Don’t think select one of your desired Cisco exam from the list below:
If you are thinking to be a Cisco IT professional in any Cisco Certification, you must select related exam course and start training. There is much competition in an IT industry. Many candidates select more than one Cisco certifications but the serious one can get success. Once you possess a skill like any Cisco Certification you will be able to get a good job. You will find difficulties in preparing Cisco Certification but remember if you got success you will get good path towards income. Success in any given Cisco Certification exam ensures you a right path. So don’t delay, just choose the right Cisco Certification track and attempt the exam with our best Cisco Exam Prep Kit powered by ExamsBrite.com. We wish you best of luck in Success of your Cisco Certification Exams.
Account Manager Certifications
IoT Sales Fundamentals Exam
IoT Connected Safety and Security Account Manager
IoT Manufacturing Account Manager
Express Security for Account Managers (ESAM)
Introduction to Cisco Sales
Cisco IoT Essentials for Account Managers
Cisco IoT Advantage for Account Managers (IOTAAM)
Additional Online Exams Certifications
Securing Cisco Networks with Sourcefire FireAMP Endpoints
Securing Cisco Networks with Sourcefire IPS
Cisco Application Centric Infrastructure for Field Engineers Exam
AppDynamics Certified Associate Certifications
Cisco AppDynamics Associate Performance Analyst(CAAPA)
Cisco AppDynamics Associate Administrator (CAAA)
AppDynamics Certified Implementation Certifications
Cisco AppDynamics Professional Implementer(CAPI)
Architecture Systems Engineer Certifications
Cisco Enterprise Networks SDA, SDWAN and ISE Exam for System Engineers
Cisco Certified Design Expert Practical Exam
Cisco Certified Design Expert (CCDE v3.1)
Administering Cisco Contact Center Enterprise (CCEA)
Advanced Administration and Reporting of Contact Center Enterprise (CCEAAR)
Implementing Cisco Contact Center Enterprise Chat and Email (CCECE)
Cisco Contact Center Enterprise Implementation and Troubleshooting
Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
CCNP Collaboration Certifications
IoT Connected Factory for Systems Engineers Exam
Implementing Cisco Collaboration Applications (CLICA)
Implementing Cisco Advanced Call Control and Mobility Services (CLACCM)
Implementing Cisco Collaboration Cloud and Edge Solutions (300-820 CLCEI)
Automating Cisco Collaboration Solutions (CLAUTO)
Implementing Cisco Collaboration Core Technologies (350-801 CLCOR)
CCNP Data Center Certifications
Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
Designing Cisco Data Center Infrastructure for Traditional and AI Workloads
Troubleshooting Cisco Data Center Infrastructure (300-615 DCIT)
Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
Automating Cisco Data Center Solutions (DCAUTO)
Implementing Cisco Data Center Core Technologies (350-601 DCCOR)
Implementing Cisco Application Centric Infrastructure - Advanced (DCACIA)
CCNP Enterprise Certifications
Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI)
Implementing Cisco SD-WAN Solutions (300-415 ENSDWI)
Designing Cisco Enterprise Networks (ENSLD)
Designing Cisco Enterprise Wireless Networks (ENWLSD)
Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
Automating Cisco Enterprise Solutions (ENAUTO)
Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
Designing and Implementing Cloud Connectivity (ENCC)
Designing and Implementing Enterprise Network Assurance(300-445 ENNA)
CCNP Security Certifications
Securing Networks with Cisco Firepower (300-710 SNCF)
Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE)
Securing Email with Cisco Email Security Appliance (300-720 SESA)
Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
Implementing Secure Solutions with Virtual Private Networks (SVPN)
Automating and Programming Cisco Security Solutions (300-735 SAUTO)
Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT)
Designing Cisco Security Infrastructure (300-745 SDSI) v1.0
CCNP Service Provider Certifications
Implementing Cisco Service Provider Advanced Routing Solutions
Implementing Cisco Service Provider VPN Services (300-515 SPVI)
Automating and Programming Cisco Service Provider Solutions (300-535 SPAUTO)
Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
