
HCIE-Datacom V1.0
Last Update Feb 28, 2026
Total Questions : 322
We are offering FREE H12-891_V1.0 Huawei exam questions. All you do is to just go and sign up. Give your details, prepare H12-891_V1.0 free exam questions and then go for complete pool of HCIE-Datacom V1.0 test questions that will help you more.



In a scenario where aVXLAN tunnelis dynamically established throughBGP EVPN, which of the following statements about the functions ofBGP EVPN Type 3 routesis incorrect?
The channelized sub-interface and FlexE technologies both can be used to implement network slicing, but the application scenarios of the two technologies are slightly different. Which of the following statements about the two technologies are correct?
If the number of MAC addresses learned on an interface enabled with port security reaches the upper limit, which of the following actions may the switch take?
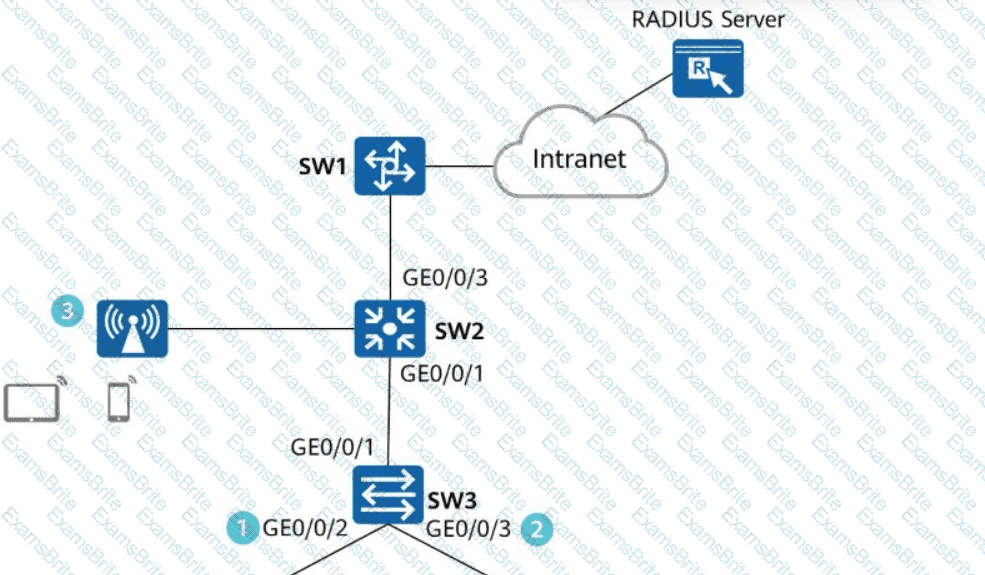
Network Admission Control (NAC) needs to be deployed on the network shown in the figure. Drag a proper authentication mode to each authentication point.
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
In the following figure, all routers are running OSPF. Given this, which of the following statements is correct?
Which of the following commands needs to be run in the BGP view to enable a VPN instance to advertise IP routes to the BGP-EVPN address family?
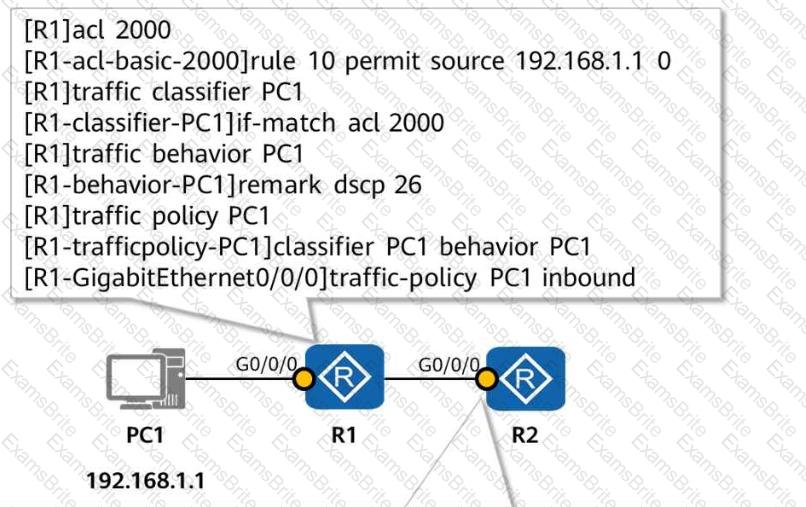
Refer to the configuration in the figure. Which queue on R2 do packets of PC1 enter by default?
