Certified in Risk and Information Systems Control (CRISC)
Last Update Apr 15, 2024
Total Questions : 1197
We are offering FREE CRISC Isaca exam questions. All you do is to just go and sign up. Give your details, prepare CRISC free exam questions and then go for complete pool of Certified in Risk and Information Systems Control (CRISC) test questions that will help you more.



Which of the following is the BEST metric to demonstrate the effectiveness of an organization's change management process?
Which of the following is the MOST important foundational element of an effective three lines of defense model for an organization?
An organization has determined a risk scenario is outside the defined risk tolerance level. What should be the NEXT course of action?
Which of the following would be MOST helpful when estimating the likelihood of negative events?
Which of the following will BEST quantify the risk associated with malicious users in an organization?
Which of the following should be the PRIMARY consideration when assessing the automation of control monitoring?
Which of the following is the BEST indication of an improved risk-aware culture following the implementation of a security awareness training program for all employees?
A risk practitioner is organizing a training session lo communicate risk assessment methodologies to ensure a consistent risk view within the organization Which of the following i< the MOST important topic to cover in this training?
Which of the following is the PRIMARY factor in determining a recovery time objective (RTO)?
An organization that has been the subject of multiple social engineering attacks is developing a risk awareness program. The PRIMARY goal of this program should be to:
A data processing center operates in a jurisdiction where new regulations have significantly increased penalties for data breaches. Which of the following elements of the risk register is MOST important to update to reflect this change?
A risk practitioner discovers several key documents detailing the design of a product currently in development have been posted on the Internet. What should be the risk practitioner's FIRST course of action?
A risk practitioner is summarizing the results of a high-profile risk assessment sponsored by senior management. The BEST way to support risk-based decisions by senior management would be to:
A risk practitioners PRIMARY focus when validating a risk response action plan should be that risk response:
A key risk indicator (KRI) is reported to senior management on a periodic basis as exceeding thresholds, but each time senior management has decided to take no action to reduce the risk. Which of the following is the MOST likely reason for senior management's response?
Numerous media reports indicate a recently discovered technical vulnerability is being actively exploited. Which of the following would be the BEST response to this scenario?
Which of the following is the BEST method to maintain a common view of IT risk within an organization?
An organization's recovery team is attempting to recover critical data backups following a major flood in its data center. However, key team members do not know exactly what steps should be taken to address this crisis. Which of the following is the MOST likely cause of this situation?
Which of the following would be of GREATEST concern regarding an organization's asset management?
When evaluating a number of potential controls for treating risk, it is MOST important to consider:
A failed IT system upgrade project has resulted in the corruption of an organization's asset inventory database. Which of the following controls BEST mitigates the impact of this incident?
Which of the following is the MOST important consideration when developing risk strategies?
An organization plans to implement a new Software as a Service (SaaS) speech-to-text solution Which of the following is MOST important to mitigate risk associated with data privacy?
Which of the following is the GREATEST benefit of a three lines of defense structure?
A risk practitioner is reviewing accountability assignments for data risk in the risk register. Which of the following would pose the GREATEST concern?
Which of the following would be a risk practitioner's BEST course of action when a project team has accepted a risk outside the established risk appetite?
Which of the following is MOST important to update when an organization's risk appetite changes?
Which of the following is MOST important to consider before determining a response to a vulnerability?
Which of the following contributes MOST to the effective implementation of risk responses?
Which of the following is MOST helpful in providing a high-level overview of current IT risk severity*?
Which of the following sources is MOST relevant to reference when updating security awareness training materials?
An organization is planning to move its application infrastructure from on-premises to the cloud. Which of the following is the BEST course of the actin to address the risk associated with data transfer if the relationship is terminated with the vendor?
An organization is considering the adoption of an aggressive business strategy to achieve desired growth From a risk management perspective what should the risk practitioner do NEXT?
Which of the following is the PRIMARY reason to engage business unit managers in risk management processes'?
A poster has been displayed in a data center that reads. "Anyone caught taking photographs in the data center may be subject to disciplinary action." Which of the following control types has been implemented?
When confirming whether implemented controls are operating effectively, which of the following is MOST important to review?
