
Palo Alto Networks System Engineer Professional - Strata
Last Update Feb 28, 2026
Total Questions : 137
We are offering FREE PSE-Strata Paloalto Networks exam questions. All you do is to just go and sign up. Give your details, prepare PSE-Strata free exam questions and then go for complete pool of Palo Alto Networks System Engineer Professional - Strata test questions that will help you more.



What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
in which step of the Palo Alto Networks Five-Step Zero Trust Methodology would an organization's critical data, applications, assets, and services (DAAS) be identified?
Which three signature-based Threat Prevention features of the firewall are informed by intelligence from the Threat Intelligence Cloud? (Choose three.)
Which two features can be enabled to support asymmetric routing with redundancy on a Palo
Alto networks next-generation firewall (NGFW)? (Choose two.)
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy.
Which two features must be enabled to meet the customer’s requirements? (Choose two.)
WildFire can discover zero-day malware in which three types of traffic? (Choose three)
Which two network events are highlighted through correlation objects as potential security risks? (Choose two.)
What helps avoid split brain in active / passive high availability (HA) pair deployment?
Which component is needed for a large-scale deployment of NGFWs with multiple Panorama Management Servers?
There are different Master Keys on Panorama and managed firewalls.
What is the result if a Panorama Administrator pushes configuration to managed firewalls?
When the Cortex Data Lake is sized for Traps Management Service, which two factors should be considered? (Choose two.)
When having a customer pre-sales call, which aspects of the NGFW should be covered?
In an HA pair running Active/Passive mode, over which interface do the dataplanes communicate?
In PAN-OS 10.0 and later, DNS Security allows policy actions to be applied based on which three domains? (Choose three.)
Which two email links, contained in SMTP and POP3, can be submitted from WildFire analysis with a WildFire subscription? (Choose two.)
What will a Palo Alto Networks next-generation firewall (NGFW) do when it is unable to retrieve a DNS verdict from the DNS cloud service in the configured lookup time?
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
Access to a business site is blocked by URL Filtering inline machine learning (ML) and
considered as a false-positive.
How should the site be made available?
WildFire subscription supports analysis of which three types? (Choose three.)
Which Palo Alto Networks pre-sales tool involves approximately 4 hour interview to discuss a customer's current security posture?
An endpoint, inside an organization, is infected with known malware that attempts to make a command-and-control connection to a C2 server via the destination IP address
Which mechanism prevents this connection from succeeding?
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A)
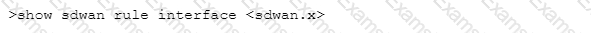
B)
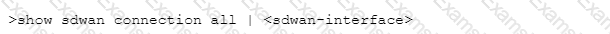
C)
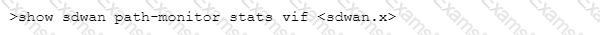
D)
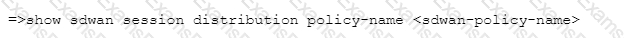
A customer is looking for an analytics tool that uses the logs on the firewall to detect actionable events on the network. They require something to automatically process a series of related threat events that, when combined, indicate a likely compromised host on their network or some other higher level conclusion. They need to pinpoint the area of risk, such as compromised hosts on the network, allows you to assess the risk and take action to prevent exploitation of network resources.
Which feature of PAN-OS can you talk about to address their requirement to optimize their business outcomes?
Which three platform components can identify and protect against malicious email links? (Choose three.)
A customer with a fully licensed Palo Alto Networks firewall is concerned about threats based on domain generation algorithms (DGAS).
Which Security profile is used to configure Domain Name Security (DNS) to Identity and block
previously unknown DGA-based threats in real time?
In Panorama, which three reports or logs will help identify the inclusion of a host source in a command-and-control (C2) incident? (Choose three.)
Which of the following statements is valid with regard to Domain Name System (DNS) sinkholing?
Which domain permissions are required by the User-ID Agent for WMI Authentication on a Windows Server? (Choose three.)
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
A client chooses to not block uncategorized websites.
Which two additions should be made to help provide some protection? (Choose two.)
WildFire machine learning (ML) for portable executable (PE) files is enabled in the antivirus profile and added to the appropriate firewall rules in the profile. In the Palo Alto Networks WildFire test av file, an attempt to download the test file is allowed through.
Which command returns a valid result to verify the ML is working from the command line.
Which three actions should be taken before deploying a firewall evaluation unt in a customer environment? (Choose three.)
Which Security profile on the Next-Generation Firewall (NGFW) includes Signatures to protect against brute force attacks?
What are two presales selling advantages of using Expedition? (Choose two.)
Which proprietary technology solutions will allow a customer to identify and control traffic sources regardless of internet protocol (IP) address or network segment?
Which option is required to Activate/Retrieve a Device Management License on the M-100 Appliance after the Auth Codes have been activated on the Palo Alto Networks Support Site?
For customers with high bandwidth requirements for Service Connections, what two limitations exist when onboarding multiple Service Connections to the same Prisma Access location servicing a single
Datacenter? (Choose two.)