The TTL field encapsulated in the MPLS label header can prevent infinite loops of MPLS packets. Which of the following statements regarding the TTL field are correct?
BGP Link State (BGP-LS) introduces a new NLRI into BGP. The NLRI carries link, node, topology prefix, and other information, and is also referred to as the link state NLRI.
In an MPLS VPN network, two-layer MPLS labels are added into data packets before they are transmitted over the public network. Which of the following statements regarding data packet processing are correct?
To prevent hackers from attacking user devices or networks using MAC addresses, you can configure MAC addresses of untrusted users as blackhole MAC addresses to filter out such invalid MAC addresses. When receiving a packet whose source or destination MAC address is a blackhole MAC address on a device, the device discards the packet.
On a CloudCampus virtualized campus network, virtual networks are defined based on services. Each virtual network corresponds to a service, and isolation needs to be manually configured between virtual networks.
In addition to indicating priority, the DSCP value can also indicate the drop probability. Which of the following DSCP values is set with the highest drop probability?
To enhance reliability, you can deploy Huawei iMaster NCE-WAN controllers in active/standby mode. Which of the following IP addresses must be configured to be the same for the active and standby controllers so that the controllers can be accessed properly? (Select All that Apply)
Which of the following is the purpose of configuring IS-IS fragmentation on an IS-IS device?
A network administrator runs the display telemetry subscription command on a device to check telemetry subscription information. The command output is as follows. Which of the following statements is incorrect?
[~CE] display telemetry subscription
Sub name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20030 RESOLVED - GRPC
Sub state : PASSIVE
Total subscription number is : 1
MPLS implements data forwarding based on two different planes. Which of the following statements regarding the forwarding mechanism are correct?
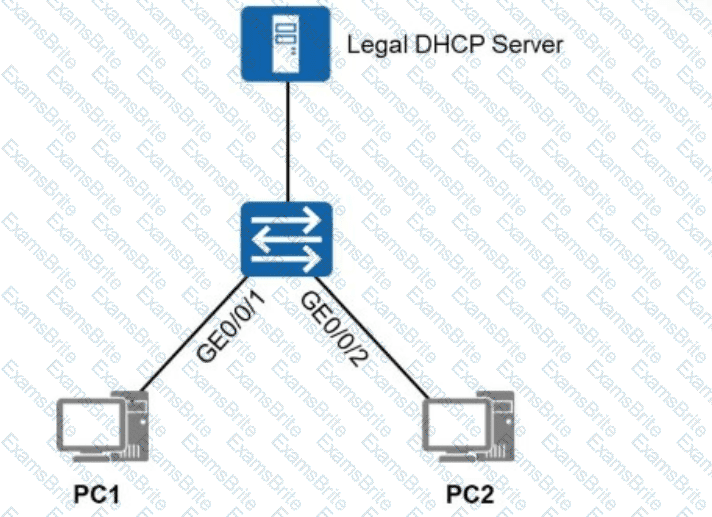
To allow only authorized users (users who obtain IP addresses through authorized DHCP servers or use specified static IP addresses) to access the network shown in the figure, which of the following solutions can be used?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
On a router,SRv6is enabled, and the configurations shown below are performed. Which of the following statements about the configurations are correct?
[Router-segment-routing-ipv6] locator srv6_locator1 ipv6-prefix 2001:DB8:ABCD::/64 static 32
iMaster NCE-Campus provides the terminal identification function to display the terminal type, operating system, and manufacturer information.
In a scenario whereSR Policiesare dynamically established through thecontroller, which of the following statements about theSR Policy solution architectureis incorrect?
On an SR-MPLS network, manually configured prefix SIDs on different devices may conflict with each other. Assume that there are four routes (prefix/mask SID) as follows. Which of the following routes will be selected according to the conflict handling principle?
