
Microsoft Security Operations Analyst
Last Update Feb 2, 2026
Total Questions : 366
We are offering FREE SC-200 Microsoft exam questions. All you do is to just go and sign up. Give your details, prepare SC-200 free exam questions and then go for complete pool of Microsoft Security Operations Analyst test questions that will help you more.



NO: 7
You provision a Linux virtual machine in a new Azure subscription.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to implement the Defender for Cloud requirements.
What should you configure for Server2?
You need to implement the Defender for Cloud requirements.
Which subscription-level role should you assign to Group1?
You need to ensure that the Group1 members can meet the Microsoft Sentinel requirements.
Which role should you assign to Group1?
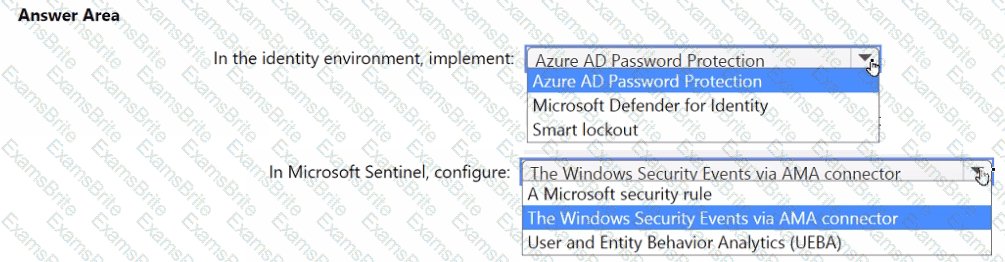
You need to monitor the password resets. The solution must meet the Microsoft Sentinel requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that the processing of incidents generated by rulequery1 meets the Microsoft Sentinel requirements.
What should you create first?
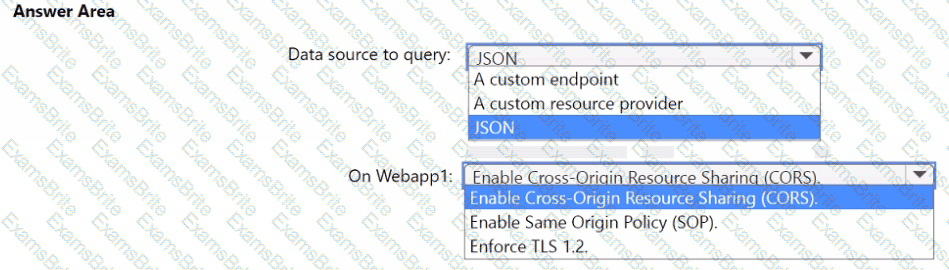
You need to implement the query for Workbook1 and Webapp1. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
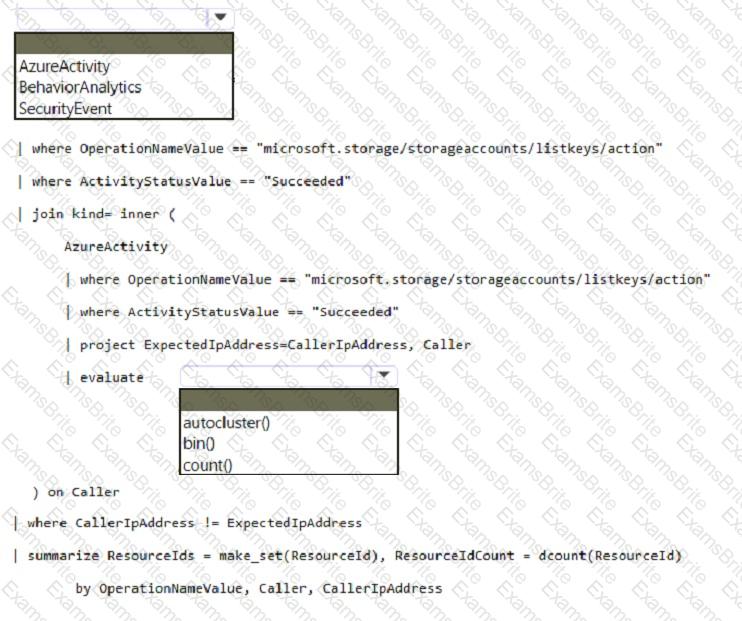
You have a Microsoft Sentinel workspace named sws1.
You need to create a hunting query to identify users that list storage keys of multiple Azure Storage accounts. The solution must exclude users that list storage keys for a single storage account.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure DevOps organization that uses Microsoft Defender for DevOps. The organization contains an Azure DevOps repository named Repo1 and an Azure Pipelines pipeline named Pipeline1. Pipeline1 is used to build and deploy code stored in Repo1.
