CompTIA CySA+ Certification Exam (CS0-002)
Last Update Apr 25, 2024
Total Questions : 372
We are offering FREE CS0-002 CompTIA exam questions. All you do is to just go and sign up. Give your details, prepare CS0-002 free exam questions and then go for complete pool of CompTIA CySA+ Certification Exam (CS0-002) test questions that will help you more.



A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
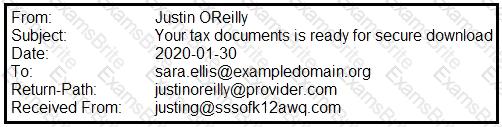
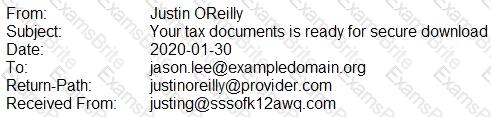
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
A security analyst is reviewing a firewall usage report that contains traffic generated over the last 30 minutes in order to locate unusual traffic patterns:
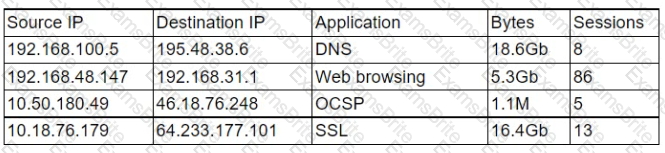
Which of the following source IP addresses does the analyst need to investigate further?
Which of the following organizational initiatives would be MOST impacted by data severighty issues?
An organization is adopting loT devices at an increasing rate and will need to account for firmware updates in its vulnerability management programs. Despite the number of devices being deployed, the organization has only focused on software patches so far. leaving hardware-related weaknesses open to compromise. Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
A company is required to monitor for unauthorized changes to baselines on all assets to comply with industry regulations. Two of the remote units did not recover after scans were performed on the assets. An analyst needs to recommend a solution to prevent recurrence. Which of the following is the best way to satisfy the regulatory requirement without impacting the availability to similar assets and creating an unsustainable process?
An analyst is reviewing email headers to determine if an email has been sent from a legitimate sender. The organization uses SPF to validate email origination. Which of the following most likely indicates an invalid originator?
While reviewing abnormal user activity, a security analyst notices a user has the following fileshare activities:
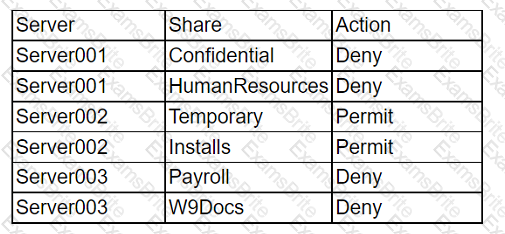
Which of the following should the analyst do first?
A security analyst is reviewing a new Internet portal that will be used for corporate employees to obtain their pay statements. Corporate policy classifies pay statement information as confidential, and it must be protected by MFA. Which of the following would best fulfill the MFA requirement while keeping the portal accessible from the internet?
Company A is m the process of merging with Company B As part of the merger, connectivity between the ERP systems must be established so portent financial information can be shared between the two entitles. Which of the following will establish a more automated approach to secure data transfers between the two entities?
A security analyst is evaluating the following support ticket:
Issue: Marketing campaigns are being filtered by the customer's email servers.
Description: Our marketing partner cannot send emails using our email address. The following log messages were collected from multiple customers:
• The SPF result is PermError.
• The SPF result is SoftFail or Fail.
• The 550 SPF check failed.
Which of the following should the analyst do next?
The following output is from a tcpdump al the edge of the corporate network:
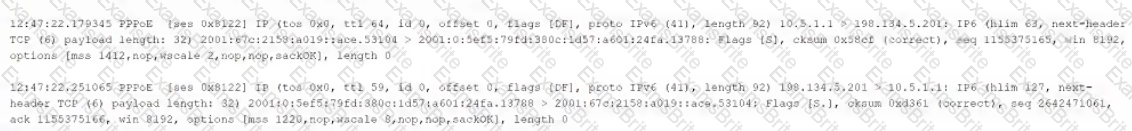
Which of the following best describes the potential security concern?