In the firewall hot standby scenario, when VGMP works in load balancing mode, which of the following functions must be enabled on the firewalls to prevent the return traffic from being discarded because it does not match any session entry in the case of inconsistent forward and return paths?
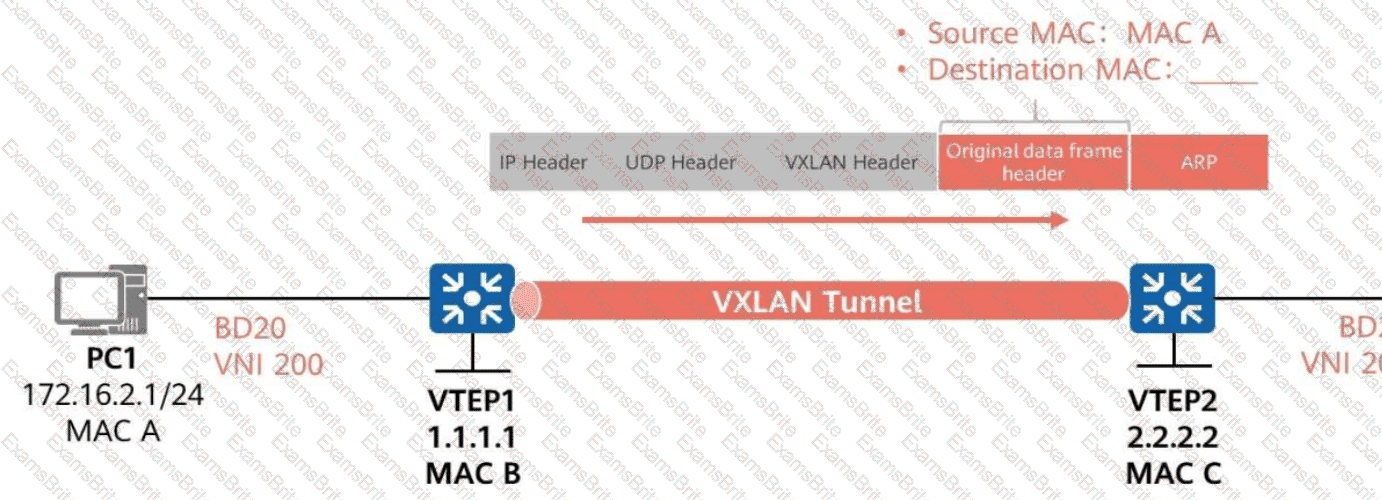
As shown in the figure,ARP broadcast suppression is enabled on VTEP1inBD 20 (VNI 200).
VTEP1 learns ARP informationaboutPC2 through BGP EVPN routes.
WhenVTEP1 forwards the ARP request for PC1’s MAC address to VTEP2,
What is the destination MAC address of the inner data frame?
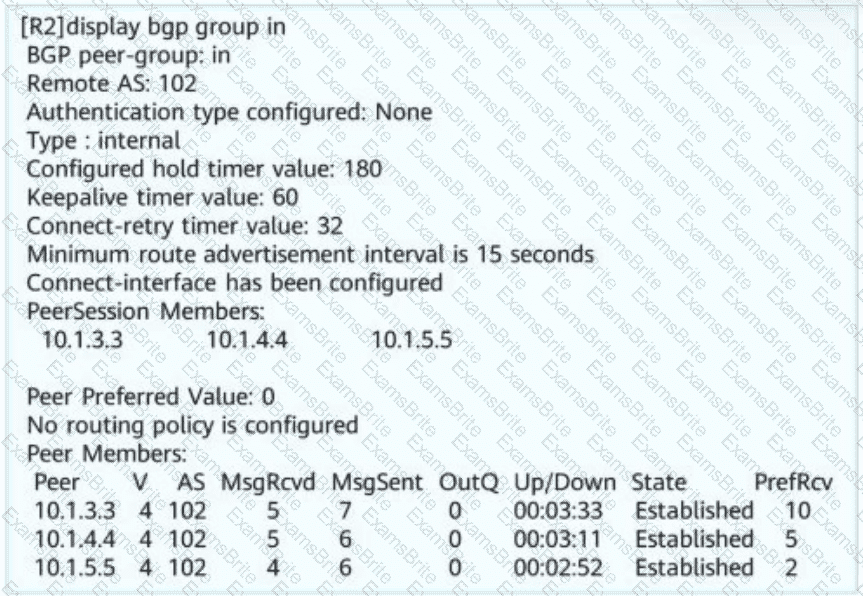
Network administrator A wants to view the BGP peer status of R2. The BGP peer status of R2 is shown in this figure. Obtain the following information: R2 resides in AS _____ (Enter only digits. Do not add punctuations or spaces.)
