CompTIA PenTest+ Certification Exam
Last Update Apr 25, 2024
Total Questions : 396
We are offering FREE PT0-002 CompTIA exam questions. All you do is to just go and sign up. Give your details, prepare PT0-002 free exam questions and then go for complete pool of CompTIA PenTest+ Certification Exam test questions that will help you more.



A penetration tester is explaining the MITRE ATT&CK framework to a company’s chief legal counsel.
Which of the following would the tester MOST likely describe as a benefit of the framework?
A security analyst is conducting an unknown environment test from 192.168.3.3. The analyst wants to limit observation of the penetration tester's activities and lower the probability of detection by intrusion protection and detection systems. Which of the following Nmap commands should the analyst use to achieve this objective?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
A penetration tester is attempting to discover live hosts on a subnet quickly.
Which of the following commands will perform a ping scan?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
A penetration tester has established an on-path attack position and must now specially craft a DNS query response to be sent back to a target host. Which of the following utilities would BEST support this objective?
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
A penetration tester was able to gain access successfully to a Windows workstation on a mobile client’s laptop. Which of the following can be used to ensure the tester is able to maintain access to the system?
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Which of the following approaches would BEST support the objective?
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
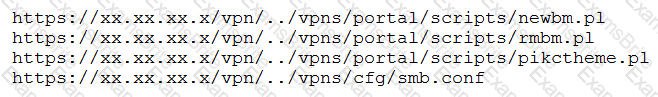
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A penetration tester is testing input validation on a search form that was discovered on a website. Which of the following characters is the BEST option to test the website for vulnerabilities?
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
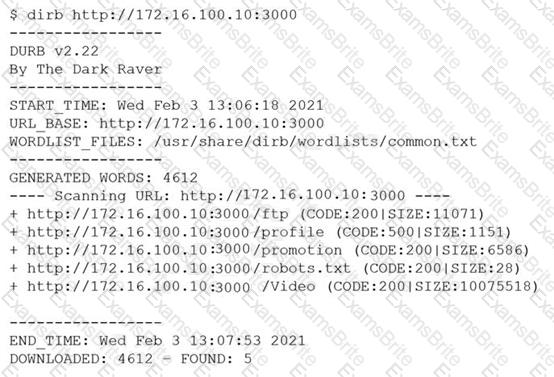
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile , a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
A penetration tester conducts an Nmap scan against a target and receives the following results:

Which of the following should the tester use to redirect the scanning tools using TCP port 1080 on the target?
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
A penetration tester has prepared the following phishing email for an upcoming penetration test:

Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
A CentOS computer was exploited during a penetration test. During initial reconnaissance, the penetration tester discovered that port 25 was open on an internal
Sendmail server. To remain stealthy, the tester ran the following command from the attack machine:

Which of the following would be the BEST command to use for further progress into the targeted network?
A company requires that all hypervisors have the latest available patches installed. Which of the following would BEST explain the reason why this policy is in place?
A penetration tester discovered that a client uses cloud mail as the company's email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue. Which of the following BEST describes this attack?
A penetration tester opened a reverse shell on a Linux web server and successfully escalated privileges to root. During the engagement, the tester noticed that another user logged in frequently as root to perform work tasks. To avoid disrupting this user’s work, which of the following is the BEST option for the penetration tester to maintain root-level persistence on this server during the test?
After running the enum4linux.pl command, a penetration tester received the following output:
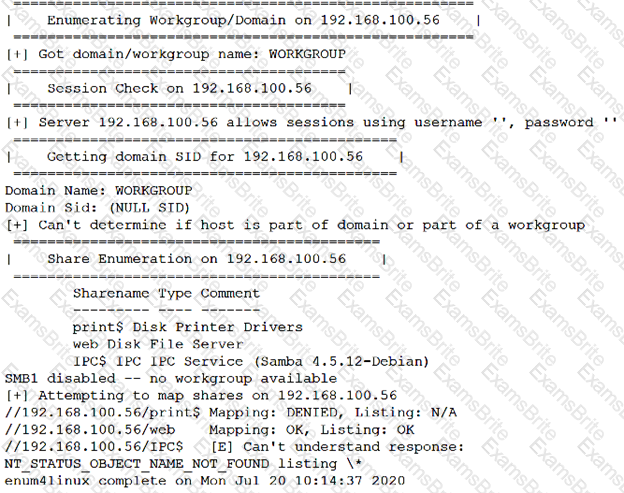
Which of the following commands should the penetration tester run NEXT?