You need to ensure that when Pipeline1 runs, Microsoft Defender for Cloud can perform secret scanning of the code in Repo1.
What should you install in the organization, and what should you add to the YAML file of Pipeline"!? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

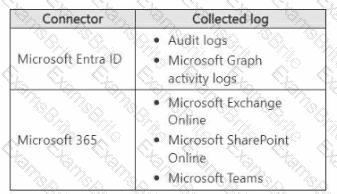
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR.
You have a Microsoft Sentinel workspace.
Microsoft Sentinel connectors are configured as shown in the following table.
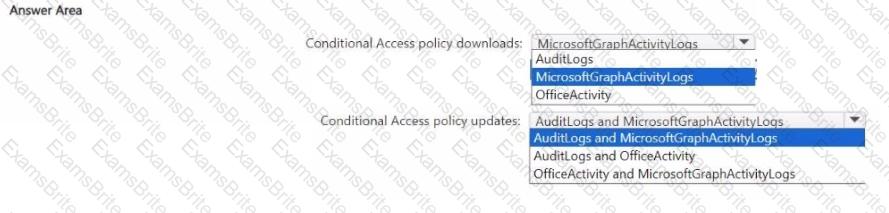
You use Microsoft Sentinel to investigate suspicious Microsoft Graph API activity related to Conditional Access policies. You need to search for the following activities:
• Downloads of the Conditional Access policies by using PowerShell
• Updates to the Conditional Access policies by using the Microsoft Entra admin center
Which tables should you query for each activity? lo answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You use Azure Defender.
You have an Azure Storage account that contains sensitive information.
You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a resource group named RG1. RG1 contains a Microsoft Sentinel workspace. The subscription is linked to a Microsoft Entra tenant that contains a user named User1.
You need to ensure that User1 can deploy and customize Microsoft Sentine1 workbook templates. The solution must follow the principle of least privilege.
Which role should you assign to User1 for RG1?
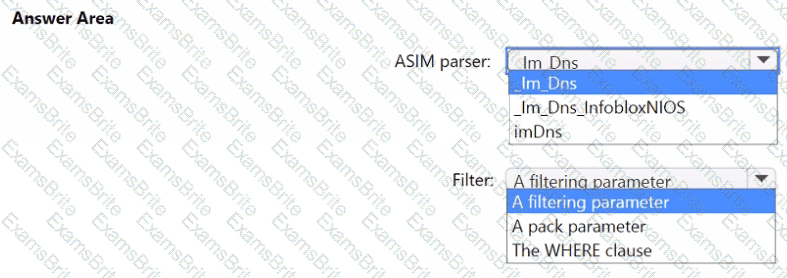
You need to implement the ASIM query for DNS requests. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
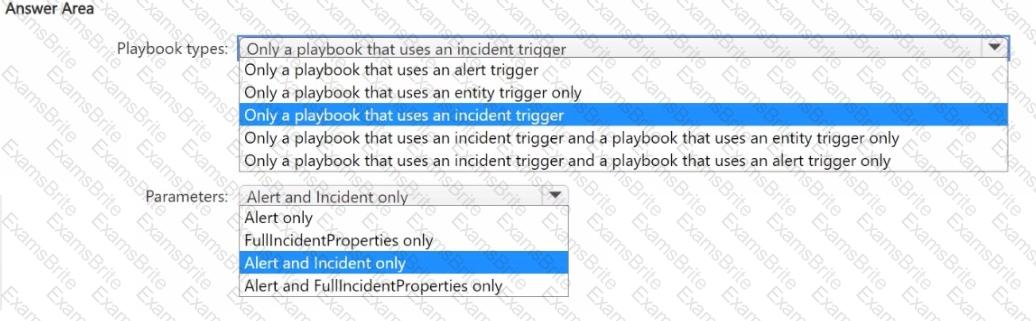
You have a Microsoft Sentinel workspace.
You need to create playbooks that meet the following requirements:
• Use an automation rule to trigger actions on an entity.
• Call the Entities - Get Hosts action.
Which types of playbooks should you use, and which parameters should you specify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft 365 Defender A remediation action for an automated investigation quarantines a file across multiple devices. You need to mark the file as safe and remove the file from quarantine on the devices. What should you use m the Microsoft 365 Defender portal?
You have a Microsoft 365 B5 subscription that contains a user named User1. The subscription uses Microsoft 365 Copilot for Security. Copilot for Security uses the Sentinel plugin. User1 is assigned the Copilot Contributor role.
