
Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20)
Last Update Feb 28, 2026
Total Questions : 411
We are offering FREE 156-215.81 Checkpoint exam questions. All you do is to just go and sign up. Give your details, prepare 156-215.81 free exam questions and then go for complete pool of Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) test questions that will help you more.



What type of NAT is a one-to-one relationship where each host is translated to a unique address?
When defining group-based access in an LDAP environment with Identity Awareness, what is the BEST object type to represent an LDAP group in a Security Policy?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
A network administrator has informed you that they have identified a malicious host on the network, and instructed you to block it. Corporate policy dictates that firewall policy changes cannot be made at this time. What tool can you use to block this traffic?
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single core CPU. After installation, is the administrator required to perform any additional tasks?
Which of the completed statements is NOT true? The WebUI can be used to manage Operating System user accounts and
What is the most recommended installation method for Check Point appliances?
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
The Network Operations Center administrator needs access to Check Point Security devices mostly for troubleshooting purposes. You do not want to give her access to the expert mode, but she still should be able to run tcpdump. How can you achieve this requirement?
Gaia includes Check Point Upgrade Service Engine (CPUSE), which can directly receive updates for what components?
Access roles allow the firewall administrator to configure network access according to:
In R80 Management, apart from using SmartConsole, objects or rules can also be modified using:
What is the main difference between Threat Extraction and Threat Emulation?
A layer can support different combinations of blades What are the supported blades:
To view the policy installation history for each gateway, which tool would an administrator use?
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
In what way is Secure Network Distributor (SND) a relevant feature of the Security Gateway?
Using AD Query, the security gateway connections to the Active Directory Domain Controllers using what protocol?
In the Check Point Security Management Architecture, which component(s) can store logs?
Fill in the blank: The position of an implied rule is manipulated in the __________________ window.
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
Gaia has two default user accounts that cannot be deleted. What are those user accounts?
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer
From the Gaia web interface, which of the following operations CANNOT be performed on a Security Management Server?
AdminA and AdminB are both logged into SmartConsole. What does it mean if AdminB sees a lock icon on a rule? Choose the BEST answer.
In which deployment is the security management server and Security Gateway installed on the same appliance?
Is it possible to have more than one administrator connected to a Security Management Server at once?
Fill in the blanks: A Check Point software license consists of a__________ and _______.
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
When comparing Stateful Inspection and Packet Filtering, what is a benefit that Stateful Inspection offers over Packer Filtering?
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
Which two Identity Awareness commands are used to support identity sharing?
One of major features in R80.x SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
