
Securing Networks with Cisco Firepower (300-710 SNCF)
Last Update Feb 28, 2026
Total Questions : 385
We are offering FREE 300-710 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 300-710 free exam questions and then go for complete pool of Securing Networks with Cisco Firepower (300-710 SNCF) test questions that will help you more.



An organization has seen a lot of traffic congestion on their links going out to the internet There is a Cisco Firepower device that processes all of the traffic going to the internet prior to leaving the enterprise. How is the congestion alleviated so that legitimate business traffic reaches the destination?
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
Which action must be taken on the Cisco FMC when a packet bypass is configured in case the Snort engine is down or a packet takes too long to process?
An engineer is integrating Cisco Secure Endpoint with Cisco Secure Firewall Management Center in high availability mode. Malware events detected by Secure Endpoint must also be
received by Secure Firewall Management Center and public cloud services are used. Which two configurations must be selected on both high availability peers independently? (Choose two.)
Which default action setting in a Cisco FTD Access Control Policy allows all traffic from an undefined application to pass without Snort Inspection?
Which Cisco Rapid Threat Containment mitigation action is enabled by integrating pxGrid Adaptive Network Control with Cisco ISE and Cisco Secure Firewall Management Center?
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two.)
A network engineer is deploying a pair of Cisco Secure Firewall Threat Defense devices managed by Cisco Secure Firewall Management Center tor High Availability Internet access is a high priority for the business and therefore they have invested in internet circuits from two different ISPs. The requirement from the customer Is that Internet access must do available to their user’s oven if one of the ISPs is down. Which two features must be deployed to achieve this requirement? (Choose two.)
Which CLI command is used to control special handling of ClientHello messages?
An administrator configures the interfaces of a Cisco Secure Firewall Threat Defence device in an inline IPS deployment. The administrator completes these actions:
* identifies the device and the interfaces
* sets the interface mode to inline
* enables the interlaces
Which configuration step must the administrator take next to complete the implementation?
Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
A Cisco FTD has two physical interfaces assigned to a BVI. Each interface is connected to a different VLAN on the same switch. Which firewall mode is the Cisco FTD set up to support?
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FTD. Which policy must be configured to accomplish this goal?
An engineer is reviewing a ticket that requests to allow traffic for some devices that must connect to a server over 8699/udp. The request mentions only one IP address, 172.16.18.15, but the requestor asked for the engineer to open the port for all machines that have been trying to connect to it over the last week. Which action must the engineer take to troubleshoot this issue?
An engineer is deploying a Cisco Secure Firewall Management Center appliance. The company must send data to Cisco Secure Network Analytics appliances. Which two actions must the engineer take? (Choose two.)
A network administrator registered a new FTD to an existing FMC. The administrator cannot place the FTD in transparent mode. Which action enables transparent mode?
An analyst is investigating a potentially compromised endpoint within the network and pulls a host report for the endpoint in question to collect metrics and documentation. What information should be taken from this report for the investigation?
An administrator is configuring the interface of a Cisco Secure Firewall Threat Defense device in a passive IPS deployment. The device and interface have been identified. Which set of configuration steps of the administrator take next to complete the implementation?
How should a high-availability pair of Cisco Secure Firewall Threat Defense Virtual appliances be deployed to Cisco Secure Firewall Management Center?
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without affecting traffic flows.
It must also collect data to provide a baseline of unwanted traffic before being reconfigured to drop it. Which Cisco IPS mode meets these requirements?
An engineer attempts to pull the configuration for a Cisco FTD sensor to review with Cisco TAC but does not have direct access to the CU for the device. The CLl for the device is managed by Cisco FMC to which the engineer has access. Which action in Cisco FMC grants access to the CLl for the device?
Refer to the exhibit.
A systems administrator conducts a connectivity test to their SCCM server from a host machine and gets no response from the server. Which action ensures that the ping packets reach the destination and that the host receives replies?
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO. Which feature must be enabled to accomplish this goal?