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
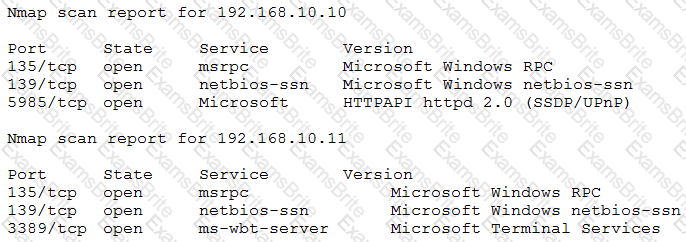
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
A penetration tester has been hired to examine a website for flaws. During one of the time windows for testing, a network engineer notices a flood of GET requests to the web server, reducing the website’s response time by 80%. The network engineer contacts the penetration tester to determine if these GET requests are part of the test. Which of the following BEST describes the purpose of checking with the penetration tester?
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code:
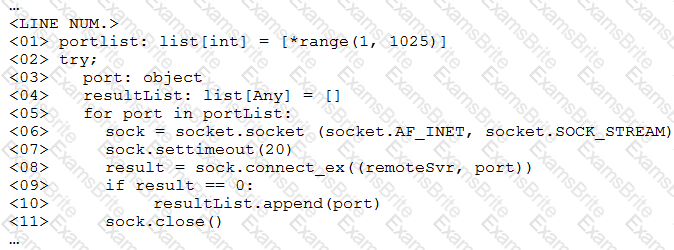
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A penetration tester ran the following command on a staging server:
python –m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
The results of an Nmap scan are as follows:
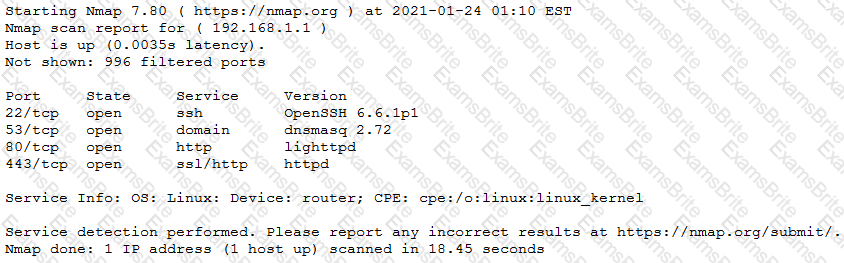
Which of the following would be the BEST conclusion about this device?
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
A penetration tester opened a shell on a laptop at a client's office but is unable to pivot because of restrictive ACLs on the wireless subnet. The tester is also aware that all laptop users have a hard-wired connection available at their desks. Which of the following is the BEST method available to pivot and gain additional access to the network?
The provision that defines the level of responsibility between the penetration tester and the client for preventing unauthorized disclosure is found in the:
During an internal penetration test against a company, a penetration tester was able to navigate to another part of the network and locate a folder containing customer information such as addresses, phone numbers, and credit card numbers. To be PCI compliant, which of the following should the company have implemented to BEST protect this data?
A penetration tester initiated the transfer of a large data set to verify a proof-of-concept attack as permitted by the ROE. The tester noticed the client's data included PII, which is out of scope, and immediately stopped the transfer. Which of the following MOST likely explains the penetration tester's decision?
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP. Which of the following steps should the tester take NEXT?
A penetration tester gains access to a system and is able to migrate to a user process:
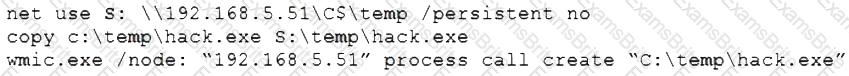
Given the output above, which of the following actions is the penetration tester performing? (Choose two.)