A new variant of malware is spreading on the company network using TCP 443 to contact its command-and-control server The domain name used for callback continues to change, and the analyst is unable to predict future domain name variance Which of the following actions should the analyst take to stop malicious communications with the LEAST disruption to service?
A manager asks a security analyst lo provide the web-browsing history of an employee. Which of the following should the analyst do first?
An application must pass a vulnerability assessment to move to the next gate. Consequently, any security issues that are found must be remediated prior to the next gate. Which of the following best describes the method for end-to-end vulnerability assessment?
A development team recently released a new version of a public-facing website for testing prior to production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility. Which of the following activities best describes the process the development team is initiating?
An IT security analyst has received an email alert regarding vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
Which of the following BEST identifies the appropriate use of threat intelligence as a function of detection and response?
While observing several host machines, a security analyst notices a program is overwriting data to a buffer. Which of the following controls will best mitigate this issue?
Which of the following attack techniques has the GREATEST likelihood of quick success against Modbus assets?
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:
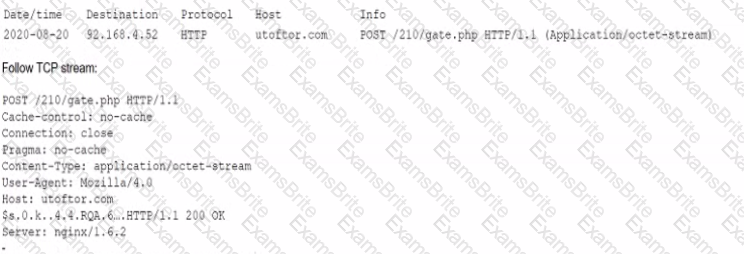
Which of the following describes what has occurred?
A company’s Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs. The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?
An organization wants to consolidate a number of security technologies throughout the organization and standardize a workflow for identifying security issues prioritizing the severity and automating a response Which of the following would best meet the organization's needs'?
An organization is experiencing security incidents in which a systems administrator is creating unauthorized user accounts A security analyst has created a script to snapshot the system configuration each day. Following iss one of the scripts:
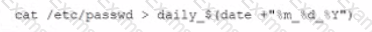
This script has been running successfully every day. Which of the following commands would provide the analyst with additional useful information relevant to the above script?
A)

B)
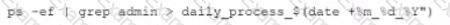
C)
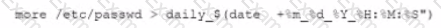
D)
An organization has the following risk mitigation policy:
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value.
The organization has identified the following risks:
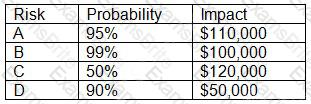
Which of the following is the order of priority for risk mitigation from highest to lowest?
A security analyst needs to provide a copy of a hard drive for forensic analysis. Which of the following would allow the analyst to perform the task?
A)
B)

C)

D)
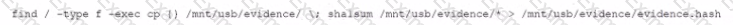
A security analyst is reviewing the following DNS logs as part of security-monitoring activities:
FROM 192.168.1.20 A www.google.com 67.43.45.22
FROM 192.168.1.20 AAAA www.google.com 2006:67:AD:1FAB::102
FROM 192.168.1.43 A www.mail.com 193.56.221.99
FROM 192.168.1.2 A www.company.com 241.23.22.11
FROM 192.168.1.211 A www.uewiryfajfchfaerwfj.co 32.56.32.122
FROM 192.168.1.106 A www.whatsmyip.com 102.45.33.53
FROM 192.168.1.93 ARAA www.nbc.com 2002:10:976::1
FROM 192.168.1.78 A www.comptia.org 122.10.31.87
Which of the following most likely occurred?
