Microsoft Security Compliance and Identity Fundamentals
Last Update Feb 14, 2026
Total Questions : 208
We are offering FREE SC-900 Microsoft exam questions. All you do is to just go and sign up. Give your details, prepare SC-900 free exam questions and then go for complete pool of Microsoft Security Compliance and Identity Fundamentals test questions that will help you more.



For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

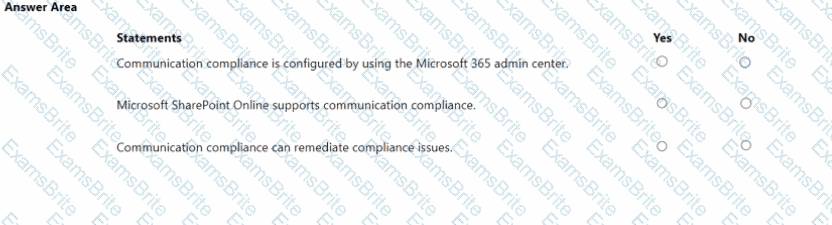
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
You need to create a data loss prevention (DLP) policy. What should you use?
Match the Microsoft Defender for Office 365 feature to the correct description.
To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

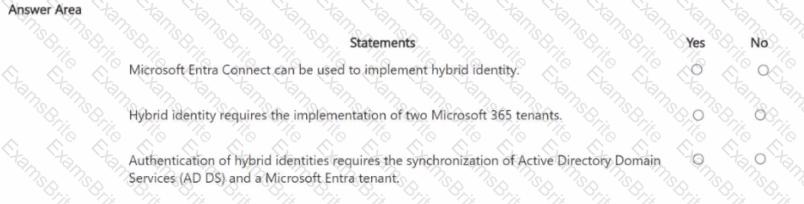
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What should you use in the Microsoft 365 security center to view security trends and track the protection status of identities?
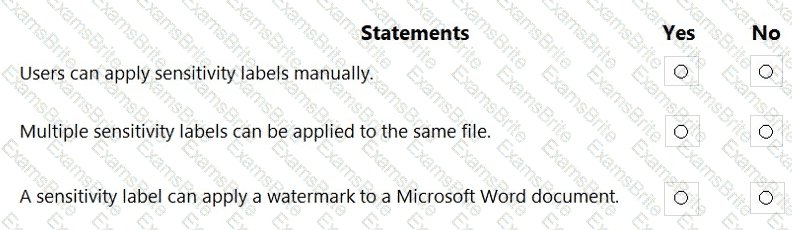
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

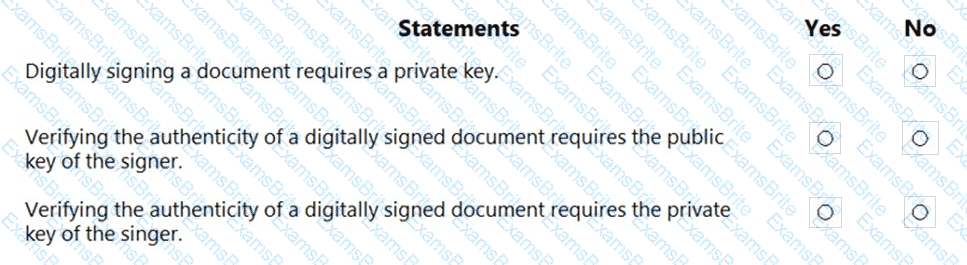
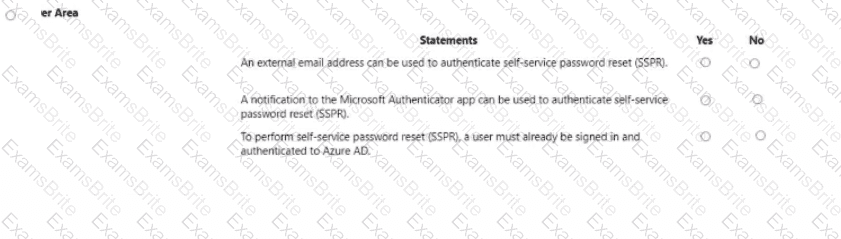
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

When you enable Azure AD Multi-Factor Authentication (MFA), how many factors are required for authentication?
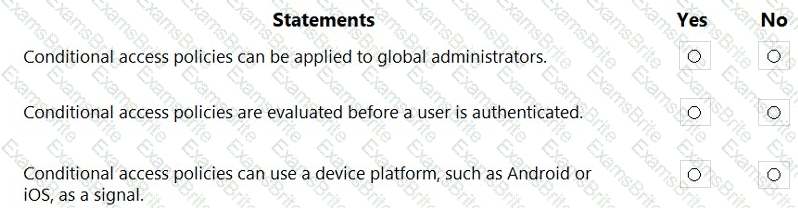
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What should you use in the Microsoft Defender portal to view security trends and track the protection status of identities?
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
Which two actions can you perform by using Azure Key Vault? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What do you use to provide real-time integration between Azure Sentinel and another security source?
Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
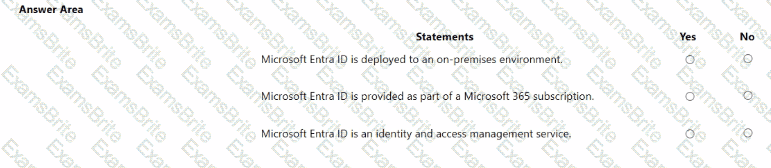
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)?
For each of the following statement, select Yes if the statement is true Otherwise, select No.
NOTE: Each connect selection a worth one point.
Which Microsoft Purview data classification type supports the use of regular expressions?
You plan to move resources to the cloud.
You are evaluating the use of Infrastructure as a service (laaS),
Platform as a service (PaaS), and Software as a service (SaaS) cloud models.
You plan to manage only the data, user accounts, and user devices for a cloud-based app.
Which cloud model will you use?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE; Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware?
Which compliance feature should you use to identify documents that are employee resumes?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
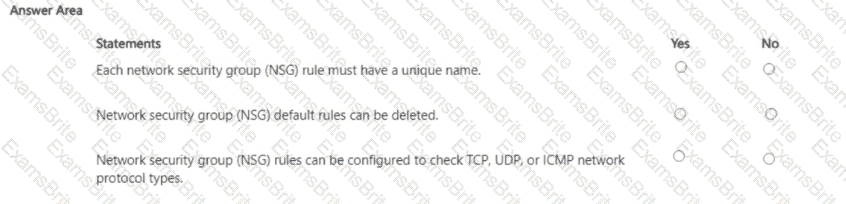
Which two Azure resources can a network security group (NSG) be associated with? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
What are customers responsible for when evaluating security in a software as a service (SaaS) cloud services model?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.