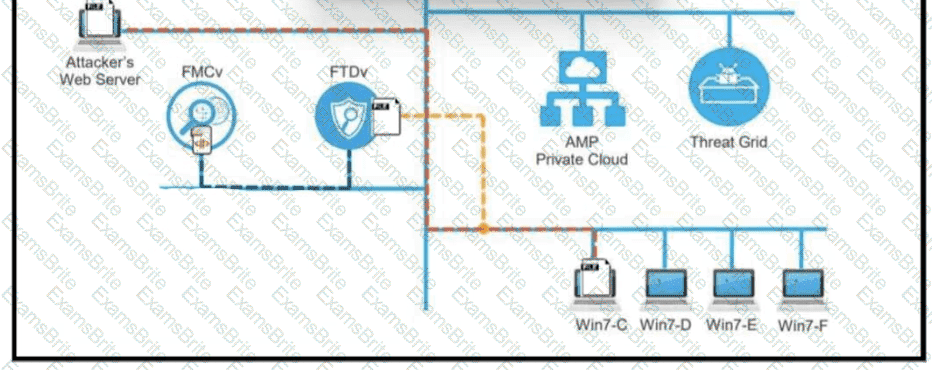
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded what would have occurred with stronger data visibility.
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
Refer to the exhibit.
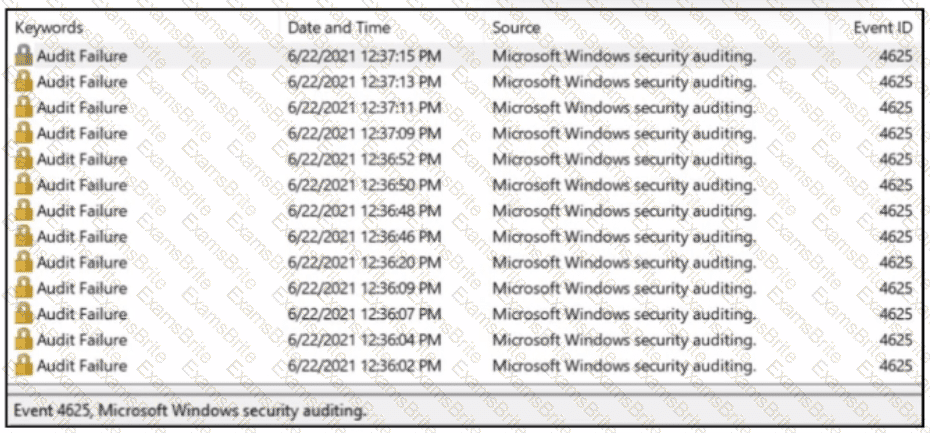
A SOC analyst received a message from SIEM about abnormal activity on the Windows server The analyst checked the Windows event log and saw numerous Audit Failures logs. What is occurring?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Refer to the exhibit.
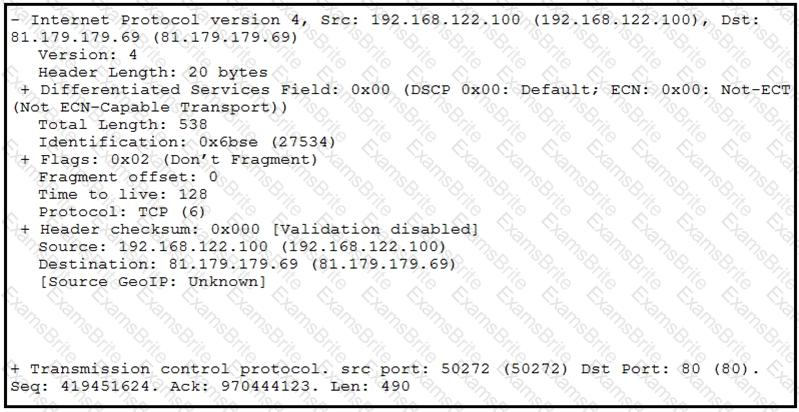
What should be interpreted from this packet capture?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
Why should an engineer use a full packet capture to investigate a security breach?
A security engineer must implement an Intrusion Prevention System (IPS) inside an organization’s DMZ. One of the requirements is the ability to block suspicious traffic in real time based on a triggered signature. The IPS will be connected behind the DMZ firewalls directly to the core switches. Which traffic integration method must be implemented to complete this project?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)
Which SOC metric represents the time to stop the incident from causing further damage to systems or data?