Senior management is deciding whether to share confidential data with the organization's business partners. The BEST course of action for a risk practitioner would be to submit a report to senior management containing the:
Which of the following issues found during the review of a newly created disaster recovery plan (DRP) should be of MOST concern?
Which of the following is PRIMARILY a risk management responsibly of the first line of defense?
Which of the following key performance indicators (KPis) would BEST measure me risk of a service outage when using a Software as a Service (SaaS) vendors
When classifying and prioritizing risk responses, the areas to address FIRST are those with:
it was determined that replication of a critical database used by two business units failed. Which of the following should be of GREATEST concern1?
An organization has made a decision to purchase a new IT system. During when phase of the system development life cycle (SDLC) will identified risk MOST likely lead to architecture and design trade-offs?
Which of the following should be a risk practitioner's NEXT step after learning of an incident that has affected a competitor?
Which of the following is the BEST control to minimize the risk associated with scope creep in software development?
An organization has completed a risk assessment of one of its service providers. Who should be accountable for ensuring that risk responses are implemented?
Which of the following would be of MOST concern to a risk practitioner reviewing risk action plans for documented IT risk scenarios?
Which of the following is MOST important to promoting a risk-aware culture?
Which of the following is the MOST important reason to validate that risk responses have been executed as outlined in the risk response plan''
When performing a risk assessment of a new service to support a core business process, which of the following should be done FIRST to ensure continuity of operations?
An organization has been experiencing an increasing number of spear phishing attacks Which of the following would be the MOST effective way to mitigate the risk associated with these attacks?
Which of the following management action will MOST likely change the likelihood rating of a risk scenario related to remote network access?
Which of the following will BEST ensure that controls adequately support business goals and objectives?
When a risk practitioner is determining a system's criticality. it is MOST helpful to review the associated:
Which of the following is MOST useful for measuring the existing risk management process against a desired state?
Following an acquisition, the acquiring company's risk practitioner has been asked to update the organization's IT risk profile What is the MOST important information to review from the acquired company to facilitate this task?
Which of the following s MOST likely to deter an employee from engaging in inappropriate use of company owned IT systems?
An organization has provided legal text explaining the rights and expected behavior of users accessing a system from geographic locations that have strong privacy regulations. Which of the following control types has been applied?
Which of the following statements describes the relationship between key risk indicators (KRIs) and key control indicators (KCIs)?
Which of the following is the MOST important responsibility of a risk owner?
Which of the following statements BEST illustrates the relationship between key performance indicators (KPIs) and key control indicators (KCIs)?
Which of The following should be of GREATEST concern for an organization considering the adoption of a bring your own device (BYOD) initiative?
Which of me following is MOST helpful to mitigate the risk associated with an application under development not meeting business objectives?
From a risk management perspective, the PRIMARY objective of using maturity models is to enable:
While reviewing the risk register, a risk practitioner notices that different business units have significant variances in inherent risk for the same risk scenario. Which of the following is the BEST course of action?
An information system for a key business operation is being moved from an in-house application to a Software as a Service (SaaS) vendor. Which of the following will have the GREATEST impact on the ability to monitor risk?
The MAIN purpose of reviewing a control after implementation is to validate that the control:
Which of the following is the MOST important reason to link an effective key control indicator (KCI) to relevant key risk indicators (KRIs)?
Which of the following is MOST helpful in aligning IT risk with business objectives?
Which of the following provides the BEST evidence that a selected risk treatment plan is effective?
An organization must make a choice among multiple options to respond to a risk. The stakeholders cannot agree and decide to postpone the decision. Which of the following risk responses has the organization adopted?
When reporting on the performance of an organization's control environment including which of the following would BEST inform stakeholders risk decision-making?
While evaluating control costs, management discovers that the annual cost exceeds the annual loss expectancy (ALE) of the risk. This indicates the:
While conducting an organization-wide risk assessment, it is noted that many of the information security policies have not changed in the past three years. The BEST course of action is to:
Which of the following is the MOST effective control to ensure user access is maintained on a least-privilege basis?
A global organization is planning to collect customer behavior data through social media advertising. Which of the following is the MOST important business risk to be considered?
