CompTIA Advanced Security Practitioner (CASP+) Exam
Last Update Apr 24, 2024
Total Questions : 439
We are offering FREE CAS-004 CompTIA exam questions. All you do is to just go and sign up. Give your details, prepare CAS-004 free exam questions and then go for complete pool of CompTIA Advanced Security Practitioner (CASP+) Exam test questions that will help you more.



All staff at a company have started working remotely due to a global pandemic. To transition to remote work, the company has migrated to SaaS collaboration tools. The human resources department wants to use these tools to process sensitive information but is concerned the data could be:
Leaked to the media via printing of the documents
Sent to a personal email address
Accessed and viewed by systems administrators
Uploaded to a file storage site
Which of the following would mitigate the department’s concerns?
A company is moving most of its customer-facing production systems to the cloud-facing production systems to the cloud. IaaS is the service model being used. The Chief Executive Officer is concerned about the type of encryption available and requires the solution must have the highest level of security.
Which of the following encryption methods should the cloud security engineer select during the implementation phase?
A security engineer is assessing the security controls of loT systems that are no longer supported for updates and patching. Which of the following is the best mitigation for defending these loT systems?
After a security incident, a network security engineer discovers that a portion of the company’s sensitive external traffic has been redirected through a secondary ISP that is not normally used.
Which of the following would BEST secure the routes while allowing the network to function in the event of a single provider failure?
Device event logs sources from MDM software as follows:
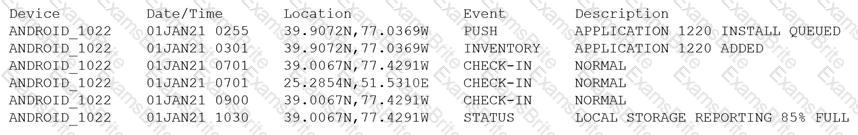
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
During a review of events, a security analyst notes that several log entries from the FIM system identify changes to firewall rule sets. While coordinating a response to the FIM entries, the analyst receives alerts from the DLP system that indicate an employee is sending sensitive data to an external email address. Which of the following would be the most relevant to review in order to gain a better understanding of whether these events are associated with an attack?
Ransomware encrypted the entire human resources fileshare for a large financial institution. Security operations personnel were unaware of the activity until it was too late to stop it. The restoration will take approximately four hours, and the last backup occurred 48 hours ago. The management team has indicated that the RPO for a disaster recovery event for this data classification is 24 hours.
Based on RPO requirements, which of the following recommendations should the management team make?
An organization’s hunt team thinks a persistent threats exists and already has a foothold in the enterprise network.
Which of the following techniques would be BEST for the hunt team to use to entice the adversary to uncover malicious activity?
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs.
Which of the following should the company use to prevent data theft?
An organization recently started processing, transmitting, and storing its customers’ credit card information. Within a week of doing so, the organization suffered a massive breach that resulted in the exposure of the customers’ information.
Which of the following provides the BEST guidance for protecting such information while it is at rest and in transit?
An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key.
Which of the following would BEST secure the REST API connection to the database while preventing the use of a hard-coded string in the request string?
A company plans to build an entirely remote workforce that utilizes a cloud-based infrastructure. The Chief Information Security Officer asks the security engineer to design connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud provider.
The company can control what SaaS applications each individual user can access.
User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
An organization recently experienced a ransomware attack. The security team leader is concerned about the attack reoccurring. However, no further security measures have been implemented.
Which of the following processes can be used to identify potential prevention recommendations?
UESTION NO: 36
Which of the following is a benefit of using steganalysis techniques in forensic response?
A security solution uses a sandbox environment to execute zero-day software and collect indicators of compromise. Which of the following should the organization do to BEST take advantage of this solution?
Which of the following should be established when configuring a mobile device to protect user internet privacy, to ensure the connection is encrypted, and to keep user activity hidden? (Select TWO).
The Chief Information Security Officer is concerned about the possibility of employees downloading ‘malicious files from the internet and ‘opening them on corporate workstations. Which of the following solutions would be BEST to reduce this risk?
Which of the following objectives BEST supports leveraging tabletop exercises in business continuity planning?
The CI/CD pipeline requires code to have close to zero defects and zero vulnerabilities. The current process for any code releases into production uses two-week Agile sprints. Which of the following would BEST meet the requirement?
A developer needs to implement PKI in an autonomous vehicle's software in the most efficient and labor-effective way possible. Which of the following will the developer MOST likely implement?
A university issues badges through a homegrown identity management system to all staff and students. Each week during the summer, temporary summer school students arrive and need to be issued a badge to access minimal campus resources. The security team received a report from an outside auditor indicating the homegrown system is not consistent with best practices in the security field.
Which of the following should the security team recommend FIRST?
Some end users of an e-commerce website are reporting a delay when browsing pages. The website uses TLS 1.2. A security architect for the website troubleshoots by connecting from home to the
website and capturing tramc via Wire-shark. The security architect finds that the issue is the time required to validate the certificate. Which of the following solutions should the security architect
recommend?