Which of the following can be used to store alphanumeric data that can be fed into scripts or programs as input to penetration-testing tools?
Which of the following tools would be BEST suited to perform a manual web application security assessment? (Choose two.)
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A Chief Information Security Officer wants a penetration tester to evaluate the security awareness level of the company’s employees.
Which of the following tools can help the tester achieve this goal?
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
Which of the following tools should a penetration tester use to crawl a website and build a wordlist using the data recovered to crack the password on the website?
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
Penetration tester who was exclusively authorized to conduct a physical assessment noticed there were no cameras pointed at the dumpster for company. The penetration tester returned at night and collected garbage that contained receipts for recently purchased networking :. The models of equipment purchased are vulnerable to attack. Which of the following is the most likely next step for the penetration?
A penetration tester captured the following traffic during a web-application test:

Which of the following methods should the tester use to visualize the authorization information being transmitted?
When accessing the URL http://192.168.0-1/validate/user.php, a penetration tester obtained the following output:
..d index: eid in /apache/www/validate/user.php line 12
..d index: uid in /apache/www/validate/user.php line 13
..d index: pw in /apache/www/validate/user.php line 14
..d index: acl in /apache/www/validate/user.php line 15
A penetration tester attempted a DNS poisoning attack. After the attempt, no traffic was seen from the target machine. Which of the following MOST likely caused the attack to fail?
Which of the following is the most secure method for sending the penetration test report to the client?
Which of the following types of assessments MOST likely focuses on vulnerabilities with the objective to access specific data?
During a penetration test, the domain names, IP ranges, hosts, and applications are defined in the:
During an assessment, a penetration tester was able to access the organization's wireless network from outside of the building using a laptop running Aircrack-ng. Which of the following should be recommended to the client to remediate this issue?
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
A penetration tester needs to upload the results of a port scan to a centralized security tool. Which of the following commands would allow the tester to save the results in an interchangeable format?
A penetration tester writes the following script:
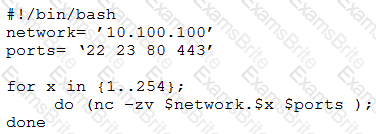
Which of the following is the tester performing?
A penetration tester was hired to perform a physical security assessment of an organization's office. After monitoring the environment for a few hours, the penetration tester notices that some employees go to lunch in a restaurant nearby and leave their belongings unattended on the table while getting food. Which of the following techniques would MOST likely be used to get legitimate access into the organization's building without raising too many alerts?
A penetration tester learned that when users request password resets, help desk analysts change users' passwords to 123change. The penetration tester decides to brute force an internet-facing webmail to check which users are still using the temporary password. The tester configures the brute-force tool to test usernames found on a text file and the... Which of the following techniques is the penetration tester using?
A security analyst needs to perform an on-path attack on BLE smart devices. Which of the following tools would be BEST suited to accomplish this task?
A penetration tester examines a web-based shopping catalog and discovers the following URL when viewing a product in the catalog:
http://company.com/catalog.asp?productid=22
The penetration tester alters the URL in the browser to the following and notices a delay when the page refreshes:
http://company.com/catalog.asp?productid=22;WAITFOR DELAY '00:00:05'
Which of the following should the penetration tester attempt NEXT?
A penetration tester is conducting an Nmap scan and wants to scan for ports without establishing a connection. The tester also wants to find version data information for services running on Projects. Which of the following Nmap commands should the tester use?
ion tester is attempting to get more people from a target company to download and run an executable. Which of the following would be the.. :tive way for the tester to achieve this objective?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?
Penetration tester has discovered an unknown Linux 64-bit executable binary. Which of the following tools would be BEST to use to analyze this issue?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
A potential reason for communicating with the client point of contact during a penetration test is to provide resolution if a testing component crashes a system or service and leaves them unavailable for both legitimate users and further testing. Which of the following best describes this concept?
A penetration tester is reviewing the logs of a proxy server and discovers the following URLs:
https://test.comptia.com/profile.php?userid=1546
https://test.cpmptia.com/profile.php?userid=5482
https://test.comptia.com/profile.php?userid=3618
Which of the following types of vulnerabilities should be remediated?
