CompTIA A+ Certification Core 2 Exam
Last Update Apr 25, 2024
Total Questions : 629
We are offering FREE 220-1102 CompTIA exam questions. All you do is to just go and sign up. Give your details, prepare 220-1102 free exam questions and then go for complete pool of CompTIA A+ Certification Core 2 Exam test questions that will help you more.



A remote user is experiencing issues connecting to a corporate email account on a laptop. The user clicks the internet connection icon and does not recognize the connected Wi-Fi. The help desk technician, who is troubleshooting the issue, assumes this is a rogue access point. Which of the following is the first action the technician should take?
A technician is setting up a new laptop for an employee who travels. Which of the following is the BEST security practice for this scenario?
A technician is installing a new business application on a user's desktop computer. The machine is running Windows 10 Enterprise 32-bit operating system. Which of the following files should the technician execute in order to complete the installation?
A technician is setting up a backup method on a workstation that only requires two sets of tapes to restore. Which of the following would BEST accomplish this task?
A developer is creating a shell script to automate basic tasks in Linux. Which of the following file types are supported by default?
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on
multiple computers on the corporate network. Which of the following BEST describes what the systems administrator should tell the user?
An organization's Chief Financial Officer (CFO) is concerned about losing access to very sensitive, legacy unmaintained PII on a workstation if a
ransomware outbreak occurs. The CFO has a regulatory requirement to retain this data for many years. Which of the following backup methods
would BEST meet the requirements?
A user connected a laptop to a wireless network and was tricked into providing login credentials for a website. Which of the following threats was used to carry out the attack?
A technician has verified that a user's computer has a virus, and the antivirus software is out Of date. Which of the following steps should the technician take NEXT?
A company discovered that numerous computers from multiple geographic locations are sending a very high number of connection requests which is causing the company’s web server to become unavailable to the general public. Which of the following attacks is occurring?
A team of support agents will be using their workstations to store credit card data. Which of the following should the IT department enable on the workstations in order to remain compliant with common regulatory controls? (Select TWO).
A technician is troubleshooting a customer's PC and receives a phone call. The technician does not take the call and sets the phone to silent. Which of the following BEST describes the technician's actions?
A systems administrator is tasked with configuring desktop systems to use a new proxy server that the organization has added to provide content filtering. Which of the following Windows utilities IS the BEST choice for accessing the necessary configuration to complete this goal?
A user reports a workstation has been performing strangely after a suspicious email was opened on it earlier in the week. Which of the following should the technician perform FIRST?
A technician received a call stating that all files in a user's documents folder appear to be Changed, and each of the files now has a look file
extension Which pf the following actions is the FIRST step the technician should take?
The findings from a security audit indicate the risk of data loss from lost or stolen laptops is high. The company wants to reduce this risk with minimal impact to users who want to use their laptops when not on the network. Which of the following would BEST reduce this risk for Windows laptop users?
A change advisory board authorized a setting change so a technician is permitted to Implement the change. The technician successfully implemented the change. Which of the following should be done next?
A technician is troubleshooting an issue that requires a user profile to be rebuilt. The technician is unable to locate Local Users and Groups in the Mtv1C console. Which of the following is the NEXT step the technician should take to resolve the issue?
An Internet cafe has several computers available for public use. Recently, users have reported the computers are much slower than they were the previous week. A technician finds the CPU is at 100% utilization, and antivirus scans report no current infection. Which of the following is MOST likely causing the issue?
A field technician applied a Group Policy setting to all the workstations in the network. This setting forced the workstations to use a specific SNTP server. Users are unable to log in now. Which of the following is the MOST likely cause of this issue?
Which of The following refers to the steps to be taken if an Issue occurs during a change Implementation?
A user is receiving repeated pop-up advertising messages while browsing the internet. A malware scan Is unable to locate the source of an infection. Which of the following should the technician check NEXT?
A technician downloaded a software program to a network share. When the technician attempts to copy the program to the Windows tablet for installation, the technician receives an error. Which of the following is the best procedure for the technician to use to complete the assignment?
A police officer often leaves a workstation for several minutes at a time. Which of the following is the BEST way the officer can secure the workstation quickly when walking away?
A user's laptop has been performing slowly and redirecting to unfamiliar websites. The user has also noticed random pop-up windows. Which of the following is the first step a technician should take to resolve the issue?
A company is recycling old hard drives and wants to quickly reprovision the drives for reuse. Which of the following data destruction methods should the company use?
A student is setting up a new Windows 10 laptop for the upcoming semester. The student is interested in customizing the wallpaper. Which of the following should the student use to change the wallpaper?
An employee has repeatedly contacted a technician about malware infecting a work computer. The technician has removed the malware several times, but the user's PC keeps getting infected. Which of the following should the technician do to reduce the risk of future infections?
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed first to prevent further damage to the host and other systems?
A corporate smartphone was stored for five months after setup. During this time, the company did not have any system updates. When the phone is turned on, an application runs, but it crashes intermittently. Which of the following should a technician do next?
Which of the following is command options is used to display hidden files and directories?
A technician is modifying the default home page of all the workstations in a company. Which of the following will help to implement this change?
An organization is updating the monitors on kiosk machines. While performing the upgrade, the organization would like to remove physical input devices. Which of the following utilities in the Control Panel can be used to turn on the on-screen keyboard to replace the physical input devices?
Which of the following is the best way to limit the loss of confidential data if an employee's company smartphone is lost or stolen?
Maintaining the chain of custody is an important part of the incident response process. Which of the following reasons explains why this is important?
A user recently purchased a second monitor and wants to extend the Windows desktop to the new screen. Which of the following Control Panel options should a technician adjust to help the user?
