
Implementing Cisco SD-WAN Solutions (300-415 ENSDWI)
Last Update Mar 10, 2026
Total Questions : 446
We are offering FREE 300-415 Cisco exam questions. All you do is to just go and sign up. Give your details, prepare 300-415 free exam questions and then go for complete pool of Implementing Cisco SD-WAN Solutions (300-415 ENSDWI) test questions that will help you more.



A network administrator is configuring Qos on a vEdge 5000 router and needs to enable it on the transport side interface. Which policy setting must be selected to accomplish this goal?
An engineer wants to track tunnel characteristics within an SLA-based policy for convergence. Which policy configuration will achieve this goal?
Which port is used for vBond under controller certificates if no alternate port is configured?
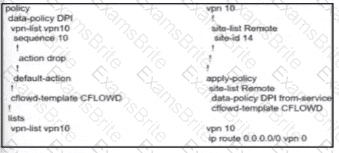
Which configuration allows VPN 10 traffic to have direct internet access locally from the WAN Edge device?
A)

B)

C)
D)

Which two requirements must be met for DNS inspection when integrating with cisco umbrella? (Choose two)
Which two protocols are supported for software image delivery when images are hosted on a remote server? (Choose two.)
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
Which component of the Cisco SD-WAN control plane architecture facilitates the storage of certificates and configurations for network components?
Which device information is requited on PNP/ZTP to support the zero-touch onboarding process?
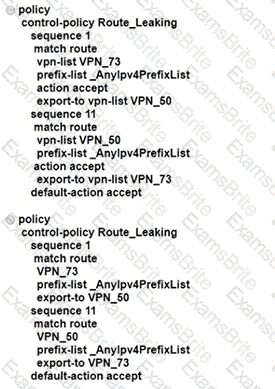
An enterprise has several sites with multiple VPNs that are isolated from each other A new requirement came where users in VPN 73 must be able to talk to users in VPN 50 Which configuration meets this requirement?
A customer wants to use AWS for Cisco SD-WAN laaS services by deploying virtual SD-WAN routers in a transit AWS VPC The transit VPC then connects via site-to-site IPsec tunnels to an AWS transit gateway Which transit VPC connects via site-to-site IPsec tunnels to an AWS transit gateway?
Which component of the Cisco SD-WAN secure extensible network provides a single pane of glass approach to network monitoring and configuration?
WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offse range?
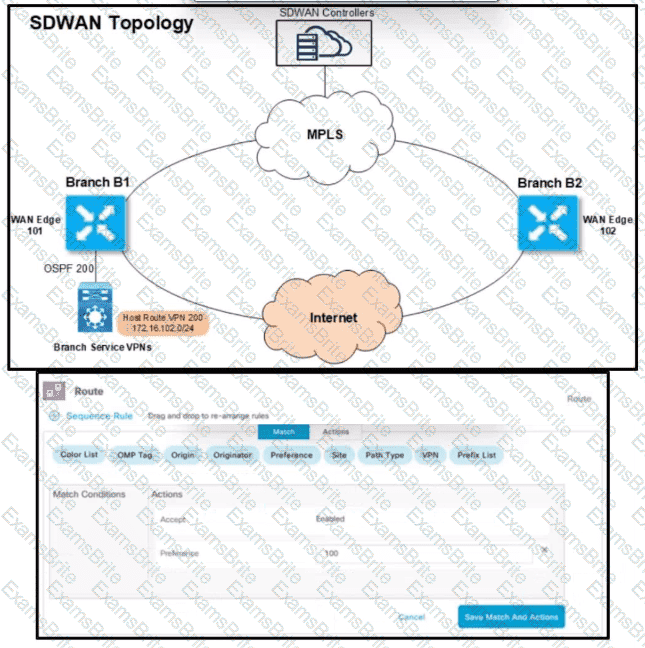
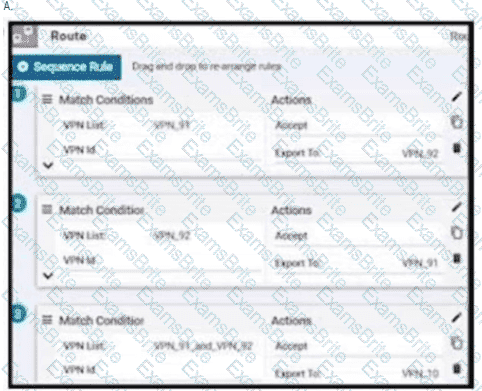
Refer to the exhibit. An engineer must configure the Overlay Management Protocol route preference so that when B2 tries to reach host routes advertised by B1 it always chooses the MPLS circuit. Which two match conditions must be configured to accomplish this task? (Choose two.)
When redistribution is configured between OMP and BGP at two Data Center sites that have Direct Connection interlink, which step avoids learning the same routes on WAN Edge routers of the DCs from LAN?