A penetration tester is conducting an on-path link layer attack in order to take control of a key fob that controls an electric vehicle. Which of the following wireless attacks would allow a penetration tester to achieve a successful attack?
Which of the following tools can a penetration tester use to brute force a user password over SSH using multiple threads?
Which of the following elements of a penetration testing report aims to provide a normalized and standardized representation of discovered vulnerabilities and the overall threat they present to an affected system or network?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
During a security assessment, a penetration tester decides to implement a simple TCP port scanner to check the open ports from 1000 to 2000. Which of the following Python scripts would achieve this task?
A penetration tester is performing an assessment for an application that is used by large organizations operating in the heavily regulated financial services industry. The penetration tester observes that the default Admin User account is enabled and appears to be used several times a day by unfamiliar IP addresses. Which of the following is the most appropriate way to remediate this issue?
A penetration tester observes an application enforcing strict access controls. Which of the following would allow the tester to bypass these controls and successfully access the organization's sensitive files?
Within a Python script, a line that states print (var) outputs the following:
[{'1' : 'CentOS', '2' : 'Ubuntu'), {'1' : 'Windows 10', '2' : 'Windows Server 2016'}]
Which of the following objects or data structures is var ?
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
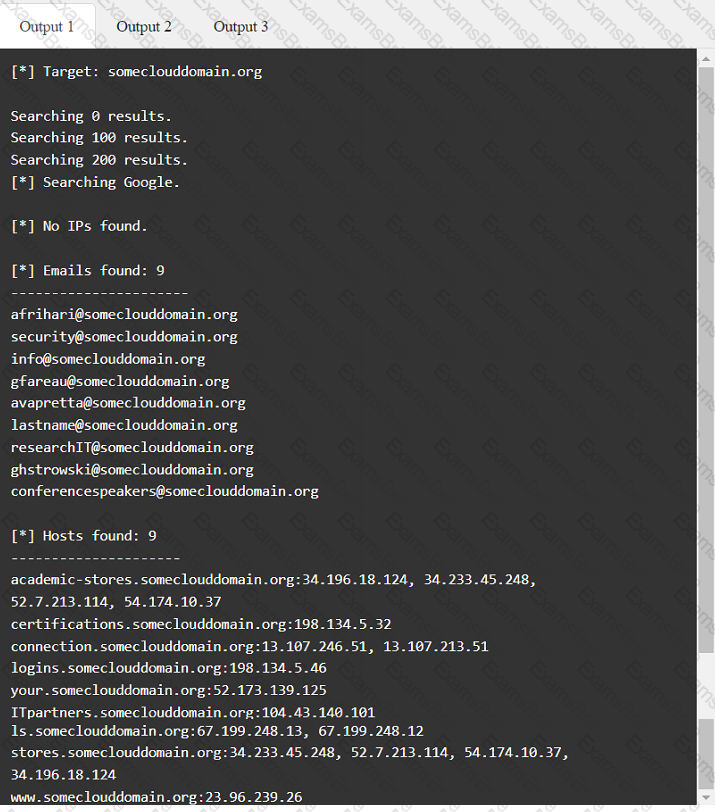
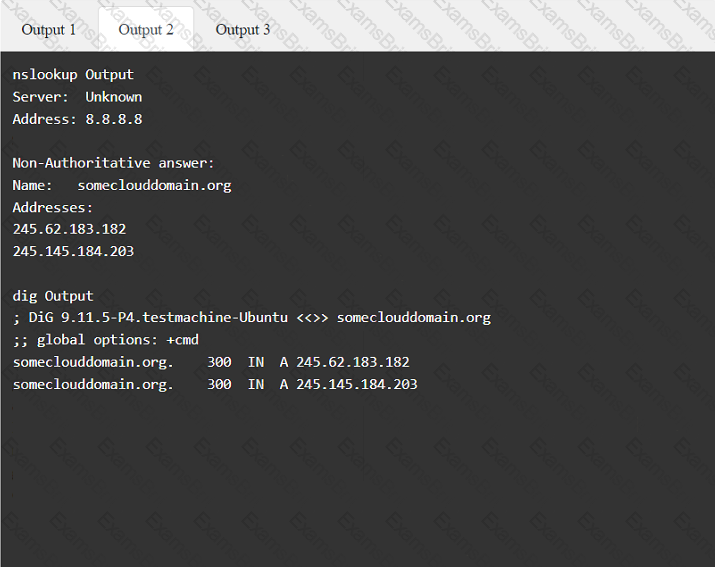
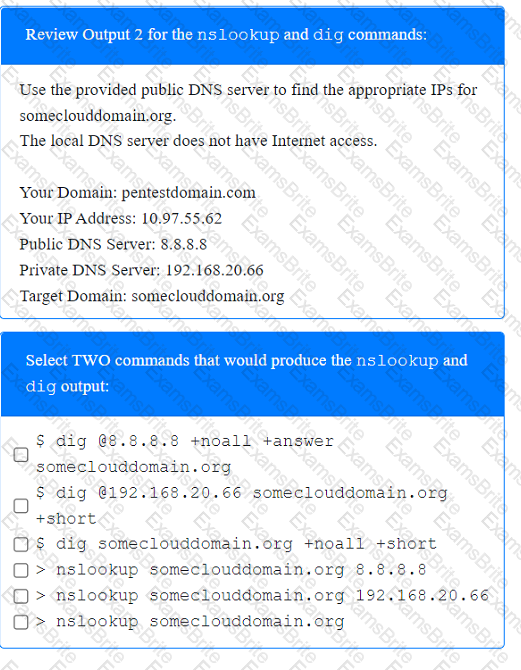
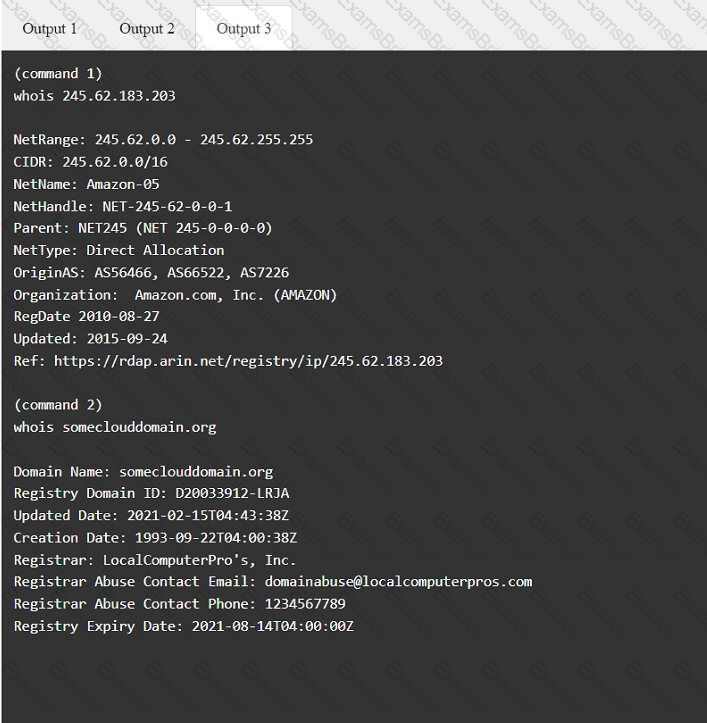
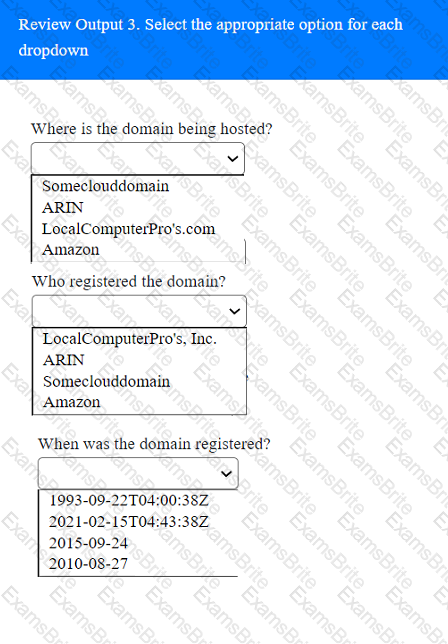
During a vulnerability scan a penetration tester enters the following Nmap command against all of the non-Windows clients:
nmap -sX -T4 -p 21-25, 67, 80, 139, 8080 192.168.11.191
The penetration tester reviews the packet capture in Wireshark and notices that the target responds with an RST packet flag set for all of the targeted ports. Which of the following does this information most likely indicate?