Which of the following items are included in static information collection and analysis?
Which of the following statements about BGP EVPN principles are correct in a scenario where a VXLAN tunnel is dynamically established through BGP EVPN?
If an engineer wants to remotely log in to a Huawei device, the engineer uses the Paramiko library to compile the following code when compiling the SSH Python script:
cli = ssh.invoke_shell()
cli.send("screen-length 0 temporary\n")
What is the function of screen-length 0 temporary?
New IS-IS TLVs are used to carry IPv6 addresses and reachability information to support IPv6 route processing and calculation.
Which of the following statements are correct about the command:
ping -aX -cY -sZ -vpn-instance M 10.5.16.2
When aclient invokes the iMaster NCE-Campus RESTful API, it sends anHTTP request. The server then returns thestatus code 401.
Which of the following errors has occurred?
Before connecting an SSH client to an SSH server in public key authentication mode, a client needs to create a key pair. Which of the following commands is used to create a DSS key pair on the client using Git Bash?
Flavors are additional behaviors defined to enhance theEnd series instructionsinSRv6. Which of the followingEnd instructionscan thePSP flavorbe attached to?
Which of the following statements about static VXLAN tunnel configuration are correct?
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is ______ IRB forwarding. (Capitalize the first letter.)
Which of the following statements is correct about the differences between NSR and NSF?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. HTTP is the most widely used network transmission protocol on the Internet. By default, the TCP port number _____ is used. (Fill in Arabic numerals.)
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
With telemetry, certain data can be sampled based on specific sampling paths. Which of the following sampling paths are supported by telemetry?
BGP routing policies can be used to control the advertisement and acceptance of routes.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following fields is NOT carried in BGP EVPN Type 5 routes?
On a broadcast network, if the DR priorities of two interfaces connecting two routers are set to 0, in which of the following states will the OSPF neighbor relationship stay?
Exhibit:
A loop occurs because Spanning Tree Protocol (STP) is not enabled on the network. Which of the following symptoms may occur?
Based on the figure, which of the following statements are correct?
1 10.1.12.2 40 ms 10 ms 10 ms
2 10.1.24.2 30 ms 20 ms 20 ms
3 10.1.34.1 20 ms 20 ms 20 ms
4 10.1.13.1 20 ms 20 ms 10 ms
5 10.1.12.2 20 ms 30 ms 20 ms
6 10.1.24.2 30 ms 30 ms 30 ms
7 10.1.34.1 50 ms 40 ms 40 ms
8 10.1.13.1 20 ms 30 ms 30 ms
An SRv6 Policy can be either statically configured on a device or dynamically generated by the controller and then delivered to the device.
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
iMaster NCE-CampusInsightuses SNMP technology to collect metrics and logs of network devices and detects network exceptions based on real service traffic.
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
You write the following Python code to invoke a RESTful API to obtain the token ID of iMaster NCE. Which of the following statements are correct?
import requests
response = requests.get("https://139.9.213.72 ")
print(response.json())
Error returned:
requests.exceptions.SSLError: HTTPSConnectionPool(host='139.9.213.72', port=18002): Max retries exceeded with url: /controller/v2/tokens (Caused by SSLError(CertificateError('hostname '139.9.213.72' doesn't match 'devzone.huawei.com')))
Options:
SR-MPLS uses the MPLS forwarding plane, and therefore requires MPLS to be enabled. Which of the following conditions must be met for MPLS to be automatically enabled on an interface? (Select all that apply)
Which of the following inter-AS MPLS L3VPN solutions needsASBRs to transmit VPNv4 routes?