A company deploys a Cisco SD-WAN solution but has an unstable Internet connection. When the link to vSmart comes back up, the WAN Edge router routing table is not refreshed, and some traffic to the destination network is dropped. The headquarters is the hub site, and it continuously adds new sites to the SD-WAN network. An engineer must configure route refresh between WAN Edge and vSmart within 2 minutes. Which configuration meets this requirement?
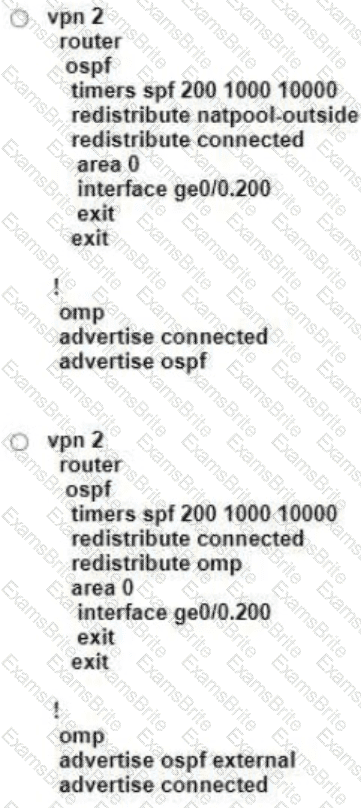
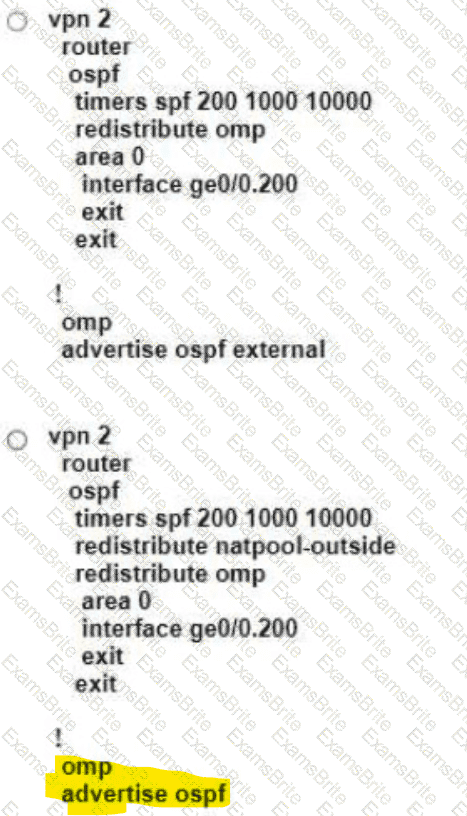
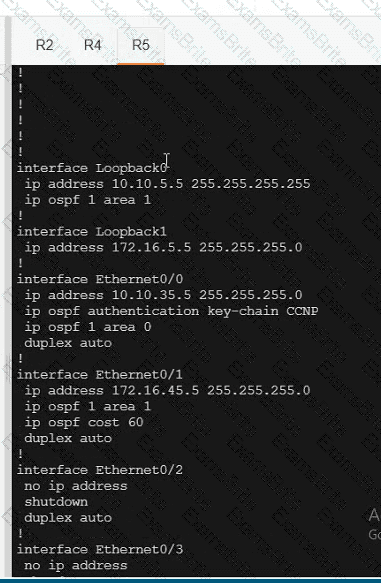
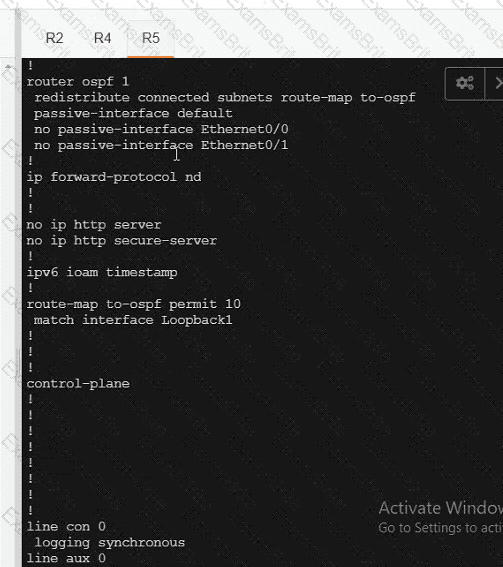
Refer to the exhibit Which configuration ensures that OSPF routes learned from Site2 are reachable at Sitel and vice-versa?
Which type of connection is created between a host VNet and a transit VNet when configuring Cloud OnRamp for laaS?
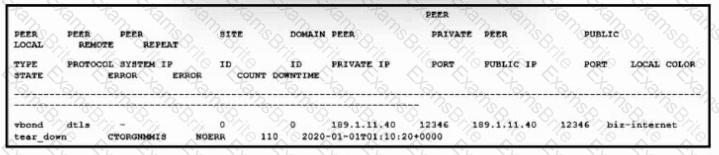
Refer to the exhibit. Which issue is shown, and which action must an engineer take to resolve the issue?
Which attributes are configured to uniquely Identify and represent a TLOC route?
Which cloud based component in cisco SD-WAN is responsible for establishing a secure connection to each WAN edge router and distributes routers and policy information via omp?
Drag and drop the security terminologies from the left onto the PCI-compliant network features and devices on the right.
Which two sets of identifiers does OMP carry when it advertises TLOC routes between WAN Edge routers? (Choose two.)
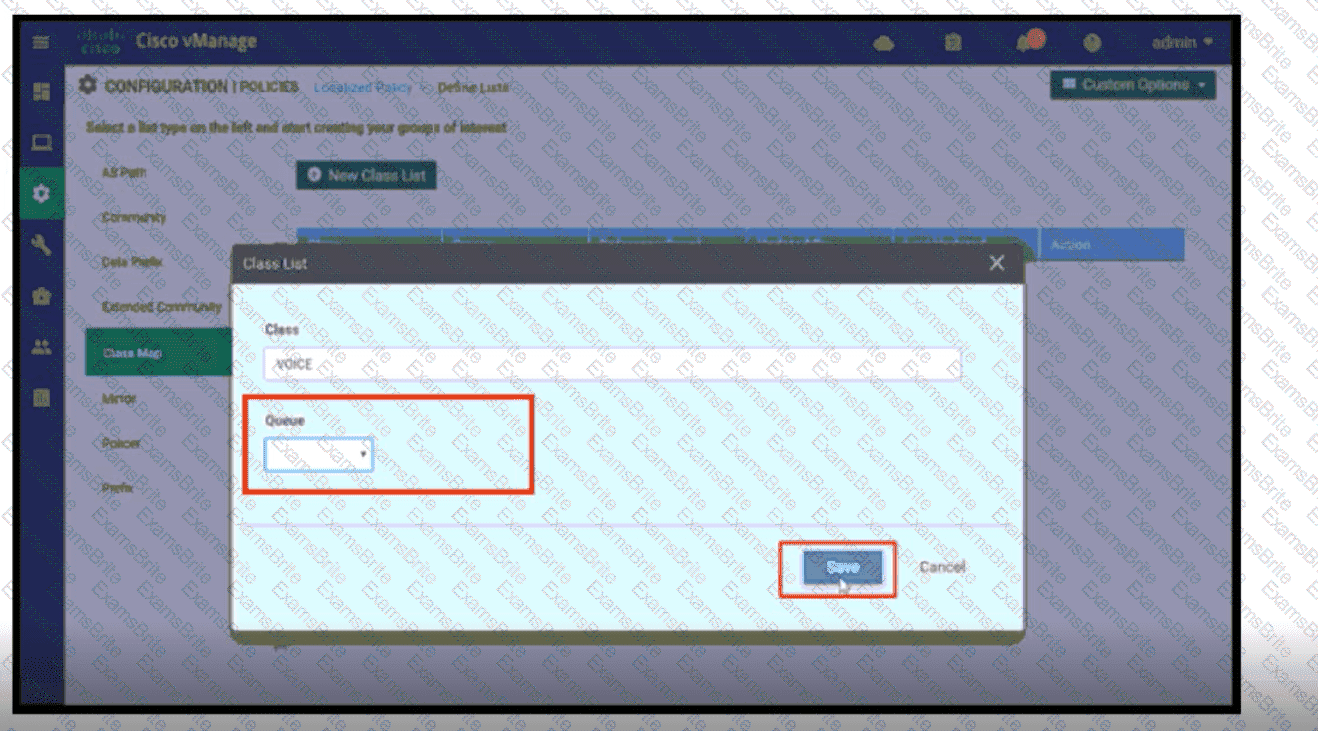
Refer to the exhibit. A network administrator is setting the queueing value for voice traffic for one of the WAN Edge routers using vManager GUI. Which queue value must be set to accomplish this task?
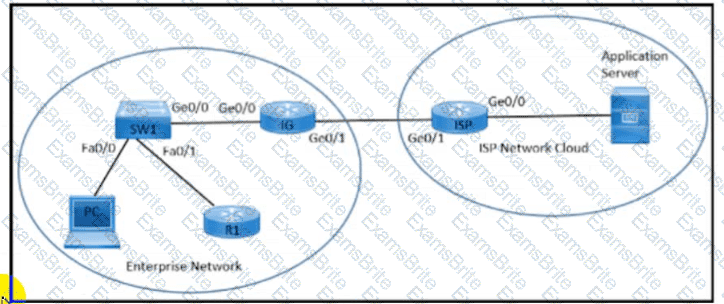
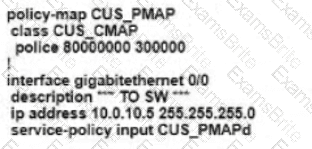
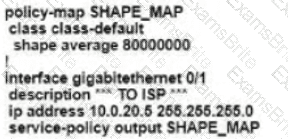
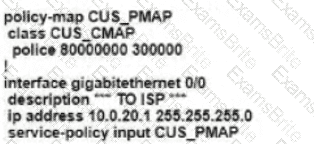
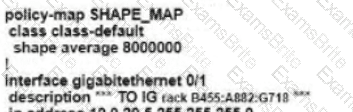
Refer to the exhibit. An enterprise network is connected with an ISP network on an 80 Mbps bandwidth link. The network operation team observes 100 Mbps traffic on the 1Gig-ISP link during peak hours Which configuration provides bandwidth control to avoid traffic congestion during peak hours?
A)
B)
C)
D)
What is the function of the AppNav Controller in the Cisco SD-WAN AppNav solution?
An engineer modifies a data policy for DIA in VPN 67. The location has two Internet-bound circuits. Only the web browsing traffic must be admitted for DIA. without further discrimination about which transport to use.
Here is the existing data policy configuration:

Which policy configuration sequence meets the requirements?
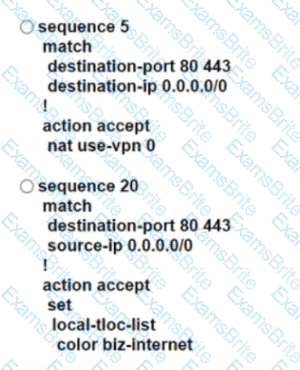
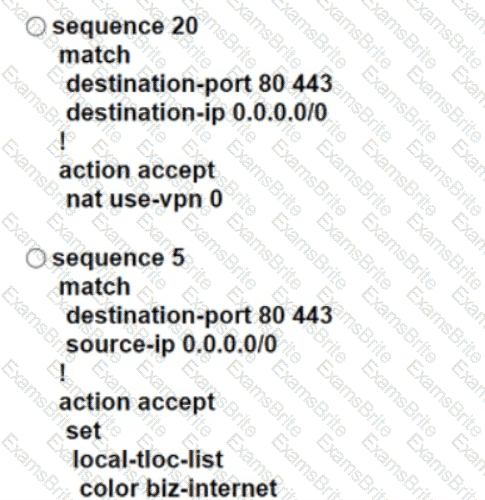
Refer to the exhibit.

Which shaping-rate does the engineer use to shape traffic at 9 Mbps?
Refer to the exhibit.
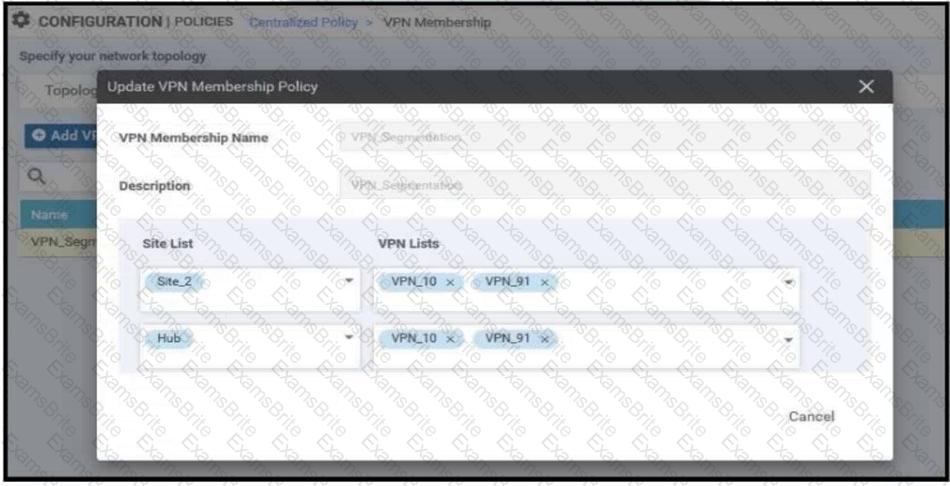
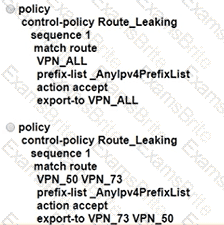
An enterprise has hub and spoke topology where it has several VPNs. An engineer must allow users in VPN91 to reach users in VPN92 and VPN10 to reach VPN91 and VPN92. Which configuration meets these requirements?
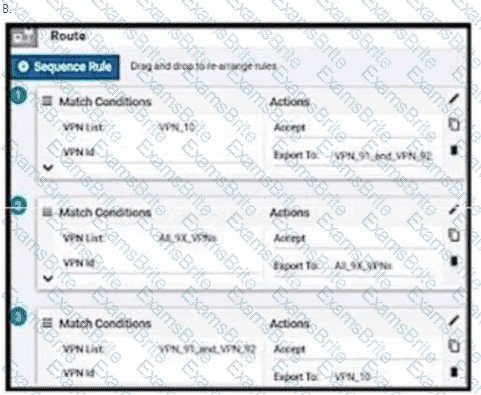
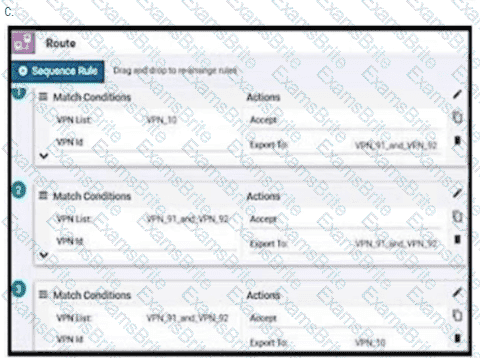
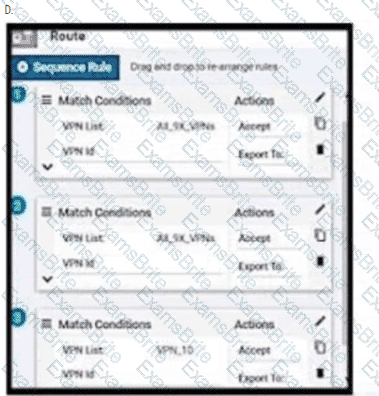
Which plane assists in the automatic onboarding of the SD-WAN routers into the SD-WAN overlay?
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.)
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
Refer to the exhibit.
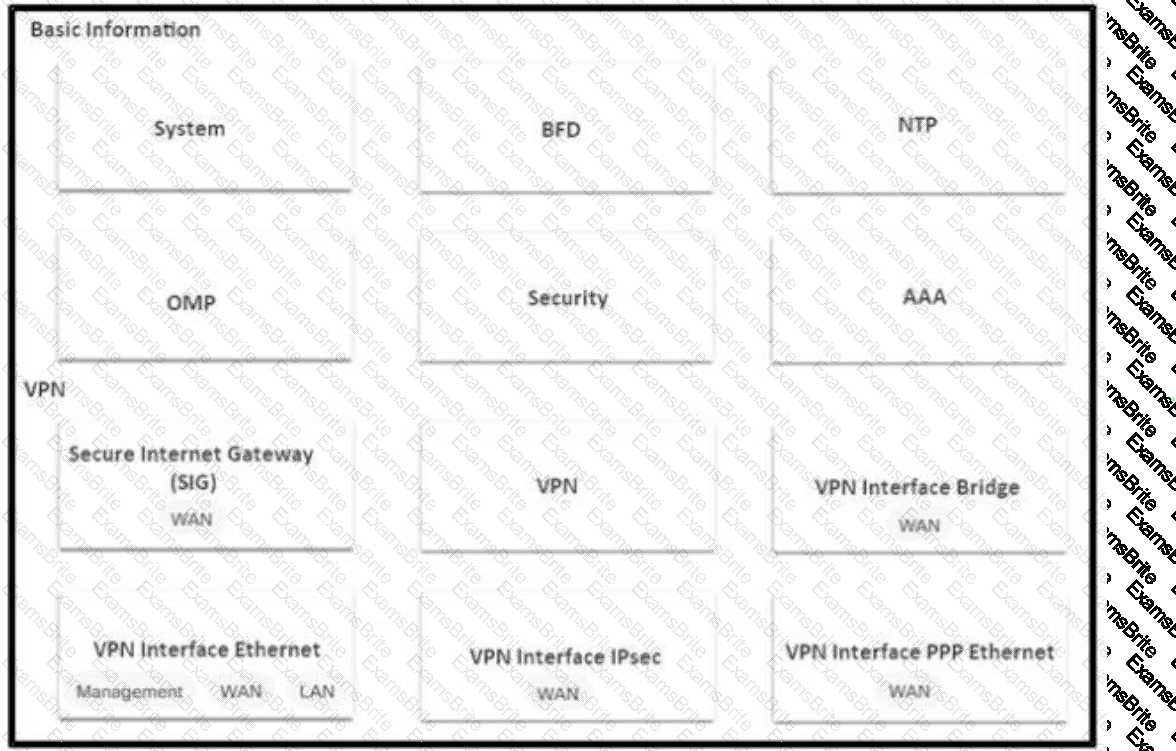
An SD-WAN customer has 23 sites connected to its hub site, where a pair of WAN Edge devices and controllers are placed. All other branches have a single WAN Edge device connected to multiprotocol label switching (MPLS) and public internet circuits. An engineer must configure application-aware routing for a branch that has MPLS and public internet circuits provisioned using feature templates. The requirements for application-aware routing are:
All types of traffic prefers using public-internet circuit.
If the average latency reaches 100 ms, jitter 85 ms, and packet loss 5%, then video and voice traffic switches to the MPLS circuit.
Which feature template must be configured or modified in addition to configuring a centralized policy?
An engineer wants to change the configuration of the certificate authorization mode from manual to automated. Which GUI selection will accomplish this?
What is the minimum Red Hat Enterprise Linux operating system requirement for a Cisco SD-WAN controller deployment via KVM?
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two.)
Which Cisco router provides a distributed multicore architecture optimized for SD-WAN branch support?
Which feature delivers traffic to the Cisco Umbrella SIG cloud from a Cisco SD-WAN domain?
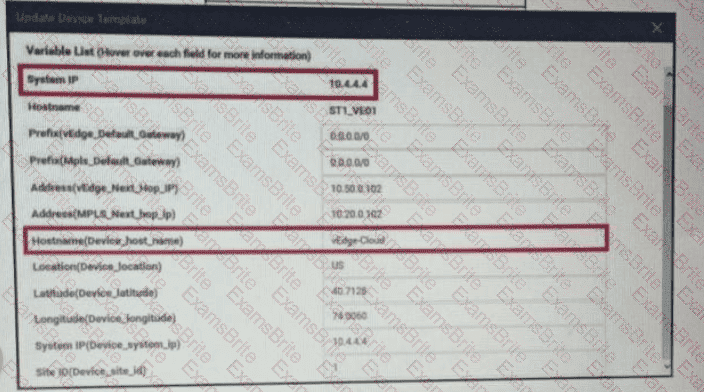
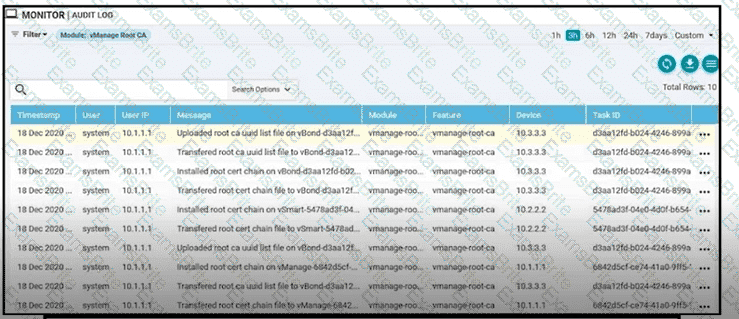