Designing and Implementing Cisco Service Provider Cloud Network Infrastructure (SPCNI v1.0)
Cisco Certified Support Technician (CCST) Networking Exam
Cisco Certified Support Technician (CCST) IT Support
Cisco Certified Support Technician Networking Exam
Cisco Certified Support Technician (CCST) Cybersecurity
CCT Routing and Switching Certifications
Channel Partner Program Certifications
Application Centric Infrastructure Support Representative
Cisco AI Technical Practitioner (AITECH) Certifications
Cisco AI Technical Practitioner
Cisco Certification Certifications
Enterprise Mobility Essentials for Account Managers
Implementing and Administering the FlexPod Solution v2.0 (FPIMPADM)
Interconnecting Cisco Networking Devices
Understanding Cisco Cybersecurity Fundamentals - Invitation Only
Implementing Cisco Cybersecurity Operations - Invitation Only
Cisco IoT Essentials for Account Managers
Cisco IoT Advantage for Systems Engineers
Cisco IoT Advantage for Systems Engineers (IOTASE)
Implementing Cisco Network Security v3.0
Designing Cisco Application Centric Infrastructure
Cisco Certified DevNet Associate Certifications
DevNet Associate (DEVASC)
Cisco Certified DevNet Professional Certifications
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
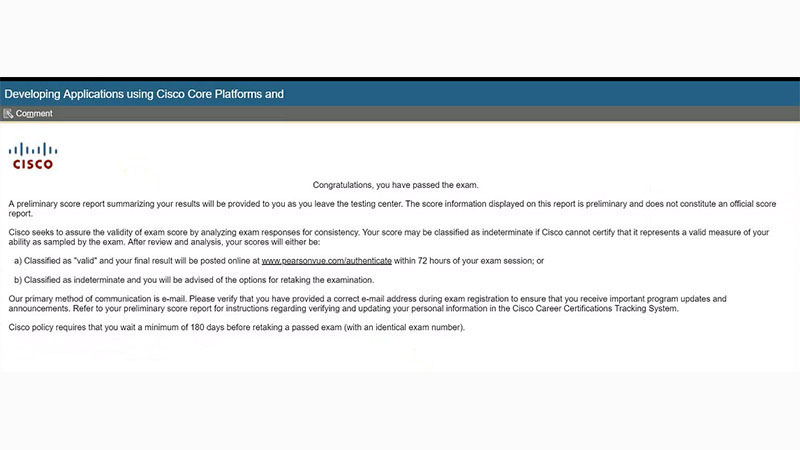
Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
Cisco Certified Field Technician (CCT) Certifications
Supporting Cisco Devices for Field Technicians (FLDTEC)
Cisco Certified Specialist Certifications
Implementing Cisco Application Centric Infrastructure - Advanced (600-660 DCACIA)
Cisco Certified Specialist - Threat Hunting and Defending Certifications
Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
Cisco Engineer SMBEN Certifications
SMB Specialization for Engineers
Cisco Meraki Solutions Specialist Certifications
Engineering Cisco Meraki Solutions (ECMS) v2.2
Cisco Other Certification Certifications
LCSARS Cisco Lifecycle Services Advanced Routing and Switching
Cisco Small and Medium Business Sales Specialization Certifications
Cisco Small and Medium Business Sales
Cisco Specialist Certifications
Cisco Express Foundation for Field Engineers
Cisco Express Foundation for Account Managers (CXFA) Exam
Implementing Cisco Connected Physical Security 1
SMB Specialization for Account Managers
Cisco Application Centric Infrastructure for Account Managers
Cisco Application Centric Infrastructure for System Engineers
Business Edition 6000 for Sales Engineers
Deploying Cisco Unified Contact Center Express
Advanced Security Architecture for Account Managers
Cisco Renewals Manager (700-805 CRM)
Cisco Security Architecture for Account Managers
Cisco Environmental Sustainability Overview(CESO)
Environmental Sustainability Practice-Building(ESPB)
Cisco Environmental Sustainability Fundamentals - Stage 1
Cisco Environmental Sustainability Practice-Building - Stage 2
CyberOps Associate Certifications
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
CyberOps Professional Certifications
Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Performing CyberOps Using Core Security Technologies (CBRCOR)
Digital Transformation Specialist Certifications
Cisco Customer Success Manager
Cisco Networking: On-Premise and Cloud Solutions
Express Specialization - SMB Track Certifications
Cisco SMB Product and Positioning Technical Overview
Cisco Small and Medium Business Engineer (SMBE)
Field Engineer Certifications
SP Optical Technology Field Engineer Representative
Video Infrastructure Implementation (VII)
Designing Cisco Enterprise Networks (ENDESIGN) exam
Sales Engineers Certifications
Enterprise Mobility Essentials for Sales Engineers
Cisco Collaboration SaaS Authorization for PreSales Engineer CSaaSSE
Systems Engineer Certifications
Cisco Service Provider Routing Field Engineer Exam
Security Architecture for Systems Engineer (SASE)
Cisco Video Infrastructure Design
Cisco Data Center Unified Computing Infrastructure Design (DCICUC)
Cisco HyperFlex for Systems Engineers
Cisco IoT Essentials for System Engineers(IOTSE)
Wireless LAN Certifications
Advanced Routing and Switching for Field Engineers – ARSFE
Implementing Cisco Connected Physical Security 2 Exam
Cisco Routing and Switching Solutions Specialist
Advanced Routing and Switching for Account Managers – ARSAM