A junior developer is informed about the impact of new malware on an Advanced RISC Machine (ARM) CPU, and the code must be fixed accordingly. Based on the debug, the malware is able to insert itself in another process ‘memory location. Which of the following technologies can the developer enable on the ARM architecture to prevent this type of malware?
A cloud security architect has been tasked with selecting the appropriate solution given the following:
* The solution must allow the lowest RTO possible.
* The solution must have the least shared responsibility possible.
« Patching should be a responsibility of the CSP.
Which of the following solutions can BEST fulfill the requirements?
A security analyst is using data provided from a recent penetration test to calculate CVSS scores to prioritize remediation. Which of the following metric groups would the analyst need to determine to get the overall scores? (Select THREE).
In a cloud environment, the provider offers relief to an organization's teams by sharing in many of the operational duties. In a shared responsibility model, which of the following responsibilities belongs to the provider in a Paas implementation?
A company has decided that only administrators are permitted to use PowerShell on their Windows computers. Which of the following is the BEST way for an administrator to implement this decision?
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems. Some of the requirements are:
• Handle an increase in customer demand of resources
• Provide quick and easy access to information
• Provide high-quality streaming media
• Create a user-friendly interface
Which of the following actions should be taken FIRST?
Which of the following testing plans is used to discuss disaster recovery scenarios with representatives from multiple departments within an incident response team but without taking any invasive actions?
A systems administrator at a web-hosting provider has been tasked with renewing the public certificates of all customer sites. Which of the following would BEST support multiple domain names while minimizing the amount of certificates needed?
A network administrator receives a ticket regarding an error from a remote worker who is trying to reboot a laptop. The laptop has not yet loaded the operating system, and the user is unable to continue the boot process. The administrator is able to provide the user with a recovery PIN, and the user is able to reboot the system and access the device as needed. Which of the following is the MOST likely cause of the error?
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity
Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).
In comparison with traditional on-premises infrastructure configurations, defining ACLs in a CSP relies on:
A security architect updated the security policy to require a proper way to verify that packets received between two parties have not been tampered with and the connection remains private. Which of the following cryptographic techniques can be used to ensure the security policy is being enforced properly?
An architectural firm is working with its security team to ensure that any draft images that are leaked to the public can be traced back to a specific external party. Which of the following would BEST accomplish this goal?
An investigator is attempting to determine if recent data breaches may be due to issues with a company's web server that offers news subscription services. The investigator has gathered the following
data:
• Clients successfully establish TLS connections to web services provided by the server.
• After establishing the connections, most client connections are renegotiated
• The renegotiated sessions use cipher suite SHR.
Which of the following is the MOST likely root cause?
A consultant needs access to a customer's cloud environment. The customer wants to enforce the following engagement requirements:
• All customer data must remain under the control of the customer at all times.
• Third-party access to the customer environment must be controlled by the customer.
• Authentication credentials and access control must be under the customer's control.
Which of the following should the consultant do to ensure all customer requirements are satisfied when accessing the cloud environment?
A company wants to refactor a monolithic application to take advantage of cloud native services and service microsegmentation to secure sensitive application components. Which of the following should the company implement to ensure the architecture is portable?
A security administrator wants to enable a feature that would prevent a compromised encryption key from being used to decrypt all the VPN traffic. Which of the following should the security administrator use?
A security engineer is re-architecting a network environment that provides regional electric distribution services. During a pretransition baseline assessment, the engineer identified the following security-relevant characteristics of the environment:
• Enterprise IT servers and supervisory industrial systems share the same subnet.
• Supervisory controllers use the 750MHz band to direct a portion of fielded PLCs.
• Command and telemetry messages from industrial control systems are unencrypted and unauthenticated.
Which of the following re-architecture approaches would be best to reduce the company's risk?
An IT department is currently working to implement an enterprise DLP solution. Due diligence and best practices must be followed in regard to mitigating risk. Which of the following ensures that authorized modifications are well planned and executed?
When implementing serverless computing an organization must still account for:
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port The service cannot be turned off, as it would impact a critical application's ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
A security engineer is creating a single CSR for the following web server hostnames:
• wwwint internal
• www company com
• home.internal
• www internal
Which of the following would meet the requirement?
A user forwarded a suspicious email to a security analyst for review. The analyst examined the email and found that neither the URL nor the attachment showed any indication of malicious activities. Which of the following intelligence collection methods should the analyst use to confirm the legitimacy of the email?
A security engineer is concerned about the threat of side-channel attacks The company experienced a past attack that degraded parts of a SCADA system, causing a fluctuation to 20,000rpm from its normal operating range As a result, the part deteriorated more quickly than the mean time to failure A further investigation revealed the attacker was able to determine the acceptable rpm range, and the malware would then fluctuate the rpm until the pan failed Which of the following solutions would be best to prevent a side-channel attack in the future?