An administrator received a new shipment of mobile devices. Per company policy, all enterprise-issued devices must have two authentication methods, and the organization has already enforced the use of PIN codes as one method. Which of the following device features should the administrator enable?
A large organization is researching proprietary software with vendor support for a multiuser environment. Which of the following EULA types should be selected?
Which of the following statements describes the purpose of scripting languages?
A branch office suspects a machine contains ransomware. Which of the following mitigation steps should a technician take first?
Which of the following involves sending arbitrary characters in a web page request?
Which of the following combinations meets the requirements for mobile device multifactor authentication?
Which of the following environments allows for the testing of critical systems without the risk of them being negatively impacted by changes?
A user's computer unexpectedly shut down immediately after the user plugged in a USB headset. Once the user turned the computer back on, everything was functioning properly, including the headset. Which of the following Microsoft tools would most likely be used to determine the root cause?
Which of the following file extensions should a technician use for a PowerShell script?
The calendar application on an employee's smartphone is experiencing frequent crashes, and the smartphone has become unresponsive. Which of the following should a technician do first to resolve the issue?
A user clicks a link in an email. A warning message in the user's browser states the site's certificate cannot be verified. Which of the following is the most appropriate action for a technician to take?
A technician was assigned a help desk ticket and resolved the issue. Which of the following should the technician update to assist other technicians in resolving similar issues?
An administrator has submitted a change request for an upcoming server deployment. Which of the following must be completed before the change can be approved?
A technician is familiar with most personnel at a customer's location and has clearance to work unsupervised. Which of the following describes how the technician should handle personal communication while on site?
Which of the following is the most likely to use NTFS as the native filesystem?
A hotel's Wi-Fi was used to steal information on a corporate laptop. A technician notes the following security log:
SRC: 192.168.1.1/secrets.zip Protocol SMB >> DST: 192.168.1.50/capture
The technician analyses the following Windows firewall information:
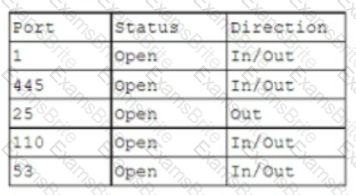
Which of the following protocols most likely allowed the data theft to occur?
When a user is in the office, the user's mobile phone loads applications and web browses very slowly on a cellular connection. Which of the following is the best way to fix this issue?
A user reports being unable to access a sports team's website on an office computer. The administrator tells the user this blocked access is intentional and based on company guidelines. Which of the following is the administrator referring to?
A company wants to take advantage of modern technology and transition away from face-to-face meetings. Which of the following types of software would benefit the company the most? (Select two).
A technician is troubleshooting a PC that is unable to perform DNS lookups. Utilizing the following firewall output:
Protocol/PortActionDirection
1 AllowOut
445 BlockOut
53 BlockOut
123 BlockOut
80 BlockOut
Which of the following ports should be opened to allow for DNS recursion?
An organization is creating guidelines for the incorporation of generative Al solutions. In which of the following would these guidelines be published?
A technician needs to replace a PC's motherboard. The technician shuts down the PC. Which of the following steps should the technician take next?
A technician is upgrading the Microsoft Windows 10 OS. Which of the following are required for the technician to safely upgrade the OS? (Select two).
A user's workstation was infected with a newly discovered virus that the AV system detected. After a full virus scan and a workstation reboot, the virus is still present in the OS. Which of the following actions should the user take to remove the virus?
A technician wants to update the local security policies on a Windows machine but is unable to launch the expected snap-in. Which of the following is the most likely reason?
A user receives an error message on a Windows 10 device when trying to access a mapped drive from a Windows XP machine in the office. Other Windows XP devices in the office can access the drive. Which of the following Control Panel utilities should the user select to enable connectivity to the device?
A technician receives a high-priority ticket about sensitive information collected from an end user’s workstation. Which of the following steps should a technician take to preserve the chain of custody for a forensic investigation?
A customer who uses a Linux OS called the help desk to request assistance in locating a missing file. The customer does not know the exact name of the file but can provide a partial file name. Which of the following tools should the technician use? (Select two).
A user is setting up a new Windows 10 laptop. Which of the following Windows settings should be used to input the SSID and password?
A malicious user was able to export an entire website's user database by entering specific commands into a field on the company's website. Which of the following did the malicious user most likely exploit to extract the data?
A technician is troubleshooting a user’s PC that is running slowly and displaying frequent pop-ups. The technician thinks malware may be causing the issues, but before the issues began the user installed anti-malware software in response to a pop-up window Which of the following is the most likely cause of these issues'?
Which of the following is used to generate passcodes necessary to access applications or systems that require an extra layer of security?
A network administrator wants to enforce a company's security policy that prohibits USB drives on user workstations. Which of the following commands should the administrator run on the users' workstations?
A user accidentally installed the incorrect word processing application on an iMac. Which of the following would allow the user to uninstall the incorrect application?
A technician has been unable to remediate a persistent malware infection on a user's workstation. After the technician reinstalled the OS. the malware infection returned later that day. Which of the following is the most likely source?
A technician is following the ticketing system’s best practices when handling user support requests. Which of the following should the technician do first when responding to a user support request that contains insufficient information?
Which of the following macOS file types requires mounting before installation?
An employee has been using the same password for multiple applications and websites for the past several years. Which of the following would be best to prevent security issues?
An employee using an Apple MacBook is receiving frequent, random pop-up requests from other Apple devices wanting to share photos and videos and asking whether the user would like to accept the request Which of the following configurations should the technician advise the user to change first"?
A technician is troubleshooting a smartphone that is unable to download and install the latest OS update. The technician notices the device operates more slowly than expected, even after rebooting and closing all applications. Which of the following should the technician check next?