During an investigation, User1 submits a prompt and receives a notification that Copilot for Security cannot respond to requests because the security compute unit (SCU) usage is nearing the provisioned capacity limit.
You need to ensure that User1 can use Copilot for Security to generate a successful response.
What should User1 do?
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have an Amazon Web Services (AWS) account that contains an Amazon Elastic Compute Cloud (EC2) instance named EC2-1.
You need to onboard EC2-1 to Defender for Cloud.
What should you install on EC2-1?
You have a Microsoft 365 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1.
The timeline of Device1 includes three files named File1.ps1, File2.exe, and File3.dll.
You need to submit files for deep analysis in Microsoft Defender XDR.
Which files can you submit?
You have the resources shown in the following table.
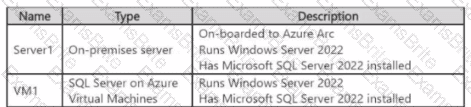
You have an Azure subscription that uses Mictosoft Defender for Cloud.
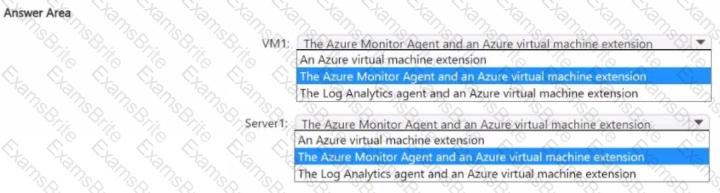
You need to use Defender for Cloud to protect VM1 and Server1. The solution must meet the following requirements:
• Support Advanced Threat Protection and vulnerability assessment
• Register each SQL Server 2022 instance as a SQL virtual machine.
• Minimize implementation and administrative effort
What should you deploy to each server? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You create a hunting query in Azure Sentinel.
You need to receive a notification in the Azure portal as soon as the hunting query detects a match on the query. The solution must minimize effort.
What should you use?
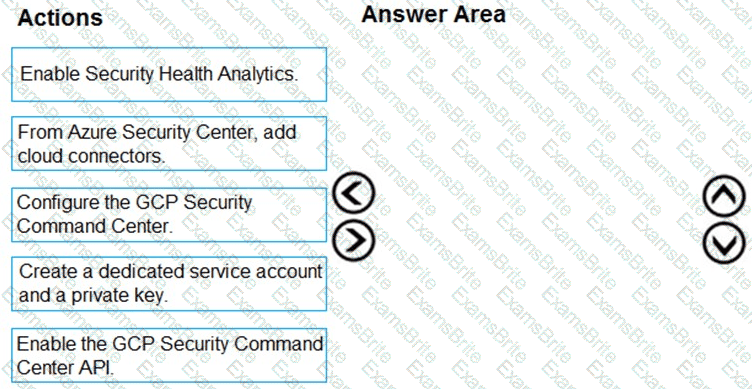
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
You create an Azure subscription.
You enable Azure Defender for the subscription.
You need to use Azure Defender to protect on-premises computers.
What should you do on the on-premises computers?
You have an on-premises network.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity.
From the Microsoft Defender portal, you investigate an incident on a device named Device1 of a user named User1. The incident contains the following Defender for Identity alert.
Suspected identity theft (pass-the-ticket) (external ID 2018)
You need to contain the incident without affecting users and devices. The solution must minimize administrative effort.
What should you do?
You need to ensure that the configuration of HuntingQuery1 meets the Microsoft Sentinel requirements.
What should you do?