Refer to the exhibit. vManage logs are available for the past few months. A device name change deployed mistakenly at a critical site. How is the device name change tracked by operation and design teams?
A)
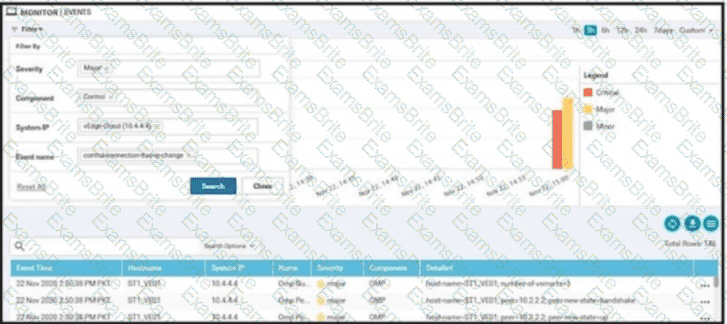
B)
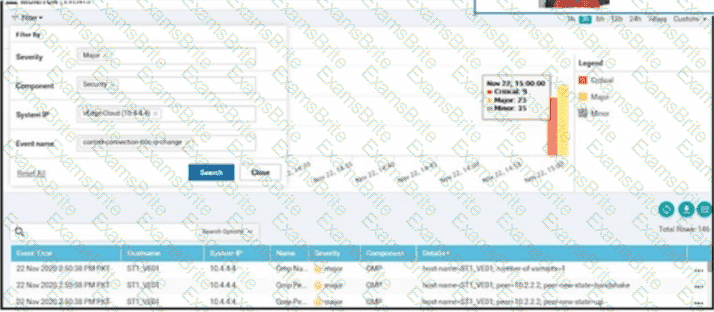
C)
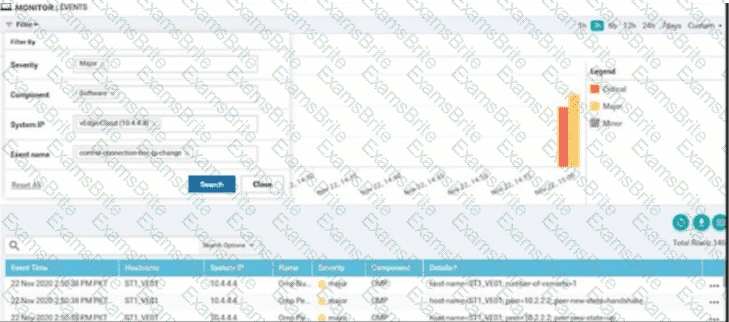
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in vManage achieves this goal?
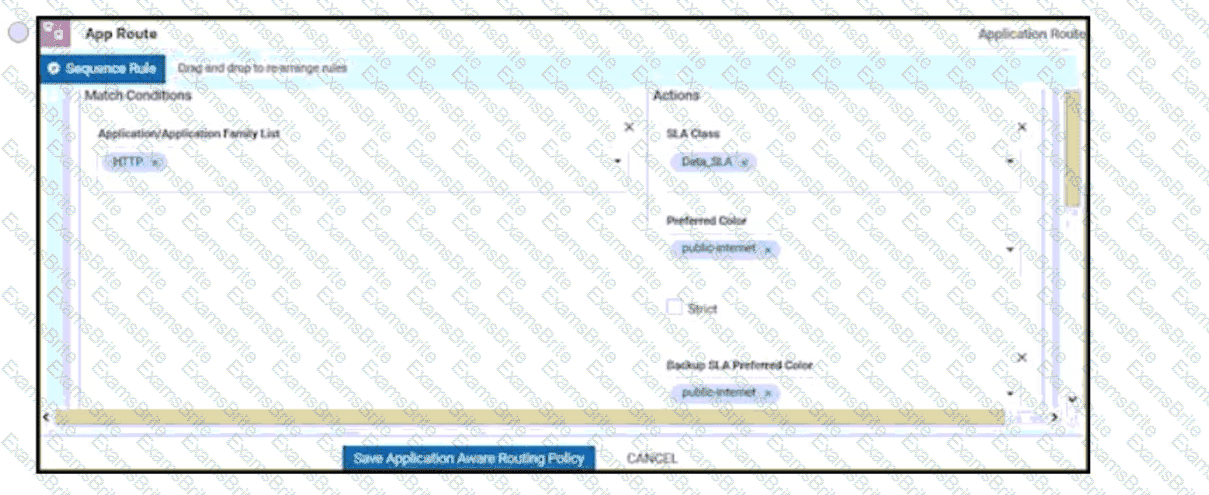
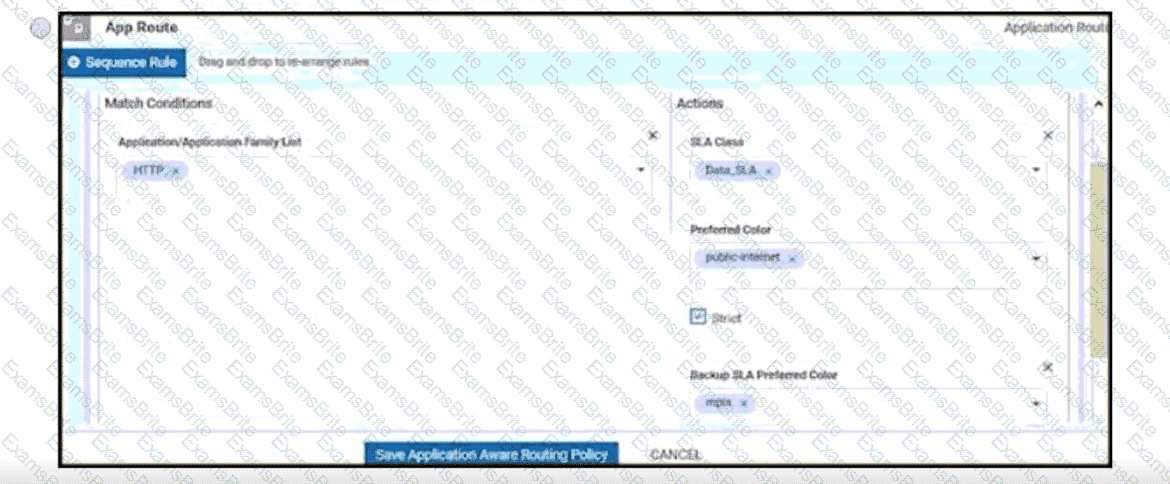
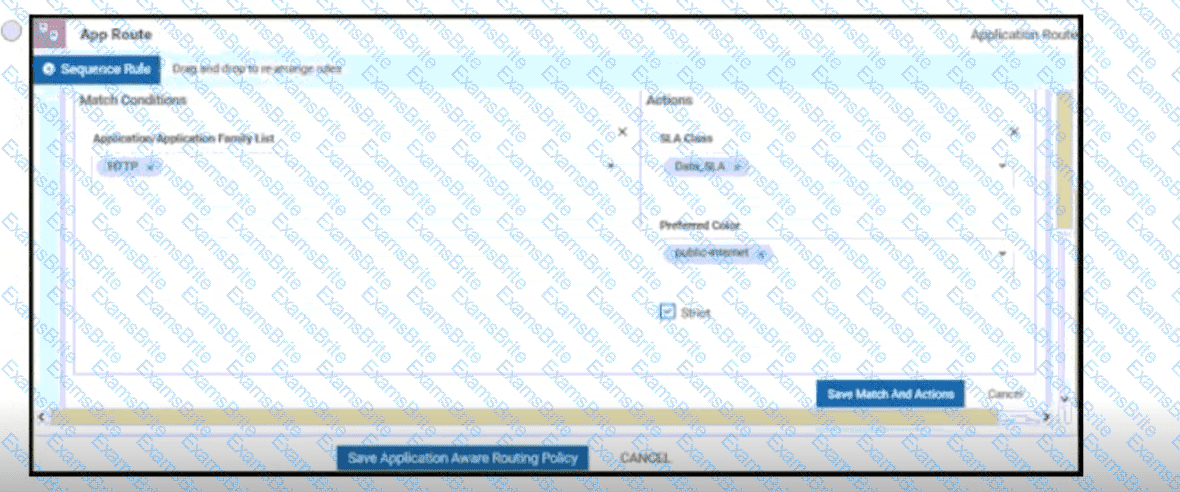
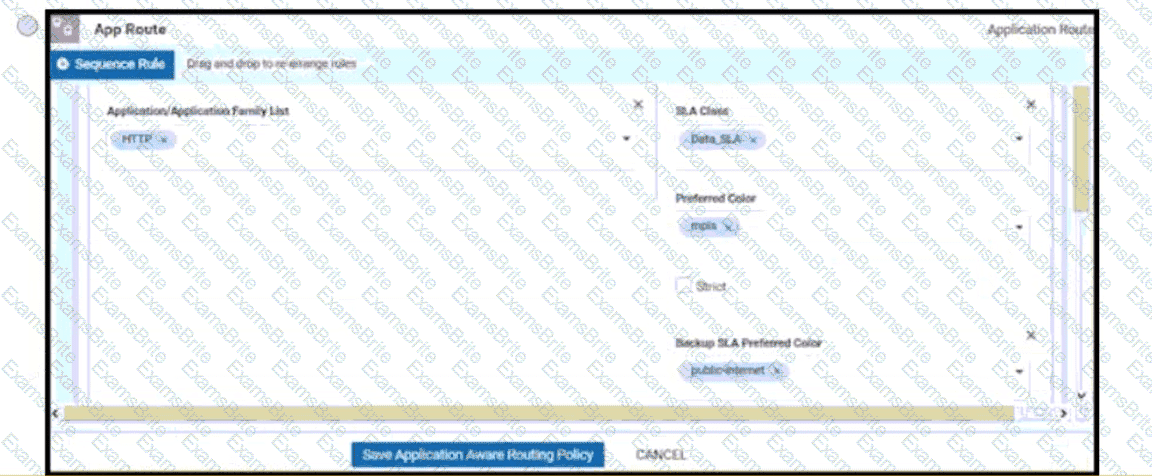
An administrator needs to configure SD-WAN to divert traffic from the company's private network to an ISP network. What action should be taken to accomplish this goal?
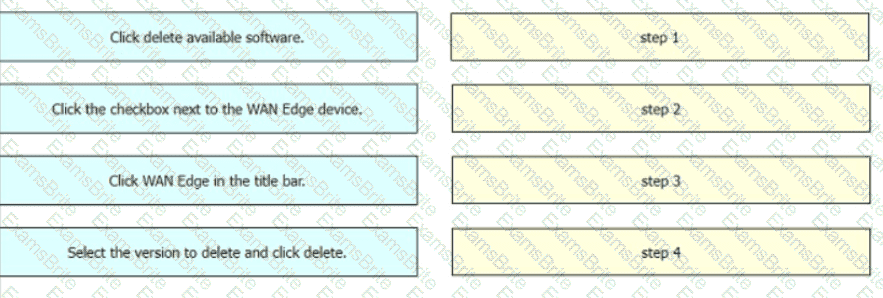
Drag and drop the steps from the left Into the order on the right to delete a software image for a WAN Edge router starting with Maintenance > Software Upgrade > Device list on vManage.
An engineer must configure the SD-WAN Edge router to identify DSCP 26 traffic coming from the router's local site and then change the DSCP value to DSCP 18 before sending it over to the SD-WAN fabric. What are the two ways to create the required configuration? (Choose two).
Which OMP route is selected for equal OMP route preference values on WAN Edge routers?
What is the default value for the number of paths advertised per prefix in the OMP feature template?
A network administrator is bringing up one WAN Edge for branch connectivity. Which types of tunnels form when the WAN edge router connects to the SD-WAN fabric?
Which type of route represents prefixes received from a local site via an SD-WAN Edge router in a Cisco SD-WAN architecture?
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
How many vCPUs and how much RAM are recommended to run the vSmart controller on the KVM server for 251 to 1000 devices in software version 20.4.x?
Which component of the Cisco SD-WAN control plane architecture should be located in a public Internet address space and facilitates NAT-traversal?
A network administrator configures SNMFV3 on a Cisco WAN Edge router from CL I for monitoring purposes How many characters are supported by the snmp user username command?
Which IP address must be reachable by a WAN Edge device for the ZIP process to work?
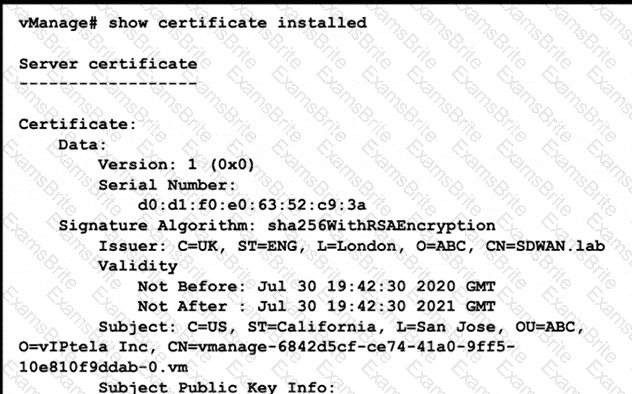