A user is unable to see transaction details on a website, and nothing happens when the user clicks the details button. Which of the following should the user do to fix this issue?
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A technician is troubleshooting a user’s PC that is displaying pop-up windows, which are advertising free software downloads. When the technician tries to open a document, the system displays an error message that reads: Not enough memory to perform this operation. Which of the following should be the technician's next step to resolve this issue?
An administrator needs to back up the following components of a single workstation:
•The installation of the operating system
•Applications
•User profiles
•System settings
Which of the following backup methods can the administrator use to ensure the workstation is properly backed up?
Employees at comptia.org are reporting getting an usual amount of emails from a coworker. A technician discovers the emails were sent from the following address:
john@cOmptia.org
Which of the following social engineering attacks is this an example of?
A technician downloaded an OS installation file but is unable to run it. When the technician tries to open the file, a message indicates no software is installed to run this file. Which of the following should the technician do next to attempt to access the OS file?
An organization wants to deploy a customizable operating system. Which of the following should the organization choose?
A user's work PC has been the target of multiple phishing attacks. Which of the following is a way for the user to prevent further attacks?
A user connected an external hard drive but is unable to see it as a destination to save files. Which of the following tools will allow the drive to be formatted?
A client wants a technician to set up a proxy server in a branch office to manage internet access. This involves configuring the workstations to use the new proxy server. Which of the following Internet Options tabs in Control Panel would be most appropriate for the technician to use to configure the settings?
A hard drive that previously contained PI I needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A technician is setting up a newly built computer. Which of the following is the fastest way for the technician to install Windows 10?
Users access files in the department share. When a user creates a new subfolder, only that user can access the folder and Its files. Which of the following will MOST likely allow all users to access the new folders?
A systems administrator is configuring centralized desktop management for computers on a domain. The management team has decided that all users' workstations should have the same network drives, printers, and configurations. Which of the following should the administrator use to accomplish this task?
A user's corporate laptop with proprietary work Information was stolen from a coffee shop. The user togged in to the laptop with a simple password. and no other security mechanisms were in place. Which of the following would MOST likely prevent the stored data from being recovered?
A user is unable to access files on a work PC after opening a text document. The text document was labeled "URGENT PLEASE READ.txt - In active folder, .txt file titled urgent please read". Which of the following should a support technician do FIRST?
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
A user corrects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the BEST solution to prevent the laptop from going to sleep when it is closed and on the docking station?
Which of the following must be maintained throughout the forensic evidence life cycle when dealing with a piece of evidence?
A technician found that an employee is mining cryptocurrency on a work desktop. The company has decided that this action violates its guidelines. Which of the following should be updated to reflect this new requirement?
A technician is unable to join a Windows 10 laptop to a domain Which of the following is the MOST likely reason?
A technician has been tasked with using the fastest and most secure method of logging in to laptops. Which of the following log-in options meets these requirements?
A technician is configuring a new Windows laptop Corporate policy requires that mobile devices make use of full disk encryption at all limes Which of the following encryption solutions should the technician choose?
A user wants to set up speech recognition on a PC. In which of the following Windows Settings tools can the user enable this option?
A company needs to securely dispose of data stored on optical discs. Which of the following is the MOST effective method to accomplish this task?
A technician has been tasked with installing a workstation that will be used tor point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
A company wants to remove information from past users' hard drives in order to reuse the hard drives Witch of the following is the MOST secure method
A user calls the help desk to report potential malware on a computer. The anomalous activity began after the user clicked a link to a free gift card in a recent email The technician asks the user to describe any unusual activity, such as slow performance, excessive pop-ups, and browser redirections. Which of the following should the technician do NEXT?
A user is unable to log in to the domain with a desktop PC, but a laptop PC is working properly on the same network. A technician logs in lo the desktop PC with a local account but is unable to browse to the secure intranet site to get troubleshooting tools. Which of the following is the MOST likely cause of the issue?
Someone who is fraudulently claiming to be from a reputable bank calls a company employee. Which of the following describes this incident?
A technician needs to formal a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
A technician receives a ticket indicating the user cannot resolve external web pages However, specific IP addresses are working. Which of the following does the technician MOST likely need to change on the workstation to resolve the issue?
A technician is configuring a SOHO device Company policy dictates that static IP addresses cannot be used. The company wants the server to maintain the same IP address at all times. Which of the following should the technician use?
A technician is troubleshooting an issue involving programs on a Windows 10 machine that are loading on startup but causing excessive boot times. Which of the following should the technician do to selectively prevent programs from loading?
A user reports a computer is running slow. Which of the following tools will help a technician identity the issued
A user reports that a PC seems to be running more slowly than usual. A technician checks system resources, but disk, CPU, and memory usage seem to be fine. The technician sees that GPU temperature is extremely high. Which of the following types of malware is MOST likely to blame?
A department has the following technical requirements for a new application:
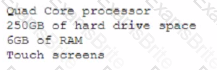
The company plans to upgrade from a 32-bit Windows OS to a 64-bit OS. Which of the following will the company be able to fully take advantage of after the upgrade?
A technician receives a help desk ticket from a user who is unable to update a phone. The technician investigates the issue and notices the following error message: Insufficient storage space
While analyzing the phone, the technician does not discover any third-party' applications or photos. Which of the following is the best way to resolve the issue?
A customer is accessing a public kiosk in a company's lobby. Which of the following should be enforced to mitigate the risk of customer data being accidentally saved to the kiosk?
A department manager submits a help desk ticket to request the migration of a printer's port utilization from USB to Ethernet so multiple users can access the printer. This will be a new network printer, thus a new IP address allocation is required. Which of the following should happen Immediately before network use is authorized?