Which component simplifies incident investigation with Cisco Threat Response?
A network administrator notices that SI events are not being updated The Cisco FTD device is unable to load all of the SI event entries and traffic is not being blocked as expected. What must be done to correct this issue?
A network engineer must configure the cabling between a Cisco Secure Firewall Threat Defense appliance and a network so the Secure Firewall Threat Defense appliance performs inline to analyze and tune generated intrusion events before going live. Which Secure Firewall Threat Defense interface mode must the engineer use?
An organization has a Cisco IPS running in inline mode and is inspecting traffic for malicious activity. When traffic is received by the Cisco IRS, if it is not dropped, how does the traffic get to its destination?
An engineer must deny ICMP traffic to the networks of separate departments that use Cisco Secure Firewall Management Center. The engineer must use the same object on the relevant device for each network. What must be configured in Secure Firewall Management Center?
An administrator is adding a new URL-based category feed to the Cisco FMC for use within the policies. The intelligence source does not use STIX. but instead uses a .txt file format. Which action ensures that regular updates are provided?
An engineer must define a URL object on Cisco FMC. What is the correct method to specify the URL without performing SSL inspection?
A network engineer is tasked with minimising traffic interruption during peak traffic limes. When the SNORT inspection engine is overwhelmed, what must be configured to alleviate this issue?
With Cisco FTD software, which interface mode must be configured to passively receive traffic that passes through the appliance?
Which communication is blocked from the bridge groups when multiple are configured in transparent mode on a Cisco Secure Firewall Threat Defense appliance?
A security analyst must create a new report within Cisco FMC to show an overview of the daily attacks, vulnerabilities, and connections. The analyst wants to reuse specific dashboards from other reports to create this consolidated one. Which action accomplishes this task?
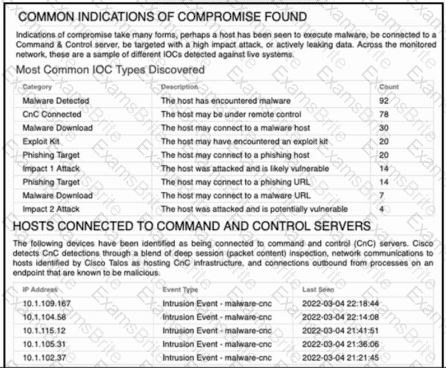
Refer to the exhibit. An engineer analyzes a Network Risk Report from Cisco Secure Firewall Management Center. What should the engineer recommend implementing to mitigate the risk?
An analyst is reviewing the Cisco FMC reports for the week. They notice that some peer-to-peer applications are being used on the network and they must identify which poses the greatest risk to the environment. Which report gives the analyst this information?
An engineer must integrate a thud-party security Intelligence teed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2 3 and has 8 GB of memory. Which two actions must be taken to implement Throat Intelligence Director? (Choose two.)
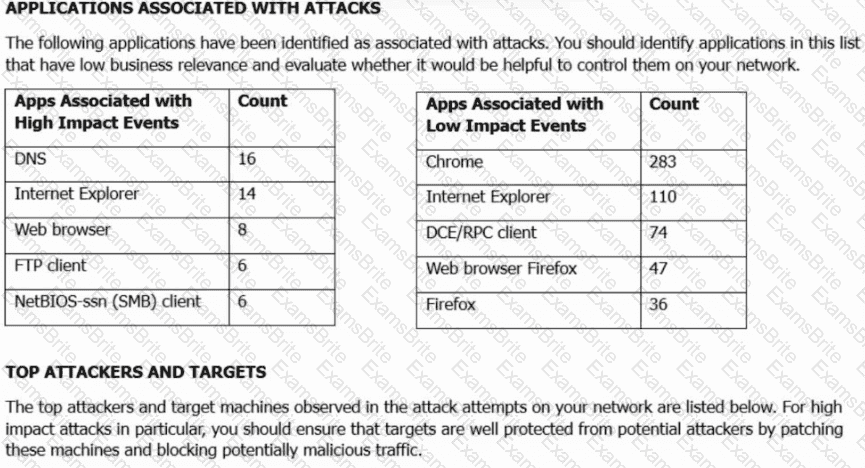
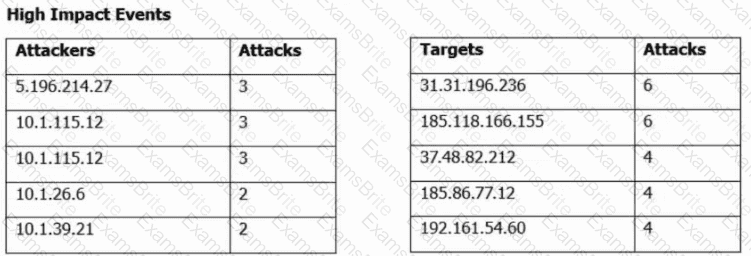
Refer to the exhibit. A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval. Which action must the security engineer take based on this Attacks Risk Report?