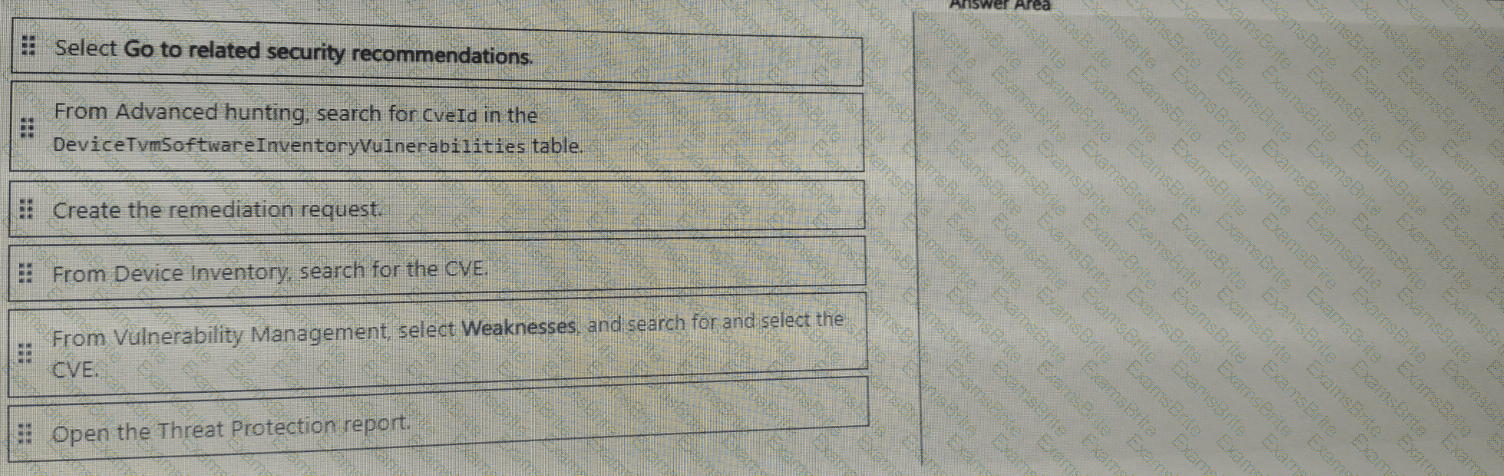
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use the Microsoft Defender portal to request remediation from the team responsible for the affected systems if there is
a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription that contains a device named Device1. From the Microsoft Defender portal, you discover that an alert was triggered for Device1. From the Device inventory page, you isolate Device1. You need to collect a list of installed programs on Device1. What should you do?
You have an existing Azure logic app that is used to block Azure Active Directory (Azure AD) users. The logic app is triggered manually.
You deploy Azure Sentinel.
You need to use the existing logic app as a playbook in Azure Sentinel. What should you do first?
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You have a virtual machine that runs Windows 10 and has the Log Analytics agent installed.
You need to simulate an attack on the virtual machine that will generate an alert.
What should you do first?
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint
You need to identify any devices that triggered a malware alert and collect evidence related to the alert. The solution must ensure that you can use the results to initiate device isolation for the affected devices.
What should you use in the Microsoft 365 Defender portal?
You implement Safe Attachments policies in Microsoft Defender for Office 365.
Users report that email messages containing attachments take longer than expected to be received.
You need to reduce the amount of time it takes to deliver messages that contain attachments without compromising security. The attachments must be scanned for malware, and any messages that contain malware must be blocked.
What should you configure in the Safe Attachments policies?
Your on-premises network contains two Active Directory Domain Services (AD DS) domains named contoso.com and fabrikam.com. Contoso.com contains a group named Group1. Fabrikam.com contains a group named Group2.
You have a Microsoft Sentinel workspace named WS1 that contains a scheduled query rule named Rule1. Rule1 generates alerts in response to anomalous AD DS security events. Each alert creates an incident.
You need to implement an incident triage solution that meets the following requirements:
· Security incidents from contoso.com must be assigned to Group1.
· Security incidents from fabrikam.com must be assigned to Group2.
· Administrative effort must be minimized.
What should you include in the solution?
You have a Microsoft 365 subscription.
You have 1,000 Windows devices that have a third-party antivirus product installed and Microsoft Defender Antivirus in passive mode. You need to ensure that the devices are protected from malicious artifacts that were undetected by the third-party antivirus product. Solution: You configure Controlled folder access. Does this meet the goal?
You have an Azure subscription that contains the users shown in the following table.
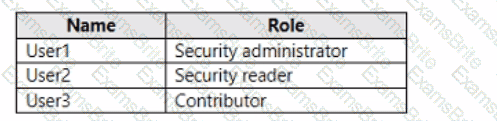
You need to delegate the following tasks:
• Enable Microsoft Defender for Servers on virtual machines.
• Review security recommendations and enable server vulnerability scans.
The solution must use the principle of least privilege.
Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You receive an alert from Azure Defender for Key Vault.
You discover that the alert is generated from multiple suspicious IP addresses.
You need to reduce the potential of Key Vault secrets being leaked while you investigate the issue. The solution must be implemented as soon as possible and must minimize the impact on legitimate users.
What should you do first?
You have a Microsoft Sentinel workspace named SW1.
You need to identify which anomaly rules are enabled in SW1.
What should you review in Microsoft Sentine1?
You have an Azure subscription that uses Microsoft Sentinel and contains 100 Linux virtual machines.
You need to monitor the virtual machines by using Microsoft Sentinel. The solution must meet the fallowing requirements:
• Minimize administrative effort
• Minimize the parsing required to read log data
What should you configure?
You need to implement the scheduled rule for incident generation based on rulequery1.
What should you configure first?