A user reported that a laptop's screen turns off very quickly after silting for a few moments and is also very dim when not plugged in to an outlet Everything else seems to be functioning normally. Which of the following Windows settings should be configured?
A user attempts to install additional software and receives a UAC prompt. Which of the following is the BEST way to resolve this issue?
A technician is selling up a newly built computer. Which of the following is the FASTEST way for the technician to install Windows 10?
The courts determined that a cybercrimes case could no longer be prosecuted due to the agency's handling of evidence. Which of the following was MOST likely violated during the investigation?
Every time a user tries to open the organization's proprietary application on an Android tablet, the application immediately closes. Other applications are operating normally. Which of the following troubleshooting actions would MOST likely resolve the Issue? (Select TWO).
A corporation purchased new computers for a school. The computers are the same make and model and need to have the standard image loaded. Which of the following orchestration tools should a desktop administrator use tor wide-scale deployment?
A small-office customer needs three PCs to be configured in a network with no server. Which of the following network types is the customer's BEST choice for this environment?
While trying to repair a Windows 10 OS, a technician receives a prompt asking for a key. The technician tries the administrator password, but it is rejected. Which of the following does the technician need in order to continue the OS repair?
A technician has been tasked with troubleshooting audiovisual issues in a conference room. The meeting presenters are unable to play a video with sound. The following error is received:
The Audio Driver is not running.
Which of the following will MOST likely resolve the issue?
A user is unable to access several documents saved on a work PC. A technician discovers the files were corrupted and must change several system settings within Registry Editor to correct the issue. Which of the following should the technician do before modifying the registry keys?
Which of the following common security vulnerabilities can be mitigated by using input validation?
An administrator responded to an incident where an employee copied financial data to a portable hard drive and then left the company with the data. The administrator documented the movement of the evidence. Which of the following concepts did the administrator demonstrate?
Which of the following threats will the use of a privacy screen on a computer help prevent?
A technician needs to establish a remote access session with a user who has a Windows workstation. The session must allow for simultaneous viewing of the workstation by both the user and technician. Which of the following remote access technologies should be used?
A technician installs specialized software on a workstation. The technician then attempts to run the software. The workstation displays a message indicating the software is not authorized to run. Which of the following should the technician do to most likely resolve the issue?
A technician is troubleshooting a customer's PC and receives a phone call. The technician does not take the call and sets the phone to silent. Which of the following BEST describes the technician's actions?
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
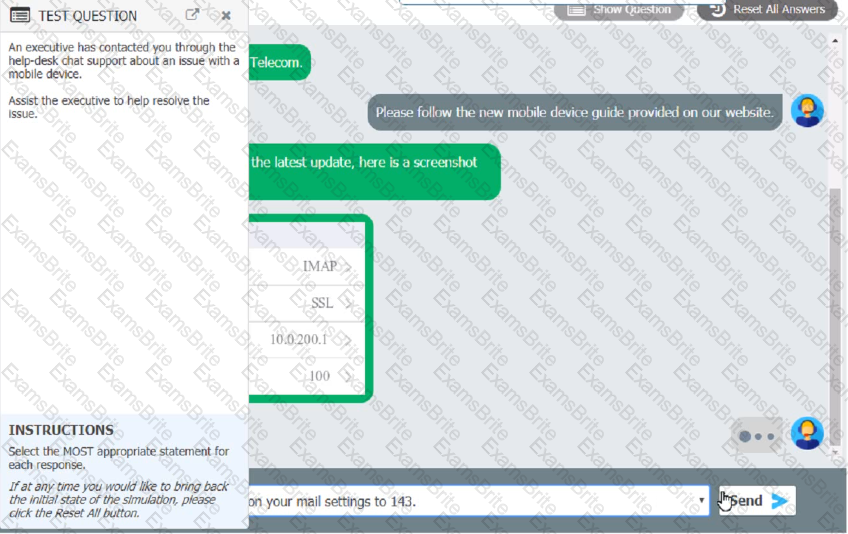
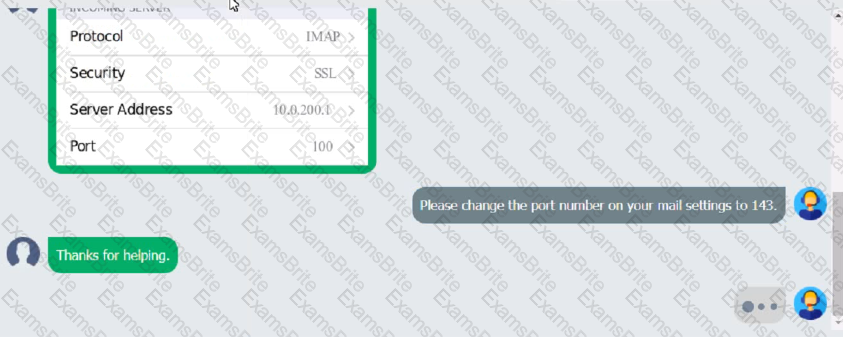
Which of the following should be done NEXT?
A technician has spent hours trying to resolve a computer issue for the company's Chief Executive Officer (CEO). The CEO needs the device returned as soon as possible. Which of the following steps should the technician take NEXT?