A network administrator is trying to configure a previously created file policy on a new access policy. Which action must the administrator take before applying the file policy?
A network administrator is implementing an active/passive high availability Cisco FTD pair.
When adding the high availability pair, the administrator cannot select the secondary peer.
What is the cause?
An engineer defines a new rule while configuring an Access Control Policy. After deploying the policy, the rule is not working as expected and the hit counters associated with the rule are showing zero. What is causing this error?
An engineer is configuring two new Cisco FTD devices to replace the existing high availability firewall pair in a highly secure environment. The information exchanged between the FTD devices over the failover link must be encrypted. Which protocol supports this on the Cisco FTD?
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
A network administrator is troubleshooting access to a website hosted behind a Cisco FTD device External clients cannot access the web server via HTTPS The IP address configured on the web server is 192 168 7.46 The administrator is running the command capture CAP interface outside match ip any 192.168.7.46 255.255.255.255 but cannot see any traffic in the capture Why is this occurring?
A network administrator is configuring Snort inspection policies and is seeing failed deployment messages in Cisco FMC. What information should the administrator generate for Cisco TAC to help troubleshoot?
An engineer needs to configure remote storage on Cisco FMC. Configuration backups must be available from a secure location on the network for disaster recovery. Reports need to back up to a shared location that auditors can access with their Active Directory logins. Which strategy must the engineer use to meet these objectives?
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
The administrator notices that there is malware present with an .exe extension and needs to verify if any of the systems on the network are running the executable file. What must be configured within Cisco AMP for Endpoints to show this data?
Which command is entered in the Cisco FMC CLI to generate a troubleshooting file?
A network administrator is configuring an FTD in transparent mode. A bridge group is set up and an access policy has been set up to allow all IP traffic. Traffic is not passing through the FTD. What additional configuration is needed?
Network traffic coining from an organization's CEO must never be denied. Which access control policy configuration option should be used if the deployment engineer is not permitted to create a rule to allow all traffic?
An engineer plans to reconfigure an existing Cisco FTD from transparent mode to routed mode. Which additional action must be taken to maintain communication Between me two network segments?
A network administrator is trying to configure an access rule to allow access to a specific banking site over HTTPS. Which method must the administrator use to meet the requirement?
An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment?
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
A network engineer wants to disable the HTTP response page and interactive blocking of the entire access control policy in Cisco Secure Firewall Management Center. What must be
selected in Block Response Page and Interactive Block Response Page?
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (Choose two.)
An engineer Is configuring a Cisco FTD device to place on the Finance VLAN to provide additional protection tor company financial data. The device must be deployed without requiring any changes on the end user workstations, which currently use DHCP lo obtain an IP address. How must the engineer deploy the device to meet this requirement?
When do you need the file-size command option during troubleshooting with packet capture?
An engineer is creating an URL object on Cisco FMC How must it be configured so that the object will match for HTTPS traffic in an access control policy?