Which of the following are the most likely reasons to include reporting processes when updating an incident response plan after a breach? (Select two).
An analyst is performing a BIA and needs to consider measures and metrics. Which of the following would help the analyst achieve this objective? (Select two).
An organization discovers motherboards within the environment that appear to have been physically altered during the manufacturing process. Which of the following is the BEST course of action to mitigate the risk of this reoccurring?
A company's Chief Information Officer wants to use a CASB solution to ensure policies are being met during cloud access. Due to the nature of the company's business and risk appetite, the management team elected to not store financial information in the cloud. A security analyst needs to recommend a solution to mitigate the threat of financial data leakage into the cloud. Which of the following should the analyst recommend?
A financial organization has offices located globally. Per the organization’s policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's data. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
An analyst is reviewing registry keys for signs of possible compromise. The analyst observes the following entries:
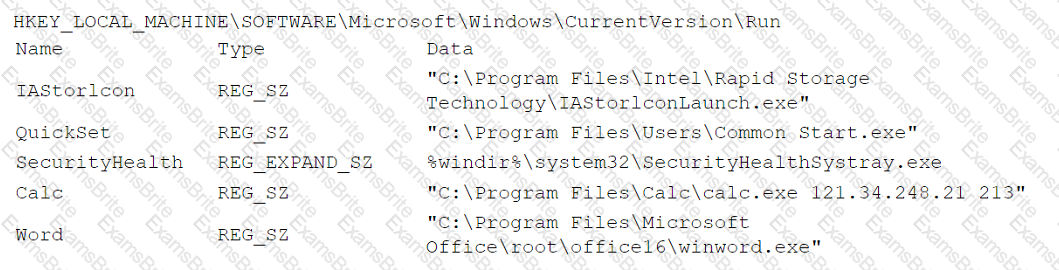
Which of the following entries should the analyst investigate first?
Which of the following describes the mam difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
After running the cat file01.bin | hexdump -c command, a security analyst reviews the following output snippet:
00000000 ff d8 ft e0 00 10 4a 46 49 46 00 01 01 00 00 01 |......JFIF......|
Which of the following digital-forensics techniques is the analyst using?
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the best solution to improve the equipment's security posture?
A security analyst observes a large amount of scanning activity coming from an IP address outside the organization's environment. Which of the following should the analyst do to block this activity?
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
Which of the following is an advantage of continuous monitoring as a way to help protect an enterprise?
A consultant evaluating multiple threat intelligence leads to assess potential risks for a client. Which of the following is the BEST approach for the consultant to consider when modeling the client's attack surface?
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages. Which of the following would most likely decrease the number of false positives?
A forensics investigator is analyzing a compromised workstation. The investigator has cloned the hard drive and needs to verify that a bit-level image copy of a hard drive is an exact clone of the original hard drive that was collected as evidence. Which of the following should the investigator do?
Which of the following describes the difference between intentional and unintentional insider threats'?
A security analyst is running a tool against an executable of an unknown source. The Input supplied by the tool to the executable program and the output from the executable are shown below:
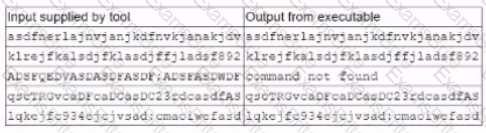
Which of the following should the analyst report after viewing this Information?
Industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacker was able to gain access to the SCADA by logging in to an account with weak credentials. Which of the following identity and access management solutions would help to mitigate this risk?
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
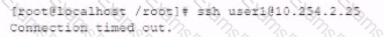
The analyst accesses the server console, and the following console messages are displayed:
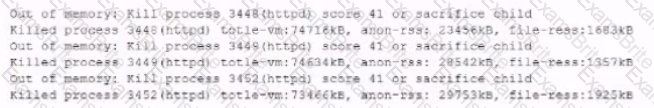
The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
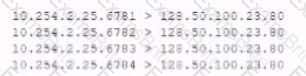
Which of the following is the BEST step for the analyst to lake next in this situation?