Refer to the exhibit A small company was acquired by a large organization As a result, the new organization decided to update information on their Enterprise RootCA and generated a new certificate using openssl Which configuration updates the new certificate and issues an alert in vManage Monitor | Events Dashboard?
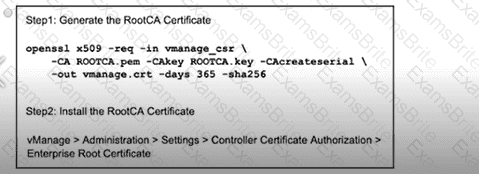
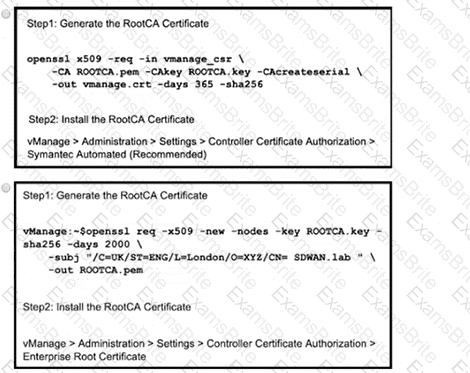

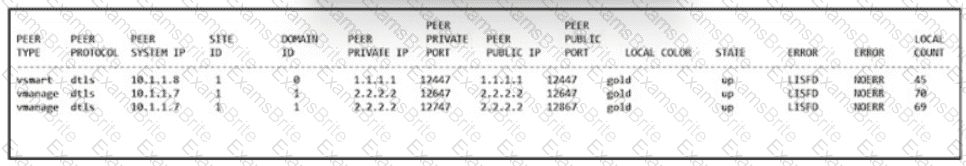
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue?
An enterprise needs DIA on some of its branches with a common location ID: A041:B70C: D78E::18 Which WAN Edge configuration meets the requirement?
A)
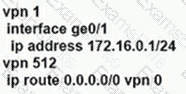
B)
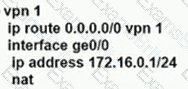
C)
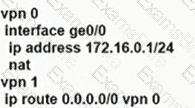
D)
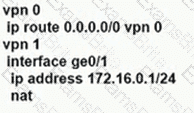
Refer to the exhibit.
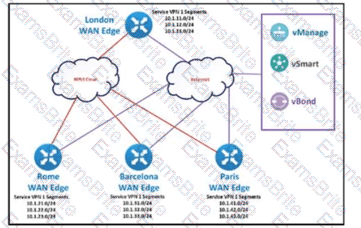
The SD-WAN network is configured with a default full-mesh topology. The SD-WAN engineer wants the Barcelona WAN Edge to use MPLS TLOC as the preferred TLOC when communicating with Rome site. Which configuration must the engineer use to create a list to select MPLS color toward the Rome TLOC?
A)
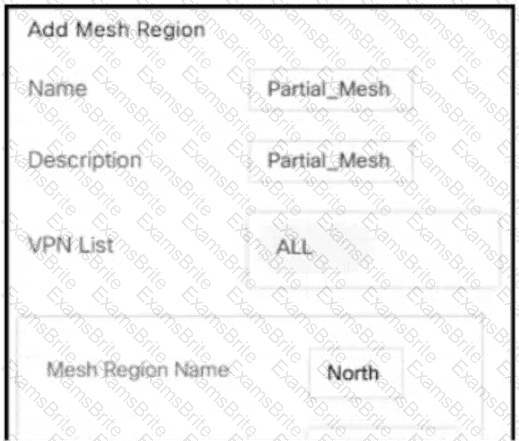
B)
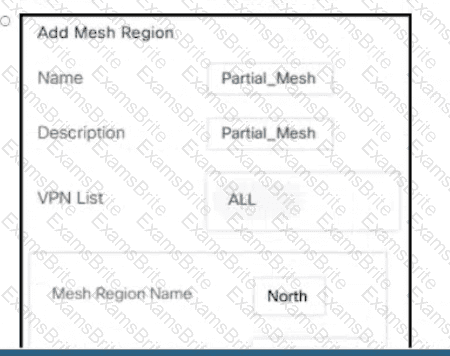
C)