While configuring FTD, a network engineer wants to ensure that traffic passing through the appliance does not require routing or Vlan rewriting. Which interface mode should the engineer implement to accomplish this task?
An administrator is creating interface objects to better segment their network but is having trouble adding interfaces to the objects. What is the reason for this failure?
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?
Remote users who connect via Cisco AnyConnect to the corporate network behind a Cisco FTD device report that they get no audio when calling between remote users using their softphones. These same users can call internal users on the corporate network without any issues. What is the cause of this issue?
An engineer wants to connect a single IP subnet through a Cisco FTD firewall and enforce policy. There is a requirement to present the internal IP subnet to the outside as a different IP address. What must be configured to meet these requirements?
A network engineer implements a new Cisco Firepower device on the network to take advantage of its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire How should this be implemented?
Refer to the exhibit.
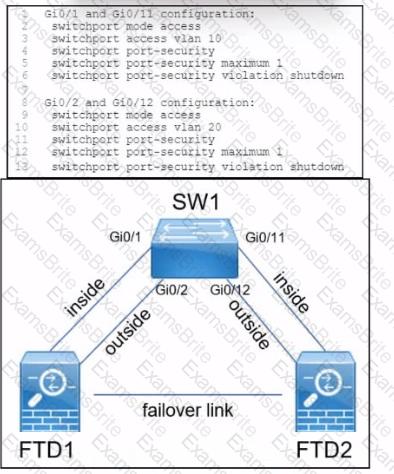
A company is deploying a pair of Cisco Secure Firewall Threat defence devices named FTD1 and FTD2. FTD1 and FTD2 have been configured as an active/standby pair with a failover link but without a stateful link. What must be implemented next to ensure that users on the internal network still communicate with outside devices if FTD1 fails?
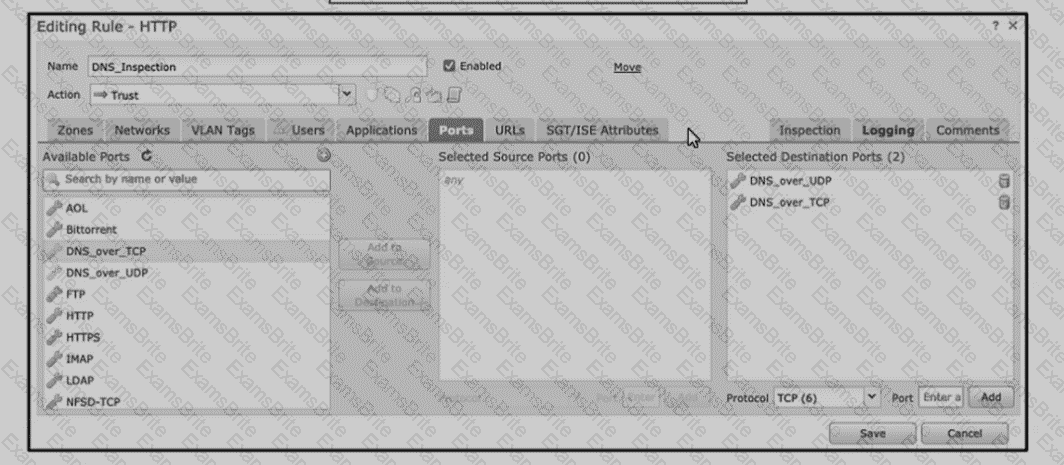
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
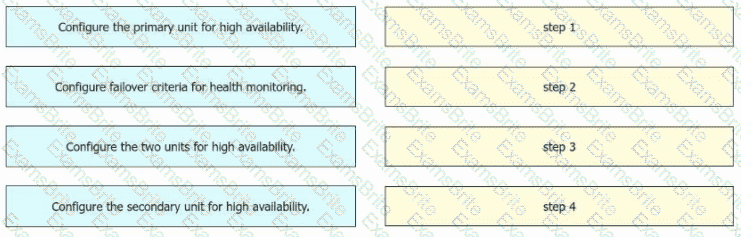
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances. Drag and drop the configuration steps from the left into the sequence on the right.