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:
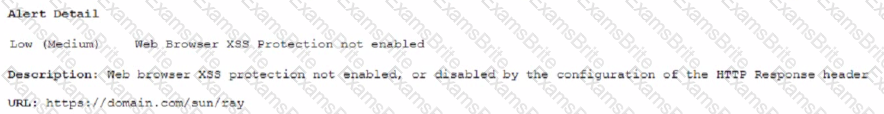
Which of the following is the MOST likely solution to the listed vulnerability?
A security analyst discovers the company's website is vulnerable to cross-site scripting. Which of the following solutions will best remedy the vulnerability?
A threat intelligence group issued a warning to its members regarding an observed increase in attacks performed by a specific threat actor and the related loCs. Which is of the following is (he best method to operationalize these loCs to detect future attacks?
During an investigation, an analyst discovers the following rule in an executive's email client:
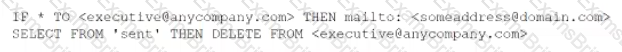
The executive is not aware of this rule. Which of the following should the analyst do first to evaluate the potential impact of this security incident?
When of the following techniques can be implemented to safeguard the confidentiality of sensitive information while allowing limited access to authorized individuals?
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IOC list for monitoring.
Which of the following is the best suggestion for improving monitoring capabilities?
A security analyst is attempting to resolve an incident in which highly confidential company pricing information was sent to clients. It appears this information was unintentionally sent by an employee who attached it to public marketing material. Which of the following configuration changes would work BEST to limit the risk of this incident being repeated?
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture." The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed. Which of the following commands will best accomplish the analyst's objectives?
A company notices unknown devices connecting to the internal network and would like to implement a solution to block all non-corporate managed machines. Which of the following solutions would be best to accomplish this goal?
A security analyst is concerned the number of security incidents being reported has suddenly gone down. Daily business interactions have not changed, and no following should the analyst review FIRST?
A small organization has proprietary software that is used internally. The system has not been wen maintained and cannot be updated with the rest or the environment. Which of the following is the BEST solution?
A company wants to configure the environment to allow passive network monitonng. To avoid disrupting the sensitive network, which of the following must be supported by the scanner's NIC to assist with the company's request?
A security analyst is logged on to a jump server to audit the system configuration and status. The organization's policies for access to and configuration of the jump server include the following:
• No network access is allowed to the internet.
• SSH is only for management of the server.
• Users must utilize their own accounts, with no direct login as an administrator.
• Unnecessary services must be disabled.
The analyst runs netstar with elevated permissions and receives the following output:
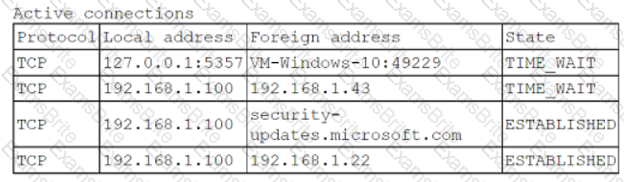
Which of the following policies does the server violate?
Which of the following types of controls defines placing an ACL on a file folder?
After a series of Group Policy Object updates, multiple services stopped functioning. The systems administrator believes the issue resulted from a Group Policy Object update but cannot validate which update caused the Issue. Which of the following security solutions would resolve this issue?
Which of the following best explains why it is important for companies to implement both privacy and security policies?
A help desk technician inadvertently sent the credentials of the company's CRM n clear text to an employee's personal email account. The technician then reset the employee's account using the appropriate process and the employee's corporate email, and notified the security team of the incident According to the incident response procedure, which of the following should the security team do NEXT?
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further in investigation?