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
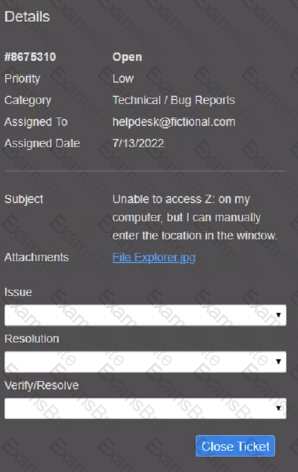
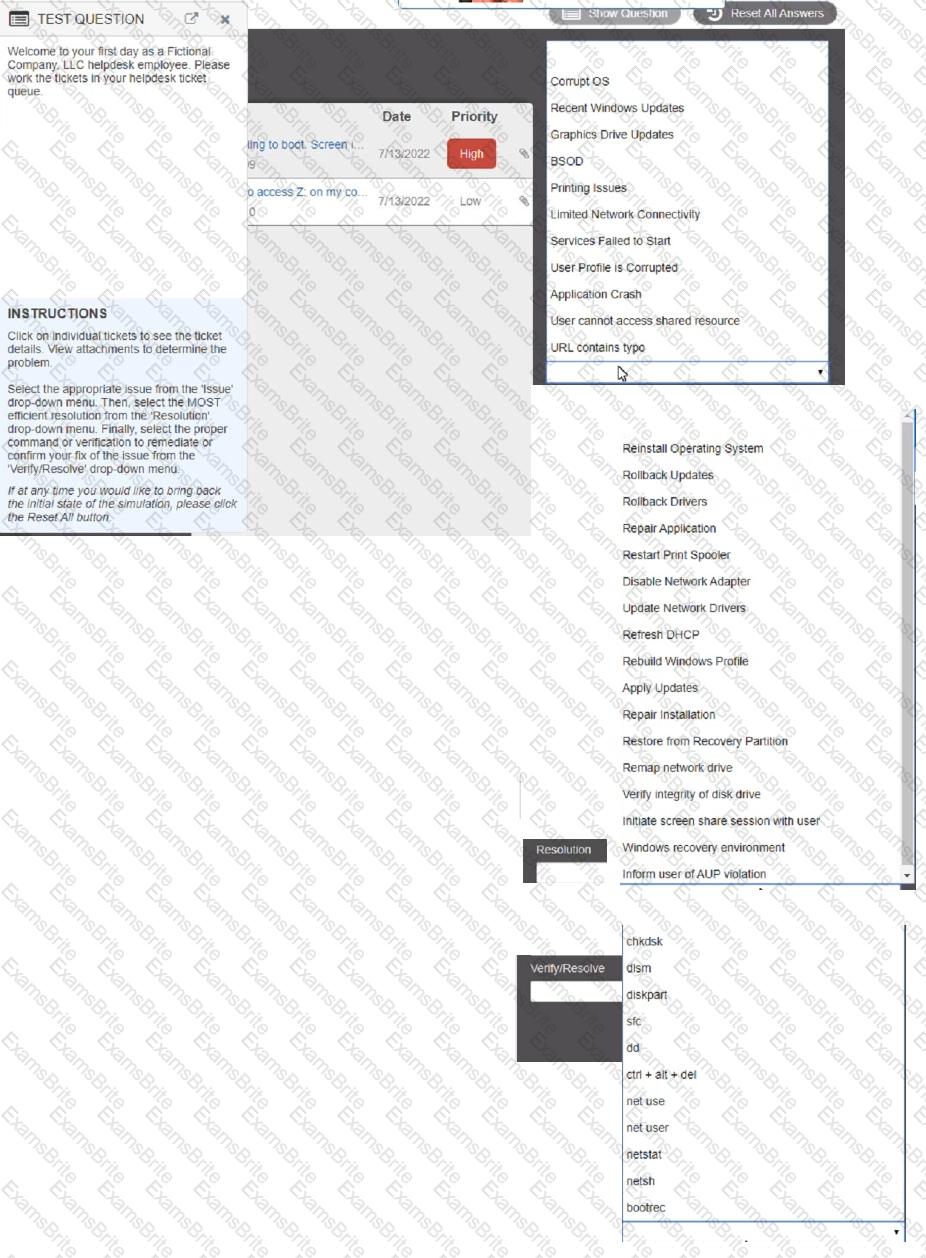
A call center technician receives a call from a user asking how to update Windows Which of the following describes what the technician should do?
A user reports that a workstation is operating sluggishly Several other users operate on the same workstation and have reported that the workstation is operating normally. The systems administrator has validated that the workstation functions normally. Which of the following steps should the systems administrator most likely attempt NEXT?
A network administrator is deploying a client certificate lo be used for Wi-Fi access for all devices m an organization The certificate will be used in conjunction with the user's existing username and password Which of the following BEST describes the security benefits realized after this deployment?
A technician needs to document who had possession of evidence at every step of the process. Which of the following does this process describe?
A user purchased a netbook that has a web-based, proprietary operating system. Which of the following operating systems is MOST likely installed on the netbook?
A change advisory board did not approve a requested change due to the lack of alternative actions if implementation failed. Which of the following should be updated before requesting approval again?
A suite of security applications was installed a few days ago on a user's home computer. The user reports that the
computer has been running slowly since the installation. The user notices the hard drive activity light is constantly solid. Which of the following should be checked FIRST?
A technician has an external SSD. The technician needs to read and write to an external SSD on both Macs and Windows PCs. Which of the following filesystems is supported by both OS types?
A technician is tasked with configuring a computer for a visually impaired user. Which of the following utilities should the technician use?
A technician is reimaging a desktop PC. The technician connects the PC to the network and powers it on. The technician attempts to boot the computer via the NIC to image the computer, but this method does not work. Which of the following is the MOST likely reason the computer is unable to boot into the imaging system via the network?
A technician is working to resolve a Wi-Fi network issue at a doctor's office that is located next to an apartment complex. The technician discovers that employees and patients are not the only people on the network. Which of the following should the technician do to BEST minimize this issue?
A new service desk is having a difficult time managing the volume of requests. Which of the following is the BEST solution for the department?