What is a difference between signature-based and behavior-based detection?
A security team receives a ticket to investigate suspicious emails sent to company employees from known malicious domains. Further analysis shows that a targeted phishing attempt was successfully blocked by the company’s email antivirus. At which step of the Cyber Kill Chain did the security team mitigate this attack?
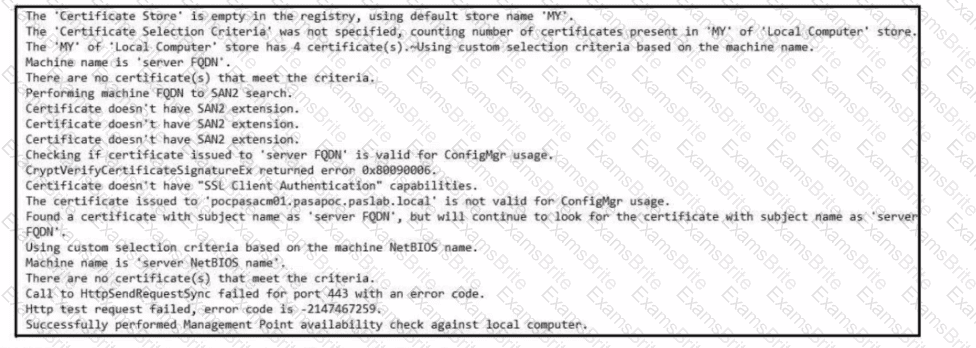
Refer to the exhibit. Which set of actions must an engineer perform to identify and fix this issue?
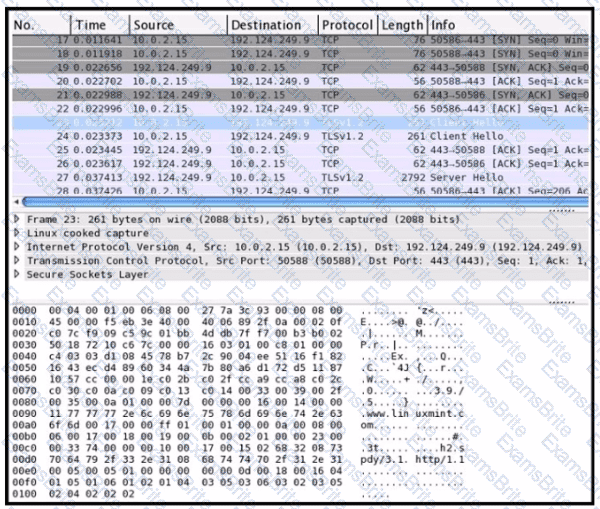
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.
A forensic investigator is analyzing a recent breach case. An external USB drive was discovered to be connected and transmitting the data outside of the organization, and the owner of the USB drive could not be identified. Video surveillance shows six people during a two-month period had close contact with the affected asset. How must this type of evidence be categorized?
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
Which management concept best describes developing, operating, maintaining, upgrading, and disposing of all resources?
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
Which event artifact is used to identify HTTP GET requests for a specific file?
Refer to exhibit.
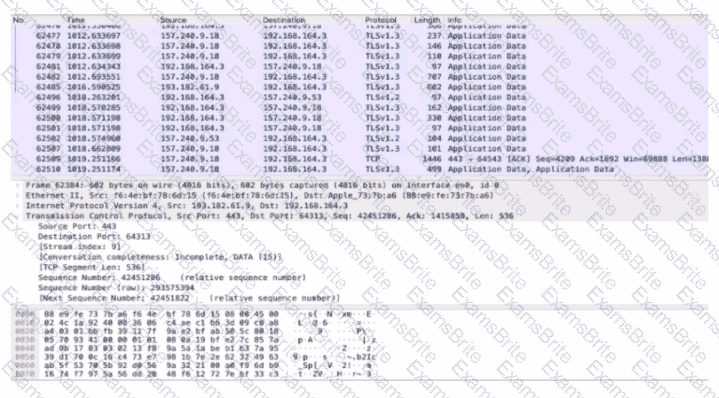
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Drag and drop the security concept on the left onto the example of that concept on the right.
Which two elements are used by the defense-in-depth strategy? (Choose two)
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?