You need to configure event monitoring for Server1. The solution must meet the Microsoft Sentinel requirements. What should you create first?
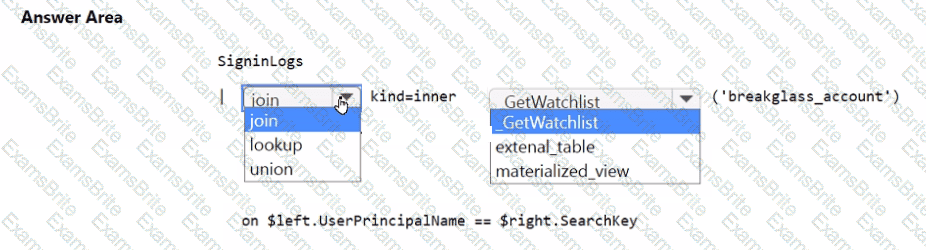
You need to implement the Microsoft Sentinel NRT rule for monitoring the designated break glass account. The solution must meet the Microsoft Sentinel requirements.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the technical requirements for the Azure virtual machines. What should you include in the recommendation?
You need to remediate active attacks to meet the technical requirements.
What should you include in the solution?
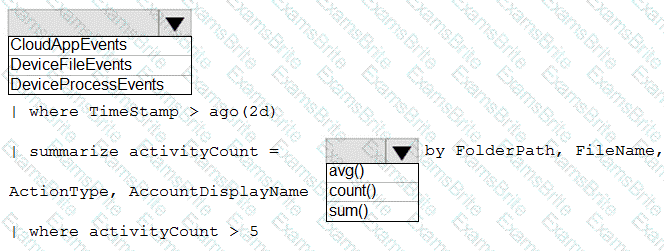
You need to create an advanced hunting query to investigate the executive team issue.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
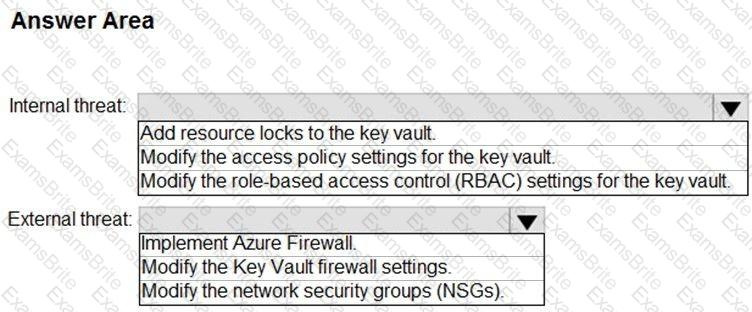
You need to recommend remediation actions for the Azure Defender alerts for Fabrikam.
What should you recommend for each threat? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
The issue for which team can be resolved by using Microsoft Defender for Office 365?
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
You need to complete the query for failed sign-ins to meet the technical requirements.
Where can you find the column name to complete the where clause?
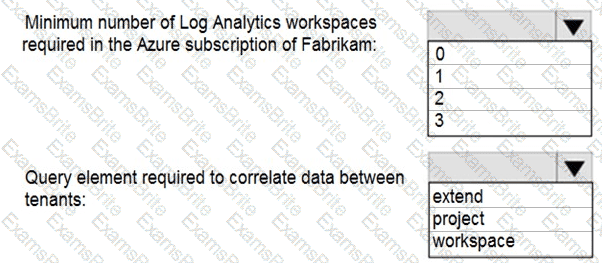
You need to implement Azure Sentinel queries for Contoso and Fabrikam to meet the technical requirements.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to modify the anomaly detection policy settings to meet the Microsoft Defender for Cloud Apps requirements and resolve the reported problem.
Which policy should you modify?
You need to restrict cloud apps running on CUENT1 to meet the Microsoft Defender for Endpoint requirements. Which two configurations should you modify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
You need to modify the anomaly detection policy settings to meet the Cloud App Security requirements. Which policy should you modify?
Which rule setting should you configure to meet the Microsoft Sentinel requirements?
You need to configure the Microsoft Sentinel integration to meet the Microsoft Sentinel requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You need to create the test rule to meet the Azure Sentinel requirements. What should you do when you create the rule?
You need to add notes to the events to meet the Azure Sentinel requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
You need to assign a role-based access control (RBAC) role to admin1 to meet the Azure Sentinel requirements and the business requirements.
Which role should you assign?
You need to restrict cloud apps running on CLIENT1 to meet the Microsoft Defender for Endpoint requirements.
Which two configurations should you modify? Each correct answer present part of the solution.
NOTE: Each correct selection is worth one point.