Which SmartConsole tab shows logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
What is the user ID of a user that have all the privileges of a root user?
The purpose of the Communication Initialization process is to establish a trust between the Security Management Server and the Check Point gateways. Which statement best describes this Secure Internal
Communication (SIC)?
Which of the following methods can be used to update the trusted log server regarding the policy and configuration changes performed on the Security Management Server?
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
Consider the Global Properties following settings:
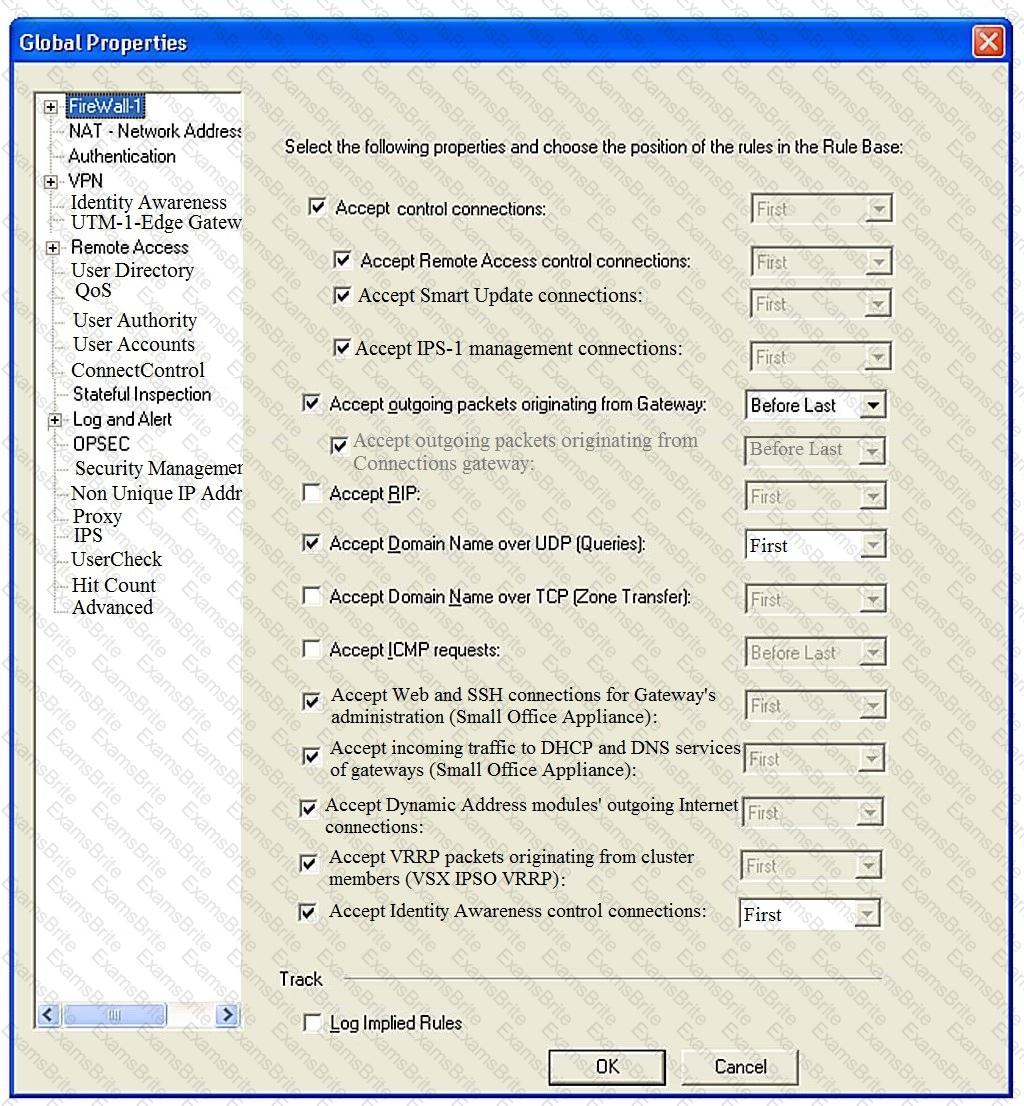
The selected option “Accept Domain Name over UDP (Queries)” means:
Which Security Blade needs to be enabled in order to sanitize and remove potentially malicious content from files, before those files enter the network?
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
An administrator wishes to use Application objects in a rule in their policy but there are no Application objects listed as options to add when clicking the"+" to add new items to the "Services & Applications" column of a rule. What should be done to fix this?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
Fill in the blank: Once a certificate is revoked from the Security GateWay by the Security Management Server, the certificate information is _______.
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ______ layer(s) of the TCP/IP model and up to and including the ______ layer.
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
In HTTPS Inspection policy, what actions are available in the "Actions" column of a rule?
In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT ________.
Which one of the following is the preferred licensing model? Select the BEST answer
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
The competition between stateful inspection and proxies was based on performance, protocol support, and security. Considering stateful Inspections and Proxies, which statement is correct?
Please choose correct command syntax to add an “emailserver1” host with IP address 10.50.23.90 using GAiA management CLI?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Which product correlates logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
Fill in the blank: When tunnel test packets no longer invoke a response, SmartView Monitor displays _____________ for the given VPN tunnel.
Which of the following is considered to be the more secure and preferred VPN authentication method?
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
Can multiple administrators connect to a Security Management Server at the same time?
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Which method below is NOT one of the ways to communicate using the Management API’s?
Tom has connected to the Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made?
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
When a SAM rule is required on Security Gateway to quickly block suspicious connections which are not restricted by the Security Policy, what actions does the administrator need to take?
Which backup utility captures the most information and tends to create the largest archives?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
What are the software components used by Autonomous Threat Prevention Profiles in R8I.20 and higher?
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
When a Security Gateway sends its logs to an IP address other than its own, which deployment option is installed?
R80.10 management server can manage gateways with which versions installed?