A technician has just used an anti-malware removal tool to resolve a user's malware issue on a corporate laptop. Which of the following BEST describes what the technician should do before returning the laptop to the user?
A technician downloaded software from the Internet that required the technician to scroll through a text box and at the end of the text box, click a
button labeled Accept Which of the following agreements IS MOST likely in use?
Which of the following is a data security standard for protecting credit cards?
A call center handles inquiries into billing issues for multiple medical facilities. A security analyst notices that call center agents often walk away from their workstations, leaving patient data visible for anyone to see. Which of the following should a network administrator do to BEST prevent data theft within the call center?
Which of the following change management documents includes how to uninstall a patch?
A change advisory board authorized a setting change so a technician is permitted to implement the change. The technician successfully implemented the change. Which of the following should be done NEXT?
Which of the following is used to integrate Linux servers and desktops into Windows Active Directory environments?
A technician is troubleshooting a mobile device that was dropped. The technician finds that the screen (ails to rotate, even though the settings are correctly applied. Which of the following pieces of hardware should the technician replace to resolve the issue?
A technician installed Windows 10 on a workstation. The workstation only has 3.5GB of usable RAM, even though the technician installed 8GB. Which of the following is the MOST likely reason this system is not utilizing all the available RAM?
Which of the following is the proper way for a technician to dispose of used printer consumables?
A user reports that the pages flash on the screen two or three times before finally staying open when attempting to access banking web pages. Which of the following troubleshooting steps should the technician perform NEXT to resolve the issue?