During a routine review of service restarts a security analyst observes the following in a server log:
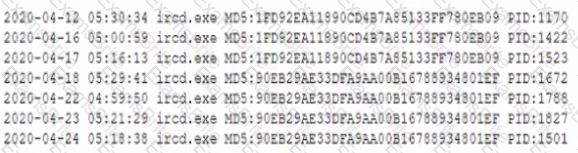
Which of the following is the GREATEST security concern?
During a risk assessment, a senior manager inquires about what the cost would be if a unique occurrence would impact the availability of a critical service. The service generates $1 ,000 in revenue for the organization. The impact of the attack would affect 20% of the server's capacity to perform jobs. The organization expects that five out of twenty attacks would succeed during the year. Which of the following is the calculated single loss expectancy?
An information security analyst discovered a virtual machine server was compromised by an attacker. Which of the following should be the first steps to confirm and respond to the incident? (Select two).
An analyst is reviewing the following output as part of an incident:
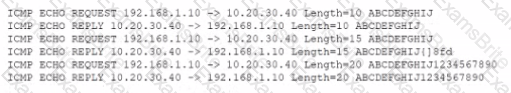
Which of the Wowing is MOST likely happening?
A company wants to run a leaner team and needs to deploy a threat management system with minimal human Interaction. Which of the following is the server component of the threat management system that can accomplish this goal?
Given the output below:
#nmap 7.70 scan initiated Tues, Feb 8 12:34:56 2022 as: nmap -v -Pn -p 80,8000,443 --script http-* -oA server.out 192.168.220.42 Which of the following is being performed?
Which of the following should a database administrator for an analytics firm implement to best protect PII from an insider threat?
A security analyst is concerned about sensitive data living on company file servers following a zero-day attack that nearly resulted in a breach of millions of customer records. The after action report indicates a lack of controls around the file servers that contain sensitive data. Which of the following DLP considerations would best help the analyst to classify and address the sensitive data on the file servers?
When investigating a report of a system compromise, a security analyst views the following /var/log/secure log file:
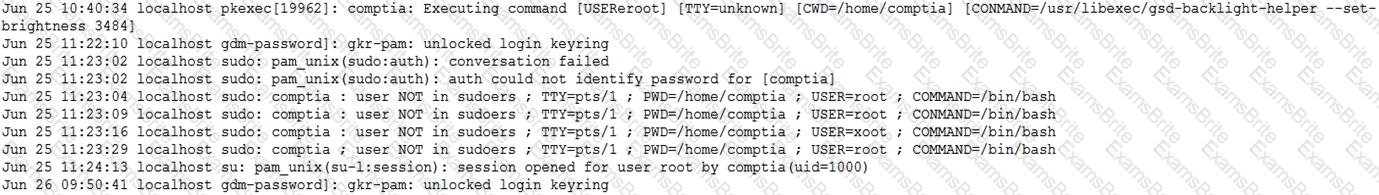
Which of the following can the analyst conclude from viewing the log file?
A company is setting up a small, remote office to support five to ten employees. The company's home office is in a different city, where the company uses a cloud service provider for its business applications and a local server to host its data. To provide shared access from the remote office to the local server and the business applications, which of the following would be the easiest and most secure solution?
A security analyst is correlating, ranking, and enriching raw data into a report that will be interpreted by humans or machines to draw conclusions and create actionable recommendations Which of the following steps in the intelligence cycle is the security analyst performing?
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user's data is not altered without the user's consent. Which of the following would be an appropriate course of action?
During routine monitoring a security analyst identified the following enterpnse network traffic:
Packet capture output:
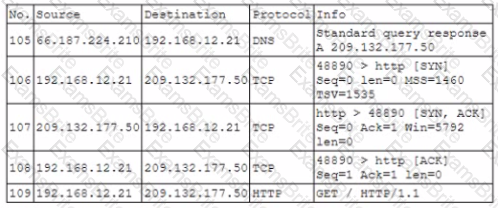
Which of the following BEST describes what the security analyst observed?