D)
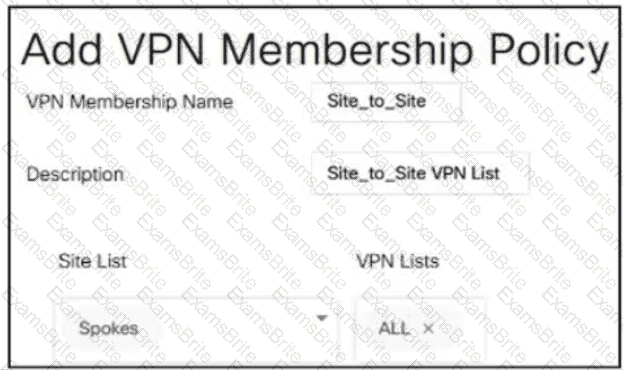
Which policy allows communication between TLOCs of data centers and spokes and blocks communication between spokes?
Which two mechanisms are used by vManage to ensure that the certificate serial number of the WAN Edge router that is needed to authenticate is listed in the WAN Edge Authorized Señal Number Hst’ (Choose two)
How many subnets are necessary in Azure VNet for a WAN Edge device to function in the cloud deployment?
Refer to the exhibit.
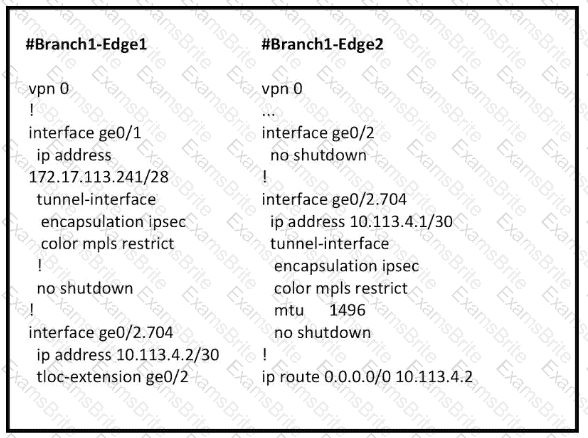
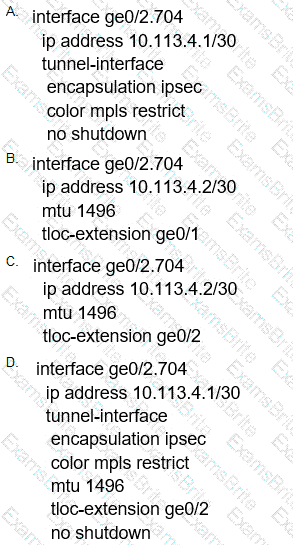
Which configuration change is needed to configure the tloc-extention on Branch1-Edge1?
Which VPNs must be configured outside the workflow to complete the SD-WAN overlay setup when using the Quick Connect workflow?
Which two actions are necessary to set the Controller Certificate Authorization mode to indicate a root certificate? (Choose two)
What two functions describe the TCP optimization tool used in the Cisco SD-WAN? (Choose two.)
An engineer must use data prefixes to configure centralized data policies using the vManage policy configuration wizard. What is the first step to accomplish this task?
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
Which on-the-box security feature supported by the Cisco ISR 4451 SD-WAN device and not on vEdge?
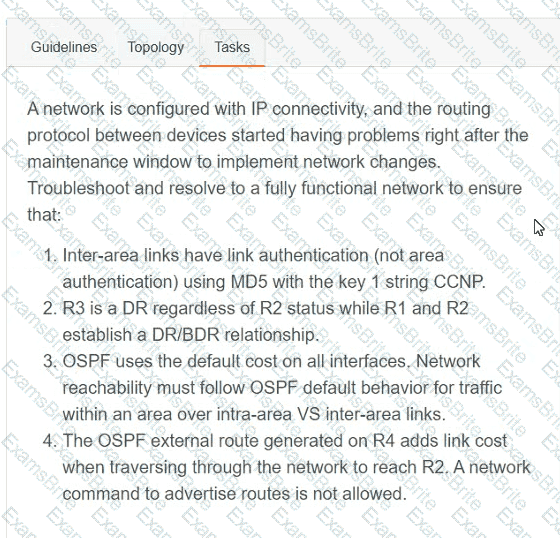
A network is configured with IP connectivity, and the routing protocol between devices started having problems right after the maintenance window to implement network changes. Troubleshoot and resolve to a fully functional network to ensure that:
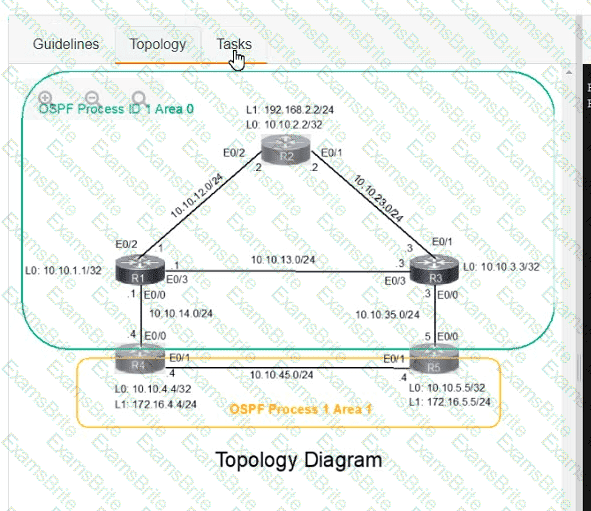
R4
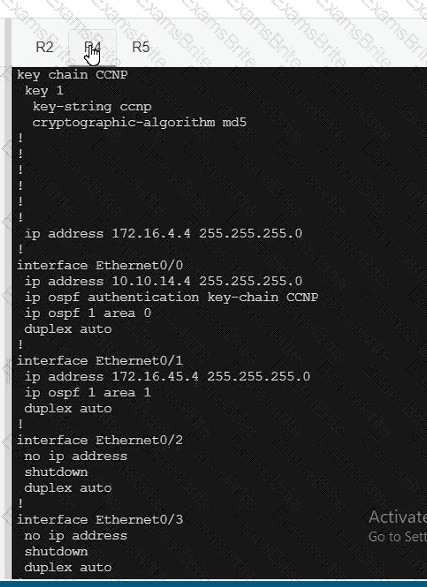
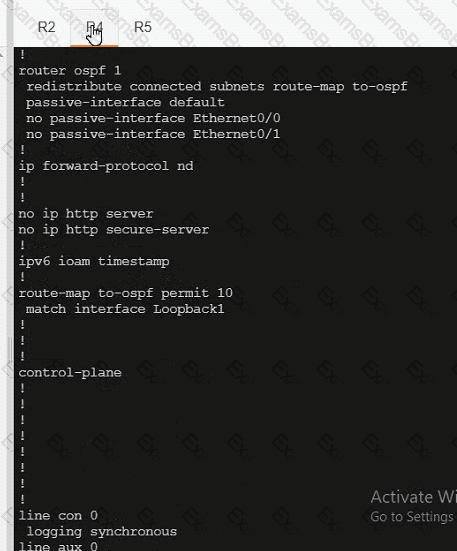
R5
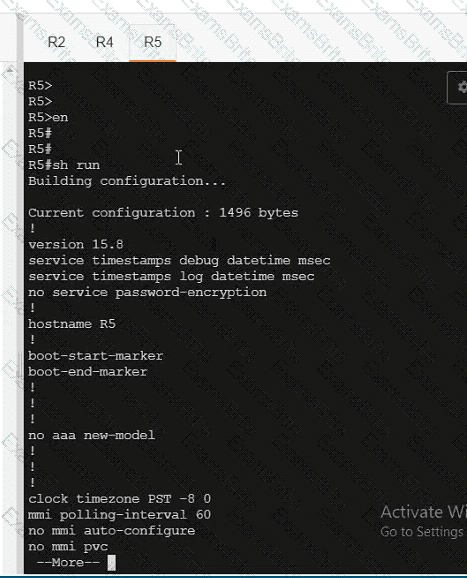
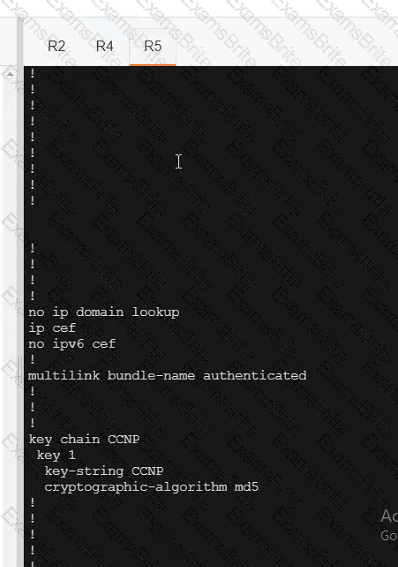
Which policy tracks path characteristics such as loss, latency, and jitter in vManage?
Which configuration step is taken on vManage after WAN Edge list is uploaded?
Refer to the exhibit. Which configuration ensures that OSPP routes learned from Site2 are reachable at Stein and vice-versa?
Refer to the exhibit An engineer must configure a QoS policy between me hub and site A (spoke) over a standard internet circuit where traffic shaping is adjusted automatically based on evaiiabk» bandwidth Which configuration meets the requirement?