A cyberanalyst for a government agency is concerned about how Pll is protected A supervisor indicates that a Privacy Impact Assessment must be done. Which of the following describes a function of a Privacy Impact Assessment?
An organization has an operational requirement with a specific equipment vendor The organization is located in the United States, but the vendor is located in another region Which of the following risks would be most concerning to the organization in the event of equipment failure?
A Chief Security Officer (CSO) is concerned about the number of successful ransomware attacks that have hit the company. The data Indicates most of the attacks came through a fake email. The company has added training, and the CSO now wants to evaluate whether the training has been successful. Which of the following should the CSO implement?
A managed security provider (MSP) is engaging with a customer who was working through a complete digital transformation Part of this transformation involves a move to cloud servers to ensure a scalable, high-performance, online user experience The current architecture includes:
• Directory servers
• Web servers
• Database servers
• Load balancers
• Cloud-native VPN concentrator
• Remote access server
The MSP must secure this environment similarly to the infrastructure on premises Which of the following should the MSP put in place to BEST meet this objective? (Select THREE)
A security operations center analyst is investigating anomalous activity between a database server and an unknown external IP address and gathered the following data:
• dbadmin last logged in at 7:30 a.m. and logged out at 8:05 a.m.
• A persistent TCP/6667 connection to the external address was established at 7:55 a.m. The connection is still active.
• Other than bytes transferred to keep the connection alive, only a few kilobytes of data transfer every hour since the start of the connection.
• A sample outbound request payload from PCAP showed the ASCII content: "JOIN #community".
Which of the following is the MOST likely root cause?
A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of assets, such as workstation, servers, and laptops. Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the company?
A security engineer needs 10 implement a CASB to secure employee user web traffic. A Key requirement is mat relevant event data must be collected from existing on-premises infrastructure components and consumed by me CASB to expand traffic visibility. The solution must be nighty resilient to network outages. Which of the following architectural components would BEST meet these requirements?
An architectural firm is working with its security team to ensure that any draft images that are leaked to the public can be traced back to a specific external party. Which of the following would BEST accomplish this goal?
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive PI I and identity information, such as passport numbers. The SaaS CRM system does not meet the organization's current security standards. The assessment identifies the following:
1) There will be a 520,000 per day revenue loss for each day the system is delayed going into production.
2) The inherent risk is high.
3) The residual risk is low.
4) There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization's requirements?
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights. Which of the following documents will MOST likely contain these elements
The Chief information Officer (CIO) wants to implement enterprise mobility throughout the organization. The goal is to allow employees access to company resources. However the CIO wants the ability to enforce configuration settings, manage data, and manage both company-owned and personal devices. Which of the following should the CIO implement to achieve this goal?
During a phishing exercise, a few privileged users ranked high on the failure list. The enterprise would like to ensure that privileged users have an extra security-monitoring control in place. Which of the following Is the MOST
likely solution?
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
A security analyst needs to recommend a remediation to the following threat:
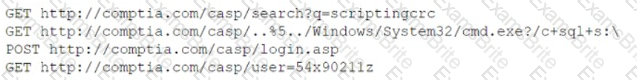
Which of the following actions should the security analyst propose to prevent this successful exploitation?
An organization's finance system was recently attacked. A forensic analyst is reviewing the contents of the compromised files for credit card data. Which of the following commands should
the analyst run to BEST determine whether financial data was lost?
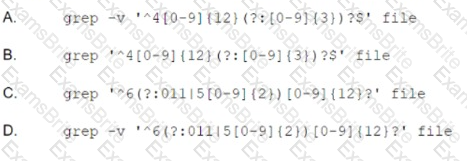
A security engineer at a company is designing a system to mitigate recent setbacks caused competitors that are beating the company to market with the new products. Several of the products incorporate propriety enhancements developed by the engineer’s company. The network already includes a SEIM and a NIPS and requires 2FA for all user access. Which of the following system should the engineer consider NEXT to mitigate the associated risks?
A security analyst wants to keep track of alt outbound web connections from workstations. The analyst's company uses an on-premises web filtering solution that forwards the outbound traffic to a perimeter firewall. When the security analyst gets the connection events from the firewall, the source IP of the outbound web traffic is the translated IP of the web filtering solution. Considering this scenario involving source NAT. which of the following would be the BEST option to inject in the HTTP header to include the real source IP from workstations?