A security analyst is reviewing WAF alerts and sees the following request:

Which of the following BEST describes the attack?
An organization has a strict policy that if elevated permissions are needed, users should always run commands under their own account, with temporary administrator privileges if necessary. A security analyst is reviewing syslog entries and sees the following:
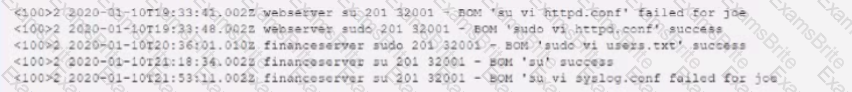
Which of the following entries should cause the analyst the MOST concern?
A security analyst was transferred to an organization's threat-hunting team to track specific activity throughout the enterprise environment The analyst must observe and assess the number ot times this activity occurs and aggregate the results. Which of the following is the BEST threat-hunting method for the analyst to use?
The security team decides to meet informally to discuss and test the response plan for potential security breaches and emergency situations. Which of the following types of training will the security team perform?
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:

Which of the following ports should be closed?
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time. Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
Which of the following is MOST dangerous to the client environment during a vulnerability assessment penetration test?
An analyst needs to provide recommendations based on a recent vulnerability scan:
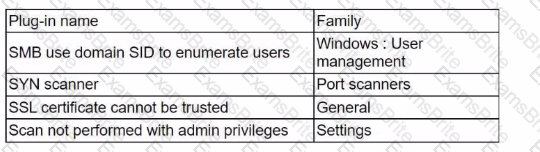
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
The management team has asked a senior security engineer to explore DLP security solutions for the company's growing use of cloud-based storage. Which of the following is an appropriate solution to control the sensitive data that is being stored in the cloud?
An organization has the following policies:
*Services must run on standard ports.
*Unneeded services must be disabled.
The organization has the following servers:
*192.168.10.1 - web server
*192.168.10.2 - database server
A security analyst runs a scan on the servers and sees the following output:
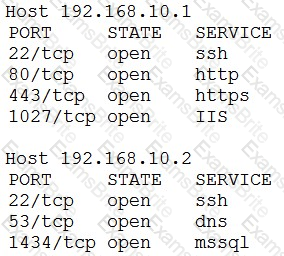
Which of the following actions should the analyst take?
An analyst determines a security incident has occurred Which of the following is the most appropnate NEXT step in an incident response plan?
An information security analyst is compiling data from a recent penetration test and reviews the following output:
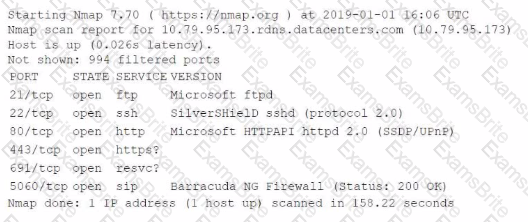
The analyst wants to obtain more information about the web-based services that are running on the target. Which of the following commands would most likely provide the needed information?
A Chief Information Secunty Officer has asked for a list of hosts that have critical and high-seventy findings as referenced in the CVE database. Which of the following tools would produce the assessment output needed to satisfy this request?
An organization has the following risk mitigation policies
• Risks without compensating controls will be mitigated first it the nsk value is greater than $50,000
• Other nsk mitigation will be pnontized based on risk value.
The following risks have been identified:
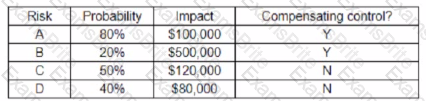
Which of the following is the ordei of priority for risk mitigation from highest to lowest?
A cybersecurity analyst routinely checks logs, querying for login attempts. While querying for unsuccessful login attempts during a five-day period, the analyst produces the following report:
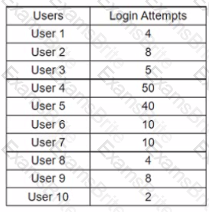
Which of the following BEST describes what the analyst Just found?