Refer to the figure.
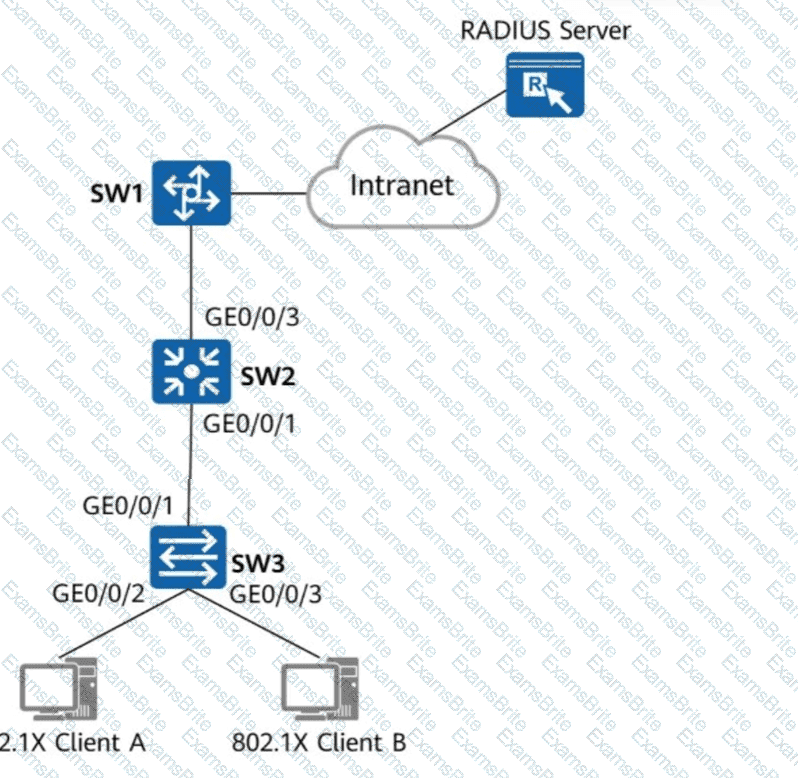
Which of the following steps are mandatory to enable 802.1X authentication on GE0/0/2 and GE0/0/3 of SW3 and configure a RADIUS server to authenticate and deliver network access rights to users?
During the implementation of iMaster NCE-Campus Wi-Fi location-based services (LBS), terminal location data is sent to an LBS platform through HTTP requests. Which of the following data formats is used in such HTTP requests?
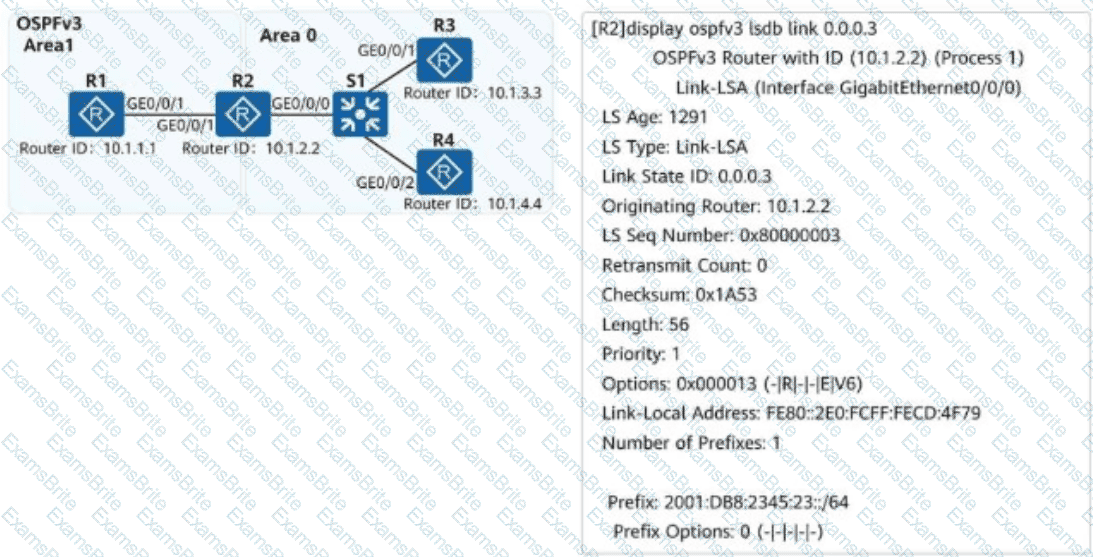
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and OSPFv3 is used for IPv6 network connectivity. An engineer checks the LSDB of R2 and obtains a Link-LSA. Which of the following statements about the LSA are correct?