Which of the following practices MOST effectively safeguards the processing of personal data?
Which of the following is the BEST course of action to help reduce the probability of an incident recurring?
Which of the following is the PRIMARY risk management responsibility of the second line of defense?
In an organization that allows employee use of social media accounts for work purposes, which of the following is the BEST way to protect company sensitive information from being exposed?
Which of the following is MOST important to communicate to senior management during the initial implementation of a risk management program?
Which of the following should be the MOST important consideration when performing a vendor risk assessment?
A financial institution has identified high risk of fraud in several business applications. Which of the following controls will BEST help reduce the risk of fraudulent internal transactions?
The BEST metric to monitor the risk associated with changes deployed to production is the percentage of:
Which of the following is the MOST appropriate key risk indicator (KRI) for backup media that is recycled monthly?
Key risk indicators (KRIs) are MOST useful during which of the following risk management phases?
A risk practitioner has been asked to advise management on developing a log collection and correlation strategy. Which of the following should be the MOST important consideration when developing this strategy?
What are the MOST essential attributes of an effective Key control indicator (KCI)?
What should be the PRIMARY driver for periodically reviewing and adjusting key risk indicators (KRIs)?
Which of the following facilitates a completely independent review of test results for evaluating control effectiveness?
Which of the following is the PRIMARY reason to use key control indicators (KCIs) to evaluate control operating effectiveness?
After a high-profile systems breach at an organization s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor's control environment?
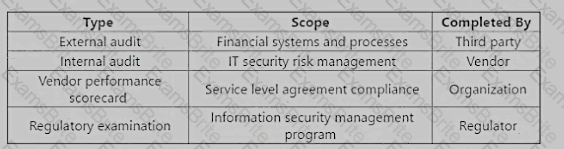
Which of the following should be a risk practitioner's PRIMARY focus when tasked with ensuring organization records are being retained for a sufficient period of time to meet legal obligations?
Management has required information security awareness training to reduce the risk associated with credential compromise. What is the BEST way to assess the effectiveness of the training?
Which of the following is the BEST indicator of the effectiveness of IT risk management processes?
Which of the following is MOST important for an organization to update following a change in legislation requiring notification to individuals impacted by data breaches?
A newly hired risk practitioner finds that the risk register has not been updated in the past year. What is the risk practitioner's BEST course of action?
Which of the following is the BEST key performance indicator (KPI) for determining how well an IT policy is aligned to business requirements?
A key risk indicator (KRI) indicates a reduction in the percentage of appropriately patched servers. Which of the following is the risk practitioner's BEST course of action?
An organization is planning to outsource its payroll function to an external service provider Which of the following should be the MOST important consideration when selecting the provider?
An internally developed payroll application leverages Platform as a Service (PaaS) infrastructure from the cloud. Who owns the related data confidentiality risk?
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of an anti-virus program?
Which of the following is MOST helpful in developing key risk indicator (KRl) thresholds?
An organization is planning to acquire a new financial system. Which of the following stakeholders would provide the MOST relevant information for analyzing the risk associated with the new IT solution?
Which of the following BEST confirms the existence and operating effectiveness of information systems controls?
Which of the following is MOST important to review when determining whether a potential IT service provider’s control environment is effective?
An organization has raised the risk appetite for technology risk. The MOST likely result would be:
Which of the following provides The MOST useful information when determining a risk management program's maturity level?
Which of the following is the BEST way for a risk practitioner to verify that management has addressed control issues identified during a previous external audit?
Which of the following provides the BEST evidence that risk responses have been executed according to their risk action plans?
Read" rights to application files in a controlled server environment should be approved by the:
A risk practitioner observes that the fraud detection controls in an online payment system do not perform as expected. Which of the following will MOST likely change as a result?
Which of the following would provide the MOST objective assessment of the effectiveness of an organization's security controls?
Which of the following will BEST help an organization select a recovery strategy for critical systems?
What is the MOST important consideration when aligning IT risk management with the enterprise risk management (ERM) framework?
Which of the following is MOST helpful in verifying that the implementation of a risk mitigation control has been completed as intended?
After migrating a key financial system to a new provider, it was discovered that a developer could gain access to the production environment. Which of the following is the BEST way to mitigate the risk in this situation?