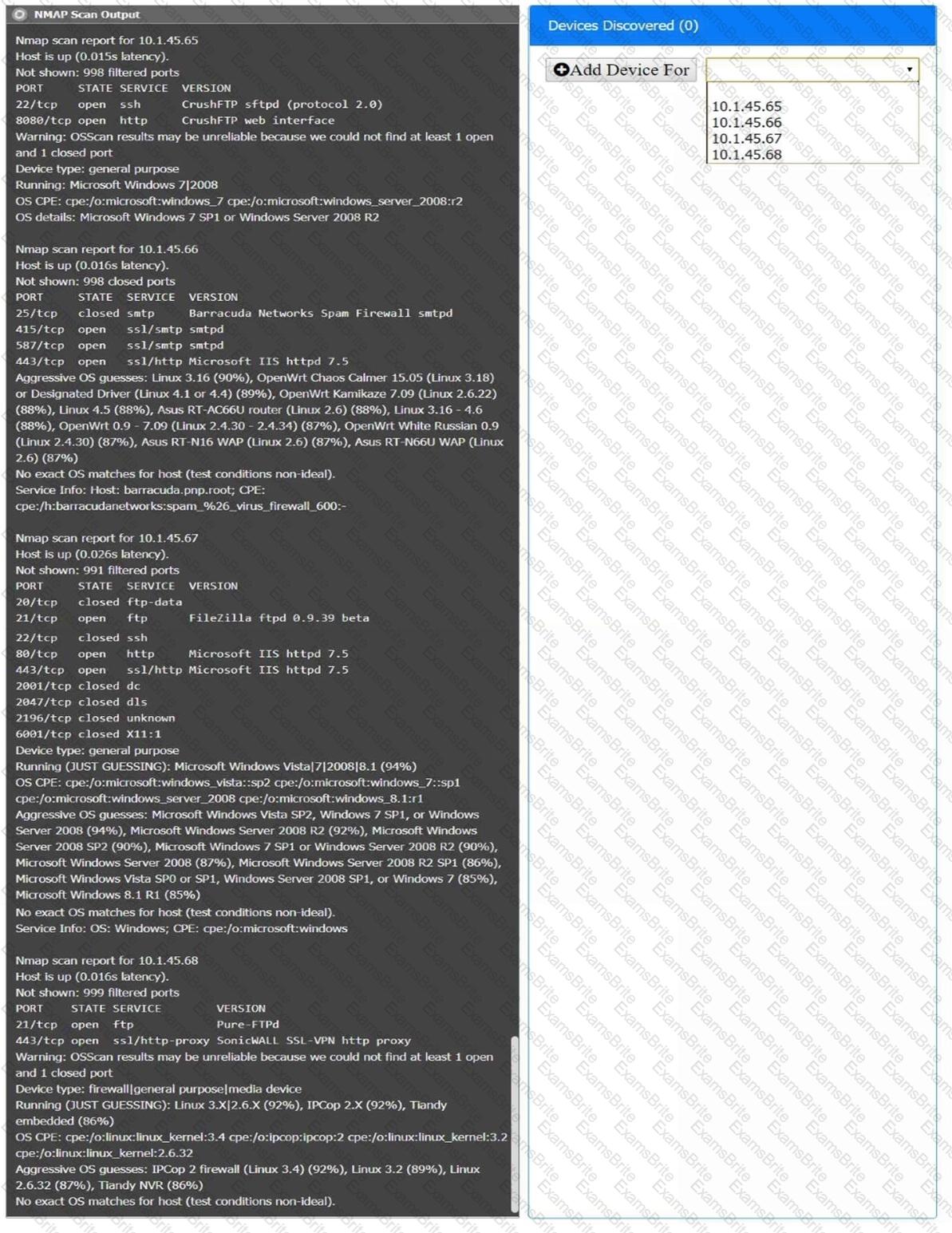
SIMULATION
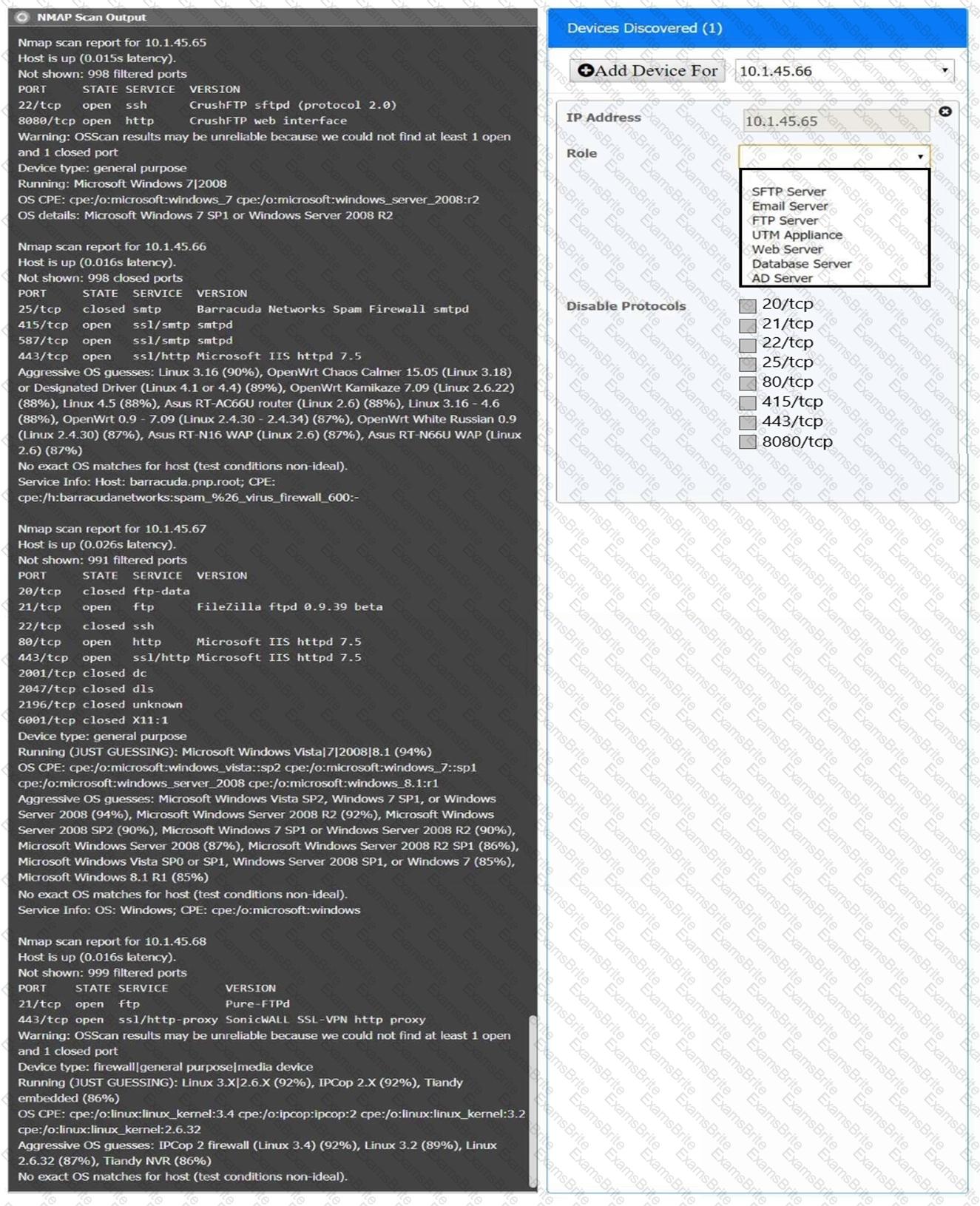
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A networking team asked a security administrator to enable Flash on its web browser. The networking team explained that an important legacy embedded system gathers SNMP information from various devices. The system can only be managed through a web browser running Flash. The embedded system will be replaced within the year but is still critical at the moment.
Which of the following should the security administrator do to mitigate the risk?
A pharmaceutical company recently experienced a security breach within its customer-facing web portal. The attackers performed a SQL injection attack and exported tables from the company’s managed database, exposing customer information.