Theon-premise modeis recommended for controller deployment onsmall and midsize campus networks.
What can be determined from the following figure?
Public Routing Table : ISIS
Summary Count: 6
ISIS Routing Table's Status : < Active >
Summary Count: 6
Destination : 3000:FDEA::4
NextHop : FE80::2E0:FCFF:FE98:2577
Cost : 20
Interface : GigabitEthernet0/0/1
PrefixLength : 128
Preference : 15
Protocol : ISIS-L2
Flags : D
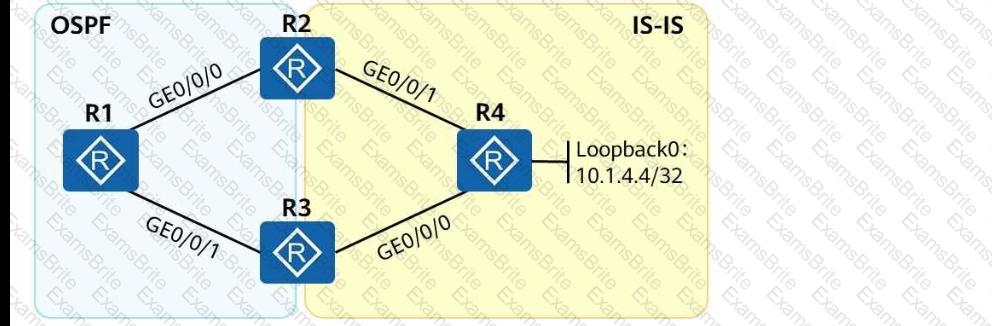
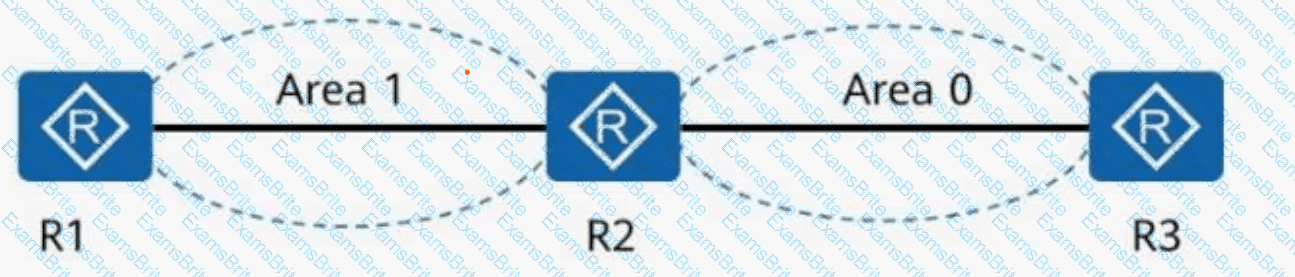
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
During the configuration of L3VPNv4 over SRv6 BE, if an RR is deployed in the SR domain, which command must be run on the RR to ensure that the PEs at both ends can correctly learn VPNv4 routes?
Which of the following are advantages of GRE tunnels? (Select All that Apply)
Which of the following statements does not cause the flapping of a VRRP group?
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and these routers use OSPFv3 for network connectivity. Which of the following statements about LSAs generated by the OSPFv3 network is incorrect?
When a client invokes the iMaster NCE-Campus RESTful API, it sends an HTTP request. The server then returns the status code 401. Which of the following errors has occurred?
When MPLS/BGP IP VPN is deployed, which of the following statements is incorrect about BGP route exchange between PEs and CEs?
In the LDP session establishment process, the initiator sends an Initialization message for parameter negotiation. Which message will be sent by the responder if it does not accept negotiation parameters?
