
Palo Alto Networks Cybersecurity Practitioner (PCCP)
Last Update Feb 28, 2026
Total Questions : 227
We are offering FREE Practitioner Paloalto Networks exam questions. All you do is to just go and sign up. Give your details, prepare Practitioner free exam questions and then go for complete pool of Palo Alto Networks Cybersecurity Practitioner (PCCP) test questions that will help you more.



You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account.
Which type of attack is this?
Which scenario highlights how a malicious Portable Executable (PE) file is leveraged as an attack?
Which activities do local organization security policies cover for a SaaS application?
Which type of portable architecture can package software with dependencies in an isolated unit?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which action must Secunty Operations take when dealing with a known attack?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
Which item accurately describes a security weakness that is caused by implementing a “ports first” data security solution in a traditional data center?
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
Which action is unique to the security orchestration, automation, and response (SOAR) platforms?
A user is given access to a service that gives them access to cloud-hosted physical and virtual servers, storage, and networking.
Which NIST cloud service model is this?
Which type of system collects data and uses correlation rules to trigger alarms?
Which security component can detect command-and-control traffic sent from multiple endpoints within a corporate data center?
What are two capabilities of identity threat detection and response (ITDR)? (Choose two.)
Which MITRE ATT&CK tactic grants increased permissions to a user account for internal servers of a corporate network?
A firewall administrator needs to efficiently deploy corporate account configurations and VPN settings to targeted mobile devices within the network.
Which technology meets this requirement?
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
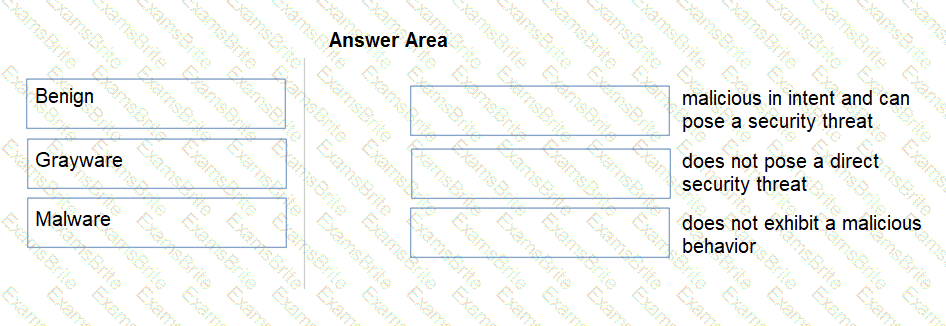
Match the Palo Alto Networks WildFire analysis verdict with its definition.
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
Which of the Cloud-Delivered Security Services (CDSS) will detect zero-day malware by using inline cloud machine learning (ML) and sandboxing?
Which component of the AAA framework regulates user access and permissions to resources?
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
Which term describes establishment of on-premises software on a cloud-based server?
What type of attack redirects the traffic of a legitimate website to a fake website?
A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
What is a reason IoT devices are more susceptible to command-and-control (C2) attacks?
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
Which capability does Cloud Security Posture Management (CSPM) provide for threat detection within Prisma Cloud?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
Which pillar of Prisma Cloud application security does vulnerability management fall under?
How does Cortex XSOAR Threat Intelligence Management (TIM) provide relevant threat data to analysts?
Which aspect of a SaaS application requires compliance with local organizational security policies?
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
Under which category does an application that is approved by the IT department, such as Office 365, fall?
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
Which statement describes a host-based intrusion prevention system (HIPS)?
Which type of malware replicates itself to spread rapidly through a computer network?
Which endpoint protection security option can prevent malware from executing software?
Which component of cloud security uses automated testing with static application security testing (SAST) to identify potential threats?