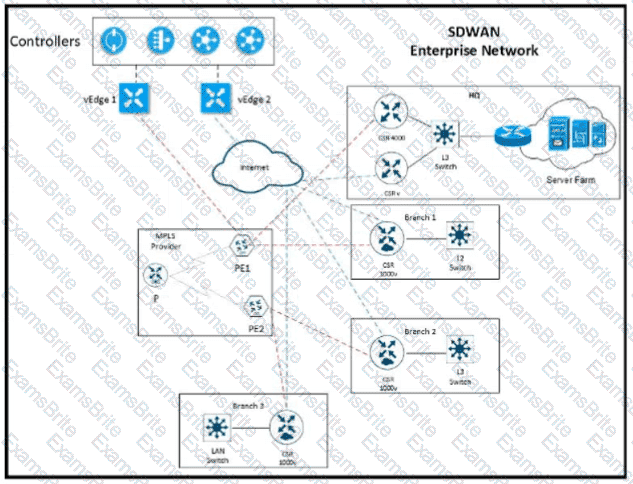
Refer to the exhibit The network team must configure ElGRP peering at HQ with devices in the service VPN connected to WAN Edge CSRv. CSRv is currently configured with
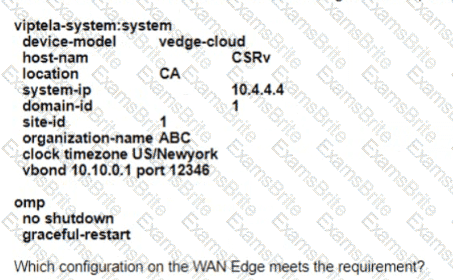
Which configuration on the WAN Edge meets the requiremnet
A)
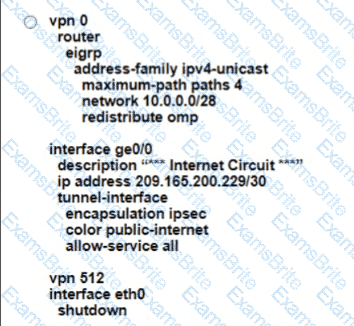
B)
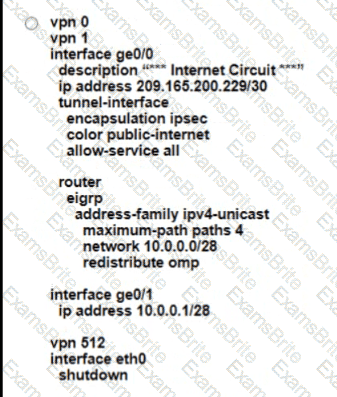
C)
D)
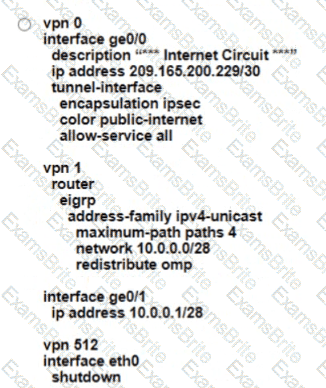
How is a TLOC uniquely identified from a WAN Edge router to the SD-WAN transport network?
Refer to the exhibit.
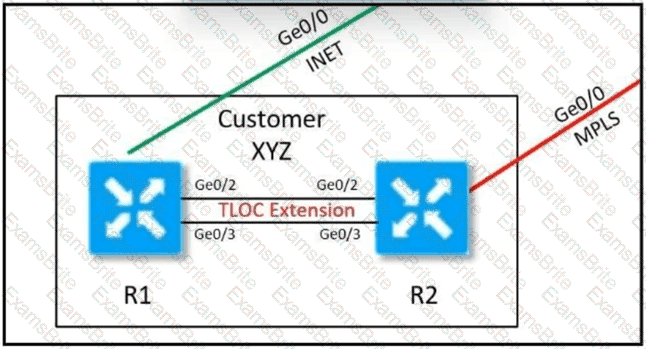
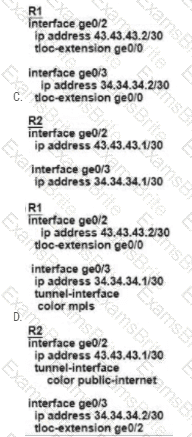
Customer XYZ cannot provision dual connectivity on both of its routers due to budget constraints but wants to use both R1 and R2 interlaces for users behind them for load balancing toward the hub site. Which configuration achieves this objective?


Which protocol is used between redundant vSmart controllers to establish a permanent communication channel?
What must an engineer conewef when decoying an SD-WAN on-pfemlses architecture based on ESXi hypervisor?
Drag and drop the alarm states from the left onto the corresponding alarm descriptions on the right.

An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN device with circuit ID 391897770. Which policy must be used to configure this ACL?
In which device state does the WAN edge router create control connections, but data tunnels are not created?
Which third-party Enterprise CA server must be used (or a cloud-based vSmart controller?
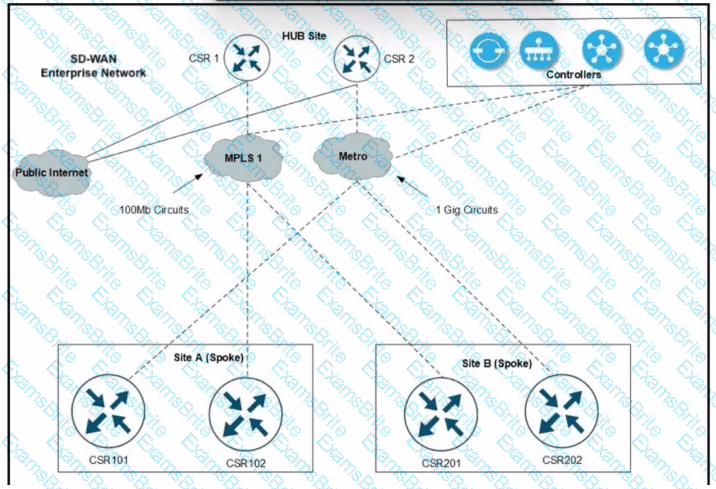
Refer to the exhibit. A Cisco SD-WAN network carries traffic for several departments and over 1200 users with several applications at site A and site B branches over the MPLS1 circuit. An engineer is provisioning a higher bandwidth on-demand metro circuit as a backup connection. Which two configurations must the engineer apply to implement the on-demand tunnels? (Choose two.)
Which two different states of a WAN Edge certificate are shown on vManage? (Choose two.)
An engineer provisions a WAN Edge router. Which command should be used from the WAN Edge router to activate it with vManage?
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration?
Which statement describes the requirement of integrating a secure internet gateway (SIG) with a Cisco SD-WAN Edge device?
At which layer does the application-aware firewall block applications on a WAN Edge?
An engineer is adding a tenant with location ID 399533345 in vManage. What is the maximum number of alphanumeric characters that is accepted in the tenant name filed?
An engineer must configure local redundancy on a site. Which configuration accomplish this task?
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration?
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric?
What are the two components of an application-aware firewall? (Choose two.)
An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
In which VPN is the NAT operation on an outgoing interface configured for direct Interne! access?
A bank is looking for improved customer experience for applications and reduce overhead related to compliance and security. Which key feature or features of the Cisco SD-WAN solution will help the bank to achieve their goals?
What is an advantage of using auto mode versus static mode of power allocation when an access point is connected to a PoE switch port?
Refer to the exhibit.
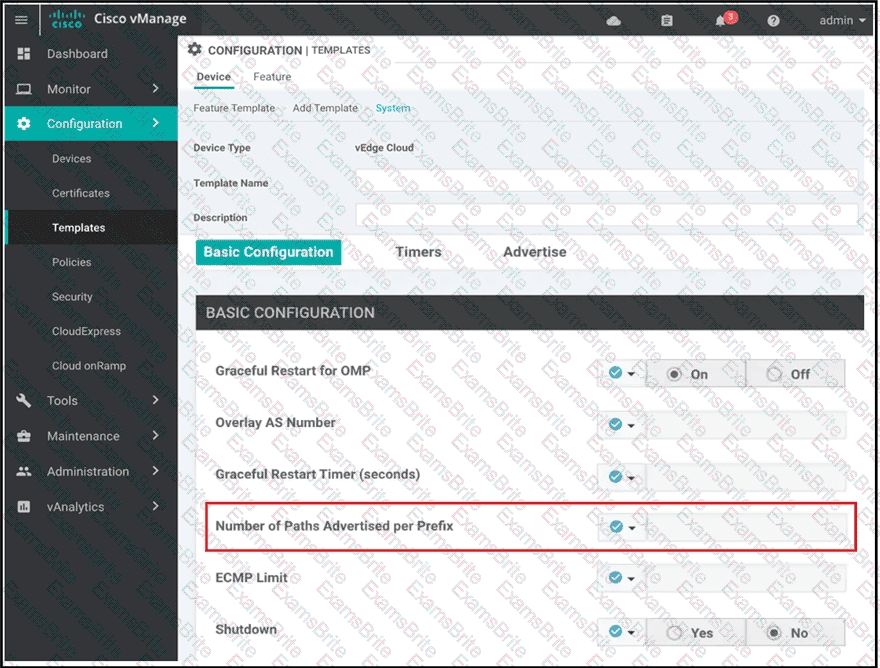
A network administrator is configuring OMP in vManage to advertise all the paths for the same prefix from a site that has two WAN Edge devices Each WAN Edge device is connected to three ISPs and two private MPLS transports. What is the minimum value for 'Number of Paths advertised per Prefix" that should be configured?
Which device information is required on PNP/ZTP to support the zero-touch onboarding process?
Which two services are critical for zero touch provisioning on-boarding? (Choose two)
In which Cisco SD-WAN deployment scenario does Cisco Umbrella SIG deliver the most value?
A network engineer sets tags in OMP for routes that were originated in the Service VPN. Which monitoring tab must be used to verify tags on the next hop?
The branch users of an organization must be prevented from accessing malicious destinations, and the local files on users' systems must be protected from malware. Which two Cisco products must the organization deploy? (Choose two.)
Which controller is excluded from the process of checking against the authorized, allowed list?
An organization requires the use of integrated preventative engines, exploit protection, and the most updated and advanced signature-based antivirus with sandboxing and threat intelligence to stop malicious attachments before they reach users and get executed. Which Cisco SD-WAN solution meets the requirements?
What do receivers request to join multicast streams in a Cisco SO-WAN network?
What is the maximum number of IPsec that are temporarily created and converged on a new set if IPsec Sas in the pairwise keys process during a simultaneous rekey?
Which hardware component is involved in the Cisco SD-WAN authentication process for ISR platforms?
Drag and drop the REST API calls from the left onto the functions on the right.
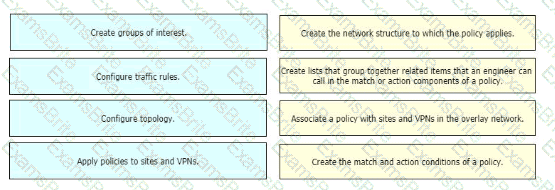
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right.
Refer to the exhibit The network team must configure application-aware routing for the Service VPN 50.0.0.0/16 The SLA must prefer MPLS for video traffic but the remaining traffic must use a public network What must be defined other than applications before the application-aware policy is create?
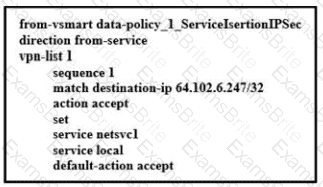
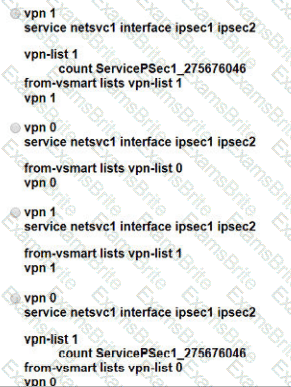
Refer to the exhibit, which configuration configures IPsec tunnels in active and standby?
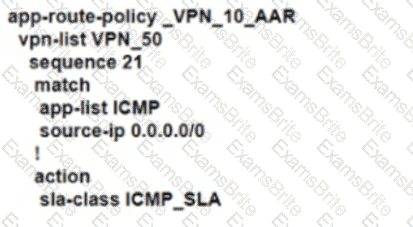
An enterprise deployed a Cisco SD-WAN solution with hub-and-spoke topology using MPLS as the preferred network over the Internet. A network engineer must implement an application-aware routing policy to allow ICMP traffic to be load-balanced over both the available links. Which configuration meets the requirement?
A)