Refer to the exhibit. Users attempt to connect to numerous external resources on various TCP ports. If the users mistype the port, their connection closes immediately, and it takes more than one minute before the connection is torn down. An engineer manages to capture both types of connections as shown in the exhibit. What must the engineer configure to lower the timeout values for the second group of connections and resolve the user issues?
An engineer must deploy a Cisco FTD device. Management wants to examine traffic without requiring network changes that will disrupt end users. Corporate security policy requires the separation of management traffic from data traffic and the use of SSH over Telnet for remote administration. How must the device be deployed to meet these requirements?
An organization has a compliancy requirement to protect servers from clients, however, the clients and servers all reside on the same Layer 3 network Without readdressing IP subnets for clients or servers, how is segmentation achieved?
A security engineer is adding three Cisco FTD devices to a Cisco FMC. Two of the devices have successfully registered to the Cisco FMC. The device that is unable to register is located behind a router that translates all outbound traffic to the router's WAN IP address. Which two steps are required for this device to register to the Cisco FMC? (Choose two.)
A network administrator is deploying a new Cisco Secure Firewall Threat Defense (FTD) firewall After Cisco Secure FTD is deployed, inside clients nave intermittent connectivity to each other. When … the packet capture on the Secure FTD firewall, the administrator sees that Secure FID is responding to all the AW requests on the inside network. Which action must the network administrator e to resolve the issue''
An engineer is configuring two new Cisco Secure Firewall Threat Defense devices to replace the existing firewalls. Network traffic must be analyzed for intrusion events without impacting the traffic. What must the engineer implement next to accomplish the goal?
A hospital network needs to upgrade their Cisco FMC managed devices and needs to ensure that a disaster recovery process is in place. What must be done in order to minimize downtime on the network?
A network engineer is planning on replacing an Active/Standby pair of physical Cisco Secure Firewall ASAs with a pair of Cisco Secure Firewall Threat Defense Virtual appliances. Which two virtual environments support the current High Availability configuration? (Choose two.)
A network administrator notices that inspection has been interrupted on all non-managed interfaces of a device. What is the cause of this?
A network engineer is configuring URL Filtering on Firepower Threat Defense. Which two port requirements on the Firepower Management Center must be validated to allow communication with the cloud service? (Choose two.)
A network engineer detects a connectivity issue between Cisco Secure Firewall Management Centre and Cisco Secure Firewall Threat Defense Initial troubleshooting indicates that heartbeats and events not being received. The engineer re-establishes the secure channels between both peers Which two commands must the engineer run to resolve the issue? (Choose two.)
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated. Which configuration addresses this concern?
An engineer wants to change an existing transparent Cisco FTD to routed mode.
The device controls traffic between two network segments. Which action is mandatory to allow hosts to reestablish communication between these two segments after the change?
Network users experience issues when accessing a server on a different network segment. An engineer investigates the issue by performing packet capture on Cisco Secure Firewall Threat Defense. The engineer expects more data and suspects that not all the traffic was collected during a 15-minute can’t captured session. Which action must the engineer take to resolve the issue?
What is the advantage of having Cisco Firepower devices send events to Cisco Threat Response via the security services exchange portal directly as opposed to using syslog?
What must be implemented on Cisco Firepower to allow multiple logical devices on a single physical device to have access to external hosts?
An engineer must create an access control policy on a Cisco Secure Firewall Threat Defense device. The company has a contact center that utilizes VoIP heavily, and it is critical that this traffic is not …. by performance issues after deploying the access control policy Which access control Action rule must be configured to handle the VoIP traffic?

A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval. Which action must the security engineer take based on this Attacks Risk Report?