A technician is troubleshooting boot times for a user. The technician attempts to use MSConfig to see which programs are starting with the OS but receives a message that it can no longer be used to view startup items. Which of the following programs can the technician use to view startup items?
A desktop engineer is deploying a master image. Which of the following should the desktop engineer consider when building the master image? (Select TWO).
The audio on a user's mobile device is inconsistent when the user uses wireless headphones and moves around. Which of the following should a technician perform to troubleshoot the issue?
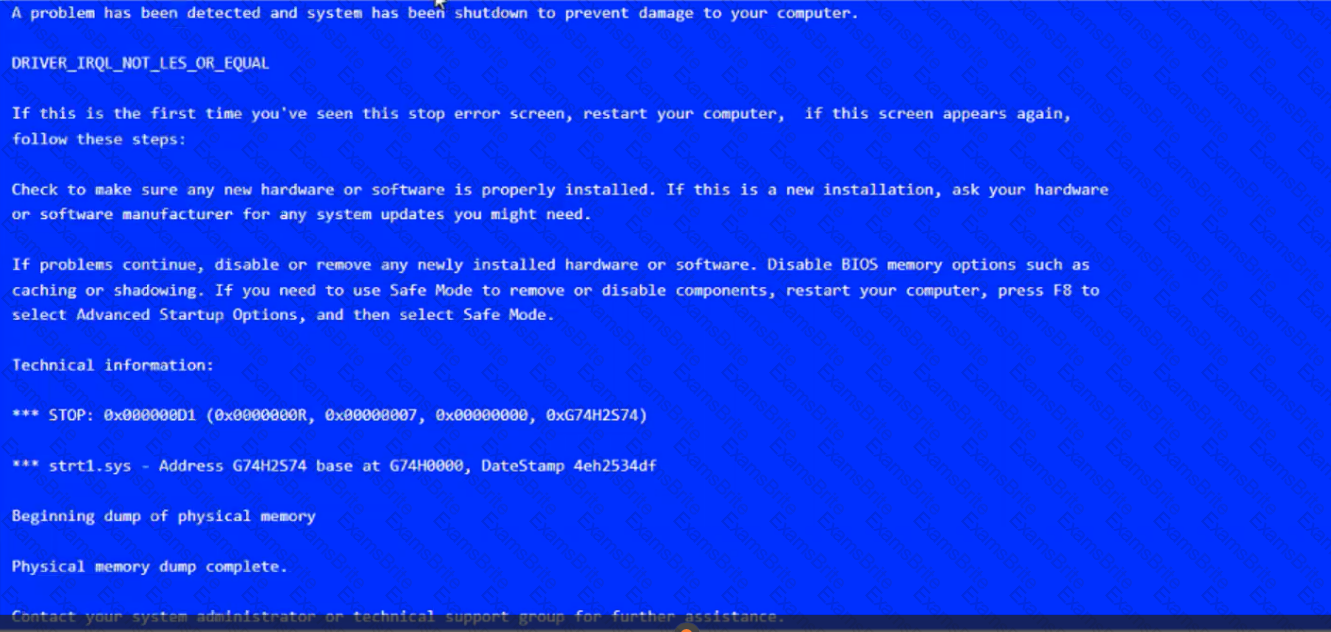
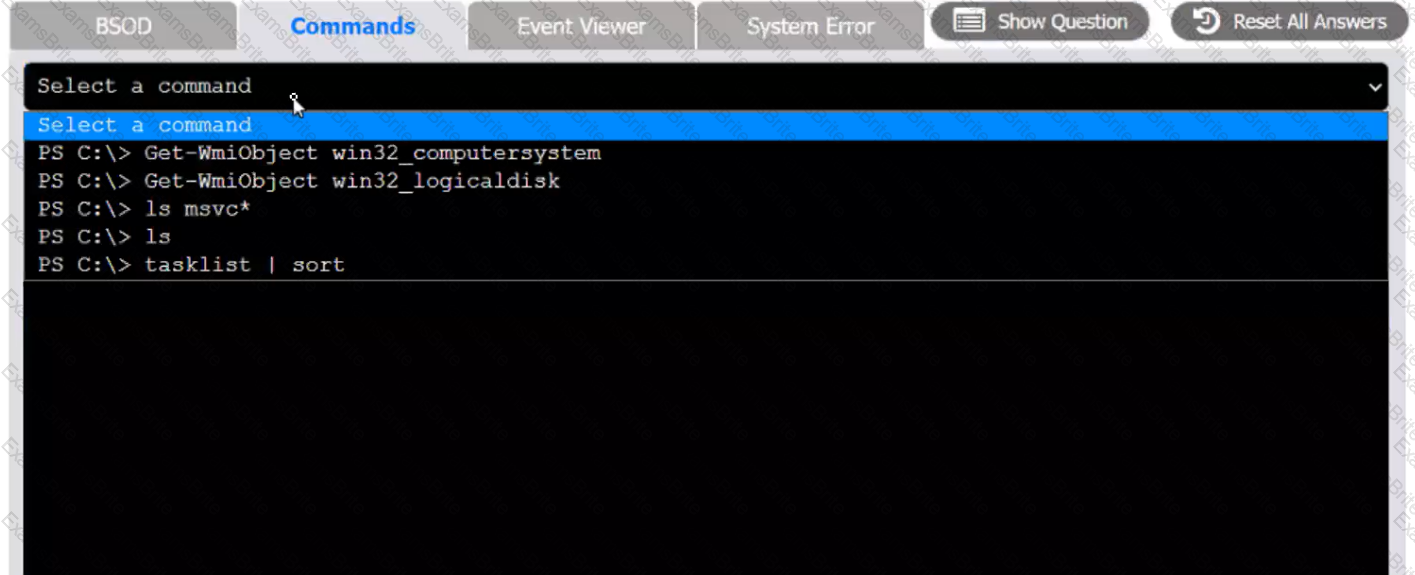
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
BSOD
Commands:
Event Viewer:
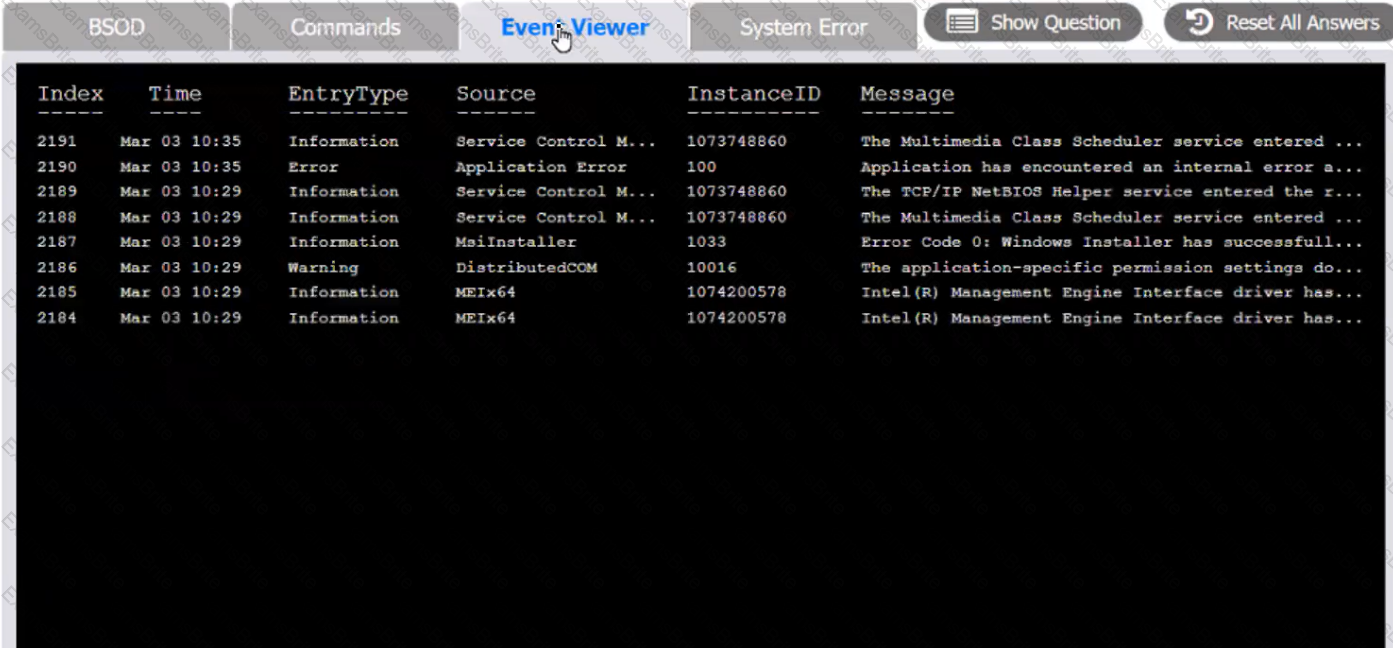
System Error:
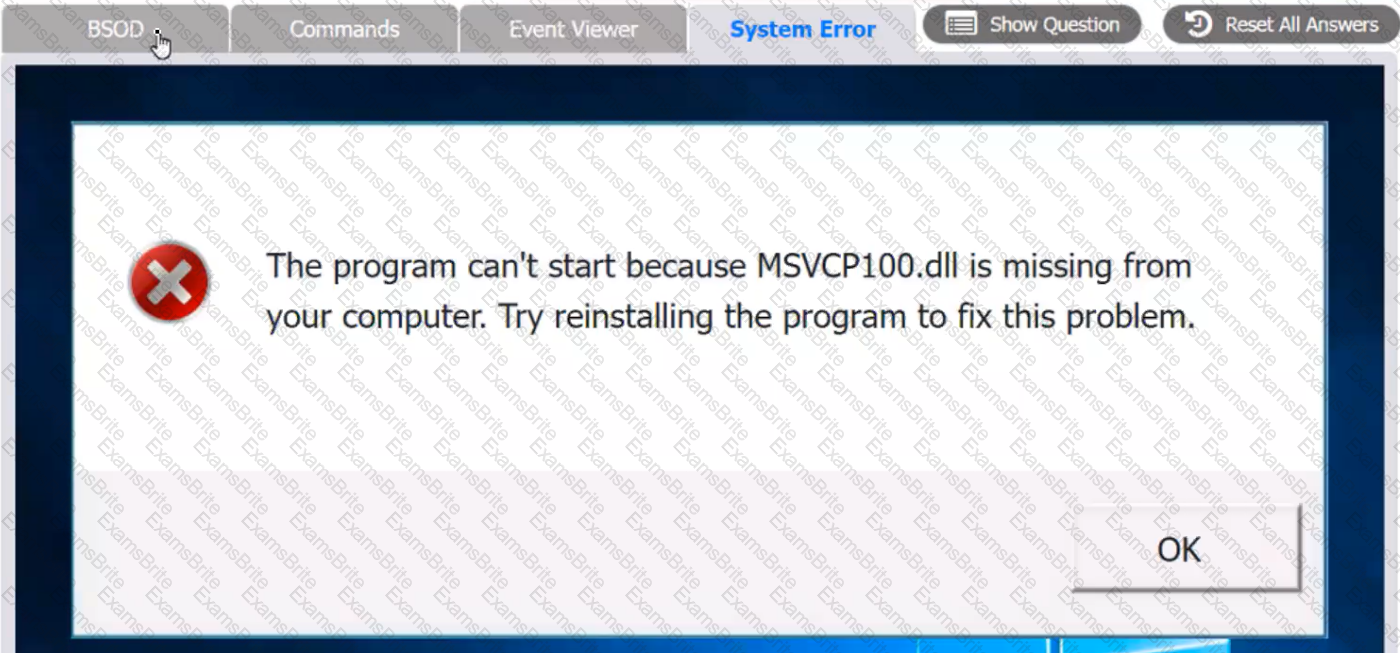

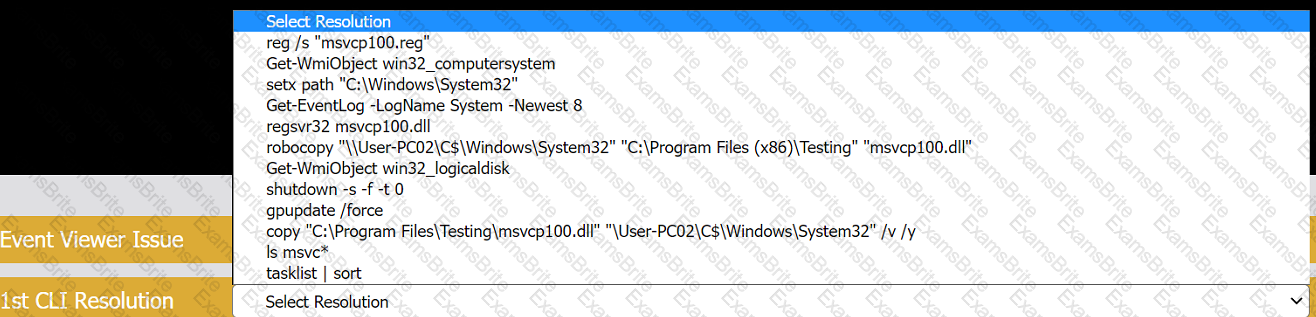
A technician is in the process of installing a new hard drive on a server but is called away to another task. The drive has been unpackaged and left on a desk. Which of the following should the technician perform before leaving?
A homeowner recently moved and requires a new router for the new ISP to function correctly. The internet service has been installed and has been confirmed as functional. Which of the following is the FIRST step the homeowner should take after installation of all relevant cabling and hardware?
A technician needs to access a Windows 10 desktop on the network in a SOHO using RDP. Although the connection is unsuccessful, the technician is able to ping the computer successfully. Which of the following is MOST likely preventing the connection?
A company needs employees who work remotely to have secure access to the corporate intranet. Which of the following should the company implement?
A user added a second monitor and wants to extend the display to it. In which of the following Windows settings will the user MOST likely be able to make this change?