B)
C)

D)

An engineer must configure egress QoS for voice traffic. Which queue must the engineer configure on the WAN Edge router to accomplish the task?
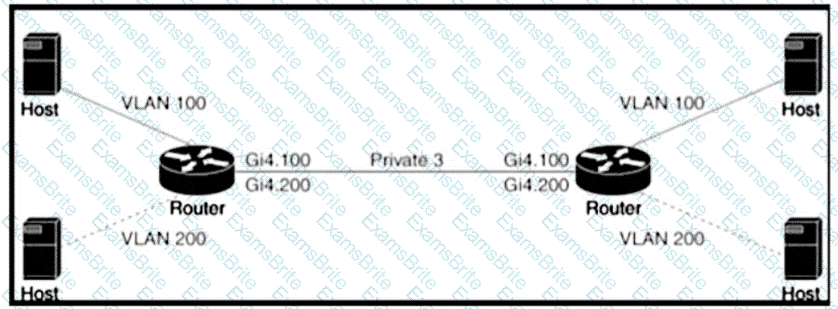
Refer to the exhibit An engineer is configuring a QoS policy to shape traffic for VLAN 100 on a subinterface Which policy configuration accomplishes the task?
A)
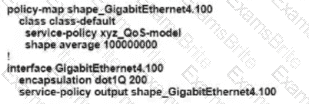
B)

C)
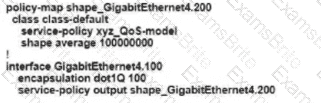
D)
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
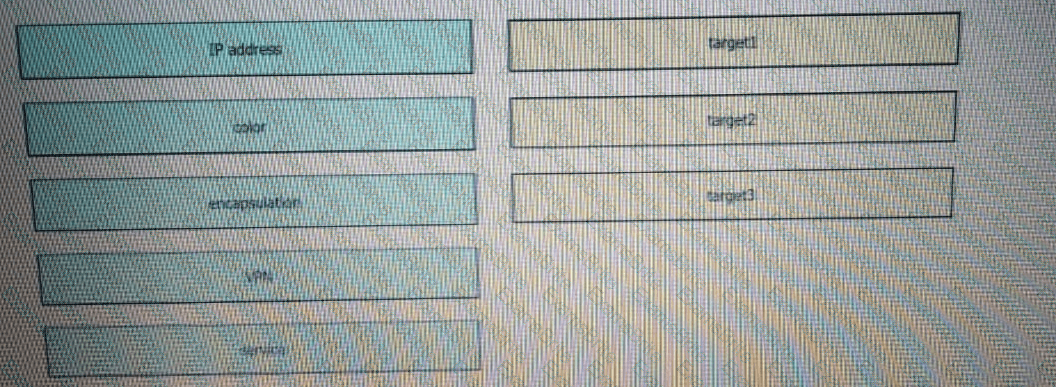
Which service VPN must be reachable from all WAN Edge devices and the controllers?
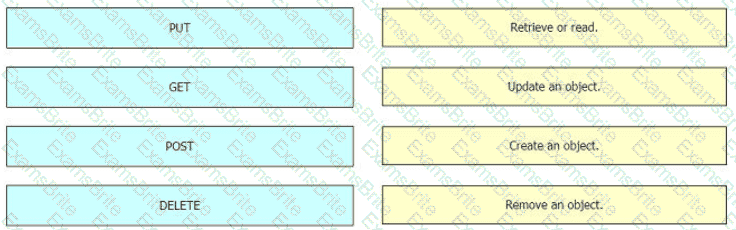
REST applications communicate over HTTP or HTTPS to make calls between network devices. Which two HTTPS standard methods are included? (Choose two.)
Which component is used to optimize the multicast distribution tree enabled through the multicast network?
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI?
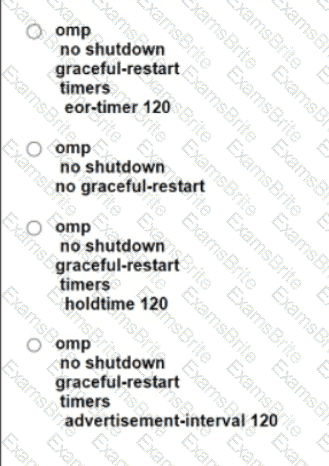
Which timer specifies information in the cache after all OMP sessions are lost at location S0123T4E56F78?
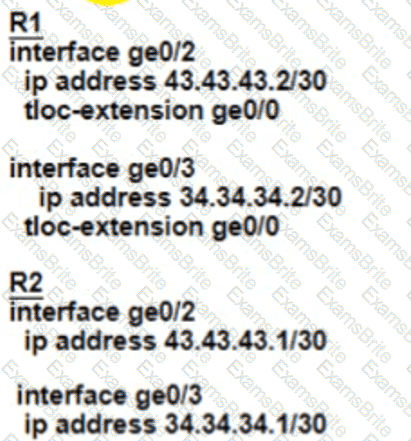
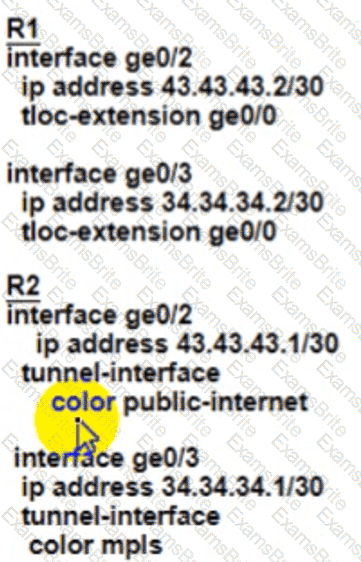
Refer to the exhibit.
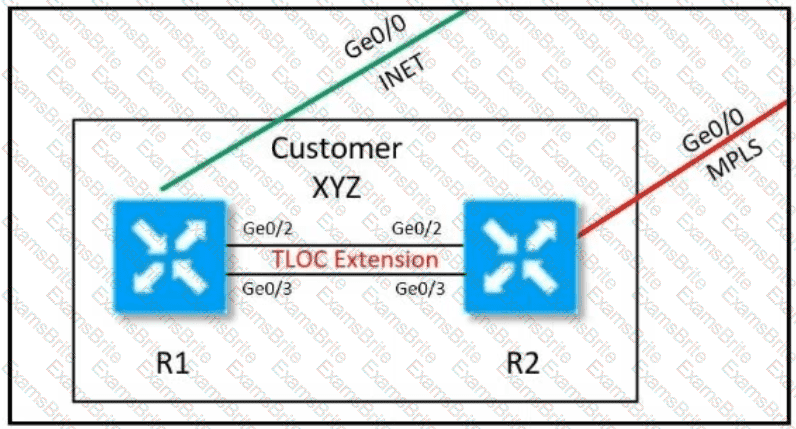
Customer XYZ cannot provison dual connectivity on both Its routers due to budget constratnts but wants to use tnth RI and R2 interface for users behind them for load toward the hub site Which configurauon achieves this objectives?
A)
B)

C)
D)

In a Cisco SD-WAN network, which component is responsible for distributing route and policy information via the OMP?
How many vManage NMSs should be installed in each domain to achieve scalability and redundancy?