The company hosts the application with a CSP utilizing the IaaS model. Which of the following parties is ultimately responsible for the breach?
Given the following log snippet from a web server:
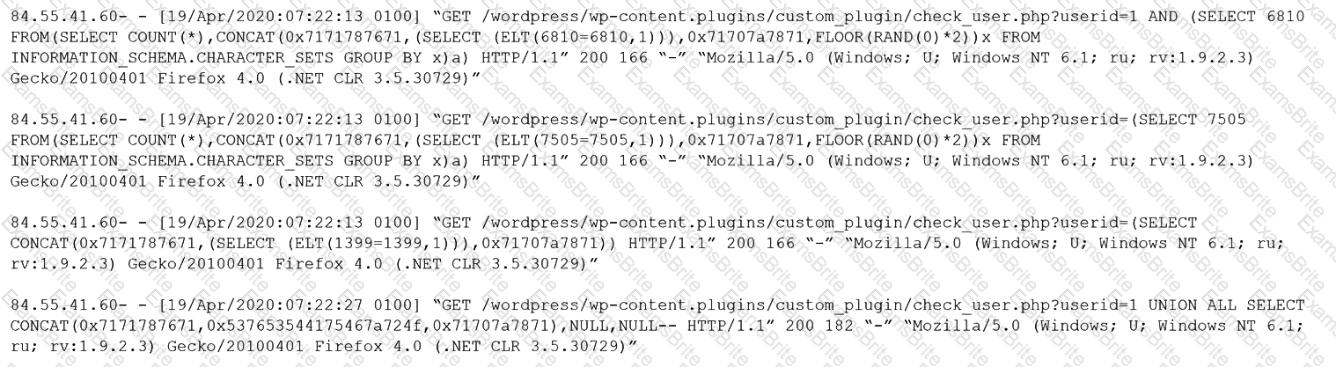
Which of the following BEST describes this type of attack?
A security architect is designing a solution for a new customer who requires significant security capabilities in its environment. The customer has provided the architect with the following set of requirements:
* Capable of early detection of advanced persistent threats.
* Must be transparent to users and cause no performance degradation.
+ Allow integration with production and development networks seamlessly.
+ Enable the security team to hunt and investigate live exploitation techniques.
Which of the following technologies BEST meets the customer's requirements for security capabilities?
