Cisco Certified Support Technician (CCST) Cybersecurity
Last Update Feb 28, 2026
Total Questions : 50
We are offering FREE 100-160 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 100-160 free exam questions and then go for complete pool of Cisco Certified Support Technician (CCST) Cybersecurity test questions that will help you more.



You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a successful login to a privileged account. What is the most appropriate next step?
Which step should be performed immediately after identifying a critical vulnerability affecting internet-facing systems?
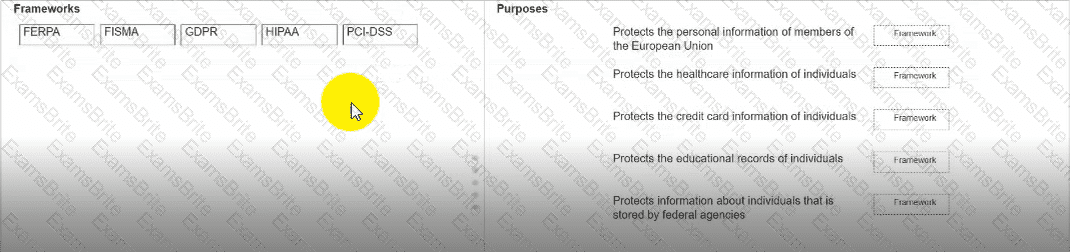
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.
Which two basic metrics should be taken into consideration when assigning a severity to a vulnerability during an assessment?(Choose 2.)
You need to design your company’s password policy to adhere to the National Institute of Standards and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST guidelines?
You are reviewing your company’s disaster recovery plan.
Which two daily data backup actions should the plan include?(Choose 2.)
What is the main purpose of a disaster recovery plan as compared to a business continuity plan?
Which security measure can prevent unauthorized devices from automatically connecting to a corporate network through unused switch ports?
Your supervisor suspects that someone is attempting to gain access to a Windows computer by guessing user account IDs and passwords. The supervisor asks you to use the Windows Event Viewer security logs to verify the attempts.
Which two audit policy events provide information to determine whether someone is using invalid credentials to attempt to log in to the computer?(Choose 2.)
Note: You will receive partial credit for each correct selection.
You are going to perform a penetration test on a company LAN. As part of your preparation, you access the company’s websites, view webpage source code, and run internet searches to uncover domain information. You also use social media to gather details about the company and its employees.
Which type of reconnaissance activities are you performing?
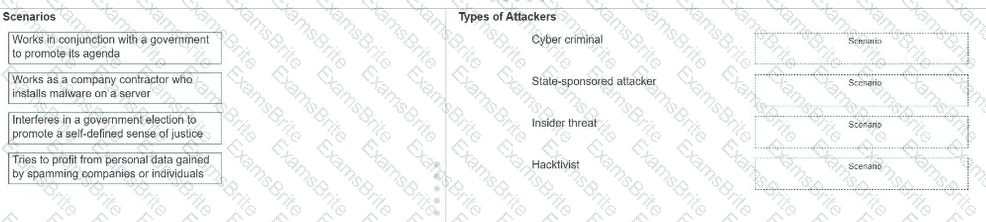
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.