Who is responsible for IT security controls that are outsourced to an external service provider?
An organization is unable to implement a multi-factor authentication requirement until the next fiscal year due to budget constraints. Consequently, a policy exception must be submitted. Which of the following is MOST important to include in the analysis of the exception?
Which of the following is the MOST important data attribute of key risk indicators (KRIs)?
Which of the following can be interpreted from a single data point on a risk heat map?
An organization's internal audit department is considering the implementation of robotics process automation (RPA) to automate certain continuous auditing tasks. Who would own the risk associated with ineffective design of the software bots?
A risk assessment indicates the residual risk associated with a new bring your own device (BYOD) program is within organizational risk tolerance. Which of the following should the risk practitioner
recommend be done NEXT?
Which of the following would BEST enable mitigation of newly identified risk factors related to internet of Things (loT)?
Implementing which of the following will BEST help ensure that systems comply with an established baseline before deployment?
Which of the following will MOST improve stakeholders' understanding of the effect of a potential threat?
A risk practitioner has learned that an effort to implement a risk mitigation action plan has stalled due to lack of funding. The risk practitioner should report that the associated risk has been:
Prior to selecting key performance indicators (KPIs), itis MOST important to ensure:
A risk assessment has identified increased losses associated with an IT risk scenario. It is MOST important for the risk practitioner to:
An identified high probability risk scenario involving a critical, proprietary business function has an annualized cost of control higher than the annual loss expectancy. Which of the following is the BEST risk response?
What is MOST important for the risk practitioner to understand when creating an initial IT risk register?
Which of the following would present the GREATEST challenge when assigning accountability for control ownership?
An organization has outsourced its backup and recovery procedures to a third-party cloud provider. Which of the following is the risk practitioner s BEST course of action?
Which of the following is the BEST key performance indicator (KPI) to measure the effectiveness of a disaster recovery plan (DRP)?
What is the BEST information to present to business control owners when justifying costs related to controls?
A risk heat map is MOST commonly used as part of an IT risk analysis to facilitate risk:
Which of the following techniques would be used during a risk assessment to demonstrate to stakeholders that all known alternatives were evaluated?
The PRIMARY reason a risk practitioner would be interested in an internal audit report is to:
A risk practitioner is assisting with the preparation of a report on the organization s disaster recovery (DR) capabilities. Which information would have the MOST impact on the overall recovery profile?
Which of the following is the MOST important requirement for monitoring key risk indicators (KRls) using log analysis?
Which of the following is the MOST important factor affecting risk management in an organization?
Which of the following would be- MOST helpful to understand the impact of a new technology system on an organization's current risk profile?
An organization is planning to engage a cloud-based service provider for some of its data-intensive business processes. Which of the following is MOST important to help define the IT risk associated with this outsourcing activity?
A review of an organization s controls has determined its data loss prevention {DLP) system is currently failing to detect outgoing emails containing credit card data. Which of the following would be MOST impacted?
Which of the following controls will BEST detect unauthorized modification of data by a database administrator?
Which of the following is MOST important when developing key performance indicators (KPIs)?
The analysis of which of the following will BEST help validate whether suspicious network activity is malicious?
Which of the following helps ensure compliance with a nonrepudiation policy requirement for electronic transactions?
Which of the following is the MOST important consideration when multiple risk practitioners capture risk scenarios in a single risk register?
Which of the following is the MOST important key performance indicator (KPI) to establish in the service level agreement (SLA) for an outsourced data center?
Which of the following is the MOST important benefit of key risk indicators (KRIs)'
Which of the following IT controls is MOST useful in mitigating the risk associated with inaccurate data?
Which of the following would be the BEST recommendation if the level of risk in the IT risk profile has decreased and is now below management's risk appetite?
IT management has asked for a consolidated view into the organization's risk profile to enable project prioritization and resource allocation. Which of the following materials would
be MOST helpful?
Which of the following is the BEST way to identify changes to the risk landscape?
Which of the following would MOST effectively enable a business operations manager to identify events exceeding risk thresholds?
Which of the following is the BEST way to validate the results of a vulnerability assessment?