A security architect for a large, multinational manufacturer needs to design and implement a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect focus on to prevent attacks against the ОТ network?
The OS on several servers crashed around the same time for an unknown reason. The servers were restored to working condition, and all file integrity was verified. Which of the following should the incident response team perform to understand the crash and prevent it in the future?
The Chief information Security Officer (CISO) of a small locate bank has a compliance requirement that a third-party penetration test of the core banking application must be conducted annually. Which of the following services would fulfill the compliance requirement with the LOWEST resource usage?
A security architect was asked to modify an existing internal network design to accommodate the following requirements for RDP:
• Enforce MFA for RDP
• Ensure RDP connections are only allowed with secure ciphers.
The existing network is extremely complex and not well segmented. Because of these limitations, the company has requested that the connections not be restricted by network-level firewalls Of ACLs.
Which of the following should the security architect recommend to meet these requirements?
During a network defense engagement, a red team is able to edit the following registry key:
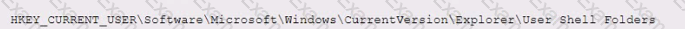
Which of the following tools is the red team using to perform this action?
After installing an unapproved application on a personal device, a Chief Executive Officer reported an incident to a security analyst. This device is not controlled by the MDM solution, as stated in the BYOD policy. However, the device contained critical confidential information. The cyber incident response team performed the analysis on the device and found the following log:
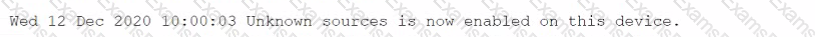
Which of the following is the most likely reason for the successful attack?
A security administrator needs to implement a security solution that will
• Limit the attack surface in case of an incident
• Improve access control for external and internal network security.
• Improve performance with less congestion on network traffic
Which of the following should the security administrator do?
A user in the finance department uses a laptop to store a spreadsheet that contains confidential financial information for the company. Which of the following would be the best way to protect the file while the user brings the laptop between locations? (Select two).
The Chief Executive Officer of an online retailer notices a sudden drop in sales A security analyst at the retailer detects a redirection of unsecure web traffic to a competitor's site Which of the following would best prevent this type of attack?
After a cybersecurity incident, a judge found that a company did not conduct a proper forensic investigation. The company was ordered to pay penalties. Which of the following forensic steps would be best to prevent this from happening again?
A small bank is evaluating different methods to address and resolve the following requirements
" Must be able to store credit card data using the smallest amount of data possible
• Must be compliant with PCI DSS
• Must maintain confidentiality if one piece of the layer is compromised
Which of the following is the best solution for the bank?
A financial institution generates a list of newly created accounts and sensitive information on a daily basis. The financial institution then sends out a file containing thousands of lines of data. Which of the following would be the best way to reduce the risk of a malicious insider making changes to the file that could go undetected?
A security architect must mitigate the risks from what is suspected to be an exposed, private cryptographic key. Which of the following is the best step to take?
An organization does not have visibility into when company-owned assets are off network or not connected via a VPN. The lack of visibility prevents the organization from meeting security and operational objectives. Which of the following cloud-hosted solutions should the organization implement to help mitigate the risk?
A systems engineer needs to develop a solution that uses digital certificates to allow authentication to laptops. Which of the following authenticator types would be most appropriate for the engineer to include in the design?
After the latest risk assessment, the Chief Information Security Officer (CISO) decides to meet with the development and security teams to find a way to reduce the security task workload The CISO would like to:
* Have a solution that uses API to communicate with other security tools
* Use the latest technology possible
* Have the highest controls possible on the solution
Which of following is the best option to meet these requirements?
An organization is designing a MAC scheme (or critical servers running GNU/Linux. The security engineer is investigating SELinux but is confused about how to read labeling contexts. The engineer executes the command stat ./secretfile and receives the following output:

Which of the following describes the correct order of labels shown in the output above?
A company with only U S -based customers wants to allow developers from another country to work on the company's website However, the company plans to block normal internet traffic from the other country Which of the following strategies should the company use to accomplish this objective? (Select two).
Which of the following best describes what happens if chain of custody is broken?
A network security engineer is designing a three-tier web architecture that will allow a third-party vendor to perform the following audit functions within the organization's cloud environment
• Review communication between all infrastructure endpoints
• Identify unauthorized and malicious data patterns
• Perform automated, risk-mitigating configuration changes
Which of the following should the network security engineer include in the design to address these requirements?
A security engineer is working for a service provider and analyzing logs and reports from a new EDR solution, which is installed on a small group of workstations. Later that day, another security engineer receives an email from two developers reporting the software being used for development activities is now blocked. The developers have not made any changes to the software being used. Which of the following is the EDR reporting?
A web service provider has just taken on a very large contract that comes with requirements that are currently not being implemented in order to meet contractual requirements, the company must achieve the following thresholds
• 99 99% uptime
• Load time in 3 seconds
• Response time = <1 0 seconds
Starting with the computing environment, which of the following should a security engineer recommend to BEST meet the requirements? (Select THREE)
A cybersecurity engineer analyst a system for vulnerabilities. The tool created an OVAL. Results document as output. Which of the following would enable the engineer to interpret the results in a human readable form? (Select TWO.)