In thesmall and midsize campus network designbased on theHuawei CloudCampus Solution, when over100 branchesneed to communicate with each other, which of the following interconnection networking models is recommended?
BGP EVPN can be used as the VXLAN control plane protocol to completely prevent traffic flooding, such as broadcast ARP packets, on the VXLAN network.
Complete the basic processing procedure for DiffServ model-based QoSshown in the figure

An SRv6 Policy can be either statically configured on a device, or be delivered to a device after being dynamically generated by the controller.
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
When configuring a static VXLAN tunnel, you need to manually configure the _____, VTEP IP address, and ingress replication list. (Enter only uppercase letters.)
In an MPLS domain, LSRs can be classified into ingress, transit, and egress LSRs based on how they process data. For the same FEC, an LSR can be both an ingress and a transit LSR of the FEC.
Huawei Open Programmability System (OPS) uses standard HTTP methods to access managed objects to manage network devices. Which of the following HTTP methods is used to configure the value of a network device's managed object?
An SRLB is a set of user-specified local labels reserved for SR-MPLS. These labels are locally configured and have only local significance. Therefore, they are not advertised through the IGP.
Which of the following inter-AS MPLS L3VPN solutions does not require MPLS to run between ASBRs?
A network administrator runs the display telemetry destination command on a device to check information about a destination group that sampled data is sent to. The command output is as follows. Which of the following statements is incorrect?
[~CE-telemetry-sensor-group-Sensor1]display telemetry destination
Dest-name Dest-addr Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
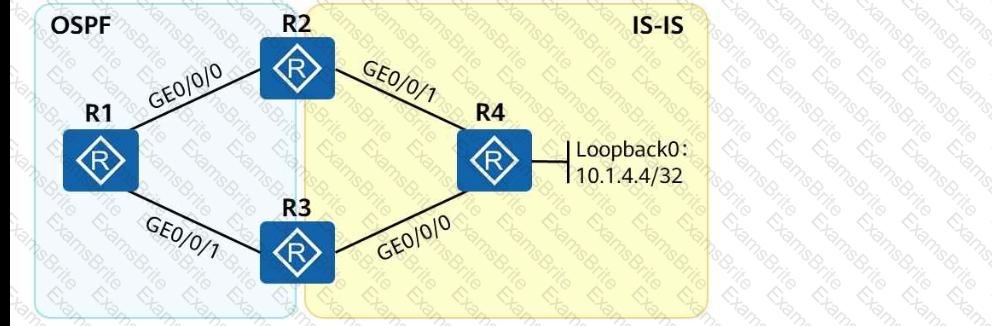
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
A network administrator needs to retrieve atoken IDfromiMaster NCEusing the following Python code:
import requests
nbi_name = "demol3@north.com"
nbi_pwd = "qqcOVcVel@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {'Content-Type': 'application/json', 'Accept': 'application/json'}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=incorrect)
Which of the following statements is incorrect?
Which of the following number sequences can be matched by the regular expression 100.s?
Which of the following operations is not involved in the middle phase of a migration?
An engineer needs todownload the configuration file vrpcfg.cfgto a local device throughSFTP, rename the configuration file to backup.cfg, and upload it to thedefault directory of the device.
The configuration file is located at /vrpcfg.cfg (default directory of the remote device), and the local directory is C:\.
Which of the followingPython Paramikocode lines can implement the required operations?
During the evolution from OSPFv2 to OSPFv3, LSA formats and functions remain unchanged, except that the network layer addresses in LSAs are changed from IPv4 to IPv6.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, run the command on the VTEP to view BGP EVPN routes. The route entries shown in the following figure are displayed. Which of the following statements about these routing entries are correct?
Network (EthTagId/IP Prefix/IP PrefixLen)
NextHop
*>i 0:172.16.2.0:24 1.1.1.2
*>i 0:172.16.13.0:24 1.1.1.2
*>i 0:192.168.122.0:30 1.1.1.2
Which of the following protocols is used in the Huawei SD-WAN Solution to report device performance data?
At the NETCONF content layer, the
Which of the following statements is incorrect about access control on small and midsize campus networks based on the Huawei CloudCampus solution?