
Palo Alto Networks Cloud Security Professional
Last Update Feb 28, 2026
Total Questions : 258
We are offering FREE CloudSec-Pro Paloalto Networks exam questions. All you do is to just go and sign up. Give your details, prepare CloudSec-Pro free exam questions and then go for complete pool of Palo Alto Networks Cloud Security Professional test questions that will help you more.



A customer has a requirement to scan serverless functions for vulnerabilities.
What is the correct option to configure scanning?
Which two bot types are part of Web Application and API Security (WAAS) bot protection? (Choose two.)
The Compute Console has recently been upgraded, and the administrator plans to delay upgrading the Defenders and the Twistcli tool until some of the team’s resources have been rescaled. The Console is currently one major release ahead.
What will happen as a result of the Console upgrade?
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication?
• Console is located at https://prisma-console.mydomain.local
• Token is: TOKEN_VALUE
• Report ID is: REPORTJD
• Container image running is: myimage:latest
Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
A customer finds that an open alert from the previous day has been resolved. No auto-remediation was configured.
Which two reasons explain this change in alert status? (Choose two.)
How is the scope of each rule determined in the Prisma Cloud Compute host runtime policy?
Which two integrations enable ingesting host findings to generate alerts? (Choose two.)
What is the purpose of Incident Explorer in Prisma Cloud Compute under the "Monitor" section?
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
Which policy type provides information about connections from suspicious IPs in a customer database?
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
Given this information:
The Console is located at https://prisma-console.mydomain.local The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
Prisma Cloud supports which three external systems that allow the import of vulnerabilities and provide additional context on risks in the cloud? (Choose three.)
Which two statements explain differences between build and run config policies? (Choose two.)
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day.
Which area on the Console will provide input on this issue?
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
What will happen when a Prisma Cloud Administrator has configured agentless scanning in an environment that also has Host and Container Defenders deployed?
Which API calls can scan an image named myimage: latest with twistcli and then retrieve the results from Console?
On which cloud service providers can you receive new API release information for Prisma Cloud?
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
In Prisma Cloud Software Release 22.06 (Kepler), which Registry type is added?
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)

C)
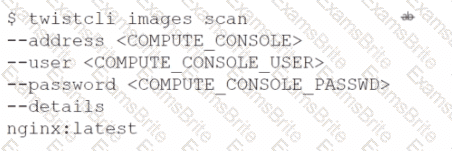
D)
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster.
Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant’s existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which option shows the steps required during the alert rule creation process to achieve this objective?
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
Which three elements are part of SSH Events in Host Observations? (Choose three.)
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
Which RQL query will help create a custom identity and access management (1AM) policy to alert on Lambda functions that have permission to terminate EC2 instances?
Which two statements apply to the Defender type Container Defender - Linux?
During the Learning phase of the Container Runtime Model, Prisma Cloud enters a “dry run” period for how many hours?
Which two statements are true about the differences between build and run config policies? (Choose two.)
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Prisma Cloud supports sending audit event records to which three targets? (Choose three.)
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
Which two frequency options are available to create a compliance report within the console? (Choose two.)
What are two ways to scan container images in Jenkins pipelines? (Choose two.)
Which three serverless runtimes are supported by Prisma Cloud for vulnerability and compliance scans? (Choose three.)
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
Which two information types cannot be seen in the data security dashboard? (Choose two).
Given a default deployment of Console, a customer needs to identify the alerted compliance checks that are set by default.
Where should the customer navigate in Console?
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
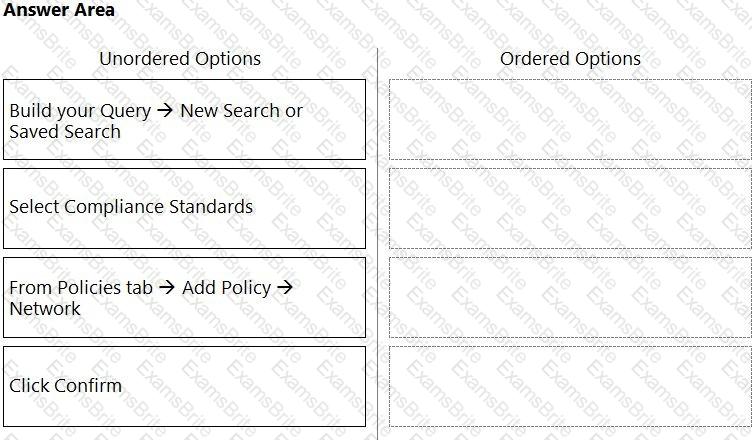
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Which two roles have access to view the Prisma Cloud policies? (Choose two.)
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
A Prisma Cloud Administrator onboarded an AWS cloud account with agentless scanning enabled successfully to Prisma Cloud. Which item requires deploying defenders to be able to inspect the risk on the onboarded AWS account?
What are two built-in RBAC permission groups for Prisma Cloud? (Choose two.)