A security architect is reviewing the following proposed corporate firewall architecture and configuration:
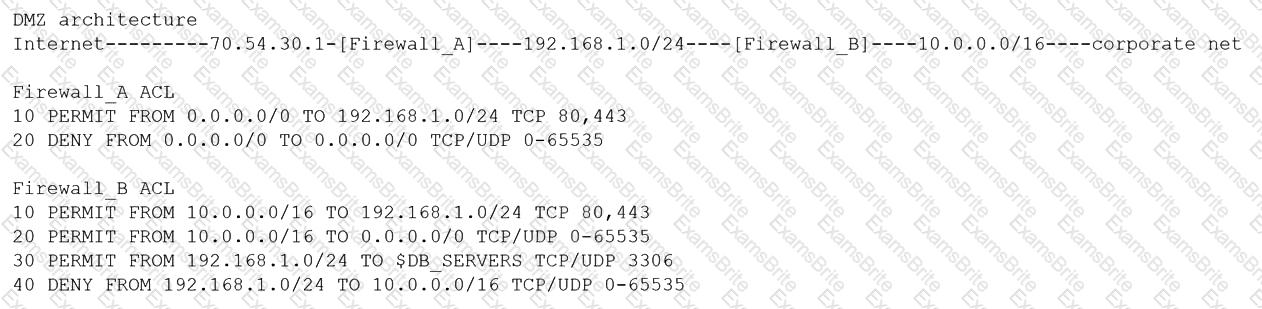
Both firewalls are stateful and provide Layer 7 filtering and routing. The company has the following requirements:
Web servers must receive all updates via HTTP/S from the corporate network.
Web servers should not initiate communication with the Internet.
Web servers should only connect to preapproved corporate database servers.
Employees’ computing devices should only connect to web services over ports 80 and 443.
Which of the following should the architect recommend to ensure all requirements are met in the MOST secure manner? (Choose two.)
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information. Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
Ann, a CIRT member, is conducting incident response activities on a network that consists of several hundred virtual servers and thousands of endpoints and users. The network generates more than 10,000 log messages per second. The enterprise belong to a large, web-based cryptocurrency startup, Ann has distilled the relevant information into an easily digestible report for executive management . However, she still needs to collect evidence of the intrusion that caused the incident. Which of the following should Ann use to gather the required information?
A Chief Information Security Officer (CISO) is concerned that a company's current data disposal procedures could result in data remanence. The company uses only SSDs. Which of the following would be the MOST secure way to dispose of the SSDs given the CISO's concern?
A networking team was asked to provide secure remote access to all company employees. The team decided to use client-to-site VPN as a solution. During a discussion, the Chief Information Security Officer raised a security concern and asked the networking team to route the Internet traffic of remote users through the main office infrastructure. Doing this would prevent remote users from accessing the Internet through their local networks while connected to the VPN.
Which of the following solutions does this describe?
The Chief information Officer (CIO) asks the system administrator to improve email security at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the boar’s concerns for this email migration?
A business wants to migrate its workloads from an exclusively on-premises IT infrastructure to the cloud but cannot implement all the required controls. Which of the following BEST describes the risk associated with this implementation?
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive Pll and identity information, such as passport numbers. The SaaS CRM system does not meet the organization's current security standards. The assessment identifies the following:
1- There will be a $20,000 per day revenue loss for each day the system is delayed going into production.
2- The inherent risk is high.
3- The residual risk is low.
4- There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization's requirements?
A security team received a regulatory notice asking for information regarding collusion and pricing from staff members who are no longer with the organization. The legal department provided the security team with a list of search terms to investigate.
This is an example of:
A company is looking for a solution to hide data stored in databases. The solution must meet the following requirements:
Which of the following techniques should be used?
A security analyst is reviewing the following output:

Which of the following would BEST mitigate this type of attack?
An organization is implementing a new identity and access management architecture with the following objectives:
Supporting MFA against on-premises infrastructure
Improving the user experience by integrating with SaaS applications
Applying risk-based policies based on location
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
A company publishes several APIs for customers and is required to use keys to segregate customer data sets.
Which of the following would be BEST to use to store customer keys?
A company’s claims processed department has a mobile workforce that receives a large number of email submissions from personal email addresses. An employees recently received an email that approved to be claim form, but it installed malicious software on the employee’s laptop when was opened.
An organization is running its e-commerce site in the cloud. The capacity is sufficient to meet the organization's needs throughout most of the year, except during the holidays when the organization plans to introduce a new line of products and expects an increase in traffic. The organization is not sure how well its products will be received. To address this issue, the organization needs to ensure that:
* System capacity is optimized.
* Cost is reduced.
Which of the following should be implemented to address these requirements? (Select TWO).
