
HCIP-Security V4.0 Exam
Last Update Feb 28, 2026
Total Questions : 60
We are offering FREE H12-725_V4.0 Huawei exam questions. All you do is to just go and sign up. Give your details, prepare H12-725_V4.0 free exam questions and then go for complete pool of HCIP-Security V4.0 Exam test questions that will help you more.



When an IPsec VPN is established in aggressive mode, AH+ESP can be used to encapsulate packets in NAT traversal scenarios.
The Common Vulnerability Scoring System (CVSS) is a widely used open standard for vulnerability scoring. It uses a modular scoring system. Which of the following is not included in the CVSS?
Sort the intrusion prevention steps in sequence based on the working mechanism of the firewall device.

The Nginx application is deployed on a Linux host. By checking Nginx logs, O&M engineers can obtain the complete URL information submitted by users and determine whether the Linux host is under SQL injection attacks.
The difference between DoS attacks and DDoS attacks is that DoS attacks are usually directly initiated by attackers, whereas DDoS attacks are usually initiated by attackers controlling multiple zombies.
HWTACACS is a centralized information exchange protocol based on the client/server structure. It uses UDP for transmission and performs authentication, authorization, and accounting for users accessing the Internet through Point-to-Point Protocol (PPP) or Virtual Private Dial-up Network (VPDN) and administrative users logging in to devices.
Which of the following statements is false about web rewriting in web proxy?
Which of the following statements is true about the incoming traffic in the firewall virtualsystem?(Select All that Apply)
When gateways are connected using GRE over IPsec, the IPsec encapsulation mode must be tunnel mode.
Trojan horses may disclose sensitive information of victims or even remotely manipulate victims' hosts, causing serious harm. Which of the following are the transmission modes of Trojan horses?(Select All that Apply)
Which of the following methods are used by flood attacks to cause denial of services?(Select All that Apply)
Network Access Control (NAC) is an end-to-end security control technology that works in combination with AAA to implement access authentication. Which of the following statements about NAC and AAA are true?(Select All that Apply)
In the figure, FW_A connects to FW_B through two links working in active/standby mode. When the active link of FW_A is faulty, the old IPsec tunnel 1 needs to be torn down, and IPsec tunnel 2 needs to be established with FW_B through the standby link to route traffic. In this case, configuring the IKE _____ detection mechanism on FW_A helps detect link faults and tear down the IPsec tunnel.(Enter lowercase letters.)
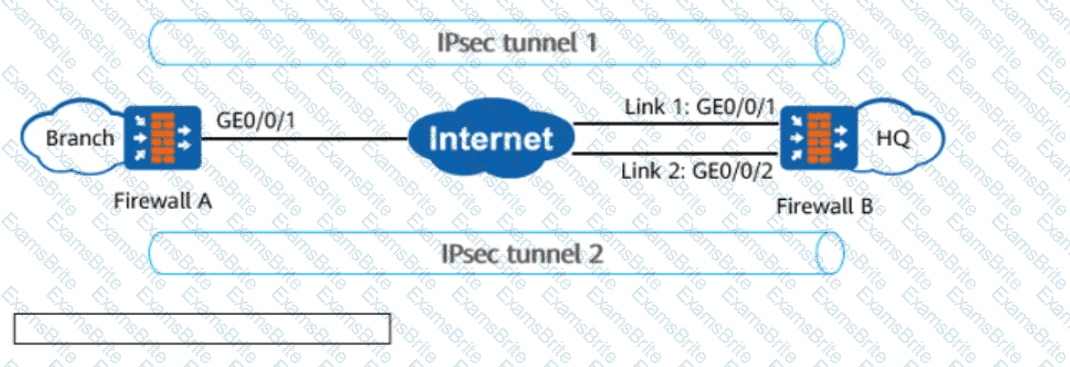
Which of the following statements is false about hot standby networking?(Select All that Apply)
On a WLAN where the WAC has Portal authentication configured, VLAN authorization can be implemented with no additional configuration required. After Portal authentication is complete, the WAC forwards STA traffic based on the authorized VLANs.
Authentication rules configured on iMaster NCE-Campus support multiple matching conditions, such as matching account information, SSID information, and terminal IP address ranges, so that different authentication rules can be executed for different users.