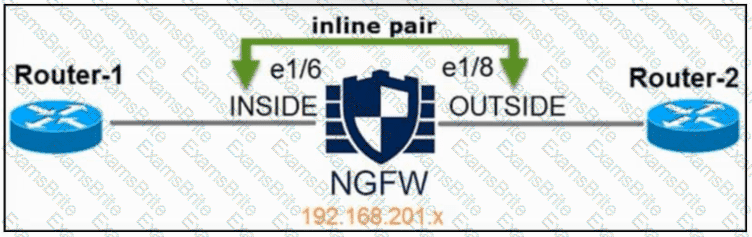
Refer to the exhibit. An engineer is configuring an instance of Cisco Secure Firewall Threat Defense with interfaces in IPS Inline Pair mode. What must be configured on interface e1/6 to accomplish the requirement?
The CEO ask a network administrator to present to management a dashboard that shows custom analysis tables for the top DNS queries URL category statistics, and the URL reputation statistics.
Which action must the administrator take to quickly produce this information for management?
Which action must be taken to configure an isolated bridge group for IRB mode on a Cisco Secure Firewall device?
A network administrator must create an EtherChannel Interface on a new Cisco Firepower 9300 appliance registered with an FMC tor high availability. Where must the administrator create the EtherChannel interface?
An engineer is setting up a new Cisco Secure Firewall Threat Defense appliance to replace the current firewall. The company requests that inline sets be used and that when one interface in
an inline set goes down, the second interface in the inline set goes down. What must the engineer configure to meet the deployment requirements?
An organization is implementing Cisco FTD using transparent mode in the network. Which rule in the default Access Control Policy ensures that this deployment does not create a loop in the network?
A consultant Is working on a project where the customer is upgrading from a single Cisco Firepower 2130 managed by FDM to a pair of Cisco Firepower 2130s managed oy FMC tor nigh availability. The customer wants the configures of the existing device being managed by FDM to be carried over to FMC and then replicated to the additional: device being added to create the high availability pair. Which action must the consultant take to meet this requirement?
An engineer must configure email notifications on Cisco Secure Firewall Management Center. TLS encryption must be used to protect the messages from unauthorized access. The engineer adds the IP address of the mail relay host and must set the port number. Which TCP port must the engineer use?
Which two considerations must be made when deleting and re-adding devices while managing them via Cisco FMC (Choose two).
An engineer is configuring a custom application detector for HTTP traffic and wants to import a file that was provided by a third party. Which type of flies are advanced application detectors creates and uploaded as?
An engineer is configuring Cisco Security Devices by using Cisco Secure Firewall Management Center. Which configuration command must be run to compare the CA certificate bundle on the local system to the latest CA bundle from the Cisco server?
An administrator is attempting to add a Cisco Secure Firewall Threat Defence device to Cisco Secure Firewall Management Center with a password of Cisco0480846211 480846211. The private IP address of the FMC server is 192.168.75.201. Which command must be used in order to accomplish this task?
What is the advantage of having Cisco Firepower devices send events to Cisco Threat response via the security services exchange portal directly as opposed to using syslog?
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
A security engineer must configure policies tor a recently deployed Cisco FTD. The security policy for the company dictates that when five or more connections from external sources are initiated within 2 minutes, there is cause for concern. Which type of policy must be configured in Cisco FMC \z generate an alert when this condition is triggered?
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two.)
How many report templates does the Cisco Firepower Management Center support?
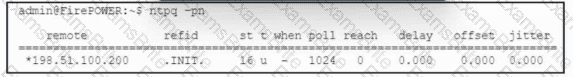
Refer to the exhibit. A security engineer views the health alerts in Cisco Secure Firewall Management Center by using the Health Monitor in the web interface. One of the alerts shows an appliance as critical because the Time Synchronization module status is out of sync. To troubleshoot the issue, the engineer runs the ntpq command in Secure Firewall Management Center. The output is shown in the exhibit. Which action must the security engineer take next to resolve the issue?
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighbouring Cisco devices or use multicast in their environment. What must be done to resolve this issue?