An administrator at a software development company would like to protect the integrity of the company's applications with digital signatures. The developers report that the signing process keeps failing on all applications. The same key pair used for signing, however, is working properly on the website, is valid, and is issued by a trusted CA. Which of the following is MOST likely the cause of the
signature failing?
The Chief Security Officer (CSO) requested the security team implement technical controls that meet the following requirements:
* Monitors traffic to and from both local NAS and cloud-based file repositories
* Prevents on-site staff who are accessing sensitive customer Pll documents on file repositories from accidentally or deliberately sharing sensitive documents on personal Saa$S solutions
* Uses document attributes to reduce false positives
* Is agentless and not installed on staff desktops or laptops
Which of the following when installed and configured would BEST meet the CSO's requirements? (Select TWO).
A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that
the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
A security architect recommends replacing the company’s monolithic software application with a containerized solution. Historically, secrets have been stored in the application's configuration files. Which of the following changes should the security architect make in the new system?
A security architect Is analyzing an old application that is not covered for maintenance anymore because the software company is no longer in business. Which of the following techniques should have been Implemented to prevent these types of risks?
A company created an external, PHP-based web application for its customers. A security researcher reports that the application has the Heartbleed vulnerability. Which of the following would BEST resolve and mitigate the issue? (Select TWO).
A CSP, which wants to compete in the market, has been approaching companies in an attempt to gain business. The CSP is able to provide the same uptime as other CSPs at a markedly reduced cost. Which of the following would be the MOST significant business risk to a company that signs a contract with this CSP?
A client is adding scope to a project. Which of the following processes should be used when requesting updates or corrections to the client's systems?
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an ОТ and IT environment?
A security analyst is researching containerization concepts for an organization. The analyst is concerned about potential resource exhaustion scenarios on the Docker host due to a single application that is overconsuming available resources.
Which of the following core Linux concepts BEST reflects the ability to limit resource allocation to containers?
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

The security engineer looks at the UTM firewall rules and finds the following:
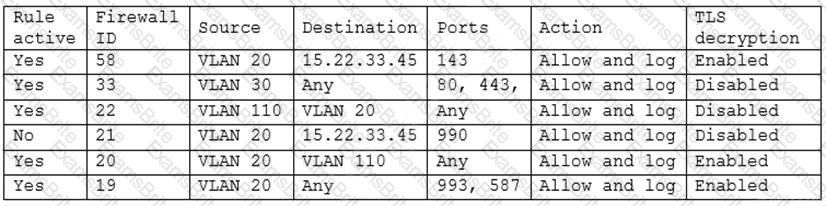
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
A security analyst is performing a vulnerability assessment on behalf of a client. The analyst must define what constitutes a risk to the organization.
Which of the following should be the analyst’s FIRST action?
Which of the following are risks associated with vendor lock-in? (Choose two.)
A company has hired a security architect to address several service outages on the endpoints due to new malware. The Chief Executive Officer’s laptop was impacted while working from home. The goal is to prevent further endpoint disruption. The edge network is protected by a web proxy.
Which of the following solutions should the security architect recommend?
A threat hunting team receives a report about possible APT activity in the network.
Which of the following threat management frameworks should the team implement?
A security engineer was auditing an organization’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
While investigating a security event, an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware.
Which of the following is the NEXT step the analyst should take after reporting the incident to the management team?
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company’s availability requirements. During a postmortem analysis, the following issues were highlighted:
1. International users reported latency when images on the web page were initially loading.
2. During times of report processing, users reported issues with inventory when attempting to place orders.
3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
Which of the following is the MOST important security objective when applying cryptography to control messages that tell an ICS how much electrical power to output?
A security analyst notices a number of SIEM events that show the following activity:
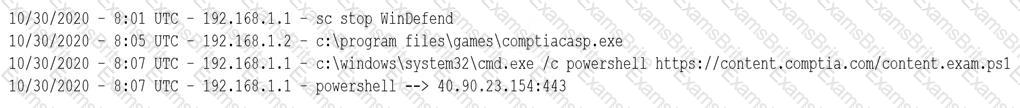
Which of the following response actions should the analyst take FIRST?
A vulnerability analyst identified a zero-day vulnerability in a company’s internally developed software. Since the current vulnerability management system does not have any checks for this vulnerability, an engineer has been asked to create one.
Which of the following would be BEST suited to meet these requirements?
A Chief Information Officer is considering migrating all company data to the cloud to save money on expensive SAN storage.
Which of the following is a security concern that will MOST likely need to be addressed during migration?
A company hired a third party to develop software as part of its strategy to be quicker to market. The company’s policy outlines the following requirements:
https://i.postimg.cc/8P9sB3zx/image.png
The credentials used to publish production software to the container registry should be stored in a secure location.
Access should be restricted to the pipeline service account, without the ability for the third-party developer to read the credentials directly.
Which of the following would be the BEST recommendation for storing and monitoring access to these shared credentials?