A systems administrator is creating a new document with a list of the websites that users are allowed to access. Which of the following types of documents is the administrator MOST likely creating?
A user receives an error message from an online banking site that states the following:
Your connection is not private. Authority invalid.
Which of the following actions should the user take NEXT?
A technician installed a new application on a workstation. For the program to function properly, it needs to be listed in the Path Environment Variable. Which of the following Control Panel utilities should the technician use?
A technician is working on a way to register all employee badges and associated computer IDs. Which of the following options should the technician use in order to achieve this objective?
A technician needs to add an individual as a local administrator on a Windows home PC. Which of the following utilities would the technician MOST likely use?
While staying at a hotel, a user attempts to connect to the hotel Wi-Fi but notices that multiple SSIDs have very similar names. Which of the following social-engineering attacks is being attempted?
A technician, who is working at a local office, has found multiple copies of home edition software installed on computers. Which of the following does this MOST likely violate?
Which of the following options should MOST likely be considered when preserving data from a hard drive for forensic analysis? (Select TWO).
Which of the following would MOST likely be used to change the security settings on a user's device in a domain environment?
A computer on a corporate network has a malware infection. Which of the following would be the BEST method for returning the computer to service?
A user needs assistance changing the desktop wallpaper on a Windows 10 computer. Which of the following methods will enable the user to change the wallpaper using a Windows 10 Settings tool?
A technician is editing the hosts file on a few PCs in order to block certain domains. Which of the following would the technician need to execute after editing the hosts file?