A security officer needs to find the most cost-effective solution to the current data privacy and protection gap found in the last security assessment. Which of the following is the BEST recommendation?
A technician working at company.com received the following email:
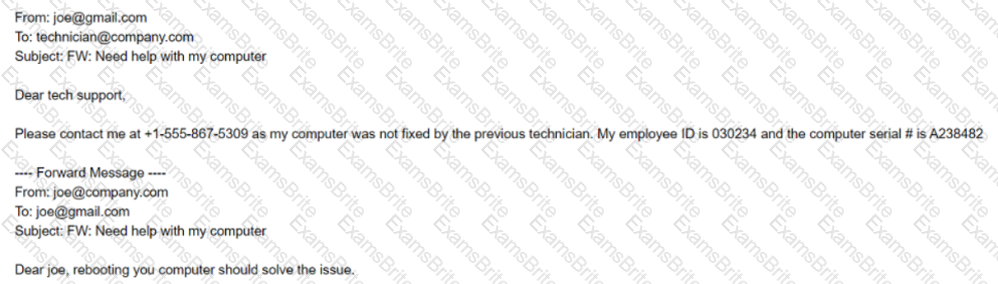
After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?
Which of the following data exfiltration discoveries would most likely require communicating a breach to regulatory agencies?
An organization implemented an extensive firewall access-control blocklist to prevent internal network ranges from communicating with a list of IP addresses of known command-and-control domains A security analyst wants to reduce the load on the firewall. Which of the following can the analyst implement to achieve similar protection and reduce the load on the firewall?
A social media company is planning an acquisition. Prior to the purchase, the Chief Security Officer (CSO) would like a full report to gain a better understanding of the prospective company's cybersecurity posture and to identify risks in the supply chain. Which of the following will best support the CSO's objective?
In SIEM software, a security analysis selected some changes to hash signatures from monitored files during the night followed by SMB brute-force attacks against the file servers Based on this behavior, which of the following actions should be taken FIRST to prevent a more serious compromise?
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
An email analysis system notifies a security analyst that the following message was quarantined and requires further review.

Which of the following actions should the security analyst take?
A security analyst needs to determine the best method for securing access to a top-secret datacenter Along with an access card and PIN code, which of the following additional authentication methods would be BEST to enhance the datacenter's security?
A security analyst reviews SIEM logs and discovers the following error event:
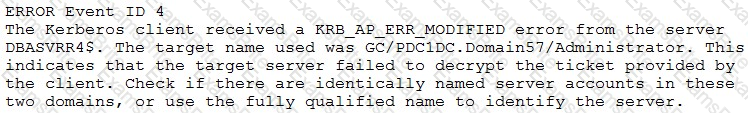
Which of the following environments does the analyst need to examine to continue troubleshooting the event?
A threat hurting team received a new loC from an ISAC that follows a threat actor's profile and activities. Which of the following should be updated NEXT?
A user receives a potentially malicious attachment that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review. Which of the following commands would most likely indicate if the email is malicious?
A security analyst who works in the SOC receives a new requirement to monitor for indicators of compromise. Which of the following is the first action the analyst should take in this situation?
While conoXicting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
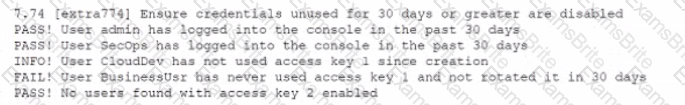
Based on the Prowler report, which of the following is the BEST recommendation?
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:

Office 365 User.
It looks like you account has been locked out Please click this link and follow the pfompts to restore access
Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
Which of the following factors would determine the regulations placed on data under data sovereignty laws?
During the security assessment of a new application, a tester attempts to log in to the application but receives the following message incorrect password for given username. Which of the following can the tester recommend to decrease the likelihood that a malicious attacker will receive helpful information?