Which of the following tools would be best to use to conceal data in various kinds of image files?
Penetration on an assessment for a client organization, a penetration tester notices numerous outdated software package versions were installed ...s-critical servers. Which of the following would best mitigate this issue?
A penetration tester was hired to test Wi-Fi equipment. Which of the following tools should be used to gather information about the wireless network?
A penetration tester is conducting an assessment for an e-commerce company and successfully copies the user database to the local machine. After a closer review, the penetration tester identifies several high-profile celebrities who have active user accounts with the online service. Which of the following is the most appropriate next step?
Which of the following assessment methods is the most likely to cause harm to an ICS environment?
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?
Which of the following best explains why communication is a vital phase of a penetration test?
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
During a security assessment of a web application, a penetration tester was able to generate the following application response:
Unclosed quotation mark after the character string Incorrect syntax near ".
Which of the following is the most probable finding?
During an assessment, a penetration tester discovers the following code sample in a web application:
"(&(userid=*)(userid=*))(I(userid=*)(userPwd=(SHAl}a9993e364706816aba3e25717850c26c9cd0d89d==))
Which of the following injections is being performed?
A penetration tester requested, without express authorization, that a CVE number be assigned for a new vulnerability found on an internal client application. Which of the following did the penetration tester most likely breach?
Which of the following tools would be the best to use to intercept an HTTP response at an API, change its content, and forward it back to the origin mobile device?
A penetration tester is conducting a test after hours and notices a critical system was taken down. Which of the following contacts should be notified first?
Which of the following members of a client organization are most likely authorized to provide a signed authorization letter prior to the start date of a penetration test?
After performing a web penetration test, a security consultant is ranking the findings by criticality. Which of the following standards or methodologies would be best for the consultant to use for reference?
A penetration tester requested, without express authorization, that a CVE number be assigned for a new vulnerability found on an internal client application. Which of the following did the penetration tester most likely breach?
The results of an Nmap scan are as follows:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-24 01:10 EST
Nmap scan report for ( 10.2.1.22 )
Host is up (0.0102s latency).
Not shown: 998 filtered ports
Port State Service
80/tcp open http
|_http-title: 80F 22% RH 1009.1MB (text/html)
|_http-slowloris-check:
| VULNERABLE:
| Slowloris DoS Attack
| <..>
Device type: bridge|general purpose
Running (JUST GUESSING) : QEMU (95%)
OS CPE: cpe:/a:qemu:qemu
No exact OS matches found for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 107.45 seconds
Which of the following device types will MOST likely have a similar response? (Choose two.)
A penetration tester discovers passwords in a publicly available data breach during the reconnaissance phase of the penetration test. Which of the following is the best action for the tester to take?
During an engagement, a penetration tester was able to upload to a server a PHP file with the following content:
Which of the following commands should the penetration tester run to successfully achieve RCE?
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
A penetration tester managed to exploit a vulnerability using the following payload:
IF (1=1) WAIT FOR DELAY '0:0:15'
Which of the following actions would best mitigate this type ol attack?
A penetration tester is testing a company's public API and discovers that specific input allows the execution of arbitrary commands on the base operating system. Which of the following actions should the penetration tester take next?
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:
[ATTEMPT] target 192.168.1.112 - login "root" - pass "abcde"
[ATTEMPT] target 192.168.1.112 - login "root" - pass "edcfg"
[ATTEMPT] target 192.168.1.112 - login "root" - pass "qazsw"
[ATTEMPT] target 192.168.1.112 - login "root" – pass “tyuio”
Which of the following is the penetration tester conducting?
Which of the following tools would help a penetration tester locate a file that was uploaded to a content management system?
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity. Which of the following is the MOST important action to take before starting this type of assessment?
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?